Kodi recently closed the third-party plug-in library XvBMC for copyright infringement warnings. After the plug-in library was closed, ESET found that it may have become part of the malicious mining activity from December 2017. This is the second public case of large-scale dissemination of malware through the Kodi add-on, and the first public mining activity initiated through the Kodi platform. This activity pushed Linux or Windows specific binaries to Kodi users on these operating systems.
For those who are unfamiliar with the Kodi platform, the popular media player software itself does not provide any content, but users can extend the functionality of the software by installing various plugins that can be found in the official Kodi repository and numerous three-party repository. Some third-party plug-ins allow users to access pirated content, sparking public controversy about Kodi.
Recently, copyright infringement add-ons have also been accused of exposing users to malware, but in addition to the addition of the DDoS module to a popular third-party Kodi add-on, there has been no evidence of malware being transmitted through the Kodi add-on.
According to the research, the malware discovered by ESET in the XvMBC repository was first added to the popular third-party add-on repository Bubbles and Gaia (a branch of Bubbles) in December 2017 and January 2018, respectively. Through these two sources, as well as update routines by unsuspecting users built by other third-party plug-in libraries and off-the-shelf Kodi, malware is further spread in the Kodi system.
The malware has a multi-level structure and measures to ensure that its final payload (cryptominer) cannot be easily traced back to malicious add-ons. Cryptominer runs on Windows and Linux and mines the cryptocurrency monroe. ESET does not currently see versions for Android or macOS devices.
The victim of the event eventually runs the malware in one of three ways:
1. The user adds the URL of the malicious repository to their Kodi installation to download some add-ons. Then, as soon as they update the Kodi add-on, malicious add-ons are installed.
2. The user installed the off-the-shelf version of Kodi, which contains the URL of the malicious repository. As long as they update the Kodi add-on, they will install a malicious load project.
3. The user installed a ready-made Kodi version that contained a malicious plugin but did not link to the repository for updates. Although an initial attack was initiated, no further update requests for malicious add-ons were received. However, if cryptominer is installed, it will keep and receive updates.
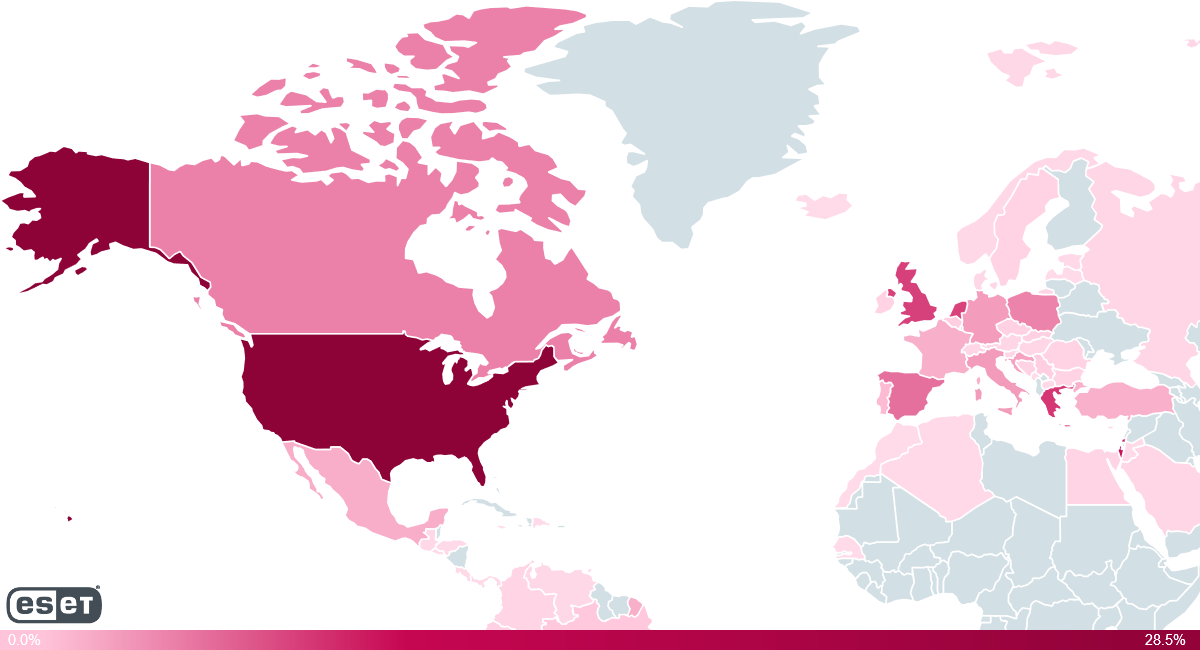
According to ESET’s telemetry data, the five countries most affected by this threat are the United States, Israel, Greece, the United Kingdom, and the Netherlands. Other possible explanations for geographic distribution are Kodi versions of specific countries, which contain malicious repositories or malicious repositories with user bases in the relevant countries.
When an ESET researcher writes an essay, the repository that the malware initially started to propagate either has either expired (bubble) or is no longer serving malicious code (Gaia). However, an unsuspecting victim who has cryptominer installed on his/her device may still be affected. Most importantly, malware still exists in other repositories and some off-the-shelf Kodi architectures, and developers of repositories and architectures are equally likely to be unaware of it.

According to ESET’s analysis, many devices are still mining Monero for criminals, and at least 4,774 victims are affected by malware. If you are using Kodi on a Windows or Linux device and have installed add-ons from a third-party repository or an off-the-shelf Kodi build, you may have been affected by this encryption activity. To check if your device has been compromised, please use a reliable anti-virus software solution to scan.
Learn more about 360 Total Security