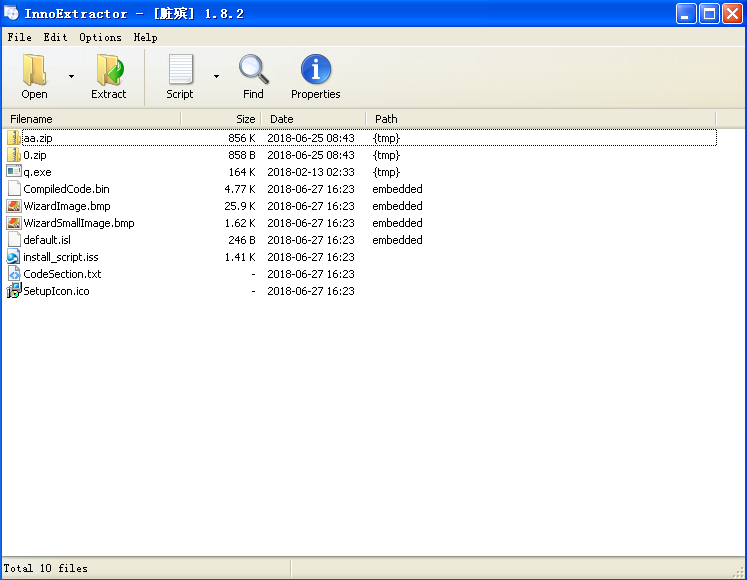
Recently, 360 Security Center discovered a type of actively spreading CryptoMiner Trojan that infected 30 thousands of computers in one day. The Trojan is installed with software cracks and plugins. It is highly recommended to download softwares from the official websites instead of unknown sources. We named it “WinstarNssmMiner3” as it has similar behavior with “WinstarNssmMiner”.
Analysis
The new Trojan is built with Inno format instead of MSI, and disguises itself by changing its name from unzip.exe to q.exe.
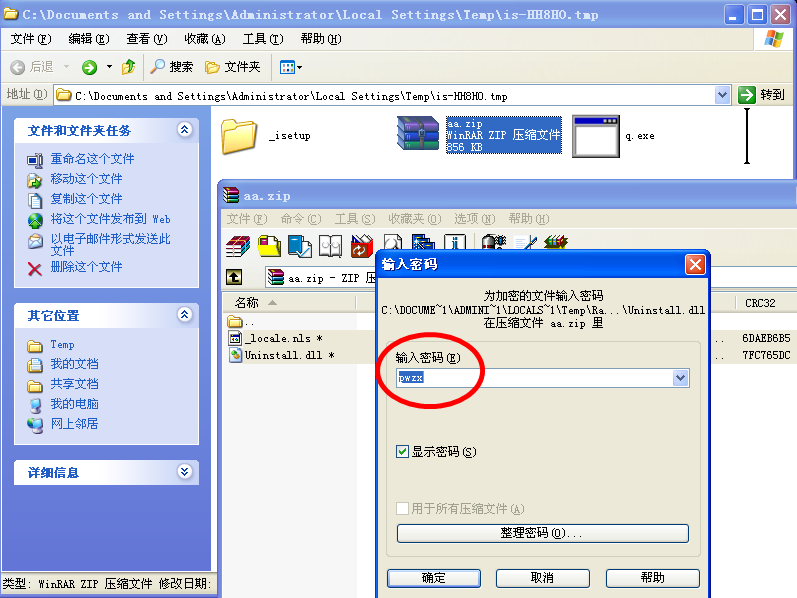
The installer runs command q.exe -o -P pwzx aa.zip to extract the Trojan.
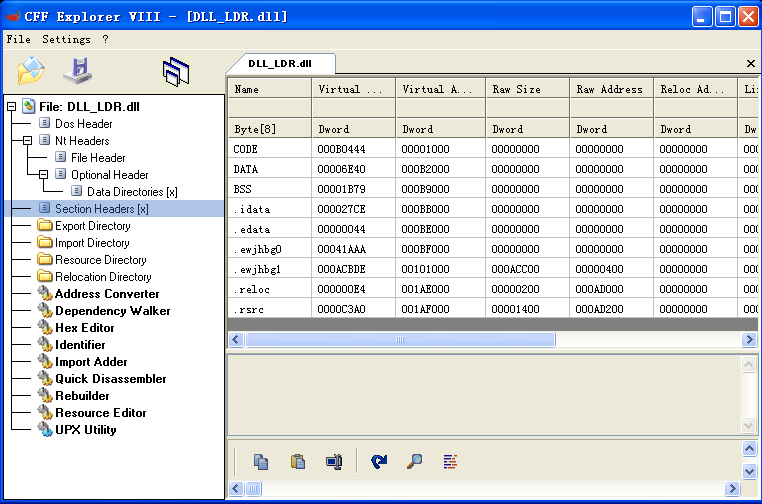
The extracted file Uninstall.dll is the loader of the Trojan, and _locale.nls is the encrypted core script. The loader decrypts and runs the core script in the memory.
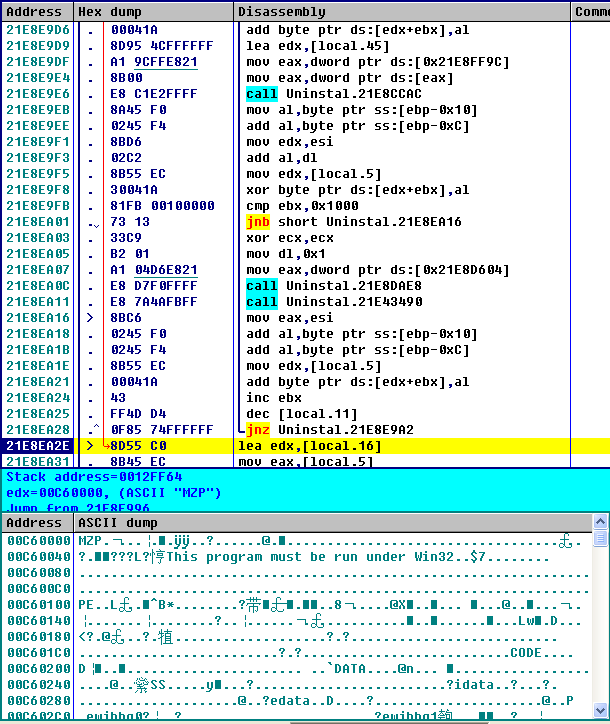
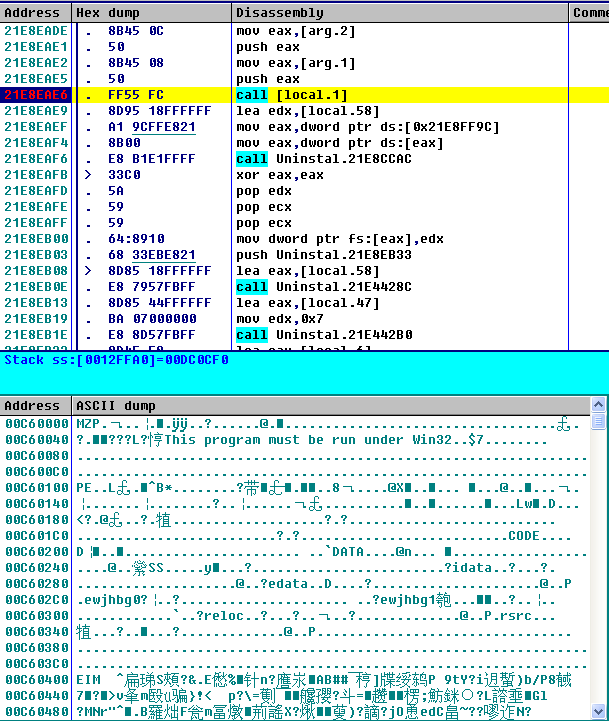
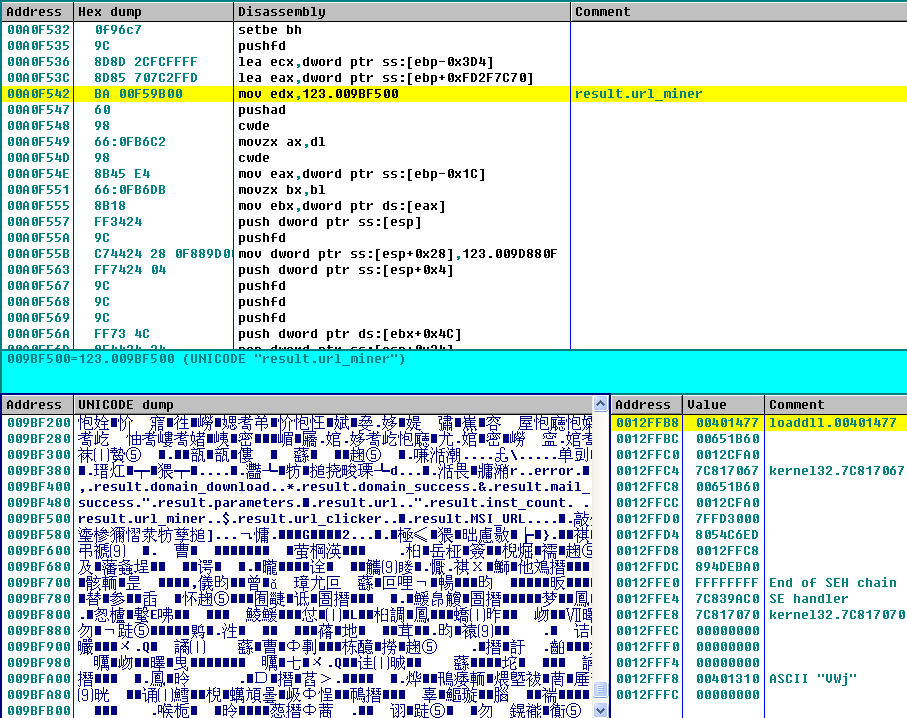
Decrypt the core PE file form _locale.ns in the memory and load it.
The decrypted Trojan mines in the memory. This variant Trojan also implement VMP to protect its code.
The Trojan creates scheduled task for keeping activated on victims’ computer, just like the previous version.
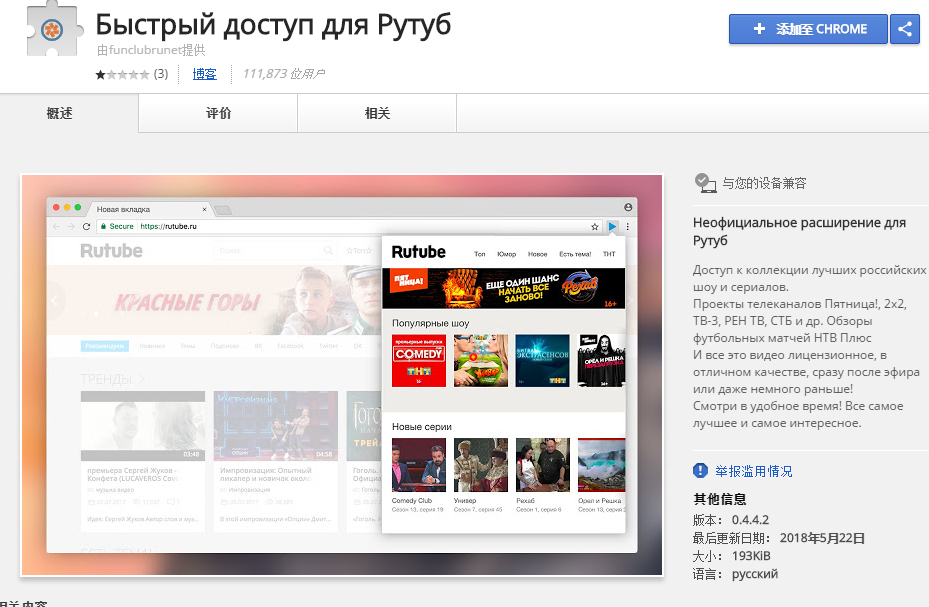
Further, it creates a malicious Chrome plugin.
The information of the plugin:
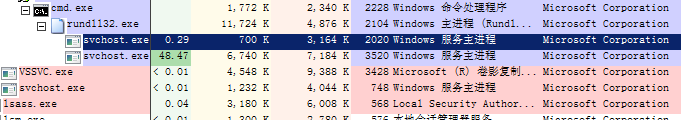
It injects the process svchost.exe for mining and uses up the CPU resource.
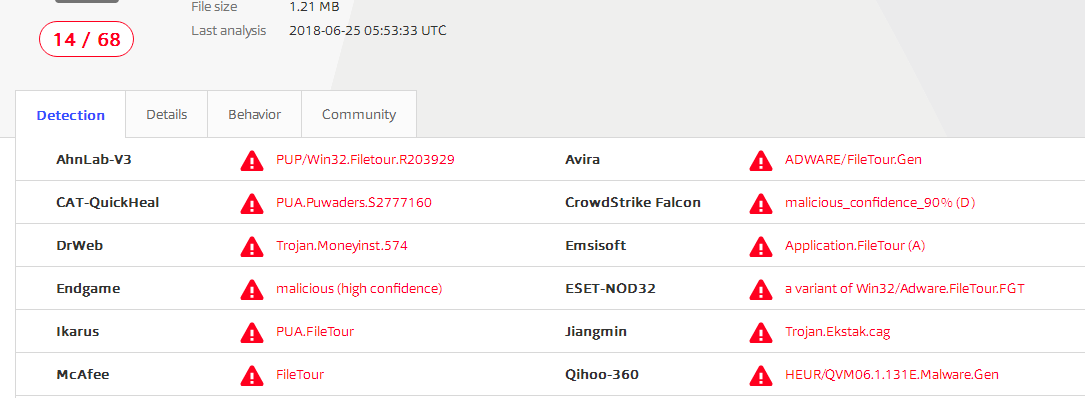
The detections on VirusTotal:
Reminder
Recently, we have found that a lot of CryptoMiner Trojans are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Learn more about 360 Total Security