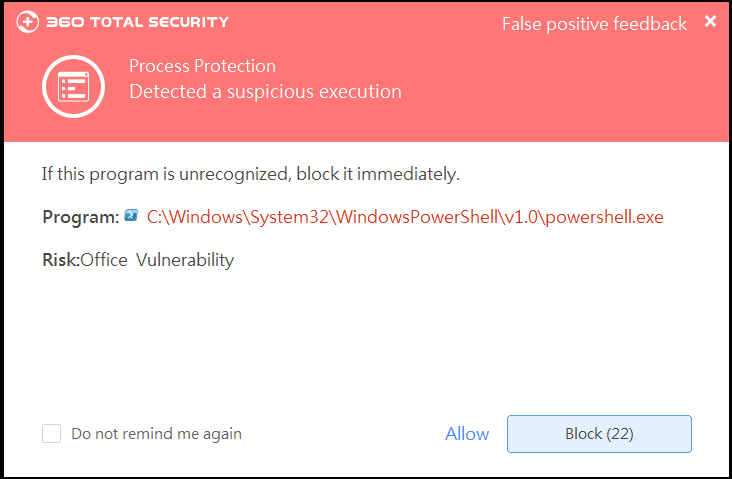
On July 30th, a new high risk loophole of Android Signature was exposed. According to mobile security expert from 360, this is yet another loophole found since July, 2013, which fake signatures can be used as authentic ones. Effected users include some Android 4.4 and all versions below 4.4 which means more than 90% of Android customers. Overseas security company Bluebox Security indicated in their report that the problem is caused by the identifying process of Android signature.Identity recognition is one of the most critical challenge in today’s internet world, for instance, to identify whether the login user of a bank account is the real owner of this account or not. Each user of Android has his own digital signature which is his ID card. For example, one cell phone APP has an owner’s signature on Android and all applications by the APP developer is based on this signed ID. However, Bluebox found that when one application showed its company ID, Android failed to identify the authenticity of the user.In other words, web criminals may be able to login with a fake ID to develop malicious software to break through the sand box protection or to gain access to higher system authority. Mobile security expert of 360 expressed, “One of the threats of this loophole is the possibility of losing private data and to be monitored with ill intention when using Webview application. Another threat is the attacker may gain NFC control power silently which may be risky for users of payment APP such as Google Wallet. Although this is also signature related problem, the threat of this loophole is relatively lower than that loophole of Android system signature. Since the attack launches only when bad APK is installed, 360 experts reminded users to download APP by using something like Google Play which is relatively safe.
Learn more about 360 Total Security360 Expert: New Loopholes found again for Android Signature
Apr 16, 2015360TS
Learn more about 360 Total Security