Recently, 360 Security Center discovered a new type of actively spreading CryptoMiner, ClipboardWalletHijacker. The Trojan monitors clipboard activity to detect if it contains the account address of Bitcoin and Ethereum. It tampers with the receiving address to its own address to redirect the cryptocurrency to its own wallet. This kind of Trojans has been detected on more than 300 thousand computers within a week.
Analysis
The main function of ClipboardWalletHijacker is a recurrent loop monitoring the content of clipboard.
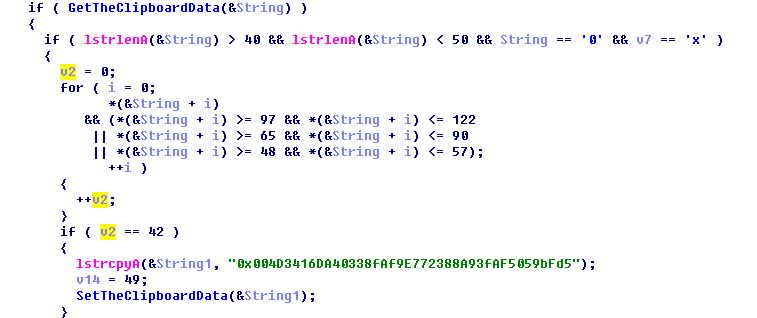
The function of the clipboard fetcher:
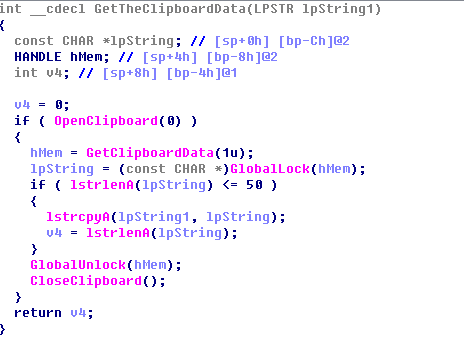
If it detects the content is the address of Ethereum wallet, it replace the address with its own:
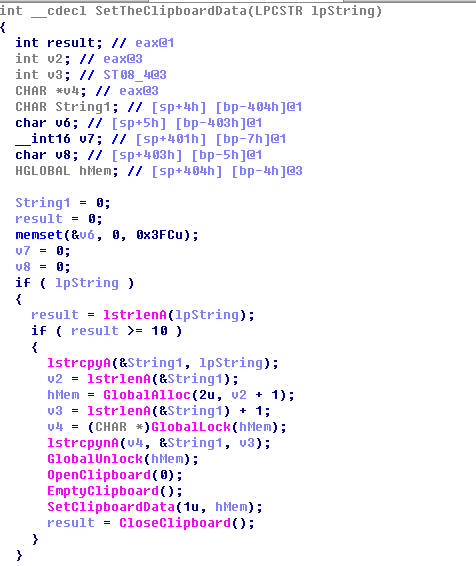
The replacement address is “0x004D3416DA40338fAf9E772388A93fAF5059bFd5”. There have been 46 successful transactions in total.
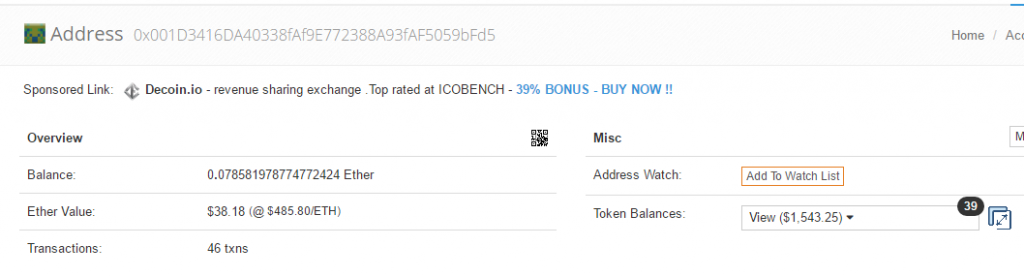
The most recent transactions are:
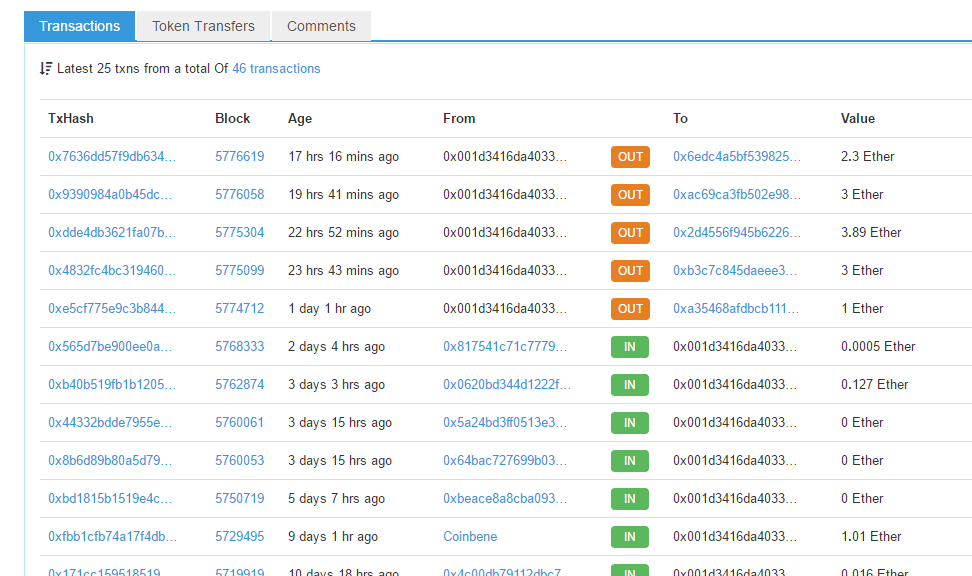
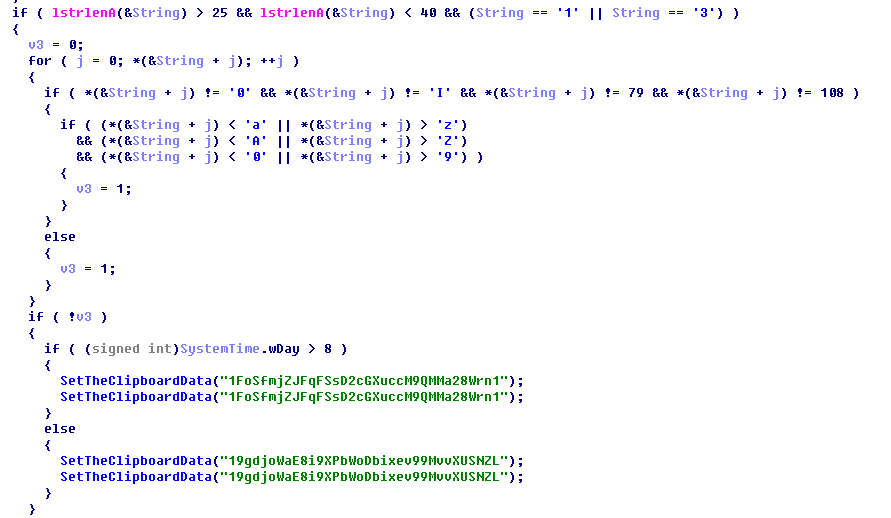
If the address is not Ethereum, the Trojan checks if it is Bitcoin address, and the address number begins with 1 or 3.
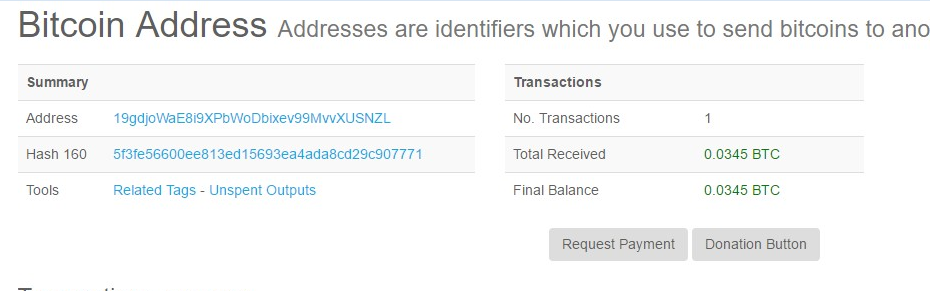
If the current date is earlier than 8th of the month, replace the address to “19gdjoWaE8i9XPbWoDbixev99MvvXUSNZL”. Otherwise, use “1FoSfmjZJFqFSsD2cGXuccM9QMMa28Wrn1” instead.
The Trojan has successfully hijacked five Bitcoin transaction already.
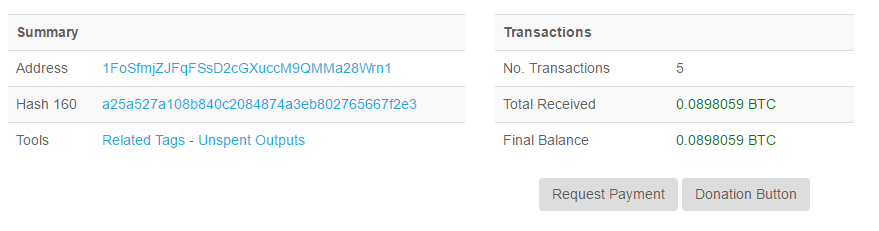
The amount of the latest transaction is 0.069 BTC (approximately equivalent to 500 US dollars).
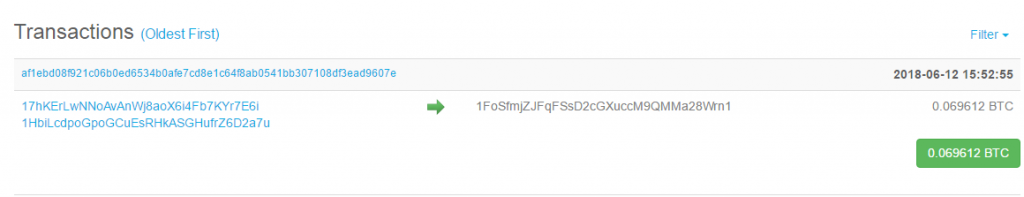
The income from another address:
Reminder
Recently, we have found that a lot of CryptoMiner Trojans are using this technique to steal victims’ cryptocurrencies. We strongly recommend users to enable antivirus software while installing new applications. Users are also recommended to run virus scan with 360 Total Security to avoid falling victim to CryptoMiner.
Learn more about 360 Total Security