360Netlab noticed a new botnet in September 2018. The number of infections in this botnet is extremely large, and the active IP address in each scan wave is about 100,000. We named the botnet as BCMUPnP_Hunter, mainly considering the characteristics of its infection target. The botnet has the following characteristics:
*The amount of infection is extremely large, and the active scanning IP in each wave is about 100,000.
*The single target of infection is mainly based on BroadCom UPnP router equipment.
*The sample capture is difficult, and it is necessary to simulate multiple device environments in a high-interaction honeypot to successfully capture.
*Self-built proxy network (tcp-proxy), the proxy network is implemented by the attacker, and the bot can be used as a springboard to proxy access to the Internet.
*The proxy network currently mainly accesses well-known mail servers such as Outlook, Hotmail, Yahoo! Mail, etc. We highly suspect that the attacker’s intention is mainly related to sending spam.
Scale assessment
The trend of scanning source IP for port 5431 in the last 30 days is as follows:
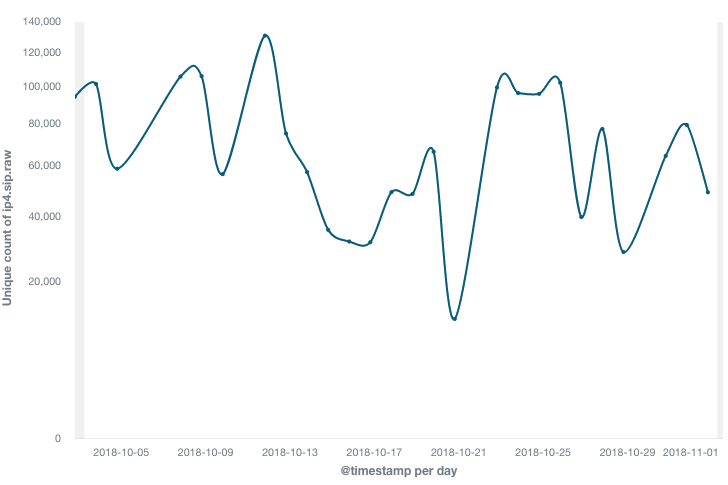
It can be seen that the scan is not continuous, but constitutes a wave every 1-3 days. The active scanning IP in a single wave is about 100,000, and we measure the size of the botnet based on this data.
There are 3.37 million scan source ips accumulated in history. Although this number is huge, it may not mean that there are already so many devices that have been infected, and it may be that the IP of the same infected device has changed over time.
The number of potential infections exceeds 420,000. This is mainly based on the scan source ip return to the web server in the banner: Server: Custom/1.0 UPnP/1.0 Proc/Ver is estimated from the search results of shodan.
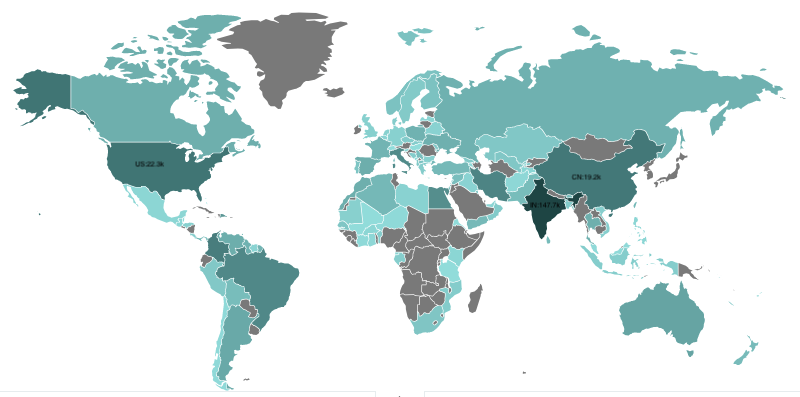
Scanning source IP geographical distribution in the last 7 days:
Infected device information
Through the detection of the attack source, 116 infected device information is obtained, and the actual
infected device type is not limited to this:
ADB Broadband S.p.A, HomeStation ADSL Router
ADB Broadband, ADB ADSL Router
ADBB, ADB ADSL Router
ALSiTEC, Broadcom ADSL Router
ASB, ADSL Router
ASB, ChinaNet EPON Router
ASB, ChinaTelecom E8C(EPON) Gateway
Actiontec, Actiontec GT784WN
Actiontec, Verizon ADSL Router
BEC Technologies Inc., Broadcom ADSL Router
Best IT World India Pvt. Ltd., 150M Wireless-N ADSL2+ Router
Best IT World India Pvt. Ltd., iB-WRA300N
Billion Electric Co., Ltd., ADSL2+ Firewall Router
Billion Electric Co., Ltd., BiPAC 7800NXL
Billion, BiPAC 7700N
Billion, BiPAC 7700N R2
Binatone Telecommunication, Broadcom LAN Router
Broadcom, ADSL Router
Broadcom, ADSL2+ 11n WiFi CPE
Broadcom, Broadcom Router
Broadcom, Broadcom ADSL Router
Broadcom, D-Link DSL-2640B
Broadcom, D-link ADSL Router
Broadcom, DLink ADSL Router
ClearAccess, Broadcom ADSL Router
Comtrend, AR-5383n
Comtrend, Broadcom ADSL Router
Comtrend, Comtrend single-chip ADSL router
D-Link Corporation., D-Link DSL-2640B
D-Link Corporation., D-Link DSL-2641B
D-Link Corporation., D-Link DSL-2740B
D-Link Corporation., D-Link DSL-2750B
D-Link Corporation., D-LinkDSL-2640B
D-Link Corporation., D-LinkDSL-2641B
D-Link Corporation., D-LinkDSL-2741B
D-Link Corporation., DSL-2640B
D-Link, ADSL 4*FE 11n Router
D-Link, D-Link ADSL Router
D-Link, D-Link DSL-2640U
D-Link, D-Link DSL-2730B
D-Link, D-Link DSL-2730U
D-Link, D-Link DSL-2750B
D-Link, D-Link DSL-2750U
D-Link, D-Link DSL-6751
D-Link, D-Link DSL2750U
D-Link, D-Link Router
D-Link, D-link ADSL Router
D-Link, DVA-G3672B-LTT Networks ADSL Router
DARE, Dare router
DLink, D-Link DSL-2730B
DLink, D-Link VDSL Router
DLink, DLink ADSL Router
DQ Technology, Inc., ADSL2+ 11n WiFi CPE
DQ Technology, Inc., Broadcom ADSL Router
DSL, ADSL Router
DareGlobal, D-Link ADSL Router
Digicom S.p.A., ADSL Wireless Modem/Router
Digicom S.p.A., RAW300C-T03
Dlink, D-Link DSL-225
Eltex, Broadcom ADSL Router
FiberHome, Broadcom ADSL Router
GWD, ChinaTelecom E8C(EPON) Gateway
Genew, Broadcom ADSL Router
INTEX, W150D
INTEX, W300D
INTEX, Wireless N 150 ADSL2+ Modem Router
INTEX, Wireless N 300 ADSL2+ Modem Router
ITI Ltd., ITI Ltd.ADSL2Plus Modem/Router
Inteno, Broadcom ADSL Router
Intercross, Broadcom ADSL Router
IskraTEL, Broadcom ADSL Router
Kasda, Broadcom ADSL Router
Link-One, Modem Roteador Wireless N ADSL2+ 150 Mbps
Linksys, Cisco X1000
Linksys, Cisco X3500
NB, DSL-2740B
NetComm Wireless Limited, NetComm ADSL2+ Wireless Router
NetComm, NetComm ADSL2+ Wireless Router
NetComm, NetComm WiFi Data and VoIP Gateway
OPTICOM, DSLink 279
Opticom, DSLink 485
Orcon, Genius
QTECH, QTECH
Raisecom, Broadcom ADSL Router
Ramptel, 300Mbps ADSL Wireless-N Router
Router, ADSL2+ Router
SCTY, TYKH PON Router
Star-Net, Broadcom ADSL Router
Starbridge Networks, Broadcom ADSL Router
TP-LINK Technologies Co., Ltd, 300Mbps Wireless N ADSL2+ Modem Router
TP-LINK Technologies Co., Ltd, 300Mbps Wireless N USB ADSL2+ Modem Router
TP-LINK, TP-LINK Wireless ADSL2+ Modem Router
TP-LINK, TP-LINK Wireless ADSL2+ Router
Technicolor, CenturyLink TR-064 v4.0
Tenda, Tenda ADSL2+ WIFI MODEM
Tenda, Tenda ADSL2+ WIFI Router
Tenda, Tenda Gateway
Tenda/Imex, ADSL2+ WIFI-MODEM WITH 3G/4G USB PORT
Tenda/Imex, ADSL2+ WIFI-MODEM WITH EVO SUPPORT
UTStarcom Inc., UTStarcom ADSL2+ Modem Router
UTStarcom Inc., UTStarcom ADSL2+ Modem/Wireless Router
UniqueNet Solutions, WLAN N300 ADSL2+ Modem Router
ZTE, Broadcom ADSL Router
ZTE, ONU Router
ZYXEL, ZyXEL VDSL Router
Zhone, Broadcom ADSL Router
Zhone, Zhone Wireless Gateway
Zoom, Zoom Adsl Modem/Router
ZyXEL, CenturyLink UPnP v1.0
ZyXEL, P-660HN-51
ZyXEL, ZyXEL xDSL Router
huaqin, HGU210 v3 Router
iBall Baton, iBall Baton 150M Wireless-N ADSL2+ Router
iiNet Limited, BudiiLite
iiNet, BoB2
iiNet, BoBLite
Transmission process and capture
For each randomly generated target IP, the Bot will first detect the openness of its TCP 5431 port. If it is opened, the vulnerability is further exploited through a potentially infectable url (access to the UDP-1900 port for this url). The IP that passes the probe check will be reported to Loader (109.248.9.17:4369), and the subsequent exploits and malicious samples will be completed by Loader.
A brief timing diagram of the attack process is as follows:
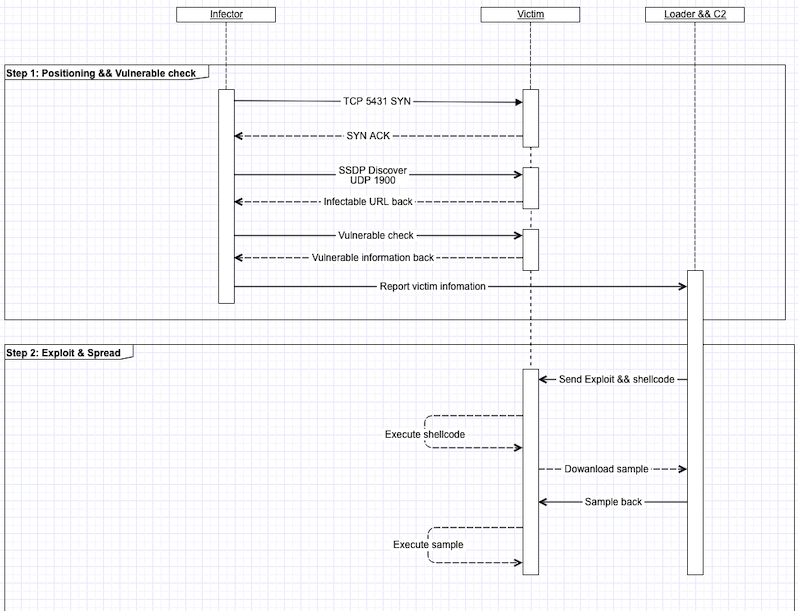
In addition to the necessary interactions described above, the exploit itself requires a multi-step interaction to be successful.
But for developers of high-interaction honeypots, every interaction is a test. Only the correct answer to each request can successfully trick the deliverer to deliver the final sample. To this end, we have modified a variety of honeypots to fully simulate infected devices, deceive the deliverers, and finally complete the analysis of the botnet.
Sample Analysis
The sample of the botnet consists of two parts, the shellcode and the bot body, which are described below.
Shellcode
The main function of shellcode is to download the main sample from c2 (109.248.9.17:8738) and execute it.
The shellcode is 432 bytes long and is a neat specification that cannot be retrieved from common search engines. At the same time, the following points are perfectly realized.
* Basic capabilities: The code has multiple syscall calls for networks, processes, files, etc.
* Code details: Using syscall 0x40404 (instead of syscall 0) and multiple inversion operations, avoiding bad characters (\x00); stack variables in the code are also reused to varying degrees to optimize the runtime stack structure.
* Code logic: By using looping rules, a variety of failed calls are reasonably circumvented, ensuring the effectiveness of shellcode execution.
Sample subject
The sample body features include Broadcom UPnP vulnerability detection and proxy access network capabilities, which can parse four instruction codes from C2:
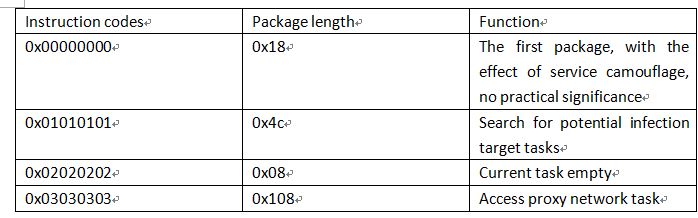
0x01010101 is to enable the port scan task command code, once the BOT end scans the potential infection target, the target IP packet will be reported to the Loader, and then the Loader will complete the subsequent infection process.
0x03030303 is the proxy service instruction code. The BOT side accesses the address provided in the instruction and reports the access result to the host.
Among these instructions, 0x03030303 can generate real economic benefits, and an attacker can use this command to build a proxy network, and then profit from sending spam, simulating clicks, and so on. Other instructions can only be used to infect and expand the size of the botnet without real economic benefits.
Proxy network and spam
In order to clarify the attacker’s attack intention, we continue to track the 0x03030303 command issued by the attacker through a series of technical means.
In the instructions we have obtained, BCMUPnP_Hunter is used to proxy traffic to the following servers:
104.47.0.33:25
104.47.12.33:25
104.47.124.33:25
104.47.14.33:25
104.47.33.33:25
104.47.48.33:25
104.47.50.33:25
106.10.248.84:25
144.160.159.21:25
188.125.73.87:25
67.195.229.59:25
74.6.137.63:25
74.6.137.64:25
98.137.159.28:25
Our basic data provides a more detailed of explanation these servers:
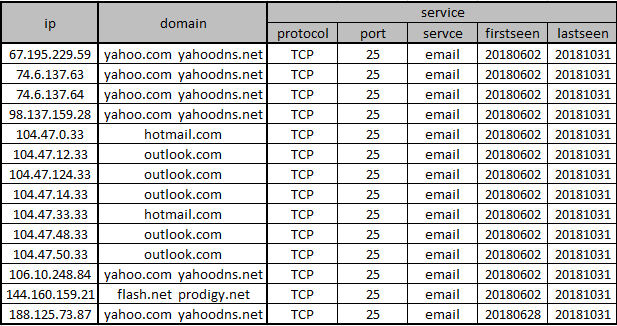
These servers are well-known mail service providers, including Outlook, Hotmail, Yahoo! Mail. For several months, these servers have provided and only provided TCP25 services. In this case, it is basically considered that the attacker is abusing the email service of these servers.
This makes us highly sceptical that the attacker is using the proxy network established by BCMUPnP_Hunter to send spam.