What is TeslaCrypt?
TeslaCrypt is a type of ransomware, first detected on February 2015. It originally affected computer gamers, since it was infecting mostly gaming files, such game saves, custom maps, recorded gameplays, player profiles, etc. However, latter versions also target a wider range of filetypes, including JPEG, Word, PDF, etc.
TeslaCrypt encrypts user’s files and prompts a message asking the user $500 ransom in bitcoins to obtain the key to decrypt the files. TeslaCrypt’s behaviour is very similar to Cryptolocker, since both of them are ransomware, although they have been developed independently and don’t share code.
Recently, the creators of TeslaCrypt have released the master decryption key to the public, thus shutting down their ransom business model. However, the malware is still circulating on the internet.
Ransomware is an increasingly popular type of malware, and it is important to have backup copies of all your files to reduce the impact of this malware in case of infection. It is crucial to have an updated antivirus installed on your system. Download and install an antivirus if you don’t have one, or update yours to the latest version if you do.
How to remove TeslaCrypt from my computer?
Follow these steps to remove this malware from your computer, if you have been infected:
1.- First of all, back up all your encrypted files, to avoid losing them in case something goes wrong.
2.- Download the decryption tool from this link, and extract it to your computer.
3.- Run the file named ‘Decryptor.exe’ and then select the file you’d like to scan.
4.- The tool will start running. If the tool detects an infection, follow the instructions on the screen to clean your computer.
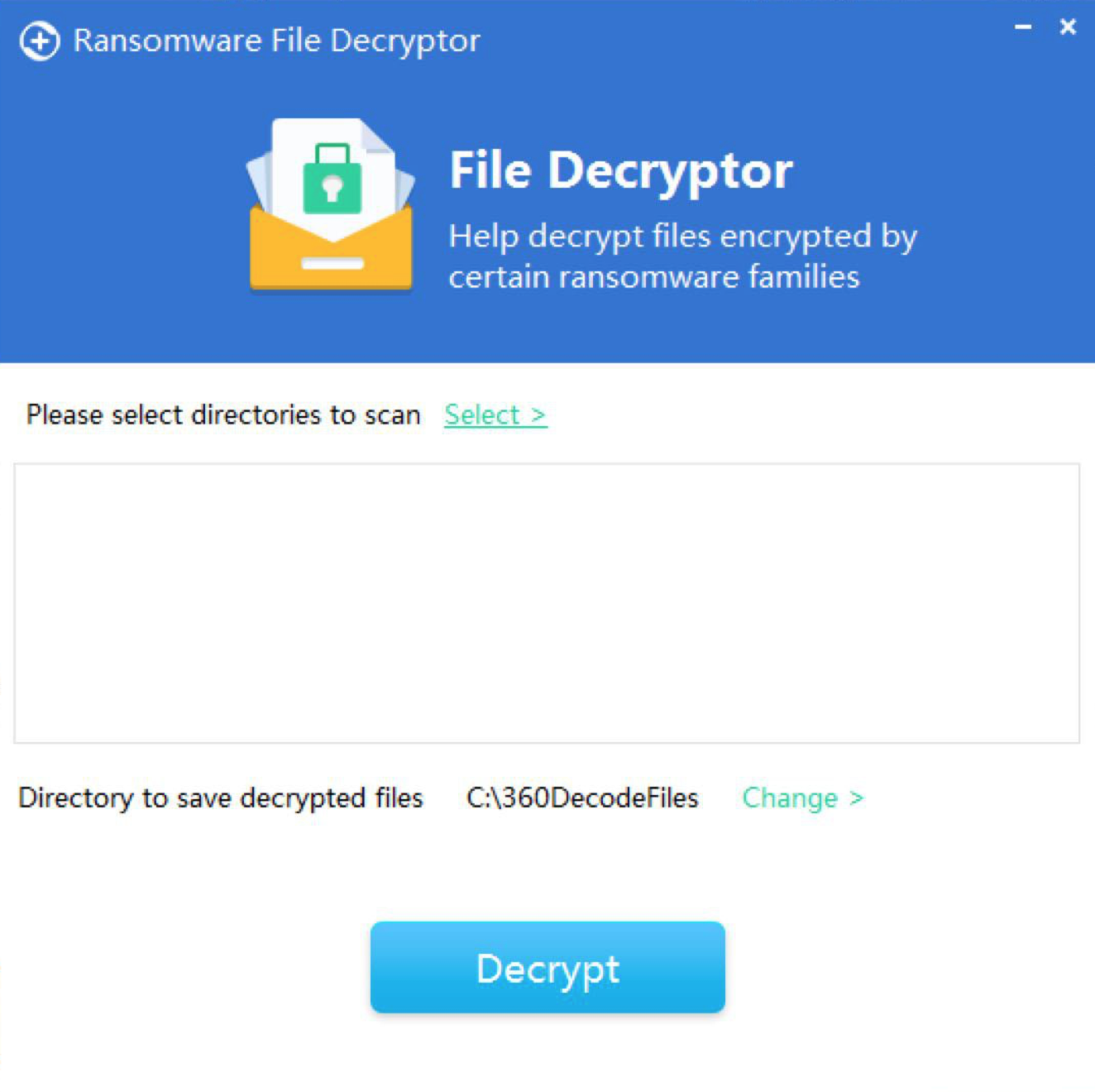
360 Total Security also includes a feature to protect you against ransomware. Help your friends to protect themselves against this kind of ransomware, and share this article with them!
Read more:
- What is ransomware?
- Data hijacking protection feature in 360 Total Security
- Bitcoin used as ransomware currency
- Jigsaw ransomware threats with deleting your files
Learn more about 360 Total Security