Ransomware has posed a serious threat to the data security of enterprises and individuals. Fortunately, 360 Internet Security Center has detected and defensed ransomware immediately. According to the feedback from our users, we found that the number of our users attacked by ransomware shows a slight upward trend in August. Also, the highest number of single-day interceptions for weak passwords reached more than 6 million times, which is 200 million times higher than the previous month.
Analysis
The statistics on ransomware infection of 2018 shows that the number of infected users has a slight upward trend from July to August, due to the new appearance of KEYPASS family, ACCDFISA family, and ONI family. At the same time, the number of users infected with GlobeImposter also grew up dramatically after mid-August.
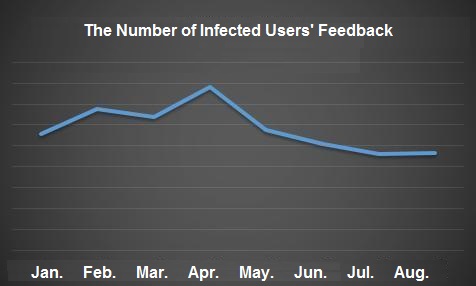
From our users’ feedback data for August 2018, the number of ransomware spread through software vulnerabilities and system vulnerabilities decreased significantly. Hackers still saw through enabling victims’ rdp (Remote Desktop Protocol) as the first choice to spread the ransomware. To attack victims’ rdp, hackers mainly exploited the negligence of server administrators who set weak passwords for server accounts. Although weak passwords are commonly set to make their login process much easier, it leaves a door wide open for hackers to launch attacks.
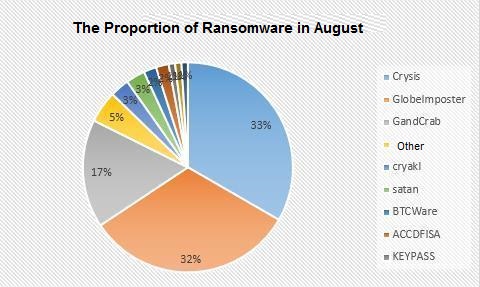
After analyzing the data for August, we found that in mid-late August, two large increases in the number of ransomware infections were caused by the outbreak of the GlobeImposter family.

For the analysis of infected systems, the infection volume of Windows 7 system is still by far the largest.

But by comparing to the infected system in the previous month, it is found that the number of infected systems increased from 10% to 22% between July and August. The compromise of the server systems commonly means that there are still many machines in the enterprise that are threatened. There are two main reasons that cause the servers of the enterprise to be infected. The first of these is the opening of shared folders within the enterprise and the lack of proper rights management. The second is the machine that has the Remote Desktop Protocol enabled on the intranet. The security of the server is important, and the increase in the proportion of infected servers means that the risk of ransomware is much higher.
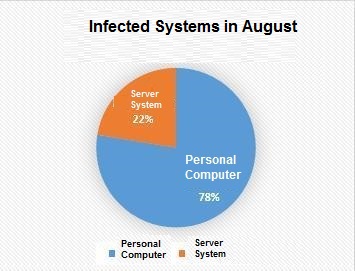
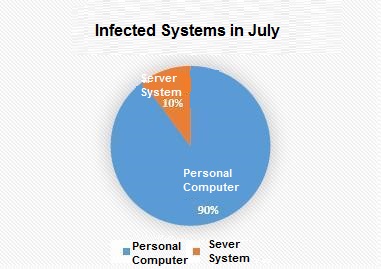
The latest information about ransomware attacks
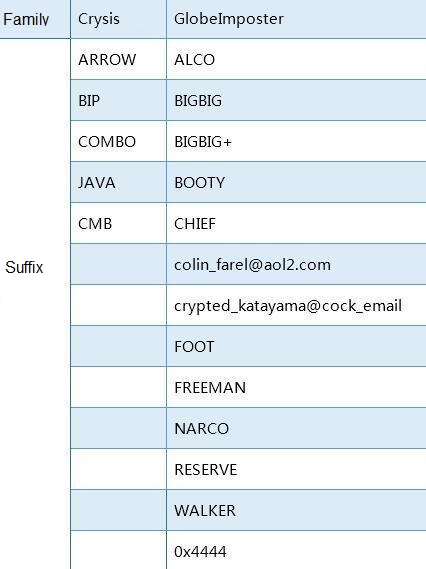
The GlobeImposter family and Crysis family are still the mainstreams of ransomware. Both families have new variants of the suffix this month (Crysis-cmb, Crysis-COMBO, GlobeImposter-NACRO, GlobeImposter-0x444), but the two family samples did not add any new features.
The following suffixes and new variants are still being used by both families.
After doing the research of the GandCrab ransomware family, we found that this family has by far the most spreading ways compared to the others. The ransomware family can be spread in a variety ways:
* Send phishing emails to induce users to open attachments. Use file name similar to Payment #72985.
* Attack the computer that is running the Remote Desktop Protocol and try to get the user’s machine password. Manually install the ransomware to the user’s machine.
* Spread the ransomware using RIG EK and GrandSoft EK exploit kits.
* Disguise as cracking software to induce users to download and execute files.
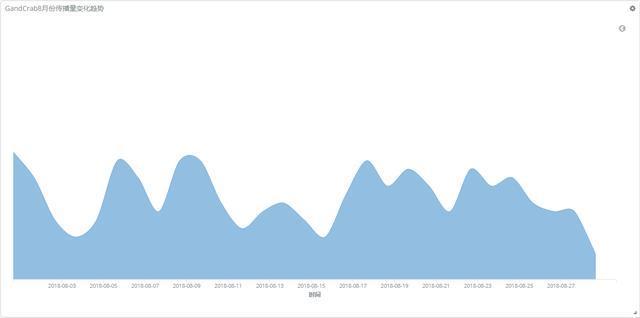
The following is a graph of the GandCrab family’s transmission trend changes detected by 360 Total Security this month.
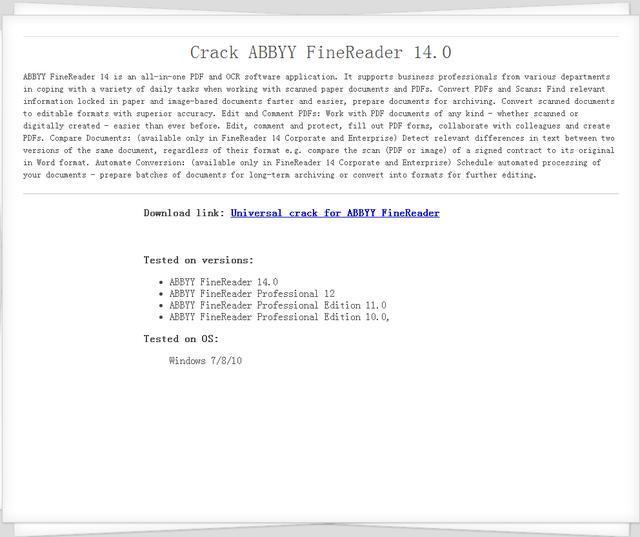
In the feedback case we received this month, there are several cases that users were infected through accessing fake cracked software download page. The user usually downloads the cracked software and then makes the files encrypted. The following is one of the cracked software download pages.
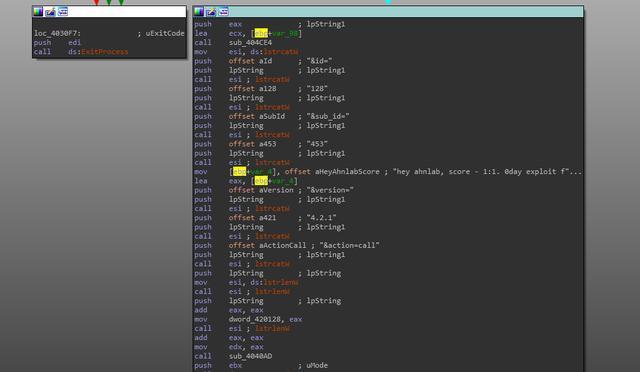
After a security company in South Korea released the GandCrab key last month, it was attacked by GandCrab ransomware makers. Since v4.2, the company has added a Denial of service attack code to the company’s antivirus software, which crashed the antivirus software.
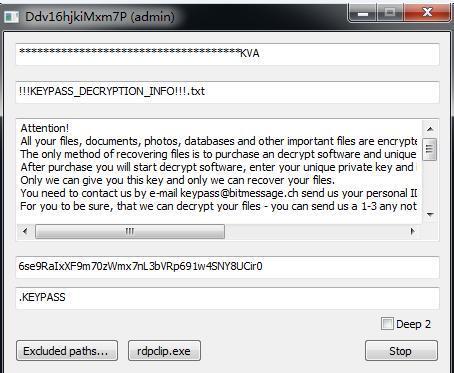
In August, the researchers of 360 Security Center discovered a new ransomware, KEYPASS. It is spread by disguising as a Windows Activator. The ransomware has a hidden function that can be activated by pressing F8 after running the ransomware. This hidden feature allows ransomware creators to make their own encryption programs. The following can be modified through the interface:
* The key used to encrypt files
* The name of extortion file
* Ransom message
* ID used to identify the victim
* The suffix of encrypted files
Jigsaw is a ransomware that is available on the black market and is also known as “Puzzle Game.” The ransomware family is one of the ransomware which has most variants. This month, the Chinese version of the ransomware family was discovered, which is spread by disguising a plugin to temp users to download. However, the ransomware is written in the .NET language and can only be executed in the system which has .NET framework.
The following are the ransomware contact emails used by hackers since August (listed some common emails):
Conclusion
The ransomware attack against the server has become a major direction of the current ransomware. Enterprises should strengthen their capabilities of information security management, especially weak passwords, vulnerabilities, file sharing and remote desktop management. Here are some suggestions to administrators:
1. Do not use the same account and password for multiple machines.
2. The login password must be complex. A password structure should be a mixture of uppercase and lowercase.








