Recently, Microsoft released a new security patch officially, for the complete repair of CVE-2018-8581, CVE-2019-0686, CVE-2019-0724, and exclusive thanks to 360 A-TEAM in its official documentation.
This article updates the Microsoft Exchange SSRF Vulnerability (CVE-2018-8581) and also the full fix solution for CVE-2019-0686, CVE-2019-0724.
Microsoft’s Exchange was previously experiencing an SSRF vulnerability with the vulnerability number: CVE-2018-8581. This CVE can cause the following two attack scenarios:
Attack scenario 1: The attacker exploits this vulnerability to take over the inbox of anyone in the network with the authority of a mailbox on the target network, causing serious information leakage.
Attack scenario 2: An attacker can use this vulnerability to directly control a Windows domain within the target network to control all Windows machines in the domain.
Microsoft officially released mitigation measures to try to fix “attack plan one” several months ago . But 360 A-TEAM found that there was a problem with the mitigation measures (the problem was subsequently assigned a new vulnerability number CVE-2019-0686) after evaluation, and submitted The problem to Microsoft’s official SRC along with “Attack 2” (this attack was subsequently assigned vulnerability number CVE-2019-0724). Recently, Microsoft officially released a new security patch for the complete repair of CVE-2018-8581, CVE-2019-0686, CVE-2019-0724, and exclusive thanks to 360 A-TEAM in its official documentation.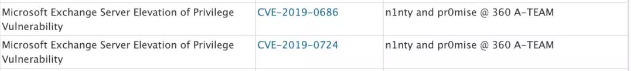
Document information
Vulnerability description
Microsoft’s Exchange was previously experiencing an SSRF vulnerability with the vulnerability number: CVE-2018-8581. Recently, another method of exploiting this vulnerability has been disclosed by foreign security researchers. This vulnerability can be used by an attacker to directly control the Windows domain in the target network and directly control all Windows machines in the domain.
An attacker can attempt to trigger this vulnerability after it has entered the target network and satisfies any of the following conditions:
- With the mailbox permissions of any user in the target network
- The attacker has controlled any machine in the target network that is on the same network segment as the intranet machine, and successfully initiated a windows name resolution spoofing attack on the intranet machine.
If the exploit is successful, the Windows domain within the target network can be controlled, causing all Windows machines in the domain to be controlled.
Currrently Microsoft has officially released an update patch for repairing CVE-2018-8581, CVE-2019-0686, CVE-2019-0724.
Risk level
360 Safety Monitoring and Response Center Risk Rating: High Risk
Warning level: blue warning (general network security warning)
Scope of influence
Microsoft Exchange Server 2010
Microsoft Exchange Server 2013
Microsoft Exchange Server 2016
Microsoft Exchange Server 2019
Note: The Exchange permissions model is divided into the SplitPermission Model and the Shared Permission Model (default), and the Exchange server with the Split Permission Model is not affected by Attack 2.
Disposal advice
Currently Microsoft has officially released an update patch for repairing CVE-2018-8581, CVE-2019-0686, CVE-2019-0724. Please refer to the following official link for repair:
https://portal.msrc.microsoft.com/en-us/security-guidance/advisory/CVE-2019-0686
Reference link
https://portal.msrc.microsoft.com/zh-cn/security-guidance/advisory/CVE-2019-0724
https://portal.msrc.microsoft.com/zh-cn/security-guidance/advisory/CVE-2019-0686
Timeline
[1] 2018-12-31 360 Security Monitoring Response Center issued a security alert notice
[2] 2019-1-22 360 Security Monitoring Response Center released the second update of the Security Alert Notice
[3] 2019-1-22 360 Security Monitoring Response Center released the third update of the Security Alert Notice
[4] 2019-1-24 360 Security Monitoring Response Center released the fourth update of the Security Alert Notice
[5] 2019-2-13 360 Security Monitoring Response Center released the fifth update of the Security Alert Notice
Learn more about 360 Total Security