A new ransomware nicknamed Bad Rabbit is on the rise. First spotted on October 24th, this ransomware has stricken organizations and media outlets in Russia, and even the Odessa International airport in Ukraine. Infections are also reported from Turkey, Germany, and the U.S.
Watch out! Another Petya just arrived
The Bad Rabbit ransomware campaign is the third major outbreak in this year, following its notorious precedents WannaCry and Petya.
Bad Rabbit and Petya are similar in some ways. For example, they both use an open source encryption tool DiskCryptor to lock down files and leverage a SMB component to spread across infected networks.
Furthermore, the ransom note of Bad Rabbit and Petya looks almost the same. In fact, this is not just a coincidence. These two malware share 67% of the same code, indicating that Bar Rabbit is another variant of Petya.
However, unlike WannaCry and Petya were using the EternalBlue exploit to spread, Bad Rabbit is distributed via “drive-by attacks”. Cyberattacker first injected malicious code to a legitimate website, then luring victims to download the malware dropper. In this case, the file-encrypting software is disguised as an Adobe Flash installer. Innocent users are tricked to install it themselves.
See also: Petya Ransomware, a new cyberattack more destructive than WannaCry, just arrived!
“Don’t waste your time! No one will be able to recover your files.”
Once a person clicks on the fake Adobe notification, their PC is locked. A ransom note is displayed, notifying the poor victims their files are no longer accessible, plus a “friendly reminder” to tell them not to waste time on looking for decryption methods. The only way to recover files is to pay the ransom.
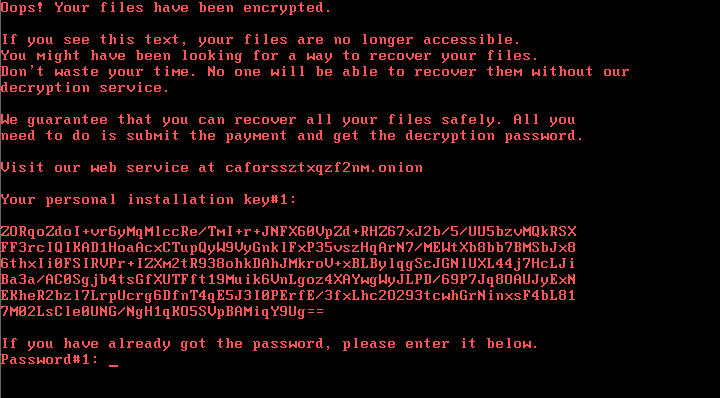
Victims are sent to a Tor payment page and asked to pay 0.05 Bitcoins (around $285) to get access to computer contents. Also on the page is a timer, counting down from just over 41 hours, pressuring victims to pay by the deadline or face the ransom rising up.
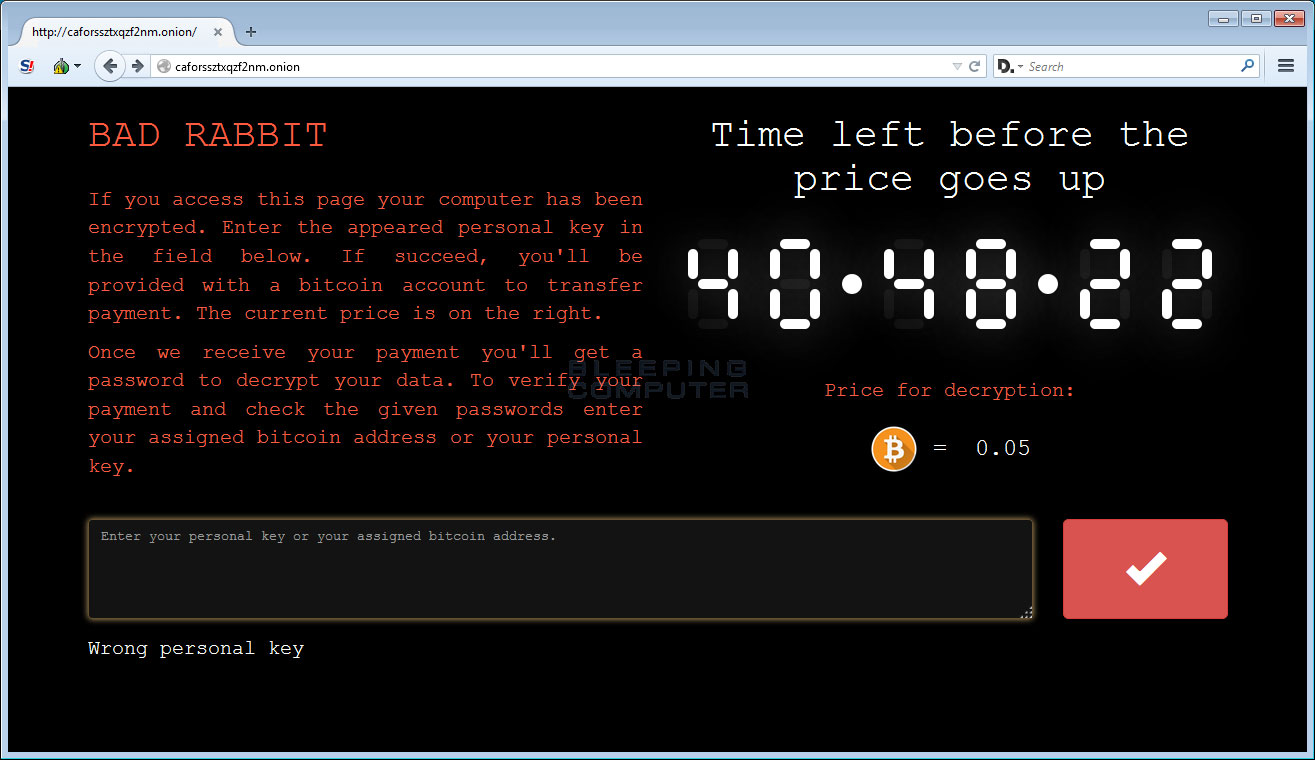
However, at this moment no one can ensure if the ransom payment can really bring back the locked files. The US computer emergency readiness team declared that it “discourages individuals and organisations from paying the ransom, as this does not guarantee that access will be restored”.
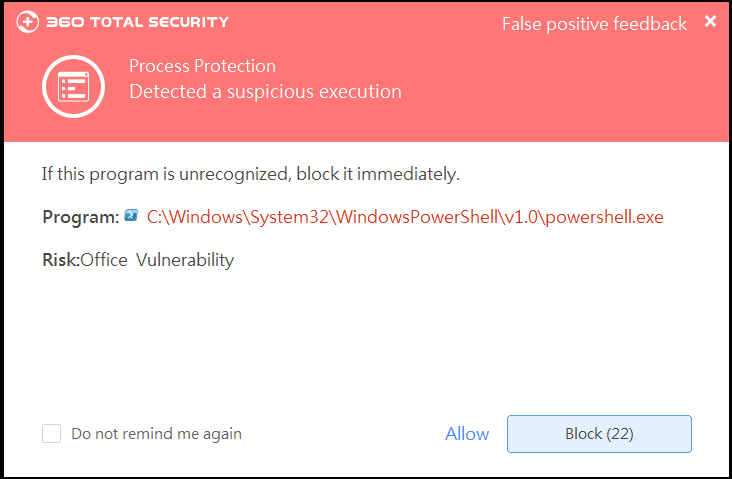
360 has intercepted this attack. Stay protected.
To secure important data from the Bad Rabbit outbreak, users are recommended to take the following action:
1. Update 360 Total Security to the latest version
360’s cloud security engines has already intercepted this malware. Make sure your 360 Total Security antivirus is up-to-date and conduct a Full Virus Scan to prevent your computer against Bad Rabbit, Petya, and other threats coming from the Internet.
2. Back up your critical data
Even if you have installed 360 Total Security, you should still back up your data. This step can save your files from ransomware as well as other computer issues like system crash.
See also: Why you need 360 Document Protector
Since the Bad Rabbit attack is still spreading, taking the precaution is critical. 360 will keep following this attack and offer comprehensive protection for all of our users.
Learn more about 360 Total Security