A new variant of “Satan” ransomware which had launched attacks to servers exploiting several web application security vulnerabilities was detected by 360 Security Center on Jan. 28th. The new “Satan” ransomware uses another encryption suffix “evopro”, and the extortion information just contains contents in Chinese (In previous version it contains Chinese, English, and Korean info). After successfully invading servers and encrypting files, the attacker demands a Bitcoin ransom. If the victim fails to pay within 72 hours, the ransom will be doubled. This is completely different from the previous version. Such ransomware strategy shows that the attackers currently have a strong demand for ransom.

Pic 1 Encrypted File
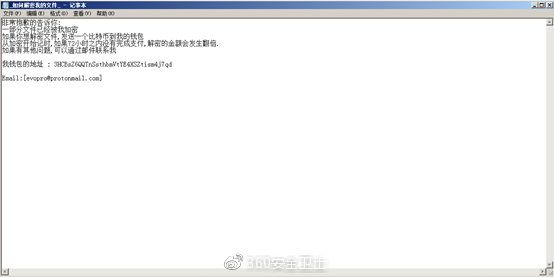
Pic 2 Extortion information
According to the monitoring data of the 360 Security Center, the “Satan” ransomware virus broke out again after nearly a month of silence. The outbreak affected more than one hundred Windows servers, and the number is still rising.
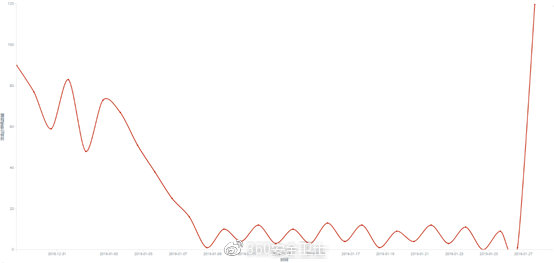
Pic 3 Attack trend in the past month
In addition to the new suffix and extortion information, the “Satan” ransomware also updated its algorithm, using the mt19937 algorithm to generate random numbers for encryption, to avoid the embarrassing situation that encryption is cracked due to the use of low-intensity pseudo-random number generation algorithms. This algorithm is more prominent in terms of performance and strength.
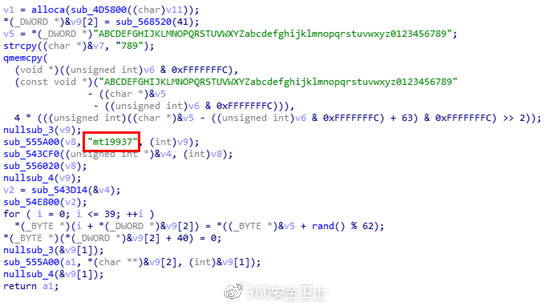
Pic 4 Random number generation algorithm
In response to the updated infection of the “Satan” ransomware, 360 Security Center suggests that server administrators should fix system and web application vulnerabilities and use high-strength passwords. Besides, it is strongly recommended that users download and install 360 Total Security to protect Windows servers from “Satan” ransomware attacks.
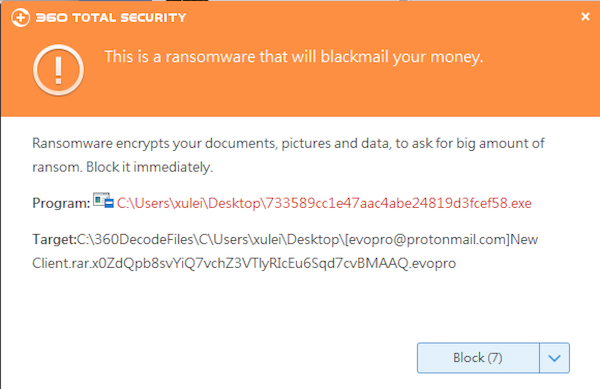
Pic5 Blocked by 360 Total Security
Learn more about 360 Total Security