Since October 2019, 360 Security Center has successively intercepted multiple cyber attacks against foreign trade, transportation, and several important maritime ports. Through a joint analysis of these attack incidents, we find that the hacker team that launched the attack is highly professional and has a powerful arsenal. The targets of the attack are of extremely high value, so we don’t think this is purely personal behavior, But a professional hacker team or APT organization.
When analyzing the organization’s CVE-2017-11882 exploit document, we found that the way to bypass the shellcode length limitation is similar to that used by the APT organization TA505, but the delivered payload is in favor of publicly sold malware such as NanoCore , Formbook, etc., did not find any Tema ever used by TA505. So we are not sure if this attack was initiated by TA505.
However, in order to facilitate the continuous follow-up of the organization, we named the attack “Bayworld”, and we will continue to track and study more attacks related to the organization.
Attack target
We analyzed the machines that infected a series of Trojan horses and found that the main attack targets of BayWorld activities were concentrated in large enterprises with import and export business, covering medical, chemical, construction, and various new manufacturing industries. Major regional transport companies, as well as a number of important maritime ports launched attacks.
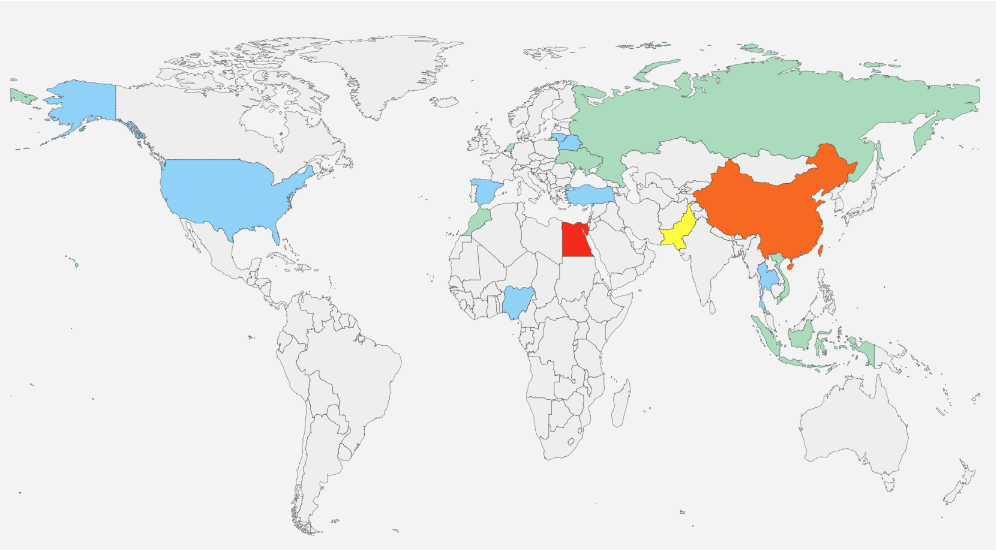
The attack area is mainly distributed in China, Egypt, Ukraine and other countries. The main attack targets are the Suez Canal, Algiers Port, Youzny Sea Port and other important commercial ports. The regional distribution is shown in the following figure:
Decoy document
We analyzed the phishing emails related to Bayworld activities from August 2019. The malicious document attachments carried in the emails are mainly divided into the following three categories:
- Contains macro viruses
- Contains CVE-2017-8570 vulnerability
- Contains CVE-2017-11882 vulnerability
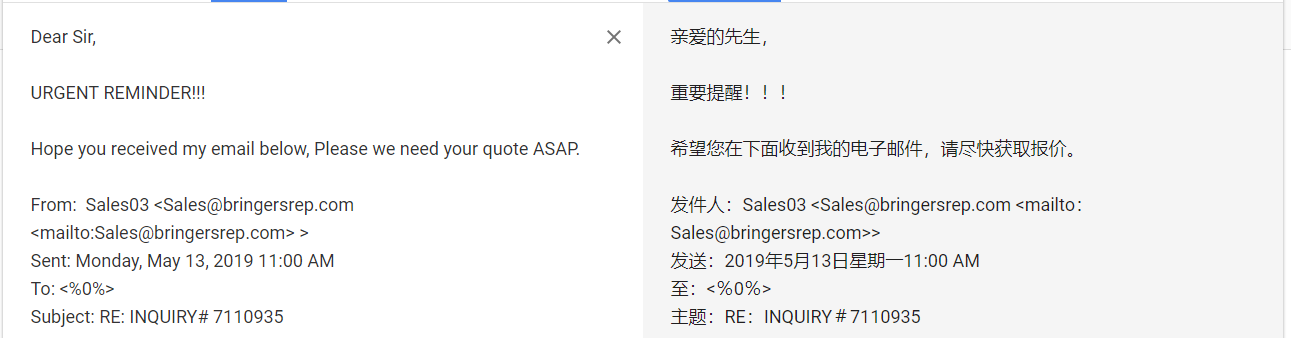
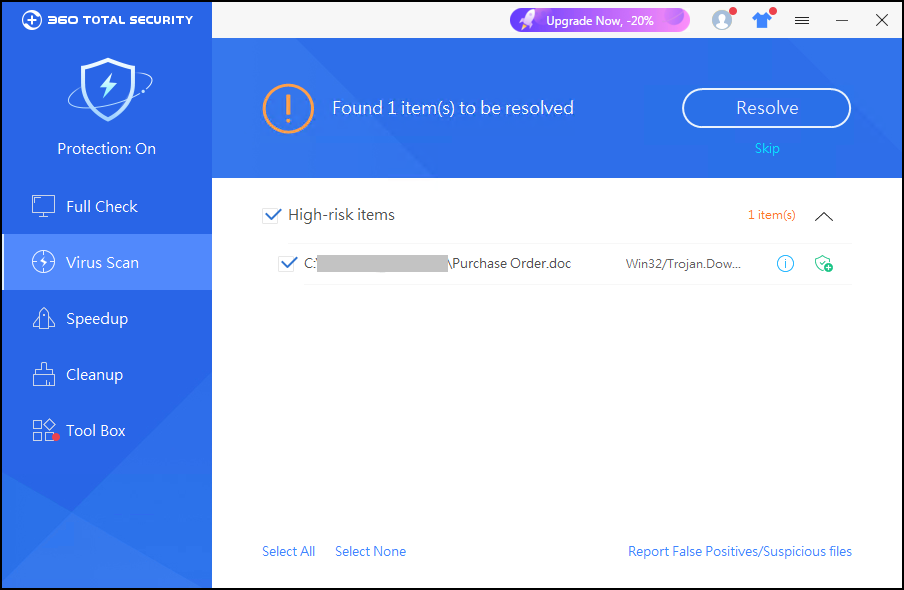
The contents of the phishing emails are relatively simple. After the embarrassment, the victims will be reminded to open the attached file:
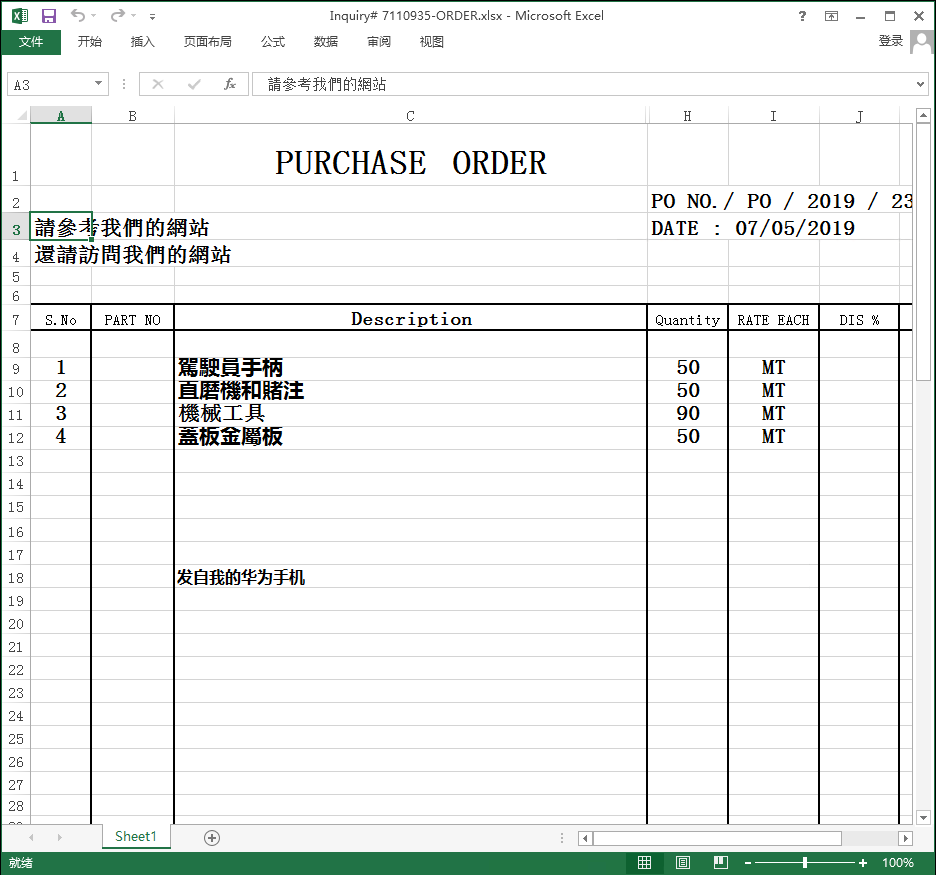
Attachments are usually disguised as purchase orders, payment vouchers, account statements, etc.
CVE-2017-11882
Unlike most previous CVE-2017-11882 exploits, Bayworld uses malicious code in xlsx files. When overflowing, it uses a 30-byte shellcode to dynamically obtain the memory pointer of the MTEFData structure and locate the remaining shellcode. In order to bypass the limit on the length of shellcode when exploiting.
This method is not the first time to appear. We found that a similar use method was mentioned in the analysis report of the TA505 hacker organization by friends and merchants, but based on one point, we are not sure that the Bayworld was initiated by the TA505 hacker organization.
CVE-2017-8570
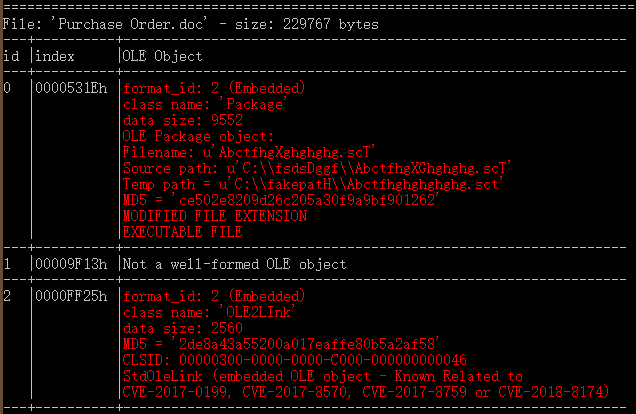
The CVE-2017-8570 exploit document contains two key ole objects. The first is a Package type malicious scriptletfile (SCT) script. After the malicious document is opened, the Package object is automatically released to the% temp% directory.
The second is an OLE2Link object, which is used to trigger the SCT script released to a random directory
The SCT script is used to download subsequent payloads.
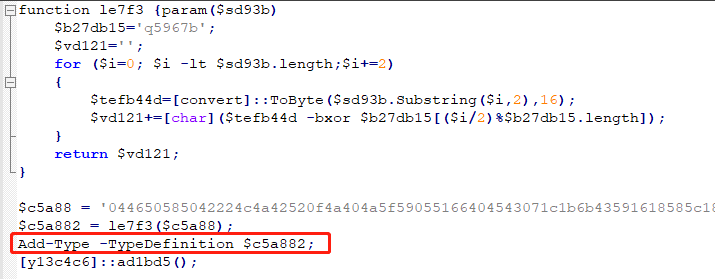
Malicious macro
In addition to exploiting vulnerabilities, a large number of macro viruses have also been used in Bayworld activities. The macro code has been obfuscated. After multiple decryptions, it will call powershell to execute the following script:
Add C # code to the current session via Add-Type and execute:

Then bypass AMSI detection through Patch AmsiScanBuffer, and finally download and execute the payload.
PayLoad
During our analysis of the activities of BayWorld, we found that there are many types of payloads delivered by them, covering the following types of mainstream remote control and spyware.

In addition, I also detected a small amount of malware from families such as Ave_Maria and NjRat. These malware have powerful functions, and hackers can control the victim’s machine and perform any desired operation through this software.
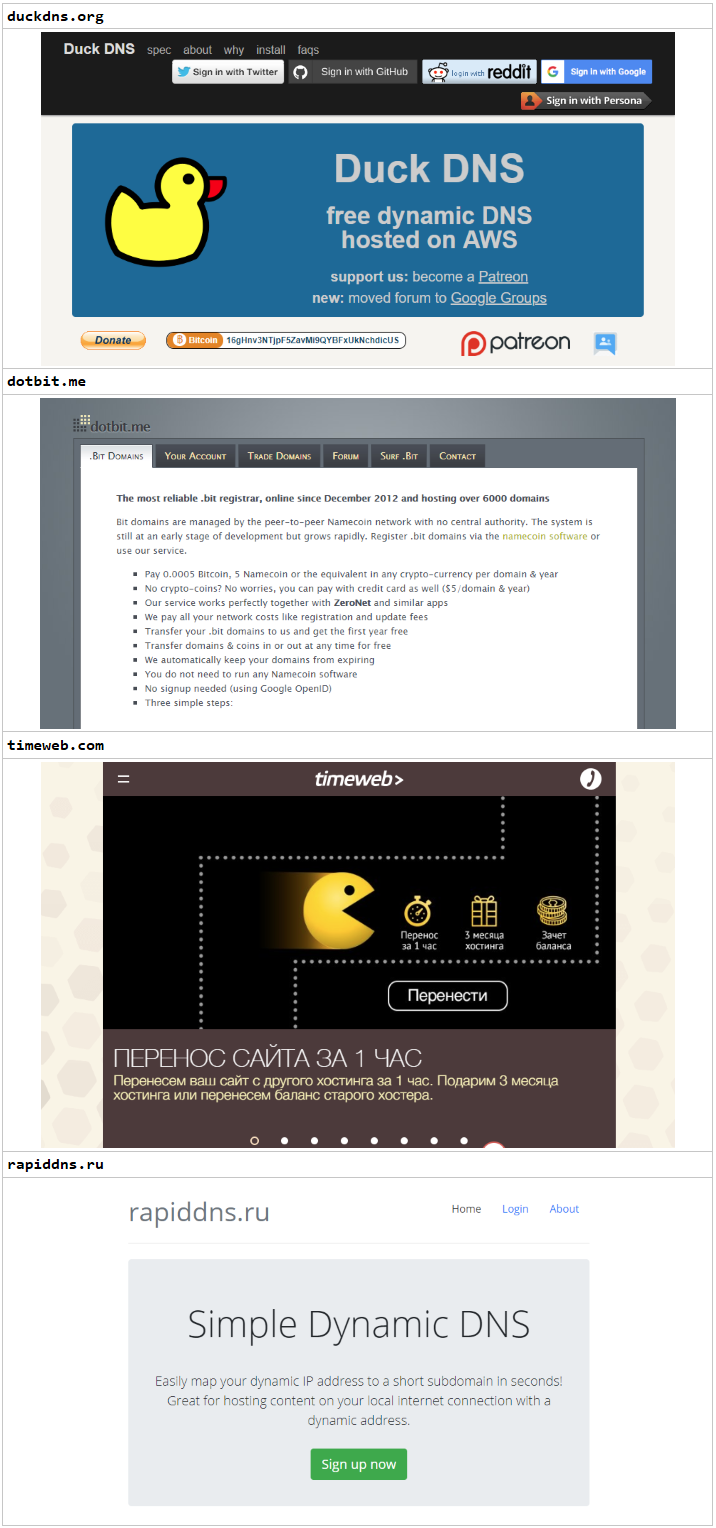
Covert means
In addition to using IP addresses in some URLs, most of them use dynamic domain names to hide real server addresses:
Summary
Bayworld is a well-targeted and highly professional cyber attack campaign. The hacking gang behind it has a powerful arsenal and diverse attack methods. It uses a large number of obfuscated codes and dynamic domain names in the entire attack process. At the same time, its own characteristics are well hidden.
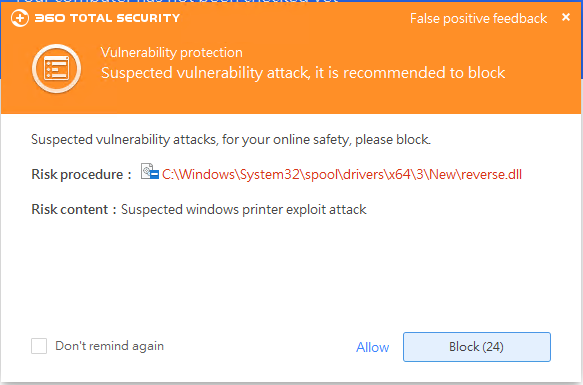
360 Total Security can intercept such cyber attacks in multiple dimensions. Users could install and use it:
Learn more about 360 Total Security