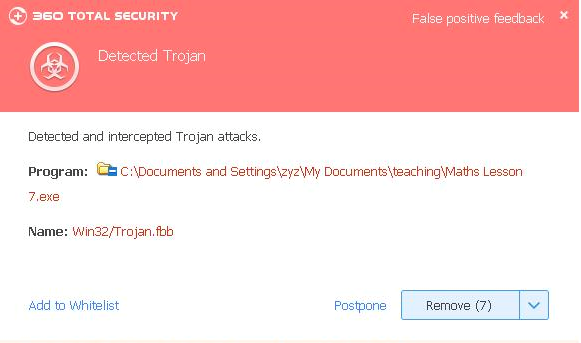
Recently, 360 Security Center discovered a type of actively spreading Trojan “BrowserHijackerDriver” that infected a hundred thousand of computers in two days. The Trojan disguises itself as utility softwares and media players. It is highly recommended to download softwares from the official websites instead of unknown sources.
Analysis
While user downloads and installs the disguised media player, the Trojan file is released. The path of the Trojan is:
%userprofile%\appdata\local\temp\8617386\ic-0.b2cbe292914f58.exe
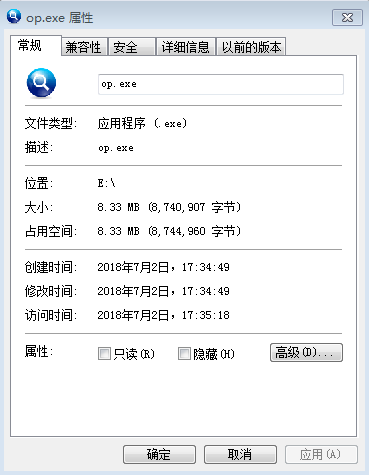
The file information is:
The Trojan will run REG first to avoid the uploading of the malicious software report.
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT /v DontReportInfectionInformation /t REG_DWORD /d 1 /f
reg add HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MRT /v DontOfferThroughWUAU /t REG_DWORD /d 1 /f
And then write a service file.
C:\Program Files\Y2YyOTU5ZTMwZmViZ\MjBkZWY.exe
Run SC command to create the service:
create OTU5YTkwNjAzMz binPath= “rundll32.exe C:\Windows\ditwabiaqskrksxp.ditha IGfZlJ” start= auto
The Trojan file releases a driver to the driver folder \windows\system32\drivers\YWQ3OWIyMjFjNzh.sys and uses system command to create a driver system group PNP_TDI.
create YWQ3OWIyMjFjNzh binpath= system32\drivers\YWQ3OWIyMjFjNzh.sys DisplayName= YWQ3OWIyMjFjNzh type= kernel start= system group= PNP_TDI
The driver information is:
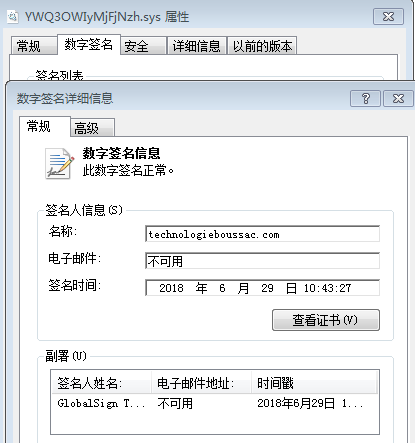
The driver is modified from an open source code and contains a signature technologieboussac.com. It interacts with Internet devices by creating a variety of device names.
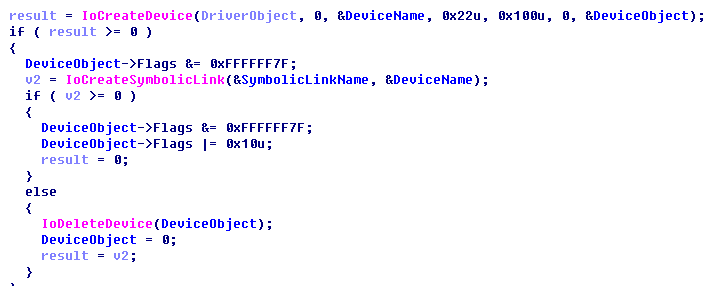
The device names are:
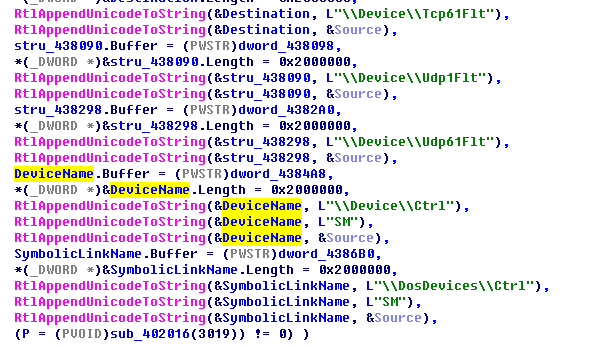
The Trojan uploads the driver to the Internet devices and modifies the Internet packages.
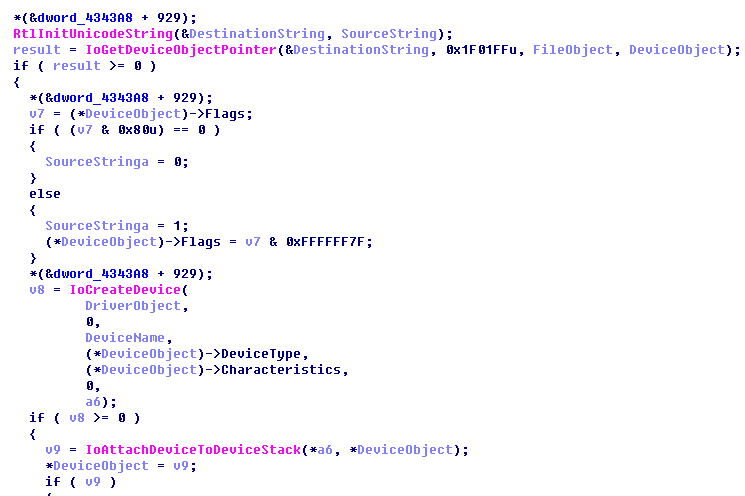
It pops up advertisements while user browsing the Internet.
Reminder
Recently, we have found that a lot of Trojans are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to Trojans.
Learn more about 360 Total Security