No patch available for the Microsoft Windows MSHTML remote code execution vulnerability, 360 Total Security takes the lead to intercept it!
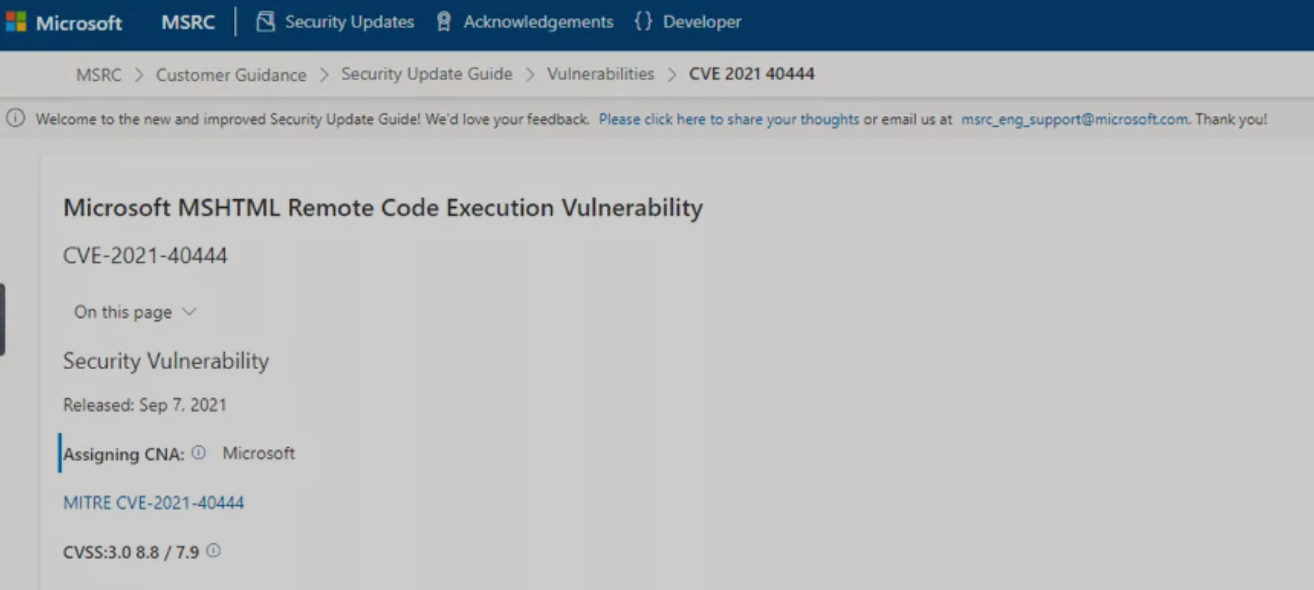
Recently, 360 Security Center monitored that Microsoft officially released an emergency notice about MSHTML components, the vulnerability number is CVE-2021-40444, and the vulnerability level: high risk. An attacker can use this vulnerability to use a specially crafted Office document to launch an attack on the target. A remote attacker who successfully exploits the vulnerability can execute arbitrary code on the target system with the user’s authority. In view of the special CVE number and high-risk attributes of this vulnerability, the 360 security team named the CVE-2021-40444 vulnerability “Necrotic Vulnerability”.
The 360 Advanced Threat Research and Analysis Center has tested and confirmed that any software that uses MSHTML components may become an attack vector, such as Office documents, browser pages, chm documents, etc., which can carry “dead loopholes” to spread. Currently, Microsoft has not officially released a patch for this vulnerability. The “Necromancer Vulnerability” is in a 0day state, and the vulnerability has been detected as an attack in the wild.
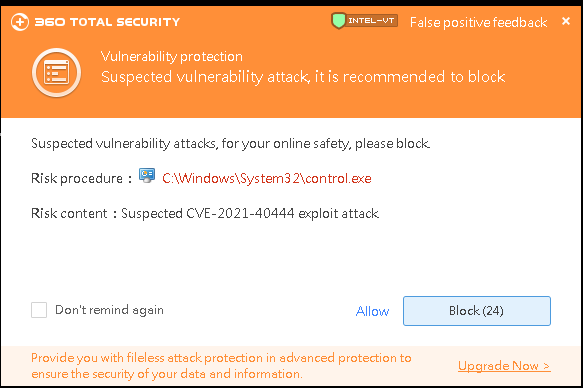
After discovering the high-risk impact of the vulnerability, 360 Security Center completed the analysis and response to the vulnerability as soon as possible, and the first online interception protection was launched on the entire network. With the strong empowerment of 360 Security Center, 360 Total Security can automatically intercept and immune the high-risk 0-day vulnerability attacks to protect user data and property security.
Faced with the risk of this vulnerability, 360 Security Center offers the following security recommendations:
- For the majority of users, you can go to http://www.360totalsecurity.com/ to download the latest version. The installed users will automatically update the protection engine, and they will be automatically immune to the risk of the vulnerability without a patch;
- Do not add trust or exit the security software easily for programs that report viruses by security software;
- Install and ensure that the security software is turned on to ensure its safety protection for the machine;
- Improve safety awareness and maintain good online habits. Do not click links from unknown sources, open shortcuts, documents, etc. of unknown browsers, and regularly check the operating system and common software vulnerabilities, and patch them in time.
Reference link:
https://cert.360.cn/warning/detail?id=b654e8a4ec2b7d93bfe74085794ae658
Learn more about 360 Total Security