On December 9, 360 Security Center monitored that Apache officially released the log4j-2.15.0-rc1 version on December 7, 2021. According to the research and judgment of 360 Group’s security experts, this version has bypass risks and security risks. The manufacturer has released the latest version log4j-2.15.0-rc2, please update as soon as possible.
After the logging function is turned on, the component can be successfully exploited by inserting the exploit code wherever the error log can be triggered. If the log recorded by this component contains the log of other systems, it may cause indirect infection. Through the intermediate system, the component indirectly reads the offensive exploit code, which can also indirectly cause the vulnerability to be triggered.
According to 360 vulnerability cloud security experts, log4j2 is a widely used java logging framework around the world. At the same time, the vulnerability also affects many common open source components that are used globally, such as Apache Struts2, Apache Solr, Apache Druid, and Apache Flink. The exploit method of this vulnerability is simple and the damage is serious. The latest version of the product has been officially released. It is recommended that users upgrade the components as soon as possible to fix and mitigate the vulnerability.
Vulnerability impact analysis
Through Google search engine to analyze the products and other open source components that depend on this component, it is found that 310 products and open source components depend on the version of Apache Log4j2 2.14.1.
According to the network space surveying system Quake, the deployment volume of products written in Java language on the entire network is shown in the following figure:
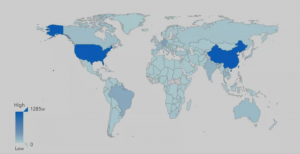
It can be seen from the statistics table of the world’s top 5 in terms of usage that the first place in the usage of Java development language is the United States, and the second is China, and the usage of China and the United States is almost the same.
Because the vulnerable component is a basic component of Java products, the vulnerability affects the entire industry. All companies that use Java as a development language to develop products or companies that use Java language to develop products need to self-check their own security risks.
Repairs and Suggestions
Upgrade to the latest version as soon as possible by referring to the official website address in the link: https://github.com/apache/logging-log4j2/releases/tag/log4j-2.15.0-rc2
Configure the network firewall to prohibit the system from actively connecting to the network, including but not limited to DNS, TCP/IP, and ICMP.
Upgrade the applications and components that are known to be affected, such as srping-boot-strater-log4j2, ApacheSolr, Apache Flink, Apache Druid.
Check the log centralized management server, as well as commercial software developed based on java, and other basic environments that may have hidden dangers.
Emergency reinforcement and mitigation measures:
①Set parameters:
log4j2.formatMsgNoLookups=True
② Modify JVM parameters:
-Dlog4j2.formatMsgNoLookups=true
③System environment variables:
FORMAT_MESSAGES_PATTERN_DISABLE_LOOKUPS is set to true
④Prohibit external connection to the server where log4j2 is located
Learn more about 360 Total Security