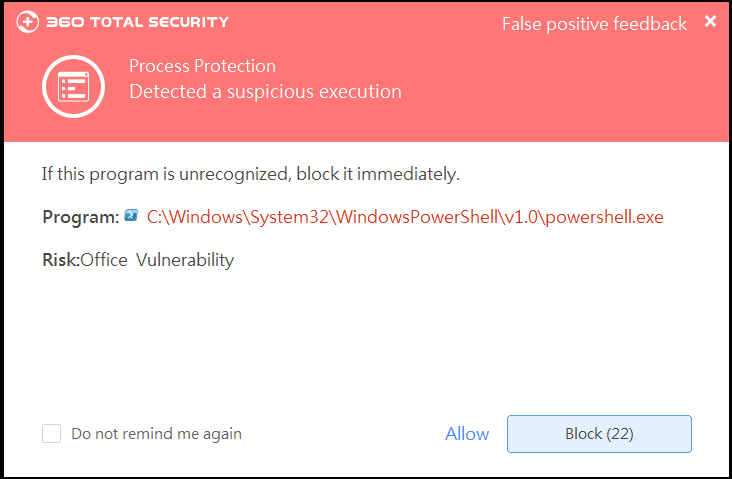
Microsoft just released a security update for a highly dangerous vulnerability (CVE-2018-0802) that were found by 360 Security Team. This vulnerability allows attackers to execute code remotely and cause memory corruption.

According to 360 Security Team, attackers lure victims into opening the infected Office file via phishing emails or online shared files. Once users open the file, attackers can gain control of their PC remotely.
Microsoft has released a security patch to this vulnerability for users who are using Office2017 sp3 and the later versions. Users can also use 360 Total Security’s Patch Up to install this security update to stay protected.
When it comes to “infected files”, most people would think of executable programs like .exe or .scr files. In fact, one of malicious actors’ favorites is Microsoft Office file, such as Word, Excel or PowerPoint, which can be compromised throughout an Office 0day vulnerability. Compared with other types of vulnerabilities, Office 0day vulnerabilities are easier to attack business users and thus to steal sensitive information.
Also, when an Office vulnerability is revealed, hackers may also use it to launch a new ransomware attack before a security update is patched. Security researchers has reported a trend of using Office vulnerabilities to spread ransomware, following the notorious WannaCry and Petya ransomware attacks last year. To stay protected against oncoming cyber threats, users are recommended to install 360 Total Security and use its Patch up feature to keep their Microsoft and Adobe programs up-to-date.
Learn more about 360 Total Security