A new file-encrypting ransomware “Telecrypt” was discovered targeting Russian-speaking users earlier this month. This malware abuses the instant messaging service Telegram by using its communication protocol to send the decryption key to attackers.

Telegram was abused as a communication channel by crooks
In a typical file encryption malware case, a cryptor program is inserted to a victim’s PC to encrypt files. In some cases, crooks may send the encryption key to a cryptor and receive data from it. The information collected will be used to unlock encrypted files when ransoms are paid.
Receiving data from a cryptor requires some other services, which leads to an additional development cost. To avoid extra costs for communications between the malware and its server, Telecrypt’s creators decide to use Telegram for command and control. And this is also the first encryption malware attack known to exploit Telegram.
How Telecrypt infects victims’ PC
Once launched, Telecrypt encrypts victims’ files ranging from Word, PDF, Excel, JPG, JPEG, PNG to database files (DBF).
Security experts explain, “A list of encrypted files is saved to the text file ‘%USERPROFILE%\Desktop\База зашифр файлов.txt’.” The malware may add the extension ‘.Xcri’ to the encrypted files, but researchers also find a sample file with its extension unchanged.
Despite that there is no further revealing for how this ransomware is inserted into end users’ PC so far, the infection path is disclosed as below:
• Before the infection, the threat actor creates a “Telegram bot” for later communications.
• When first launched, Telecrypt generates a file encryption key and an infection ID. Then it checks if the aforementioned Telegram bot is already existing.
• Once confirmed, this malware uses Telegram’s publicly available API to inform the attackers of the successful infection. It also sends back information of the infected system, including the computer name, infection ID, and the number used as a basis to generate the file encryption key.
• The ransomware searches its victim’s hard drive for certain files and encrypts them. It also informs the attackers via the Telegram bot when the encryption finishes.
• Telecrypt downloads an executable file from a compromised WordPress Site. This graphic interface displays a ransom note telling the victim what happened and how to pay 5,000RUB($77) via Qiwi or Yandex.Money to get their files back.
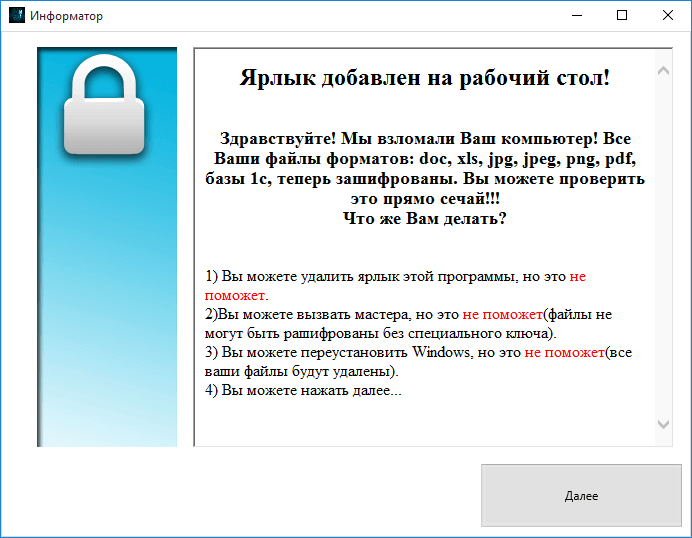
Security experts suggest that victims should not pay the ransom; instead, they should turn to security solution providers to get help for file decryption.
Learn more about 360 Total Security







