Preface
Recently, 360MarvelTeam (a research team in Qihoo 360) discovered a typical virtualization DoS flaw of QEMU, CVE-2016-4037, which has been confirmed by Red Hat. 360MarvelTeam found the association between this vulnerability and another one, CVE-2015-8558, and provided a solution to fix them.
Because of the VENOM vulnerability (CVE-2015-3456), the virtual machines (VMs) provided by cloud service providers have been put at risk of cyber attack. The VENOM flaw could lead to a virtual machine escape, allowing attackers to crash the monitoring process and gain control of the host machine and all the VMs on it.
In the field of virtualization security, virtual machine escape is not the only source of damage. Vulnerabilities can also be used to trigger a Denial-of-Service(DoS) attack to occupy the system resources of the cloud data center.
Damage
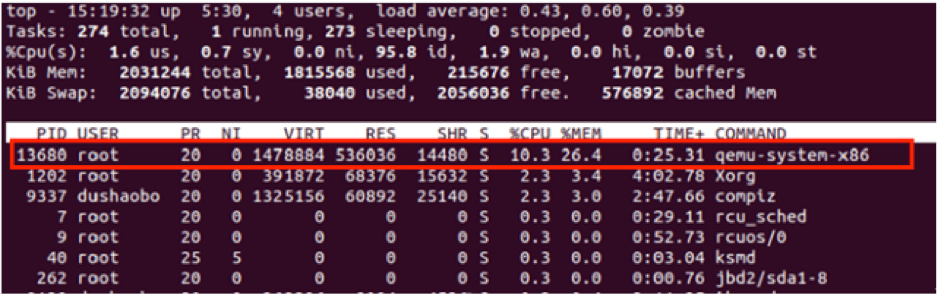
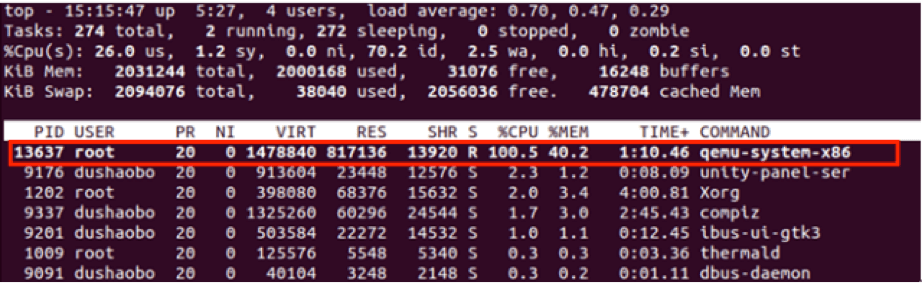
Attackers may exploit this vulnerability to cause a DoS of a virtual machine, by completely consuming the CPU resources, thus impacting the host machine as well as other VMs. Once this flaw is triggered, the CPU usage rate of the host machine is stuck at 100%.
Solution
Upon discovering the vulnerability, 360MarvelTeam reported it to the QEMU team. Together they fixed this issue within 10 days by adding a cycle limit to the while statement of the problematic code to patch this vulnerability.
Also, 360MarvelTeam analyzed CVE-2015-8558, found the association between these two flaws and solved the problem holistically via changing the implementation of the ehci_process_itdc () function.
Red Hat revealed the detail of this vulnerability on April 18th and acknowledged 360MarvelTeam’s contribution.