Recently, 360 Security Center has observed a CryptoMiner spreading actively. This malware exploits Microsoft application, srvany.exe, to avoid detection by antivirus. It also carries NSA cyber weapons to power itself up, making users’ computers extremely vulnerable to this malware attack. Our researcher has named it “NSASrvanyMiner”.

According to our analysis, this malware was written in E language. It spawns two malicious files after successfully infecting victims’ computers. The first file, muma.exe, is a remote access tool which allows attackers to control victims’ computers. The second file, rasm.exe, is in charge of the mining and infection process.
When running, muma.exe downloads its core module in the form of an encrypted DLL which will be decrypted and executed in memory. After in-depth analysis, it’s discovered to be a variant of a famous RAT(Remote Access Tool), Wolf. It not only allows intruders to remotely control victims’ computers, it also makes itself antivirus-aware to fly under the radar.
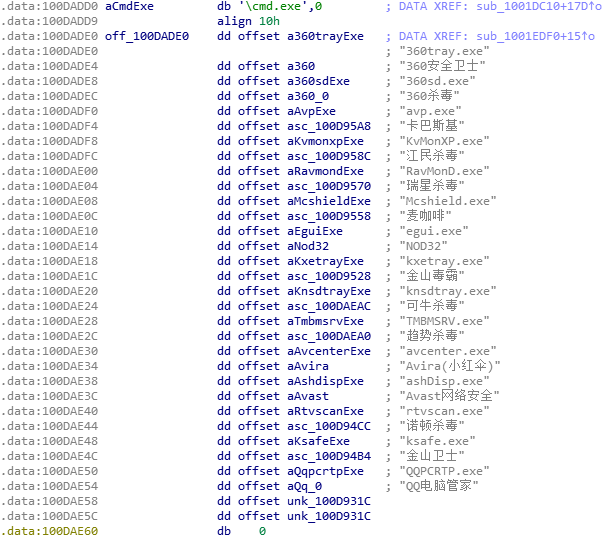
Figure 1. Functions of remote control and antivirus identification.
Srvany.exe is a Microsoft tool that can help run any executable as a Microsoft system service at boot up. It was abused by the second malicious file, rasm.exe, to start its mining application “CPUInfo.exe” at boot up. It also drops vulnerability scanners and other exploit kits to infect other machines.
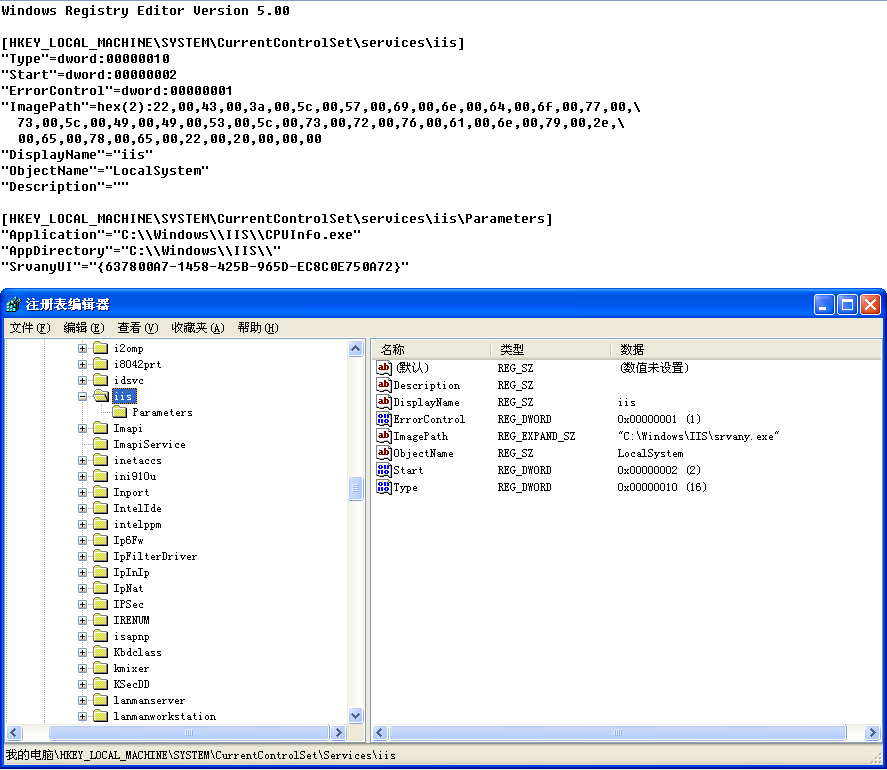
Figure 2. Abuse srvany.exe to start itself at boot up.
Mining application “CPUInfo.exe” drops and runs csrs.exe(renamed from famous open source mining tool, xmrig.exe) to begin mining. The relevant mining parameters(mining pool and wallet address) are as below:
-o stratum+tcp://minero.posthash.org:8080
-o stratum+tcp://note.posthash.org:443
-o stratum+tcp://note1.posthash.org:5555
-u 43BEKp4t8km3wEBasxmPMcV5n5XPPjRN4VcicaSwKZkTHxKzc4hTYwd3tyqR8SLZahfuSsTeJEG3fcEMnX3jA1F86iao1GU
-p x
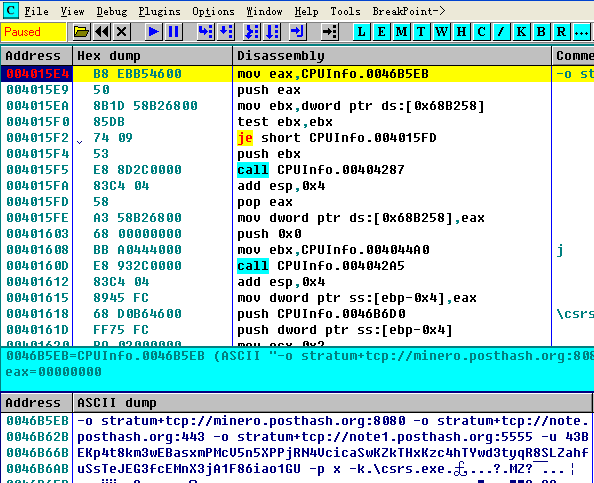
Figure 3. CPUInfo.exe for mining
Reminder
Recently, we have found a lot of CryptoMiner malware actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner and other malware.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security