Recently, the researchers of 360 Enterprise Security Group Codesafe Team discovered several high-risk security vulnerabilities in Oracle’s WebLogic Server products (CVE-2018-3245, CVE-2018-3248, CVE-2018-3249, CVE-2018-3252) ), and reported to Oracle for the first time to help it fix the vulnerability.
Oracle WebLogic Server is one of the most widely used business application middlewares in the world. On October 17, 2018, Beijing time, Oracle released the Critical Patch Update Advisory (October 2018), publicly acknowledged the Thanks to 360 Enterprise Security Group Codesafe Team, and issued a corresponding patch fix vulnerability.
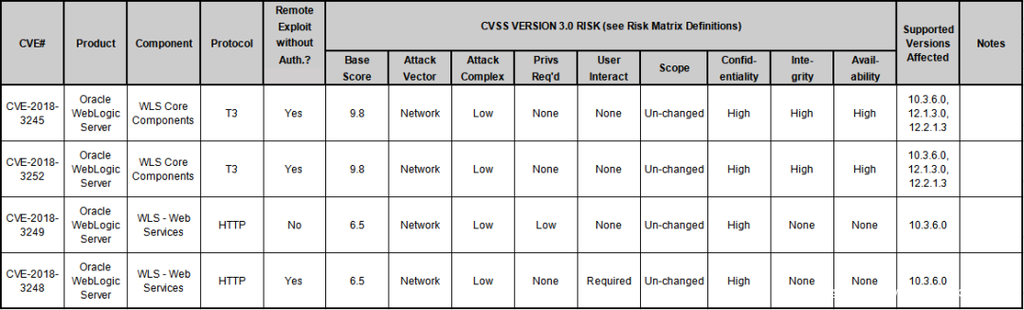
Figure: Oracle’s official announcement

Figure: Thanks to 360 Enterprise Security Group Codesafe Team
Among the vulnerabilities fixed by Oracle, CVE-2018-3245 and CVE-2018-3252 are high-risk deserialization vulnerabilities, affecting multiple versions of WebLogic. The CVSS score is 9.8. Under certain conditions, remote code can be generated. This article will briefly describe these two vulnerabilities.
Vulnerability Overview
CVE-2018-3245 (JRMP Deserialization via T3)
The vulnerability is a bug that bypasses the patch and can be bypassed in Oracle’s July patching feature that fixes the JRMP deserialization vulnerability, causing the patch ineffective. The vulnerability is at high risk and can execute arbitrary code remotely.
CVE-2018-3252 (Deserialization via HTTP)
The trigger of this vulnerability is not the officially described T3 protocol, but can be triggered by HTTP (more harmful, HTTP general firewall can pass). Due to the release of the patch, there are a large number of WebLogic Servers that are not patched in time on the Internet. The details of the vulnerability are temporarily not disclosed.